Scarab ransomware – a dangerous crypto-malware that is using sophisticated AES-256 and RSA-2048 algorithms to encrypt victims’ files

Scarab is ransomware-type infection which is designed to corrupt the data and make it unreadable for blackmail purposes.

Scarab is ransomware-type infection which is designed to corrupt the data and make it unreadable for blackmail purposes.
Scarab is ransomware that employs sophisticated AES-256 and RSA-2048 algorithms to lock personal data on the targeted computer. As soon as it locks files, it marks them with a specific extension, such as .scarab, .langolier, and, later on, email-based appendixes like [email protected] or [email protected]. However, you can also become a victim of Scarab-Recovery, Scarab-Turkish, Scarab-Barracuda, [email protected], and numerous other versions.
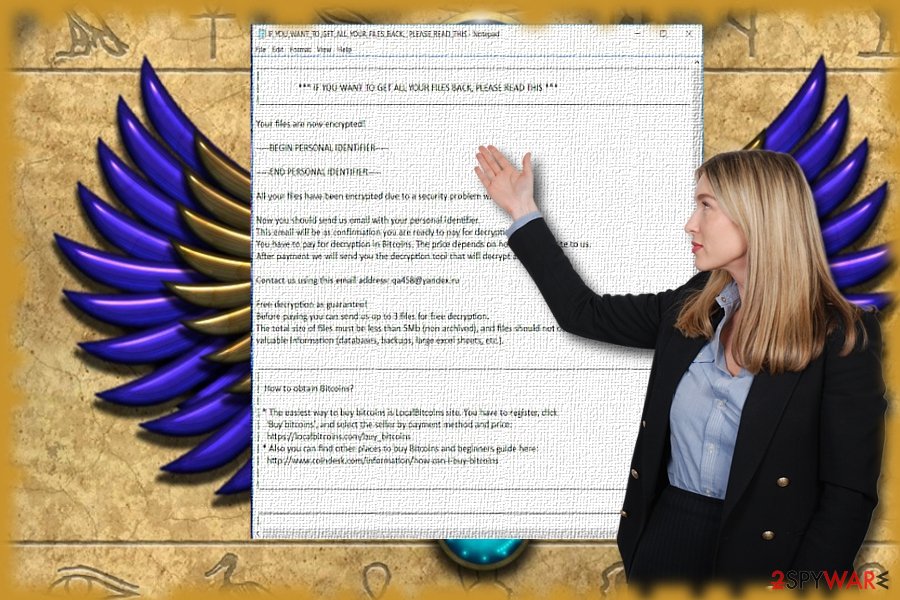
After the data locking process, the Scarab virus drops a ransom note demanding from $300 to $500 in exchange for the key that can unlock encrypted data. The name of dropped ransom notes also varies depending on the version – HOW TO RECOVER ENCRYPTED FILES.TXT, IF YOU WANT TO GET ALL YOUR FILES BACK, PLEASE READ THIS.TXT, and a few others, were used.
Scarab ransomware was spotted for the first time in June 2017 and had been reappearing with new versions since then. According to the latest research, it could be hailing from Animus ransomware developers, as it has been using the same email address for quite some time now. Sadly, only versions released prior to June 2018 can be decrypted, as new Scarab ransomware variants use an improved RSA encryption method.
| SUMMARY | |
|---|---|
| Name | Scarab |
| Type | Ransomware |
| might be related to | Animu Locker |
| Versions | Scorpio, Scarab-Amnesia, Scarab-Crypto, Scarab-Please, Scarab-Decrypts, Scarab-Horsia, Scarab-Walker, Scarab-Osk, DiskDoktor, [email protected] ransomware, Scarab-Leen ransomware, Scarab-Bomber, Scarab-Good, Oneway, Danger, BtcKING, Recme, JungleSec, Dan ransomware, Deep ransomware, Scarab-Recovery, Scarab-Turkish, Scarab-Barracuda, Scarab-Anonimus, Scarab-zzzzzzzz |
| Danger level | High. At the moment, the virus is especially active and keeps appearing with new versions |
| Cryptography | AES-256; RSA-2048 |
| File extensions | .scarab, [email].scarab, [email].scorpio, [[email protected]].scarab, .amnesia, .crypto, .please, [email protected], .red, .DD, .decryptsairmail.cc, [email protected], .JohnnieWalker, .osk, [email protected], .DiskDoctor, [email protected], .leen, .bomber, .recme, .oneway, .good., .deep, .BD.Recovery, .enter, .fast, .key, .[[email protected]], .BARRACUDA, [email protected], .zzzzzzzz, .{[email protected]}.exe, [email protected], [email protected] |
| Related files |
IF_YOU_WANT_TO_GET_ALL_YOUR_FILES_BACK_ PLEASE_READ_THIS.txt; HOW TO RECOVER ENCRYPTED FILES.TXT; TO RECOVER ENCRYPTED [email protected]; HOW TO DECRYPT WALKER INFO.txt; HOW TO RECOVER ENCRYPTED [email protected]; HOW TO RECOVER ENCRYPTED [email protected]; Recover [email protected]; INSTRUCTIONS FOR RESTORING FILES.TXT, HOW TO RECOVER – [email protected] ENCRYPTED FILES.TXT. |
| Language translated | English, Russian, Turkish |
| Distribution | Necurs botnet, malicious email attachments, fake Java or Adobe Flash Player updates, corrupted remote desktop apps |
| Decryption | Dr. Web announced that some of the files encrypted by Scarab can be decrypted. Users should send an email to [email protected] with few examples of affected data together with the ransom note |
| ElIMINATION | Manual removal is not possible. To get rid of ransomware and its variants, download a reputable anti-malware, such as SpyHunter 5Combo Cleaner or Malwarebytes, and run a full system scan |
| System fix | Ransomware is a complex computer infection, and it can negatively impact its performance even after it is eliminated. As a result, users might experience crashes, lags, and other stability issues. To remediate Windows and avoid its reinstallation, run a scan with repair software Reimage Reimage Cleaner Intego |
This ransomware[1] is not an ordinary crypto-virus – it was found to use Necurs botnet[2] to spread around. Having in mind that it is the largest spam botnet, the possibility to get infected with Scarab increases greatly. Luckily, the notorious botnet was majorly disrupted in March 2020, reducing malware infections worldwide. In addition, some variants are spread via fake Flash Player and use exploit kits to get into the affected machines all over the world.
Right after the infiltration, the virus encrypts video, music, picture, document and similar personal data by using symmetric and asymmetric encryption algorithms. You can find files encrypted by ransomware by looking at the appendix of your files. If they have .scarab file extension, .scorpio, .zzzzzzzz, and similar suffixes, they are encrypted and you won’t be capable of using them.
Scarab virus uses AES-256 cryptography for data encryption.

Scarab virus uses AES-256 cryptography for data encryption.
Virus functionality to gain income
Originally, the ransom note of Scarab virus is using the Russian language, but its latest versions are using the note translated into English. Typically, it reads:
*** IF YOU WANT TO GET ALL YOUR FILES BACK, PLEASE READ THIS ***
Your files are now encrypted!—– BEGING PERSONAL IDENTIFIER ————-
—– END PERSONAL IDENTIFIER ——————
All your files have been encrypted due to a security problem with your PC.
Now you should send us email with your personal identifier.
This email will be as confirmation you are ready to pay for decryption key.
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.Contact us using this email address: [email address]
Free decryption as guarantee!
Before paying you can send us up to 3 files for free decryption.
The total size of files must be less than 10Mb (non archived), and files should not contain
valuable information (databases, backups, large excel sheets, etc.).[……]
To gain users’ trust, the developers are offering free decryption of three files up to 1 MB in size. However, felons do not indicate the sum of the ransom but rather urge affected users to contact them as soon as possible since the deadline for the ransom payment ends after 72 hours.
Following these orders is not recommended. Cybercriminals cannot be trusted in any way, so after paying the ransom you may be left without both money and files. Security experts recommend victims to remove Scarab ransomware instead using a professional anti-malware tool, like Reimage Reimage Cleaner Intego or Malwarebytes.
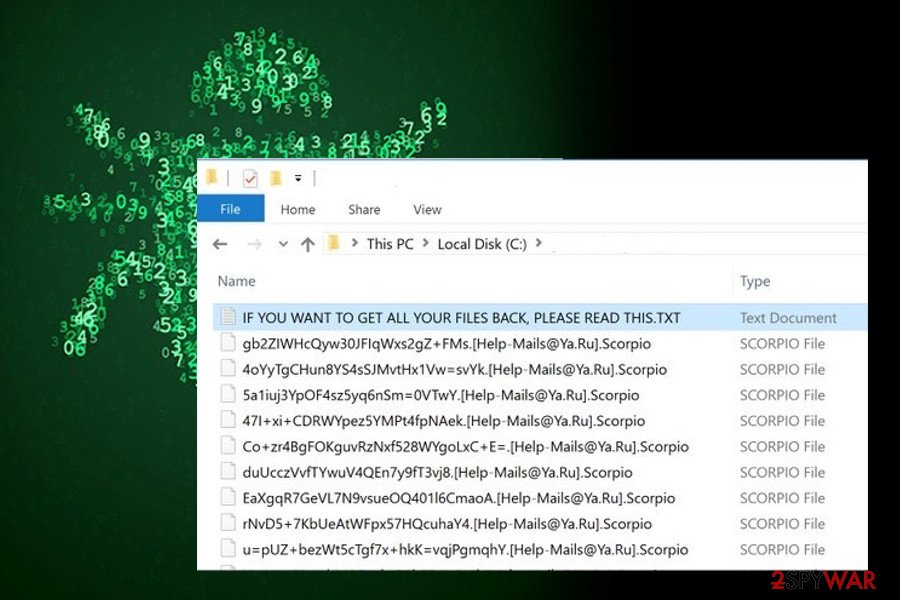
.scorpio file extension virus is an upgraded version of Scarab ransomware.

.scorpio file extension virus is an upgraded version of Scarab ransomware.
Once you complete the Scarab removal, you will be able to recover the biggest or even all of encrypted files using third-party data recovery tools. You can find a comprehensive decryption tutorial at the end of this article. Alternatively, you can email few encrypted files to Dr.Web ([email protected]) and see if security experts can decrypt files for you.
The ransom note of the virus is typically instructing the victim to provide the personal identifier and contact the felons via provided email address. Updated variants of Scarab virus have been using different email addresses for communication with victims. Some of the used emails are:
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
Note that Scarab ransomware decryptor has not been yet created, so it is quite difficult to retrieve files back. However, in April 2018, Doctor Web announced[3] that some cases of ransomware can be decrypted. For that, victims should send the ransom note HOW TO RECOVER ENCRYPTED FILES – [email protected] and 3-4 encrypted files to the email [email protected]. If infected with any of these versions, try this method for files’ decryption. If it does not work for you, jump to the end of this post to use other methods for data recovery. However, make sure you remove Scarab ransomware before this procedure.
Cybercriminals continue to upgrade Scarab virus and infect computers worldwide.

Cybercriminals continue to upgrade Scarab virus and infect computers worldwide.
The list of Scarab versions
Scarab ransomware has been appearing with new versions since last year. Recently, it came to researchers’ attention as the malware that receives updates pretty much each month. At the moment, there are twenty different members of this money extortionist family that are listed below.
Scorpio ransomware
Scorpio ransomware is believed to be the first new update to the original variant of Scarab ransomware. The most noticeable features of this virus are its ability to crack the computer in multiple different stages.
Firstly, it settles on the computer with the help of bogus scripts executed via Command Prompt Admin. The next phase encompasses data encryption. Scorpio ransomware scans the system for targeted files, applies AES cipher to lock them, and eventually appends .[[email protected]].scorpio file extension to distinguish them from the others. The final phase is informative. Scorpio virus generates a ransom note named IF YOU WANT TO GET ALL YOUR FILES BACK, PLEASE READ THIS.txt. The file contains a unique victim’s ID, and contact information, including email address ([email protected] and [email protected]).
Scarab-Crypto ransomware
Scarab-Crypto is the name of the next Scarab ransomware version detected in the second half of March 2018. Just like its ancestors, it uses AES cryptography and targets the most popular file types. Its distinctive feature is a .crypto file extension and HOW TO RECOVER ENCRYPTED FILES.TXT file. It instructs the victim to email Scarab-Crypto ransomware developers via [email protected] and indicate a personal identification number.
Extortionists should subsequently unlock two files encrypted by Scarab-Crypto for free to claim their trustworthiness. The sum of the payment is not revealed in the note, but the victim is demanded to initiate a transaction via Bitcoin wallet asap to get a decryptor.
Cybercriminals developed a new version, called Scarab-Cryptor.

Cybercriminals developed a new version, called Scarab-Cryptor.
Scarab-Amnesia
Spotted at the end of March 2018, this new version spreads via Necurs botnet and executed its payload when the potential victim extracts a 7Zip email attachment. Likewise other Scarab versions, it uses AEX-256 encryption algorithm. However, it can easily be distinguished from the rest of Scarab versions by an .amnesia file extension added to locked files. The list of targeted files:
.Png, .psd, .pspimage, .tga, .thm, .tif, .tiff, .yuv, .ai, .eps, .ps, .svg, .indd, .pct, .pdf, .xlr, .xls, .xlsx, .accdb, .db, .dbf, .mdb, .pdb, .sql, .apk, .app, .bat, .cgi, .com, .exe, .gadget, .jar, .pif, .wsf, .dem, .gam, .nes, .rom, .sav, .dwg, .dxf, .gpx, .kml, .kmz, .asp, .aspx, .cer, .cfm, .csr, .css, .htm, .html, .js, .jsp, .php, .rss, .xhtml, .doc, .docx, .log, .msg, .odt, .pages, .rtf, .tex, .txt, .wpd, .wps, .csv, .dat, .ged, .key, .keychain, .pps, .ppt, .pptx, .ini, .prf, .hqx, .mim, .uue, .7z, .cbr, .deb, .gz, .pkg, .rar, .rpm, .sitx, .tar.gz, .zip, .zipx, .bin, .cue, .dmg, .iso, .mdf, .toast, .vcd, .sdf, .tar, .tax2014, .tax2015, .vcf, .xml, .aif, .iff, .m3u, .m4a, .mid, .mp3, .mpa, .wav, .wma, .3g2, .3gp, .asf, .avi, .flv, .m4v, .mov, .mp4, .mpg, .rm, .srt, .swf, .vob, .wmv, .3d, .3dm, .3ds, .max, .obj, .r.bmp, .dds, .gif, .jpg, .crx, .plugin, .fnt, .fon, .otf, .ttf, .cab, .cpl, .cur, .deskthemepack, .dll, .dmp, .drv, .icns, .ico, .lnk, .sys, .cfg.
Scarab-Amnesia ransomware informs its victims about the current situation and the steps he or she has to take to decrypt files on a HOW TO RECOVER ENCRYPTED FILES.TXT file. Typically, it is stored on the desktop, but can also be found on random folders that contain files with .amnesia file extensions.
Scarab-Please ransomware
At the end of March 2018, security experts discovered Please ransomware that is using AES encryption to modify targeted files. It is appending .please file extension to target data and dropping a ransom note “HOW TO RECOVER ENCRYPTED FILES.TXT” on a desktop. This message informs the victim to use an email called [email protected] or [email protected] to contact its developers and get further instructions needed for the recovery of affected files. Cybercriminals are also claiming that the victim can test the decryption procedure to ensure that it is possible. However, we do not recommend contacting hackers. Ransomware also can make changes to Windows registry key so this is better be deleted soon.
Scarab-Decrypts ransomware
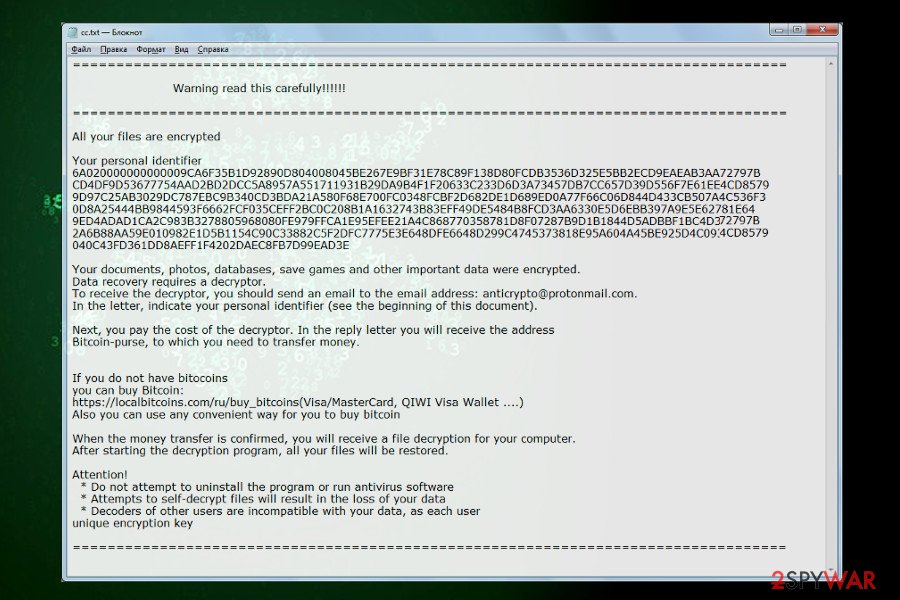
It is yet another version of ransomware. It’s more or less similar to its ancestors, though exhibits different file extensions and the ransom note. Written on Delphi, it takes advantage of AES-256 cipher to attack victim’s files and render them useless by altering their file extension.
Following the encryption phase, each locked file gets either .decrypts @ airmail.cc or .decryptsairmail.cc file extension. Consequently, the owner cannot dispose of them in any way. The Scarab-Decrypts ransomware provides its victims with a ransom note called HOW TO RECOVER ENCRYPTED [email protected]. It does not say much, except that the files have been encrypted and provides an email address which asks the victim to contact to [email protected] and provide a unique identification number for further instructions. You can see an example of the Scarab-Decrypts ransom note below.
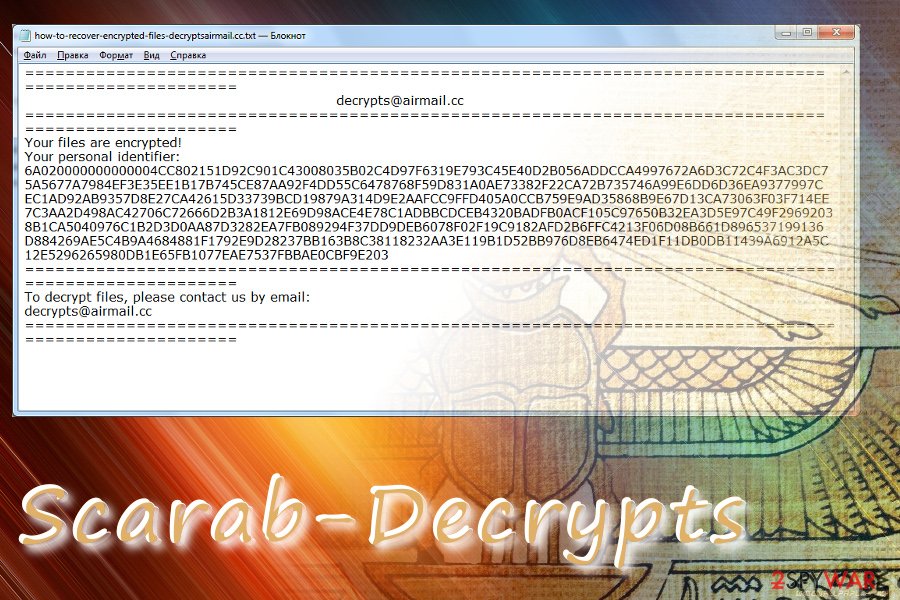
Scarab-Decrypts is a different version of the original virus.

Scarab-Decrypts is a different version of the original virus.
Scarab-Horsia
Horsia ransomware version was spotted at the beginning of May 2018. Disguised under 7Zip and otherwise named email attachments, the ransomware targets English-speaking PC users. Once it’s installed, malicious processes start running in the background to protect the Horsia ransomware from removal.
Encrypted files are easy to notice as they get [email protected] file extension, which cannot be modified manually. Besides, each folder, including the desktop, contains a HOW TO RECOVER ENCRYPTED FILES.TXT file explaining the current situation, including payment and contact information. The full ransom note reads as follows:
Scarab-Walker
This version of the dangerous cyberthreat and was spotted by security experts shortly after Horsia variant came out. Just as all previous versions, Walker ransomware users AES cryptography to encrypt files. It changes all media, video, text and other personal files and makes them unusable by adding .JohnnieWalker extension.
As usual, after data encryption, Scarab-Walker virus drops a ransom note in the .txt format, explaining the situation to the user. Hackers demand payment in Bitcoins. Soon after the ransom is paid, users are prompted to e-mail [email protected] and include their personal ID. Additionally, cybercrooks offer to unlock one file to prove that data is decryptable.

Scarab-Walker is another variant of the virus which has started spreading in the middle of 2018.

Scarab-Walker is another variant of the virus which has started spreading in the middle of 2018.
[email protected]
Additionally, the malware reappeared in June 2018 with the [email protected] file extension to mark each of the affected files. The virus drops a ransom note HOW TO RECOVER ENCRYPTED [email protected] into each folder which explains about files’ encryption using RSA-2048 cipher. The only way to recover locks files is said to be a special decryprion key that is stored by criminals on a remote server.
Scarab-Osk
Scarab-Osk is encrypting data by using AES cipher. It is using .osk extension to mark every affected file. Hackers ask for 0.013 Bitcoin in HOW TO RECOVER ENCRYPTED FILES.txt message to be paid and then email sent to [email protected] for further instructions and the decryptor. As usual, we advise refraining yourself from contacting cybercrooks and restore all encoded data using a backup.
Scarab-DiskDoctor ransomware
DiskDoctor ransomware is still encrypting files with the same AES-256 encryption algorithm. Differently from previous variants, this one appends .DiskDoctor file extension to the targeted files. But it still displays data recovery instructions in the text file called “HOW_TO_RECOVER_ENCRYPTED_FILES.txt.”
In the ransom note, crooks demand to contact them via [email protected] email address in order to learn about data recovery possibilities. However, we do not recommend trying to get back your files in this way. Crooks will demand to transfer a few hundreds of dollars in Bitcoins in order to get a decryption tool. However, once you make a transaction, they might disappear and never give you a needed tool. Hence, you should remove DiskDoctor from the computer ASAP.
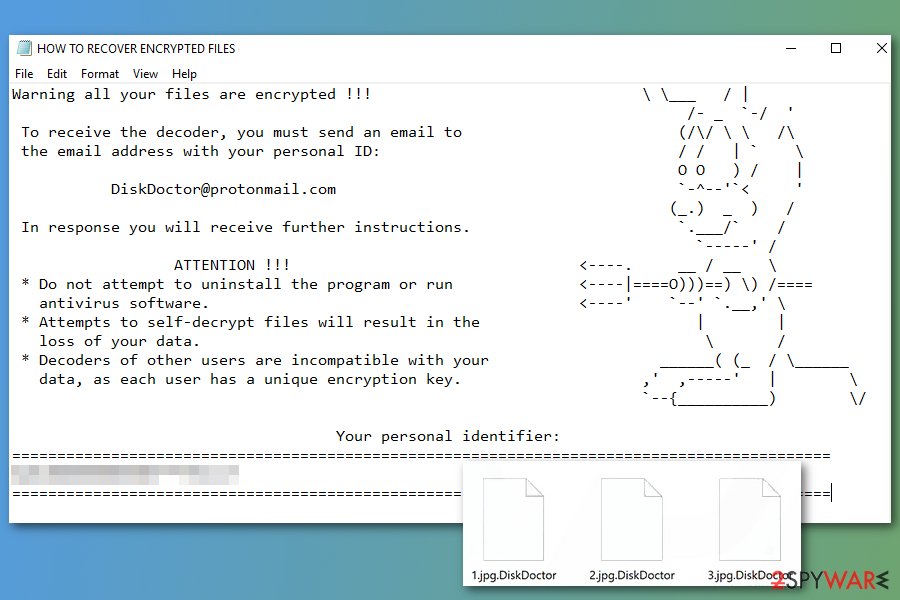
Scarab-DiskDoctor is a file-encrypting virus which compromises the data by appending .DiskDoctor extension.

Scarab-DiskDoctor is a file-encrypting virus which compromises the data by appending .DiskDoctor extension.
Scarab-Good ransomware
In June 2018, researchers detected a few version of Scarab and this one is decryptable with Dr. Web. “.good” is a file extension that virus adds to modified files and “[email protected]” is the contact email address. As typical for the Scarab family ransom note is placed in file “HOW_TO_RECOVER_ENCRYPTED_FILES.txt.”. This contains information about encryption and what to do but no specifics about the ransom or decryption. This virus version came to the light alongside other ones.
Leen ransomware
Just like its name suggests, Leen ransomware is using “.leen” to each of the files that become modified. As soon as that is complete, a ransom note is placed in every folder. “INSTRUCTIONS FOR RESTORING FILES.TXT.” contains information about this certain attack:
Contact us using this email address: [email protected]
Free decryption as guarantee!
Before paying you can send us up to 3 files for free decryption.
The total size of files must be less than 10Mb (non archived), and files should not contain
valuable information (databases, backups, large excel sheets, etc.).
Cybercriminals demand unspecified payment in Bitcoins and suggest victims contact them via email “[email protected].” in order to get a key or more information.
Danger ransomware
Danger ransomware is decryptable with Dr. Web, but it is different from the most of the members in the family because this version uses RSA-2048 encryption algorithm. “[email protected]” is a file extension that this virus adds after the modification is complete. Typical “HOW_TO_RECOVER_ENCRYPTED_FILES.txt.” ransom message placed on pretty much every folder on the PC. Information about changing contacts and encryption method is the main useful things in the note. No specific ransom amount just email address “[email protected]” that changes after three days.
Oneway ransomware
Difficult weeks in the cyber-security world while Scarab develops new variants each week. This version is targeting Russian-speakers because while this adds “.oneway” file extension the ransom note called “Расшифровать файлы oneway.TXT.” Email address “[email protected]” is provided in the message and the note contains more information about test decryption and the attack itself.
Scarab- BtcKING ransomware
BtcKING ransomware came with more similar patterns. Encryption is done in a similar way and “.BtcKING” file extension looks like other previous versions. Also, this variant places ransom message called ” How To Decode Files.txt” on every existing folder on the system and desktop. This ransomware also came in June 2018 alonside other dangerous versions.
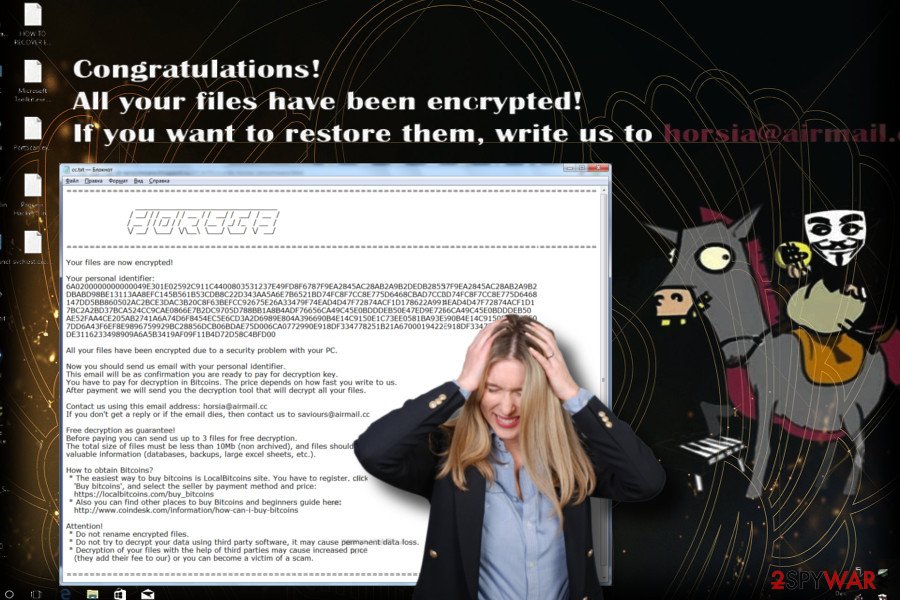
Scarab-Horsia virus “congratulates” its victims with the infection.

Scarab-Horsia virus “congratulates” its victims with the infection.
Bomber ransomware
Another ransomware targeting Russian victims. This ransomware appends photo, video, text and other files with “.bomber” file extension so it is easily detected which ones are modified. After this encryption process is completed virus creates a ransom note “HOW recover encrypted FAYLY.TXT” and you can have more details about the attack. This is placed on your desktop and in every folder where you can find modified files. This version displays [email protected]; [email protected]; [email protected] as possible contact emails.
JungleSec ransomware
JungleSec version of Scarab has more specific details. Encryption is done while appending “.jungle@anonymousspechcom” extension to modified files. And after that ransom note, “ENCRYPTED.md” is placed in multiple places on the system. In this file, you can discover that virus developers demand certain 0.3 in Bitcoin and state their contact email as “[email protected]” which you are suggested to contact after the payment is done. This version has no decryption option.
Recme ransomware
Recme ransomware is one of the newest variants discovered in late June of 2018, with classical Scarab encryption patterns. After the encryption process, during which “.recme” file extension is placed on your photos, videos, text or archive files, this ransomware creates ransom message called “HOW_TO_RECOVER_ENCRYPTED_FILES.txt.”. In this message, you can find more details about the cyber attack.
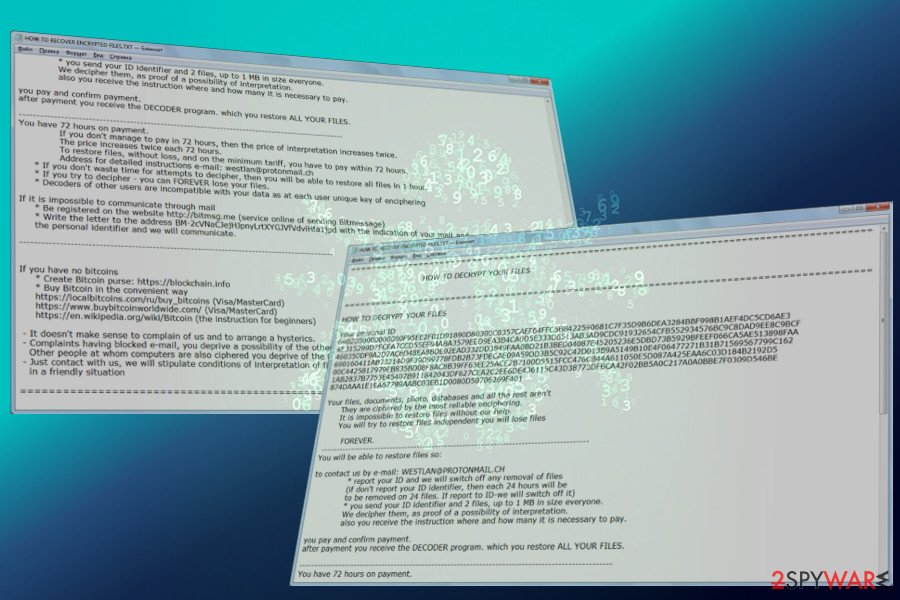
Scarab-Amensia is a crypto-malware which has emerged from the initial Scarab ransomware.

Scarab-Amensia is a crypto-malware which has emerged from the initial Scarab ransomware.
Scarab-Dan ransomware
This version of Scarab ransomware came alongside the previous five is the one that adds “[email protected]” file extension to targeted files. These can be anything from images, photos or videos to text files or even archives. After this modification is complete you can find ransom note file “HOW TO RECOVER ENCRYPTED [email protected]”. This is a ransom message that often contains various information about the initial attack and instructions for the victim.
Scarab-Recovery ransomware
Scarab-Recovery came out in early July 2018. The virus is written in Delphi programming language and uses AES to lock up data. The crypto-virus adds .BD.Recovery extension to each of the affected file and drops ransom note “HOW TO RECOVER FILES.TXT” which states that victims should email crooks via [email protected] or [email protected]. However, hackers should never be contacted as it can result in a loss of money.
Scarab-Turkish ransomware
As the name suggests, this version of Scarab focuses on Turkish PC users. However, all the Turkish characters were replaced by English letters, making it impossible to understand. The virus uses AES to encrypt data and ads [[email protected]] appendix to each of the affected files, which is also a contact email of cybercriminals. As usual, we suggest you ignore cybercrooks and remove Scarab-Turkish from your machine ASAP.
Scarab-Barracuda ransomware
The latest variant of crypto-virus is dubbed Scarab-Barracuda because it encrypts files and adds .BARRACUDA file extension. The virus is closely related to Scarab-Rebus and can be decrypted. Therefore, do not waste your money and do not pay cybercrooks. Merely contact security experts who can help to decode data. Unlike many other versions, Barracuda ransomware drops a ransom note which includes its name in it – BARRACUDA RECOVERY INFORMATION.TXT. Cybercriminals are trying their best to scare users with the following:
Attention!
Do not attempt to remove a program or run the anti-virus tools
Attempts to decrypt the files will lead to loss of Your data
Decoders other users is incompatible with Your data, as each user unique encryption key
Scarab-zzzzzzzz ransomware
In 2019, the owners of Scarab ransomware returned with a new file extension used to block victims’ files and convince them to pay the ransom. At the moment, the virus is appending .zzzzzzzz file extension after using an encryption algorithm to scramble the code of separate files. Keys which are required to unlock encrypted files and saved in external servers which can be reached only by cybercriminals. According to the ransom note, victims have 5 days to unlock files by paying a ransom. The payment should be made either in Bitcoin or Dash cryptocurrency. Zzzzzzzz ransomware is not decryptable yet, just like numerous other versions of Scarab. If infected, use third-party tools to unlock your files.


[email protected] ransomware
[email protected] ransomware is one of the variants that resurfaced after its initial release in July 2018. Almost two years later, users started reporting infections of this Scarab version once again. Since the malware is using an improved RSA algorithm to lock files, it cannot be decrypted with previously-working methods, unless working backups are retained.
Soon after the infiltration, the [email protected] virus begins performing the necessary changes to make the machine ready for data encryption. Malware targets hundreds of file types, although it skips system and some executable files for the computer to be functional after the infection (the goal of ransomware is not to destroy Windows per se – hackers seek to retrieve money from ransom payments instead).
After the encryption, each of the affected files receives a marking [email protected], and can no longer be accessed. For data recovery, users need to email the attackers and then pay a ransom (typically in bitcoin cryptocurrency) to retrieve a decryption tool with a unique key. The information about the infection and further actions can be found in a ransom note HOW TO RECOVER ENCRYPTED FILES.txt file, which is dropped in several places on victims’ computers.
Hackers are taking advantage of the infamous Necurs botnet to distribute the virus
Necurs botnet is infamous for the distribution of different ransomware-type infections. In November, cybersecurity experts have also detected it spreading Scarab virus[4]. Criminals are aiming to affect computers located in[5]:
- Australia;
- Germany;
- United Kingdom;
- France.
At the moment of writing, the botnet already sent about 12.5 million emails with a malicious 7Zip archive with the Visual Basic script that downloads and executes the third version of the virus.
These subject line of these emails are made by this scheme: “Scanned from [printer/scanner company name].” Currently, the most popular versions of titles are:
- Scanned from Lexmark;
- Scanned from Canon;
- Scanned from HP;
- Scanned from Epson.
The infected archive itself is named image2017-11-23-4360760.7z. However, the name of this file might change based on the distribution data. Therefore, users are advised to be careful and watch out emails sent from copier@[your email address or company’s domain].
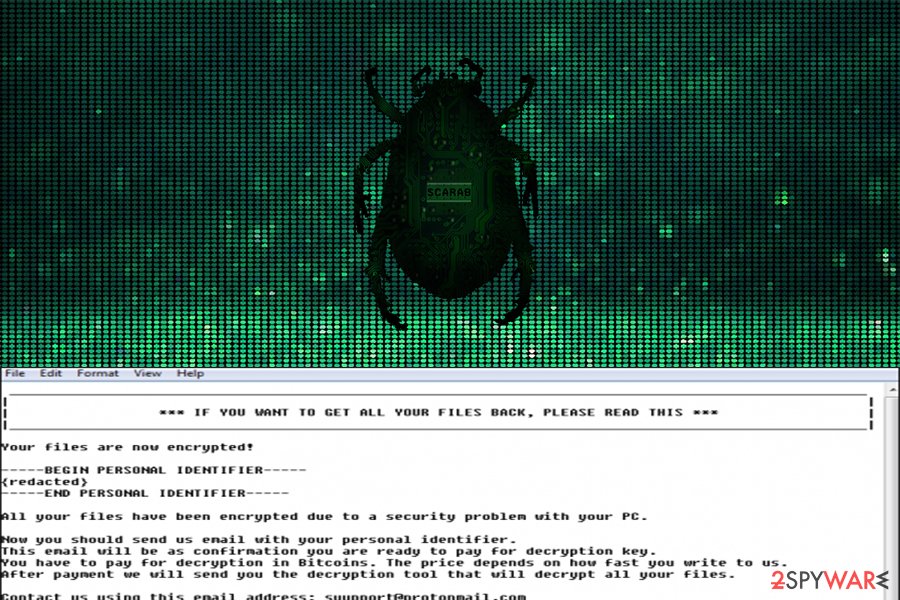
Different versions of Scarab malware delivers slightly changed ransom notes.

Different versions of Scarab malware delivers slightly changed ransom notes.
Spam emails is yet another method used to spread Scarab
The authors of this crypto-malware continue to distribute the virus in the old-school way which relies on malicious spam emails[6]. Cybersecurity experts have detected an enormous wave of malicious emails distributed with the help of Necurs botnet in the late 2017. The content of the letter included VBS scripts disguised as innocent scanned documents in 7Zip archive.
Therefore, users should be aware of potential dangers that might be sent straight to the inbox. Keep in mind that if you do not retain rational thinking and cautiousness, no anti-virus will be able to save you from Scarab hijack or another malware infiltration. In addition, note that some hackers still use old trickery: visiting a corrupted site, you may notice a fake alert prompting to update your Java or Adobe Flash Player.
The only way to get rid of Scarab ransomware is a reliable malware removal tool
Our security experts understand how threatening it might seem to lose encrypted data by trying to remove Scarab ransomware. Although, the only way to decrypt files without paying the ransom is to get rid of this cyber threat with a robust antivirus. We suggest using Reimage Reimage Cleaner Intego, SpyHunter 5Combo Cleaner. or Malwarebytes. Afterward, you will be able to try alternative data recovery methods presented below.
In case you cannot launch your security software, take a look at the bottom instructions. They should help you launch it and overcome this issue. However, note that cybersecurity application does not decode files and can help you only for Scarab ransomware removal.
This entry was posted on 2020-04-24 at 03:23 and is filed under Ransomware, Viruses.

