Scammers seek to take advantage of pandemic fears by sending phishing emails that lure recipients to visit malicious websites
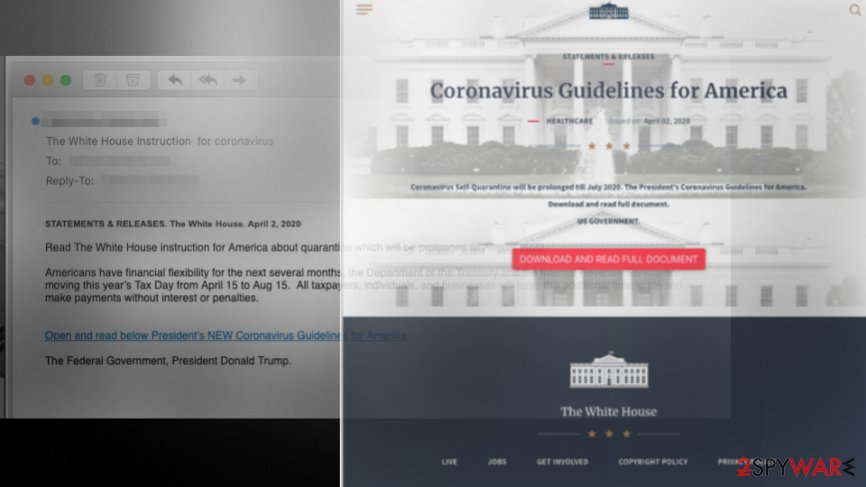

INKY researchers report that scammers impersonate White House, President Donald Trump, and Vice President Mike Pence on email notifications listed as informational alerts for citizens.[1] Global pandemic and sensitive time in the world comes with more active criminal activities.[2]. This campaign is not the first and not the last that involves COVID-19.[3] The particular phishing emails tarted users to trick them into visiting malicious websites and downloading malware on their devices.
People all over the world wait for the updates, search for more information from officials and government in their country, so scammers decided to take advantage of such unprecedented times. Phishing email campaign analysis revealed many attempts to take people to malware-laced sites and expose them to extortion campaigns. Scammers even aimed to impersonate real people from Trump’s office by including names of presidential spokespersons Valentina and Rosie as senders.
Scammers rely on the macro virus technique
Coronavirus guidelines on behalf of President Trump delivered via these emails, can distribute malware or trigger extortion scams-based messages. Notification encourages people to click on the hyperlink that launches the download of the document with an alleged document with “Coronavirus Guidelines for America” name.
Clicking on the link redirects the user to a website that further impersonates the White House and contains the button “Download and read the full document.” One users’ click on the button automatically launches the download a malicious Word document that encourages people to enable the content further or allow editing by clicking on the Enable editing button to view the contents.
Once the content is enabled, malicious macros[4] get launched and installs malware on the computer of the person that received this phishing email. This is a common way that cybercriminals use to spread malware, like ransomware and trojans, around.[5]
The initial phishing site is taken down, so the malware is no longer distributed, but there are many other attacks with the same techniques. The malicious website was authentic, and the high success rate was based on this fact, as explained by INKY researchers:
It’s an exact HTML and CSS replica of the exact content on the real White House Coronavirus informational site at the time these emails arrived. The attacker’s easiest path to creating convincing fakes is not to create any content at all, but simply to copy a real email or website.
People more likely to fall for such scams during sensitive times
Many vendors have reported these phishing email campaigns that rely on the global panic state. Criminals seek to distribute their malware, steal credentials, and data from gullible internet users. Unfortunately, campaigns distribute successfully because people fall for these scams even though reports get released all the time.
Security experts state that users as falling for COVID-19-related scam emails more often and in larger numbers when compared to regular phishing emails. Anything related to President, government, or Vice President- related officials[6] should be taken into consideration. You need to notice that emails are filled with typos, grammar mistakes.
The best method to stay safe is skepticism because being suspicious during these times can keep your device safe from malware and keep your privacy secure.
This entry was posted on 2020-04-10 at 08:16 and is filed under News, Spam and phishing.
