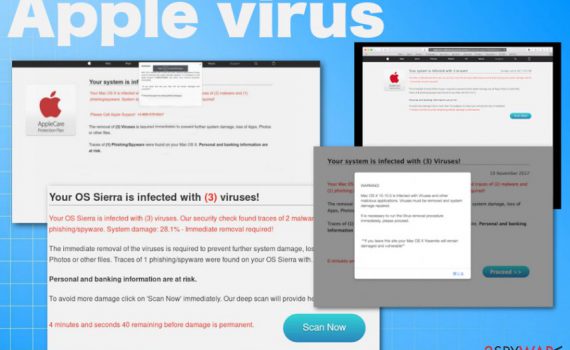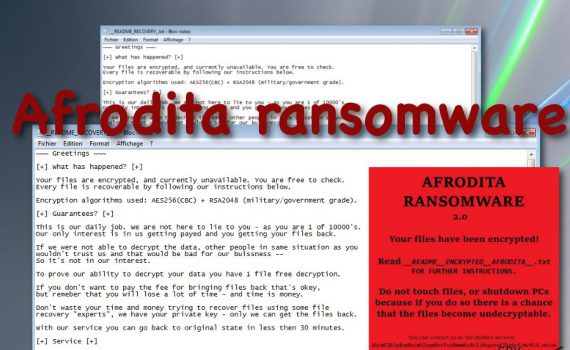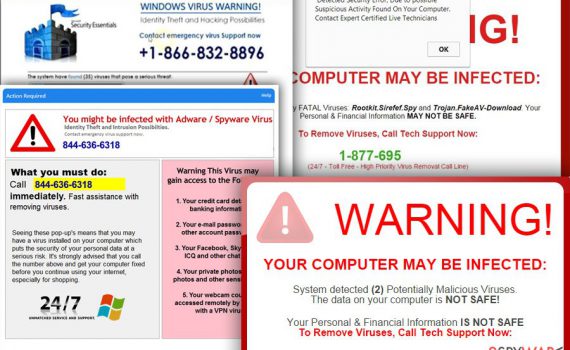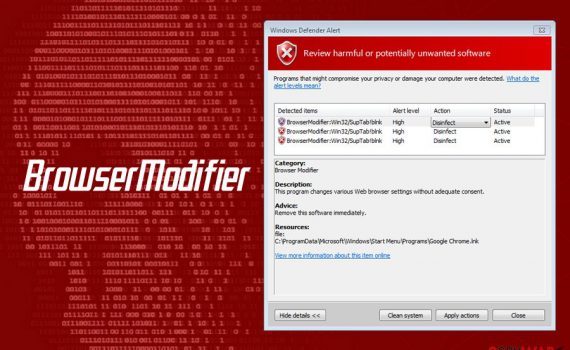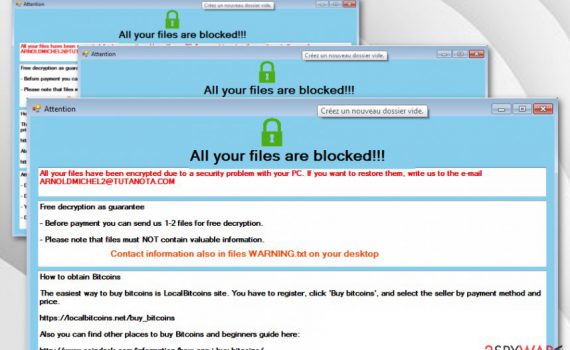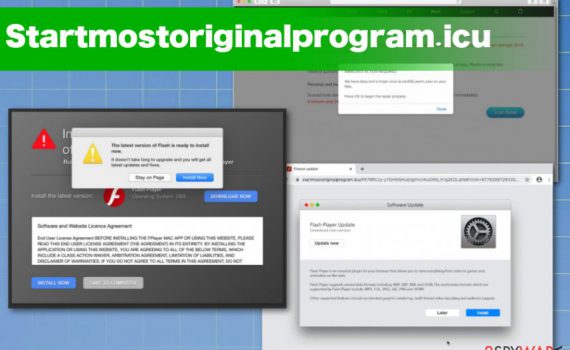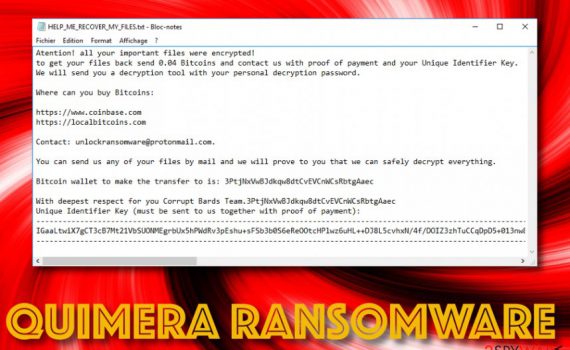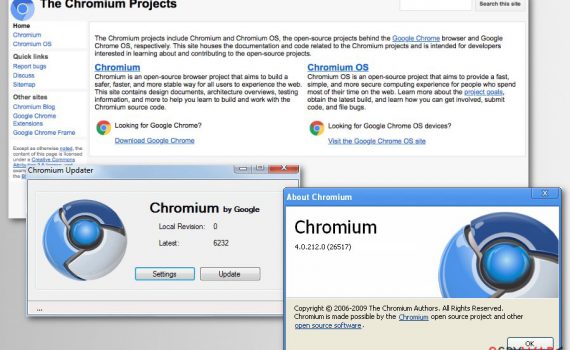
Chromium virus is a browser virus misusing the name of the legitimate Google open-source project Chromium is a legitimate project by Google. However, the application is often modified to launch malicious examples that can harm end-users. Chromium virus is a term used to describe malicious browser application that is using […]