Potential victims receive fake email messages from Who asking them to click on a link or download a file

The Coronavirus scandal, also recognized as COVID-19, has overflown the entire planet very fast and some hackers decided to misuse it for their own goals. Recently, crooks were found impersonating World Health Organization (WHO) representatives while trying to deliver misleading content related to the infection via email messages.
Phishing emails look like they are sent by the WHO but, in fact, come from an unknown location where the cybercriminals are working from. The main goal of such messages is to convince the user to click on a hyperlink, download some type of attachment, verify email addresses, or provide personal details, including passwords and usernames.
A phishing campaign is redirecting users to an email verification page
Earlier this month, Sophos researchers released a report on Coronavirus-related phishing campaigns.[1] The reporters discovered that cybercriminals were targetting potential victims by sending them such email messages:
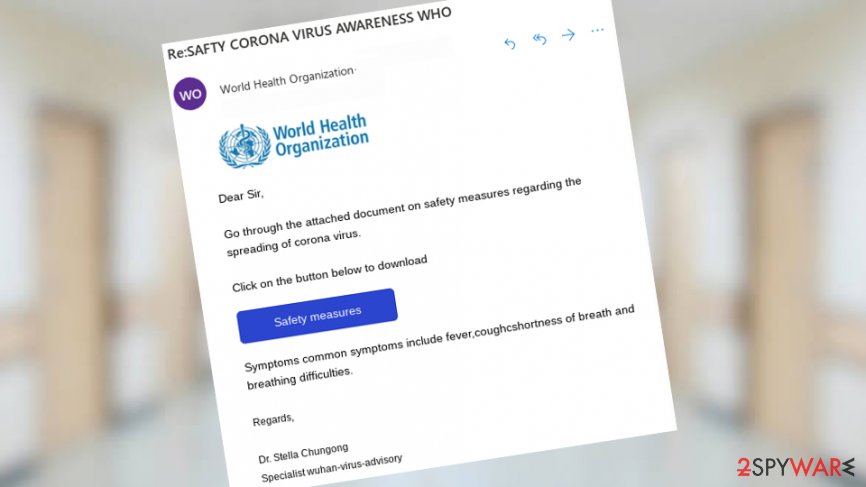
Dear Sir,
Go through the attached document on safety measures regarding the spreading of corona virus.
Click on the button below to download.
[Safety measures]
Symptoms common symptoms include fever,coughshortness of breath and breathing difficulties.
Regards,
Dr. Stealla Chungong
Specialist wuhan-virus-advisory
Even though the “Safety measures” button is claimed to download some type of attachment that should provide the users with more information on how to protect themselves from the widespread infection, it does not do anything like that. A click on the given button redirects users to a phishing website that opens the official WHO domain in the background of the computer and provides the user with a new pop-up window asking for email verification.[2]
You should not type in any private data such as your username and password as these details will fall in the hands of the hackers. If you do enter the required information and hit the “Verify” button, the gathered data will be transferred to a remote server that is held by the cybercriminals and uses an unencrypted HTTP connection.[3]
Afterward, the victim is sent back to the official WHO website like nothing had happened whereas the crooks will have swindled personal data.
The name of Coronavirus infection has already been misused for malicious purposes
The previously-mentioned email spam campaign is not the only one that has tried to capture victims. A little bit different but still an email-orientated attack was initiated at the end of January this year when criminals used misleading information to distribute Emotet Trojan virus.[4]
Spam emails had reached Japanese people from territories such as Osaka, Gifu, and Tottori. The content of the text warned about the widespread infection and claimed that the users could find more important details about it in an attached file which truly appeared to be the malicious payload.
The malware-laden content came in the form of a Word document which is a popular way of spreading trojans. When the user opens the file, he has to click on the “Enable Content” section to activate the macros and start the installation of Emotet. Afterward, the virus continuos to steal private and banking information and can even bring another Trojan horse to the computer system known as Trickbot.
Protective measures are crucial while trying not to fall for misleading emails
World Health Organization encourages all users to report a scam if they see one.[5] The company has also provided some security tactics that every person should use while trying not to fall for scammers’ tricks. First of all, you should always check if the email is coming from a well-known email address as it would be [email protected] for the WHO and this is the only type of email that the organization is using for contacting its clients.
Also, the WHO recommends investigating every hyperlink that is included in the email message before clicking on it. In this case, the link should look like this: https://www.who.int. Furthermore, always be aware if someone asks for personally-identifiable data from you as there are not many reasons why one would need such type of information.
Another security tip that we want to add from ourselves is to check for grammar and typo mistakes when an official message falls into your inbox. We have analyzed the email that was reported by Sophos and found a few mistakes in the content. For example, hackers did not separate the words “coughshortness”, mentioned the word “symptoms” two times in the same sentence, and so on. Keep in mind that a trustworthy organization will always deliver their notes free of such mistakes.
This entry was posted on 2020-02-19 at 09:39 and is filed under News, Spam and phishing.
