ProLock ransomware is the self-named cryptovirus that uses PowerShell to inject malicious scripts into memory
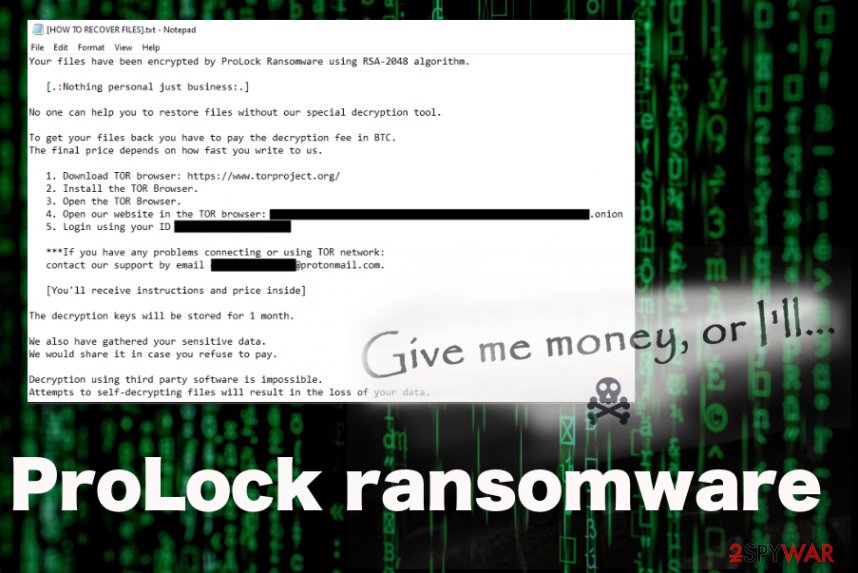

ProLock ransomware – malware that adds .ProLock extension to files after encryption and greets victims with a particular threat name. Virus developers provide all the information in a text file placed on the desktop and in other folders with encoded data that is named [HOW TO RECOVER FILES].txt. This ransom note informs victims about the encryption method used – RSA-2048[1] and possibilities to get files restored after the payment. This is typical ransomware virus behavior because malicious actors who spread these extortion-based programs are focused on getting money and scaring people into paying for useless or non-existent decryption tools.
Most often threats like this ProLock ransomware virus starts the infection with encryption procedures. When the victim decides to pay and contact criminals, they can follow up with all the background processes, in the meantime. This is a new threat, so researchers[2] only can speculate and base their judging on samples that can be obtained. It is thought that this malware spreads around using exposed RDP or by using cracking tools and keygens. These methods become more and more common for ransomware than the before-used spam email campaigns.[3]
| Name | ProLock ransomware |
|---|---|
| File marker | .ProLock is the appendix added to every encrypted file that differentiates affected files from safe ones |
| Encryption method | RSA-2048 – army grade algorithm used to modify the original file code and make data useless, so there is the reason for ransom demands |
| Distinct feature | .BMP picture file is used to inject malware into memory via PowerShell |
| Distribution | Typical ransomware threats get distributed via spam email campaigns when infected files get attached or malicious sites that drop the malicious script. This malware spreads using unprotected RDP or via pirated software services |
| Ransom note | [HOW TO RECOVER FILES].txt delivers the message from ransomware creators, so people can know what to do next and follows strict instructions of contacting them and paying the ransom. This is the file where malicious actors determine the name of this ransomware |
| Elimination | ProLock ransomware removal should be quick, so choose professional anti-malware tools for the procedure and ensure that all virus-related applications and files get deleted |
| Repair | System functions needed for file recovery or virus termination can be disabled by the threat itself because it alters files and adds net entries to control the functionality. Repair these corrupted programs and files with the help of Reimage Reimage Cleaner Intego or a similar tool |
ProLock ransomware, as any other cyber threat, is developed by criminals, so there are many additional features that this cryptocurrency-extortion based virus can have. Of course, the most frustrating is encryption and file-locking because your files get altered and become inaccessible without guaranteed recovery possibility.
However, the newer features of these threats started to involve data exfiltration from the machine directly or the web browser. In the ransom note, ProLock ransomware mentions having gathered sensitive data and claims to share those details if you refuse to pay. There a few different scenarios regarding such data recording. Malware creators may copy known techniques of threat actors who have published non-paying victims’ data online and:
- collect information from devices or online accounts with keystroke loggers, other malware, worms, and so on;
- trick people into believing they did so to make people more scared and willing to pay up.
Do not fall for these tricks and malicious techniques, you should remove ProLock ransomware instead. The sooner you run an anti-malware on your machine the quicker you can get to your files. Anti-malware programs are based on virus detection engines, and a full system scan allows the application to detect, find, and delete all the malicious intruders and files planted on the system.
Deleted Shadow Volume Copies keep the ShadowExplorer out of the list for data recovery methods, disabled security functions cannot provide you the detection and virus identification needed for system cleaning. ProLock ransomware can also install direct trojans and information-stealers, so private and sensitive data is at risk, and you may become a victim of the targeted scam later on. Make sure to double-check that there is nothing malicious or possibly dangerous on the machine when you add the external device with your data backups. 
ProLock ransomware is the new cryptovirus that cannot be analyzed without samples, so more details may get discovered in time.

ProLock ransomware is the new cryptovirus that cannot be analyzed without samples, so more details may get discovered in time.
Unfortunately, there are no indications about the infection before ProLock ransomware displays some symptoms itself, so you cannot react before encryption. However, encryption, in most cases, is the first step, so when you get the ransom demanding note – get a security tool and run in on the machine. You may get rid of the threat before any crucial damage is done.
Even though ProLock ransom note file states about the possibility of getting your files decrypted, you cannot know how big the ransom amount is. This question is the main one that people ask criminals via the email or TOR website link provided in the note. This communication can lead to the installation of additional malware or direct access to your device if you don’t pay attention to connections that criminals make via email notifications or the website. Experts[4] note to stay away from these malicious actors at any cost.
ProLock ransomware is reportedly injecting code into the memory of the device and adding additional files on the system to affect the persistence and possibly damage the device further. You should take that into consideration and clean the system properly from any malware.
ProLock ransomware removal can get difficult because of this PowerShell functionality any fileless malware execution is easier than you may think. Attackers can rely on this system tool and load automated scripts of malware that also can become a way for criminals to directly launch the attack.
One of the more common ways used to spread malware like ProLock ransomware virus can rely on breaking through unprotected remote desktop connections or using pirating software services and deliver payload as a file included in one of the cracking tool packages. You may have already been exposed to a few different types of malware, so an automatic anti-malware tool check is crucial for the security of your machine.
Hijacking RDP – method to spread malware around
The feature that allows connecting to another session is useful for many people, but can also be used by malicious actors. In most cases, such features should be protected by passwords, but unprotected RDP configurations can be easily broken into and used to distribute malware or directly access the machine.
Criminals have various methods of identifying particular RDP sessions that are vulnerable and possibly exploitable. So attackers can steal identities, logins, other credentials, and install or launch malware, including ransomware. You need to protect such sessions if you continuously use these tools and make sure to avoid any other dangerous activities:
- spam emails with attachments that may include malicious macros;
- hyperlinks randomly included in such email notifications;
- pirating services and downloading cracks or cheats from such pages.
Terminate the dangerous ProLock virus and related files or apps
There are no particular connections between already known malware and ProLock ransomware virus, so you should consider this new variant more dangerous and powerful because of this. There are many unanswered questions since researchers cannot get needed malware samples and fully test them.
However, based on the facts that are known right now, you can try to remove ProLock ransomware using typical malware elimination methods like anti-malware tools and some system features that help with AV detection applications. Choose professional software like SpyHunter 5Combo Cleaner or Malwarebytes and run a full system check.
Follow indications and scan results and go for the proper ProLock ransomware removal method when the AV tool detects malware, intruders, and potential threats. Of course, this is not going to recover your encrypted files or repair damage in the system folders, so you should manage that yourself or with the help of a system repair tool Reimage Reimage Cleaner Intego. Also, check the methods below with decryption and data recovery alternatives.
Remove ProLock using Safe Mode with Networking
To get rid of the virus completely, you can reboot the machine in Safe Mode with Networking and then run the AV tool
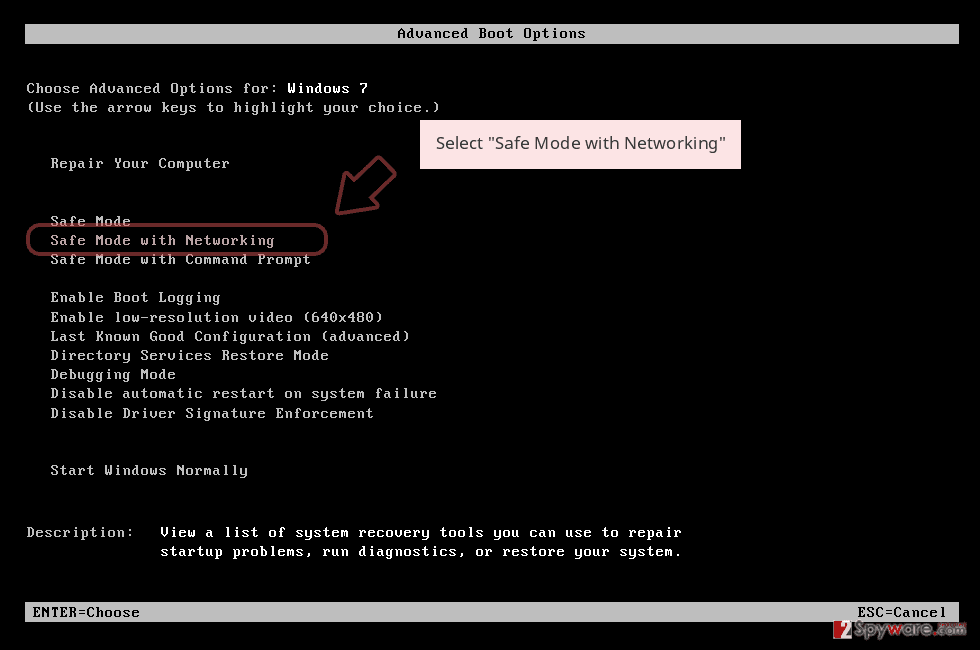
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
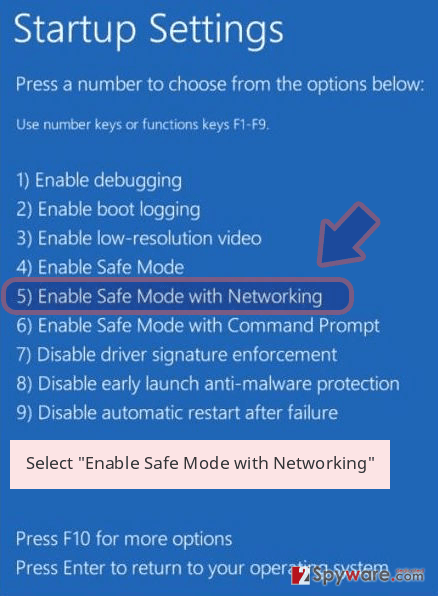
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner Intego or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete ProLock removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove ProLock using System Restore
Remove ProLock ransomware virus by recovering the machine in the previous state with the help of System Restore
Bonus: Recover your data
Guide which is presented above is supposed to help you remove ProLock from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If your files are encrypted by ProLock, you can use several methods to restore them:
Data Recovery Pro – a program that restores encrypted and otherwise affected data
File damaged by ProLock ransomware virus or another threat or accidentally deleted data can be restored with the help of Data Recovery Pro
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by ProLock ransomware;
- Restore them.
Windows Previous Versions gives the opportunity to recover your data
When System Restore feature gets enabled it provides another data backup alternative – Windows Previous Versions
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer for encoded files
If you know that ProLock ransomware virus has not affected Shadow Volume Copies, you can rely on ShadowExplorer that can restore your data
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Decryption tool is not available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from ProLock and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner Intego, SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2020-03-18 at 07:39 and is filed under Ransomware, Viruses.

