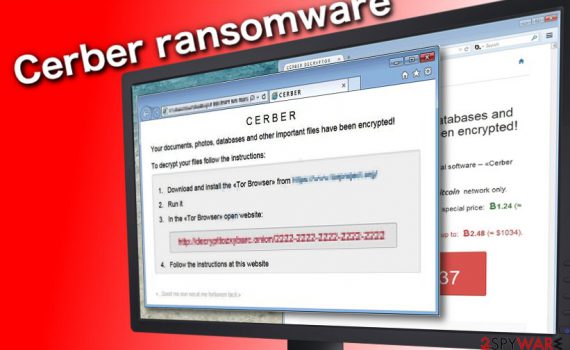
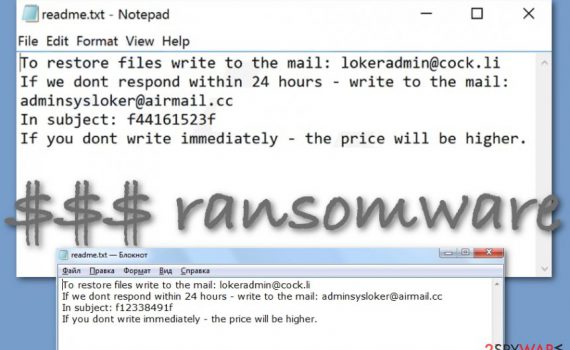
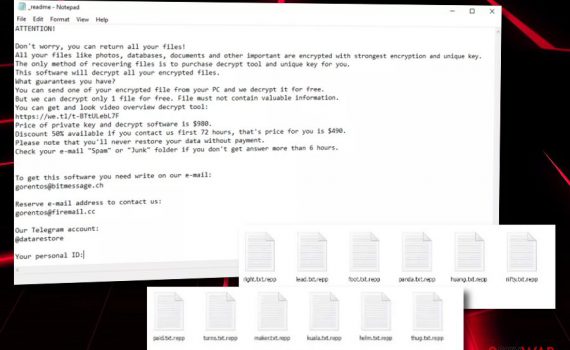
Alka ransomware is the cryptovirus that encrypts files and corrupts the system settings in several attack stages Alka ransomware – malware that extorts a particular fee for the alleged decryption tool that should help to unlock encoded files marked using .alka extension. It is a version of the DJVU virus that […]