Pakistan-related hackers use Coronavirus health advisories to infect potential victims

COVID-19 appears to be not such a bad thing for some remote hackers when it has placed fear throughout the rest of society. Crooks have discovered many ways how to abuse the name of the Coronavirus disease for their own benefits and distributing Crimson RAT (remote administration tool)[1] through phishing emails that include health advisories for protection from Corona appears to be another malicious tactic that was recently reported by cybersecurity researchers.
Experts suspect a Pakistan-based hacker group to be responsible for this type of activity. They believe that the guilty ones are hiding behind the name APT36 that is alternatively known as ProjectM, Mythic Leopard, Transparent Tribe, and TEMP.lapis. This malicious actor group has first shown up in 2016 and employed various malicious software since then.
However, APT36 is mostly interested in the distribution of Remote Administration Tools and Crimson is not the first one that they have tried to spread. In the past, the group has also employed other RATs such as DarkComet, njRAT, Luminosity RAT,, and BreachRAT.
During their past work, the hacker group was able to break into Indian military and government databases, access and steal information such as training data, strategy documents, official notices, passport copies, personally-identifiable content, written text notes, contact information.
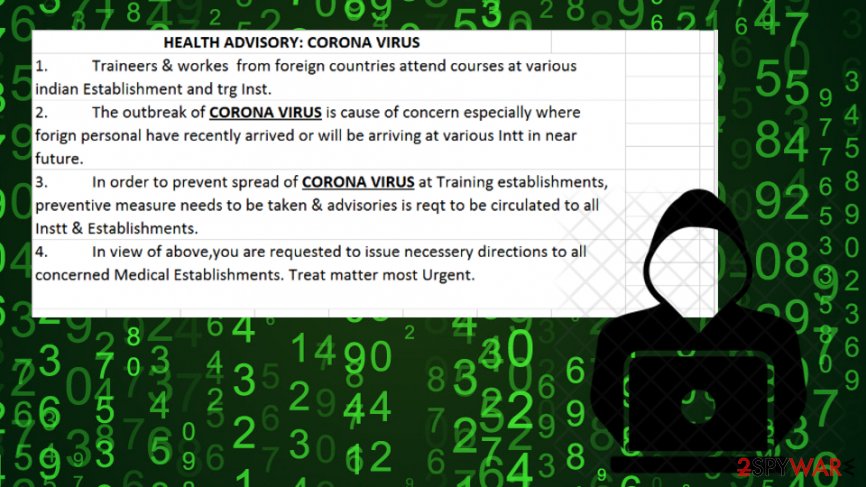
Enabling macros in the malicious executable file executes the Crimson RAT payload
Malicious executables spreading the RAT-related payload by the delivery of Coronavirus phishing emails were first discovered by RedDrip Team who announced their findings on the Twitter social platform.[2] According to these cybersecurity researchers from China, the hacker group pushes health advisories to notify people how to protect themselves from the Coronavirus disease. However, the aim of these messages is not to inform the scared society about prevention.
APT36 seeks to distribute Crimson RAT through executable files and RTF documents which aim to exploit the CVE-2017-0199 flaw[3] that is related to Microsoft Office and Notepad. When the user opens the received file, he is encouraged to enable macros. If this is done, the RAT-related content will be executed via a 32-bit or 64-bit variant relying on the type of operating system the victim is using on his computer.
When the malicious payload is launched, the remote administration tool will connect to a remote C&C server where it will be able to deliver all gathered information about the computer’s owner and the machine itself (hostname, username data, active processes, etc.).
Furthermore, ATP36 can employ Crimson RAT for a wide range of activities such as catching screenshots on the infected machine, accessing personally-identifiable information and valuable files, stealing some financial data from the browser app, capturing active software and drives, gathering details related to antimalware tools.[4]
Past attacks related to Coronavirus disease name
The deployment of Crimson RAT is not the first time when crooks abuse the name of the Coronavirus infection. Not so long ago, hackers thought about a way how to trick users who are feared and interested in the spreading disease nowadays. This is how the crooks came up with an idea how to spread malware by pushing maps that show areas in the entire world that have been already infected by the Corona disease.[5]
Criminals decided to steal reliable information from Johns Hopkins University and provided the exact same map to people so it would not look suspicious in any type of way. However, when the users are searching for infected areas, counting deaths and recoveries, the malicious payload is getting executed in the background of their computers. The map app releases malware that contains a module related to the AZORult Trojan virus. This means that users can get personal and credential information easily stolen from their machines.
Other malicious events regarding the Coronavirus name were related to email phishing. Some scammers pretended to be from the World Health Organization and delivered “Safety measures” to users which opened could also have launched malware. Other hackers also distributed misleading emails holding Word documents that included the Emotet virus.
This entry was posted on 2020-03-18 at 08:15 and is filed under News, Spam and phishing.
