[email protected] ransomware is a type of malware that blackmails victims to pay ransom by locking their files

[email protected] ransomware is a file locking virus that belongs to a well-established Scarab family, which operates as RaaS (Ransomware-as-a-service).[1] This version of the malware was first spotted in July 2018, although it is now resurfacing again, with multiple victims reporting getting infected.
Once inside the system, [email protected] ransomware strips Windows computers from their defenses and then initiates the data encryption process. After that, all pictures, documents, databases, and other files can no longer be accessed, and are marked with [email protected] appendix. As soon as data is locked, victims can access HOW TO RECOVER ENCRYPTED FILES.txt file, which is essentially a note from the attackers. Inside, the attackers claim that an email to [email protected] address should be sent in order to negotiate a price for a decryptor.
The note also mentions that if the requirements are not fulfilled within two days, the secret key that can unlock files will be deleted permanently. It is important to note that [email protected] ransomware removal will not retrieve access to data, although there are a few other methods that might help you in some cases.
| Name | [email protected] |
|---|---|
| Type | Ransomware |
| Ransomware family | Scarab |
| encryption method | All non-system and non-executable files are encrypted with the help of RSA |
| extension | Files are appended with [email protected] appending. Example of the encrypted file: [email protected] |
| distribution | Threat actors employ a variety of delivery methods, including spam emails, malicious ads, software cracks, etc. |
| symptoms | Files marked with a specific extension are no longer accessible and encrypted with a strong algorithm |
| File Decryption | Unfortunately, this variant of Scarab is using improved encryption method to lock data with RSA, so it can no longer be decrypted for free without backups. Alternative ways how to get back compromised data are indicated at the end of this article |
| elimination | To get rid of malware, perform a full system scan with a powerful anti-malware tool |
| System fix | In case your Windows does not perform as well as prior to malware infection (lags, crashes, returns errors), fix virus damage with Reimage Reimage Cleaner Intego repair software |
Since the [email protected] virus utilizes a Ransomware-as-a-Service scheme, it can be delivered in several different methods. In essence, it makes the infection rate much higher, which also increases the chances of victims paying the ransom. Some of the delivery techniques include:
- Spam emails with boobytrapped attachments (documents, archives, PDF files);
- Malicious ads that are placed on less secure of hacked websites;
- Weakly protected Remote Desktop (RDP) connections that are using a default port;
- Botnets – malicious spam is sent by using infected hosts (Necurs is known to spread Scarab ransomware variants);
- Software cracks and pirated program installers, etc.
After the infiltration, [email protected] ransomware leaves the ransom-demanding message and indicates the following information:
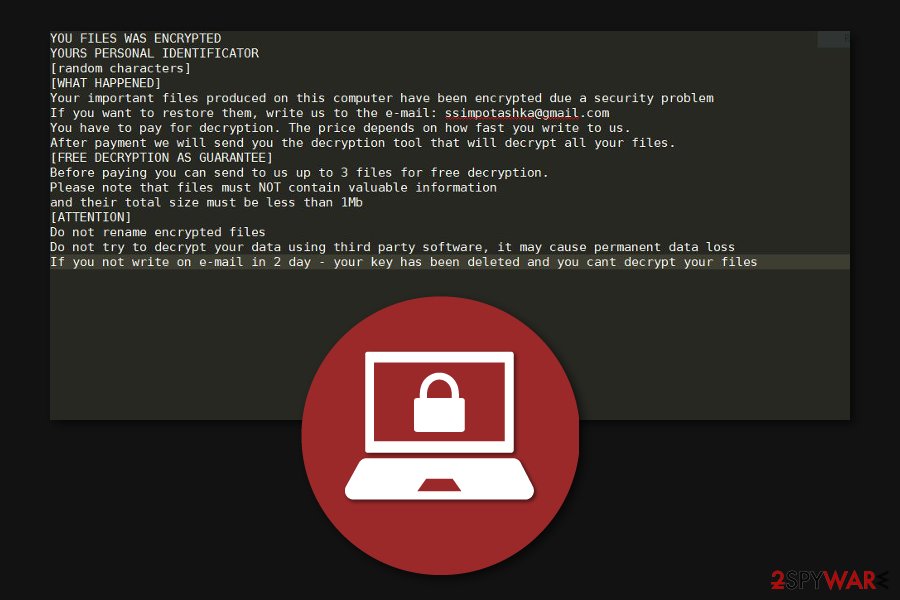
YOU FILES WAS ENCRYPTED
[WHAT HAPPENED]
Your important files produced on this computer have been encrypted due a security problem
If you want to restore them, write us to the e-mail: [email protected]
You have to pay for decryption. The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.[FREE DECRYPTION AS GUARANTEE]
Before paying you can send to us up to 3 files for free decryption.
Please note that files must NOT contain valuable information
and their total size must be less than 1Mb[ATTENTION]
Do not rename encrypted files
Do not try to decrypt your data using third party software, it may cause permanent data loss
If you not write on e-mail in 2 day – your key has been deleted and you cant decrypt your files
Cybercriminals claim that they have [email protected] virus decryptor and offer free decryption of 3 regular files. Additionally, they ask to contact them as soon as possible since the price of data recovery depends on it. However, our experts note that attackers are unreliable people and one should never agree to their terms[2].
There are multiple other ways how you can decrypt files with [email protected] extension without financially motivating the hackers. Furthermore, if you have backups stored in the cloud, you can quickly restore locked files to the primary state and avoid financial losses.
[email protected] ransomware is a new variant of Scarab virus family.

Ssimpotashka@gmail.com ransomware is a new variant of Scarab virus family.
Thus, we strongly advise you to remove [email protected] ransomware before it has damaged your system even more. Unfortunately, simple elimination procedure won’t eliminate this cyber threat as it would reappear after the startup and start data encryption once again.
You can perform safe [email protected] ransomware removal by employing a reliable security tool. Such antivirus applications are designed to get rid of all virus-related components from the computer and ensure its security in the future. Later, make sure to check alternative data recovery methods below and also fix virus damage with the help of Reimage Reimage Cleaner Intego.
Spam emails and malicious ads are the primary ransomware distribution sources
The answer to the question of how I got infected with ransomware is very simple. Most file-encrypting viruses spread utilizing the same technique for quite some time now — malicious email attachments. This distribution method is based on the recklessness of novice PC users as they tend to open spam emails that include malicious files.
Criminals create emails that mimic legal documents, invoices, or shopping receipts from well-known brands and companies. Typically, attachments that execute malware are macro-embedded documents, such as .doc, or .xls, although other file types, such as .zip, .pdf, .html, can also be used.
Likewise, you should carefully monitor your activity online and avoid opening any emails from unreliable and suspicious sources. Also, stay away from ads on insecure websites, such as porn, torrent, and similar. If clicked, they might enable malicious scripts and start an automatic download of the crypto-malware[3].
Get rid of [email protected] ransomware and proceed to data recovery
We understand that you want to recover files with [email protected] extension as quickly as possible. Although, experts[4] note that it is only possible when you uninstall the file-encrypting virus from your system completely. Since this task might be complicated, we suggest using a professional malware removal software.
You should start [email protected] ransomware removal by installing an antivirus. Our top choices are SpyHunter 5Combo Cleaner and Malwarebytes. They are effective, and easy-to-use to you will be able to proceed with data recovery steps and unlock your files quickly.
Although, if you can’t remove [email protected] ransomware since the virus prevents you from installing the security tool, you should check the instructions below. They are designed to guide you through the whole elimination and file recovery procedure.
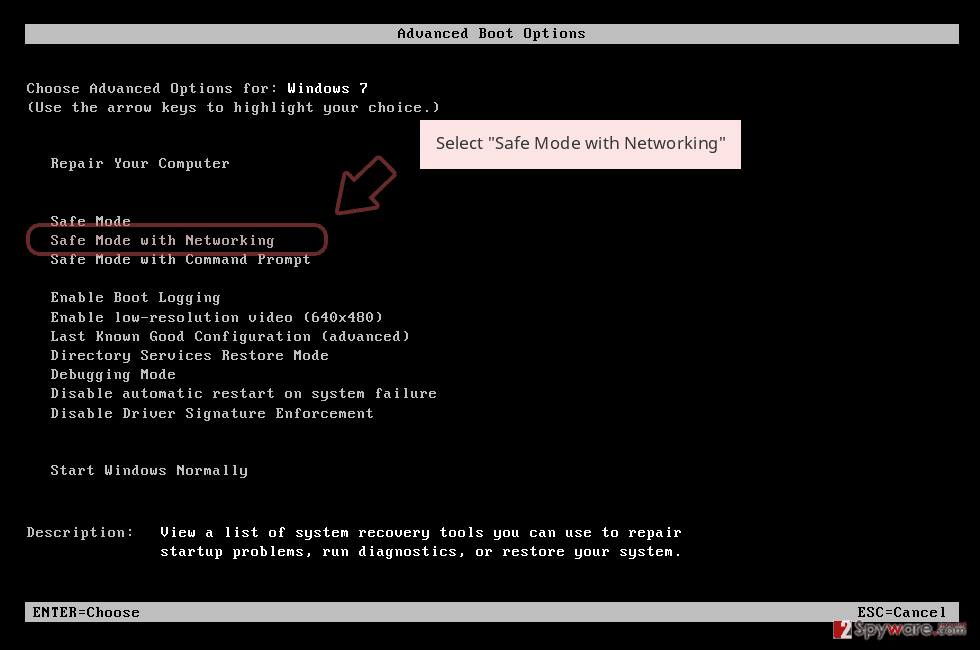
Remove [email protected] using Safe Mode with Networking
Boot your computer into Safe Mode with Networking to disable the infection:
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
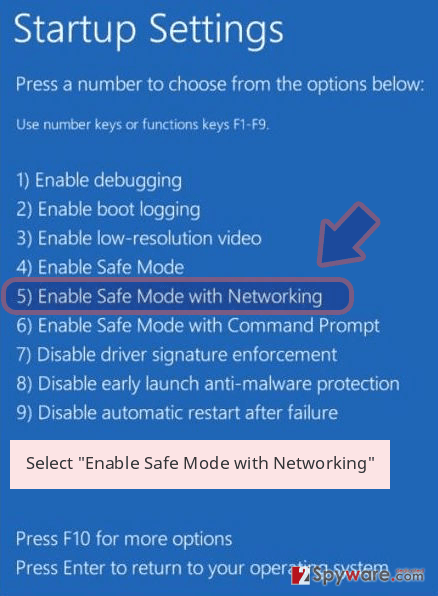
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner Intego or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete [email protected] removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove [email protected] using System Restore
Bonus: Recover your data
Guide which is presented above is supposed to help you remove [email protected] from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If your files are encrypted by [email protected], you can use several methods to restore them:
Data Recovery Pro could help [email protected] ransomware victims
If you have files encrypted by the ransomware, try recovering them with this professional software. Additionally, it might help you get back the access to data which has been accidentally deleted or compromised in other ways.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by [email protected] ransomware;
- Restore them.
Windows Previous Versions Feature option
Fortunately, Windows users can take advantage of an inbuilt feature which allows to travel back in time and restore files from their previous versions.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Try ShadowExplorer software
This application is designed to use Shadow Volume Copies on the system to recover encrypted data. Make sure that they are in place and follow the instructions below:
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
[email protected] ransomware decryptor is not available.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from [email protected] and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner Intego, SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2020-04-24 at 02:49 and is filed under Ransomware, Viruses.

