SepSys ransomware – a file locking virus that launches a ransom note soon after the encryption process is complete
SepSys ransomware is a file locking virus that demands $100 in BTC for data decryption tool

SepSys ransomware is a file locking virus that demands $100 in BTC for data decryption tool
SepSys ransomware is cryptomalware that was first identified by security researcher GrujaRS at the end of February 2020.[1] The malware attacks Windows machines exclusively and does not seem to have any connections to other file locking virus families, although the developers present themselves as “Silicon Venom.”
Soon after infiltration, the SepSys virus encrypts data with a symmetric[2] AES cipher, adding a .sepsys marker in the process. As a result, users are unable to access their files – although that is not the only symptom of the infection that is noticed right away. Right after the data encryption, README.html ransom note is dropped on the desktop, and also presented to victims. Allegedly, they need to “donate” $100 worth of Bitcoin to the provided Bitcoin wallet, and then email the attackers at [email protected] for the SepSys ransomware decryptor.
| Name | SepSys ransomware |
|---|---|
| Type | File locking virus, cryptomalware |
| Developer | Silicon Venom |
| Executable | destructy-1.0.exe, although it can also be named as anything else |
| Cipher used | All personal files are encrypted with the help of symmetric encryption algorithm AES |
| Ransom note | README.htm is dropped on the desktop and all the folders where locked files are located |
| Contact | After the payment, users are asked to email the attackers at [email protected] in order to retrieve decryption software |
| Ransom size | Malicious actors ask victims to pay $100 in Bitcoin |
| Bitcoin wallet | 3BL1TbL96gQFTR9EJFKX7JSp889oj2nJmj |
| File recovery | Without paying criminals, recovering data is very difficult, although there may be a chance of retrieving at least some files with the help of the methods listed below |
| Malware removal | It is imperative to get rid of the infection as soon as possible, as all the incoming files will be encrypted as well. To do that, employ anti-malware software like SpyHunter 5Combo Cleaner or Malwarebytes and perform a full system scan (in Safe Mode if required) |
| System fix | Malware can sometimes corrupt system files that may negatively impact Windows performance after its termination. To fix virus damage, use Reimage Reimage Cleaner |
SepSys virus developers most likely employ various distribution methods to infect as many users as possible – these may include spam emails, exploits, web injects, weakly protected RDP connections, software cracks, hacked sites, drive-by downloads, and others. To prevent malware from entering (as well as prompt SepSys ransomware removal), employ reputable security software that can recognize the threat.
According to Virus Total, over 30 different AV engines detect the main SepSys ransomware executable as malicious under the following names:[3]
- Trojan.GenericKD.42682853
- Trojan.Win32.Zudochka.ebg
- Ransom:Win32/SepSys!MTB
- Artemis!FD2E7CCA1605
- W32/Ransom.FVG!tr
- FileRepMetagen [Malware], etc.
The detection rate is predominately low (approximately 44% at the time of the writing), so there is a higher chance of users being infected. Unfortunately, there is no anti-virus that would protect you from all types of infections 100%, so precautionary measures should be practiced in order to avoid malware. As for now, you should remove SepSys ransomware and then fix the damaged Windows files with Reimage Reimage Cleaner to prevent computer instability.
SepSys ransomware is a type of malware that encrypts pictures, documents, videos and other data with AES

SepSys ransomware is a type of malware that encrypts pictures, documents, videos and other data with AES
Encryption and operation
Once the malicious file destructy-1.0.exe is launched, the infection routine begins, and a variety of files are dropped on the desktop, as well as user and temp folders. Besides that, SepSys ransomware prepares the machine for a smooth encryption process.
For example, the malware deletes Shadow Volume Copies, which are responsible for the automatic Windows backup system, to prevent users from recovering their files easily. Additionally, the SepSys virus also modifies Windows registry in order to be launched every time a Windows machine is booted. In the background, it likewise establishes a connection with a remote C&C server for communication.
Just as similar ransomware viruses, SepSys targets the most commonly used files, such as .pdf, .doc, .mp4, .zip, .txt, .dat, xml, etc. Nevertheless, it skips system and executable files mostly, as the goal of developers is not to corrupt your system completely, as it serves as a tool for communication.
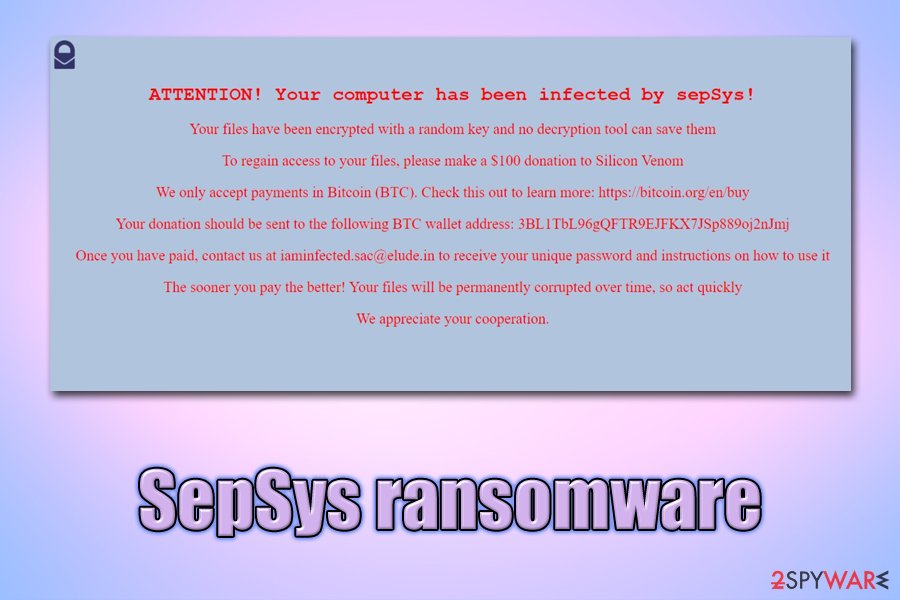
After encryption, SepSys ransomware drops the following ransom note titled README.html:
ATTENTION! Your computer has been infected by sepSys!
Your files have been encrypted with a random key and no decryption tool can save themTo regain access to your files, please make a $100 donation to Silicon Venom
We only accept payments in Bitcoin (BTC). Check this out to learn more: hxxps://bitcoin.org/en/buy
Your donation should be sent to the following BTC wallet address: 3BL1TbL96gQFTR9EJFKX7JSp889oj2nJmj
Once you have paid, contact us at [email protected] to receive your unique password and instructions on how to use it
The sooner you pay the better! Your files will be permanently corrupted over time, so act quickly
We appreciate your cooperation.
While it is difficult to determine whether the SepSys ransomware decryptor will be deleted by the attackers, paying the ransom is discouraged by most security researchers and advisers. Keep in mind that they can simply not return the decryption tool as soon as you pay them – this is especially common with new ransomware strains that do not have an established name for themselves. In other words, the SepSys virus may be a quick-cash project for criminals.
Unfortunately, recovering data safely without paying criminals is only possible with backups – and most users do not have those ready. That is why it is crucial to backup files regularly – it can completely negate the ramification of the infection. If you had no backups, you could try using alternative recovery methods we list below, although keep in mind that chances of a successful outcome are low.
Note: make a copy of encrypted files before you remove SepSys ransomware virus, or you may corrupt the data permanently otherwise.
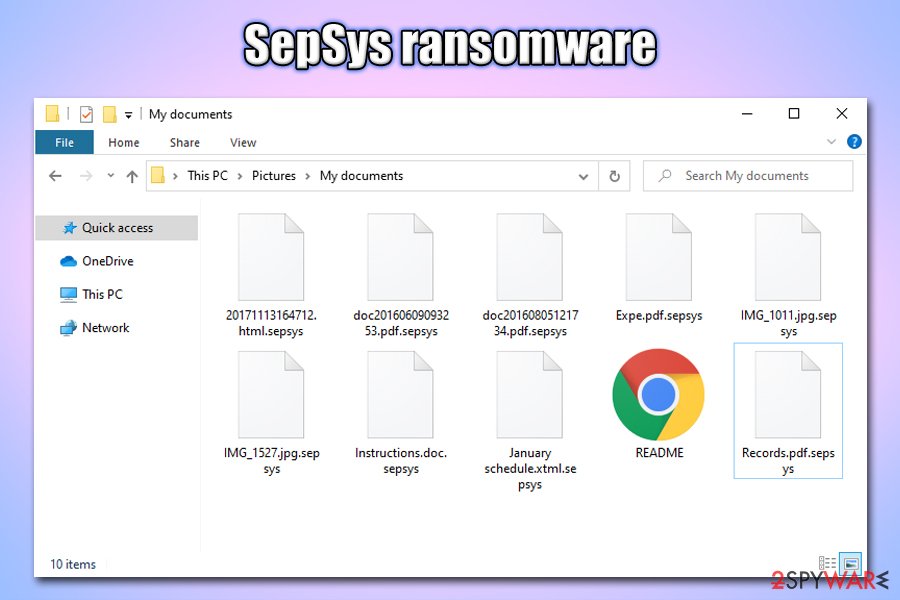
The encrypted files are marked with .sepsys extension, which also removes the regular icons with blanks

The encrypted files are marked with .sepsys extension, which also removes the regular icons with blanks
Ransomware infection can be devastating – learn how to avoid it
Because many users who do get infected with ransomware have no clue about the malware, its operation, and other important factors, they often believe that they can regain access to files as soon as it is eliminated from the computer. Unfortunately, that is not how this type of malware works – the infection of the operating system and file encryption are two separate processes, although the virus is what allows the latter to happen. In other words, you will not regain access to your files, even after ransomware elimination.
Therefore, you should ensure that you do not get infected with this dangerous malware in the first place – here are some tips from security experts:[4]
- Install reputable anti-malware software with real-time protection feature;
- Backup your most important files regularly either on an external drive or online storage service;
- Update your operating system and the installed applications as soon as security patches are released;
- Employ additional security tools, such as Firewall and ad-block;
- Disable Remote Desktop connection as soon as it is not needed anymore, protect it with a secure password, and never use a default TCP port 3389;
- Don’t click on links inside a spam email, and never allow an attachment to run macro function;
- Stop visiting high-risk websites, including torrent, gambling, free online video streaming, etc.;
- Never download software cracks or pirated software installers.
Get rid of SepSys file virus with the help of anti-malware software
As we mentioned before, file encryption and malware infection ate two separate issues that should be handled differently. In many cases, victims are confused about what to do soon after ransomware strikes, simply because they do not know much about it in the first place. Thus, SepSys ransomware removal and file recovery process depend on whether you had backups prepared. If you did – get rid of malware immediately and only then copy over files from backups. However, the majority of the infected do not have backups prepared – that is why the encrypted data should be handled differently.
First of all, you should make a copy of all the encrypted files you care about, and only then remove SepSys ransomware from your computer, as the process may permanently damage data. To get rid of malware, you should employ reputable anti-virus software that can recognize the infection. In case you are unsuccessful in normal mode, enter Safe Mode as per instructions below and perform a full system scan from there. Once you are sure that the SepSys virus is gone, proceed with the file recovery methods listed below.
This entry was posted on 2020-02-27 at 05:56 and is filed under Ransomware, Viruses.

