Malicious actors decide to follow the well-known trails that were first employed by Maze ransomware operators
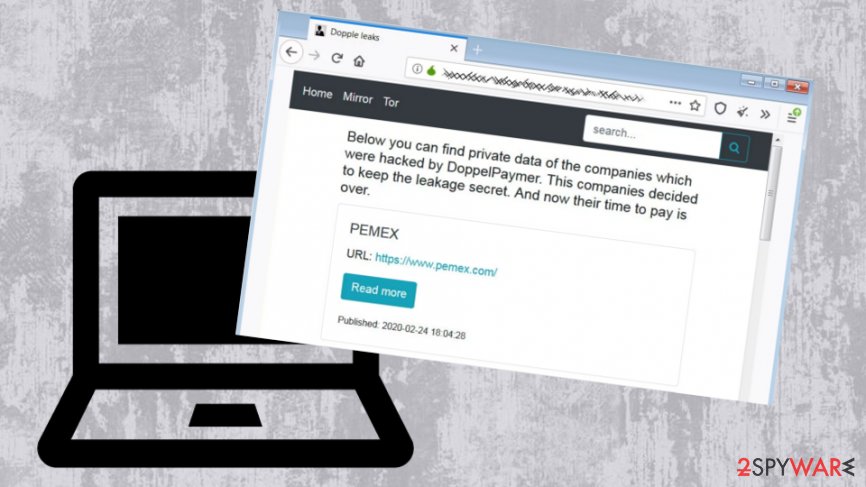

The creators of DoppelPaymer ransomware have configured a website called “Dopple leaks” that reveals private information collected from users who disagreed to pay the demanded ransom. The exposed information is supposed to include the files that were leaked from Windows computers before the encryption.
This technique was first used by Maze ransomware distributors[1] as a way to receive ransom payments by threatening victims that their collected data will be revealed to law enforcement agencies or sold online for profits. It seems like threat actors of other ransomware strains, such as Nemty, Sodinokibi, and the mentioned DoppelPaymer, also decided to follow the same path.
Pemex – one of the few companies data of which was published on the site
The “Dopple leaks” website that is owned by DoppelPaymer ransomware creators has been released on February 25, and already includes four company names, along with their data. One of the well-known firms is Pemex that suffered a ransomware attack in the first half of November last year.[2] Malicious actors asked for $4.9 million to be paid in exchange for the decryption tool, and the company refused to comply.
Other companies that are listed on the Dopple leaks website also have received ransom demands of $150K to $500K – a much smaller sum in comparison to Premex.[3] The malicious actors have been more interested in revealing Pemex’s information and claimed that the other three firms did not hold any valuable information combining to the first one, which explains lower charge rate when it comes to the other three firms.
Furthermore, DopperPaymer owners claim that their website is still being tested, and its main goal is to shame the victims that did not agree to pay the ransom by providing their names and file content publicly. This way, anyone can access the exposed data and documents, as well as misuse the information for illegitimate purposes such as identity theft, scams, spear-phishing attacks, as well as data sale on the underground market.
Be careful online to avoid getting your files encrypted and receiving huge ransom demands
DoppelPaymer is a ransomware virus that encrypts files on the infected Windows computer, also steals them, and provides high ransom demands in exchange for the recovery tool. The main target of this malware is rather worldwide companies than regular users but you still cannot deny the risk of getting infected by this ransomware virus even if you are not running a popular business.
DopperPaymer employs the AES-256[4] and RSA-2048 ciphers to lock up all files and documents that are found on the infected computer system.[5] Afterward, all files receive the .locked extension and cannot be properly accessed anymore. Then comes the ransom note and urges to contact the cybercriminals in order to get the decryption tool for a specific amount of money.
The best way to avoid ransomware attacks and receiving huge ransom demands is to stay focused on your online work every time you are completing a browsing session. Do not click on any links and advertisements that look strange to you, do not open any phishing messages and, especially, do not execute their attachments. Furthermore, avoid downloading software, films, and various tools from torrenting websites that often hold infected cracks.
