Qensvlcbymk ransomware – dangerous file locking malware that targets organizations
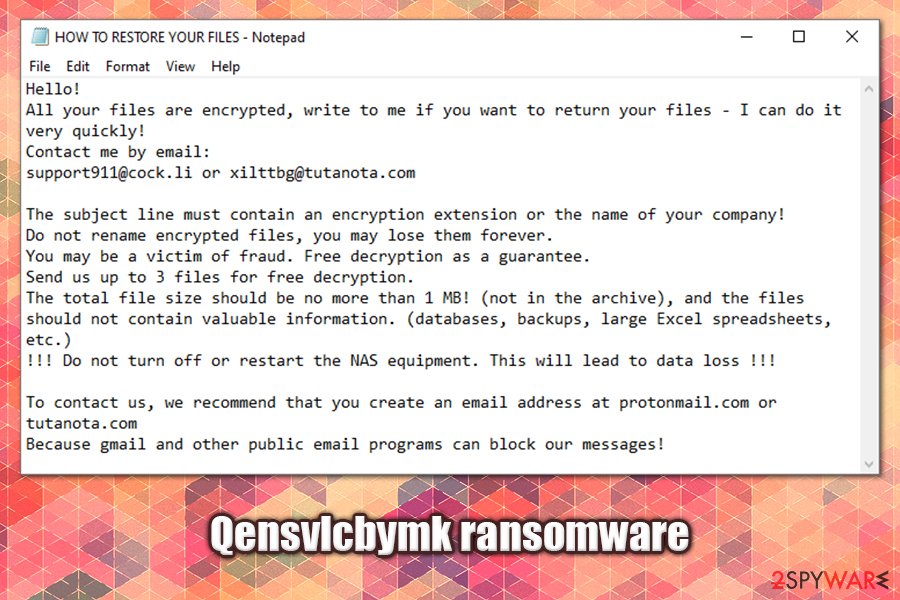
Qensvlcbymk ransomware is a data locking virus that mainly attacks corporate networks

Qensvlcbymk ransomware is a data locking virus that mainly attacks corporate networks
Qensvlcbymk ransomware is a variant of Snatch malware and was first identified by a security researcher GrujaRS on Twitter in the middle of May 2020.[1] While the version might vary slightly from other malware of such type, its main goal is to extort money from victims. While ransomware strains like Djvu mainly target regular consumers, Qensvlcbymk ransomware mostly focuses on corporations and businesses for larger ransom sums.
Once inside the system, the malware performs various checks and system changes before scanning for data to encrypt on local and networked drives (including NAS devices often used in corporations for data backups). It will encrypt most of the files with AES cipher, appending .qensvlcbymk extensions to each. The virus will also drop a ransom-demanding message (HOW TO RESTORE YOUR FILES.TXT) that asks users to email the attackers at [email protected] or [email protected] and pay the ransom in cryptocurrency for Qensvlcbymk ransomware decryption tool.
| Name | Qensvlcbymk ransomware |
| Type | File locking virus, cryptomalware |
| Family | The virus belongs to Snatch ransomware family |
| File extension | Each of the non-system and non-executable files are appended with .qensvlcbymk extension and can no longer be accessed |
| Ransom note | HOW TO RESTORE YOUR FILES.TXT is dropped into each folder where the locked data is located |
| Contact | Users are asked to email the attackers via [email protected] or [email protected] for negotiations about size of the ransom and data recovery process |
| Distribution method | Malware is highly likely to spread via weakly protected RDP connections, as its attacks are targeted |
| Main targets | Small to medium size businesses and organizations |
| Data restore |
Unfortunately, there is no secure method to recover Qensvlcbymk ransomware encrypted files if no backups were prepared or were also encrypted. Alternative methods include:
|
| Malware removal | To eliminate the infection, the infected computer or NAS device should be disconnected from the network and only then malware elimination performed with the help of powerful security software |
| System fix | To fix system damage after ransomware infection, employ repair tools like Reimage Reimage Cleaner Intego |
Snatch is a relatively established ransomware strain in the illegal crypto-extortion business since its first release back in December 2018. While it is not the most active cryptoviruses around, it released around a dozen variants (e.g., Jupstb, Egmwv, and others), targets of which are corporate networks.
At the end of 2019, the malware has started rebooting Windows computers to avoid the detection of anti-malware software and performing data encryption without interruptions.[2] Due to this, victims might also struggle with Qensvlcbymk removal, although adequate security solutions like SpyHunter 5Combo Cleaner or Malwarebytes should be able to handle the infection. Additionally, the malware is detected under following names by security tools:[3]
- Win64:Trojan-gen
- Gen:Variant.Ransom.Snatch.1
- Ransom:Win64/Qensvl!MSR
- Ransom.Snatch.GO
- Trojan-Ransom.Win32.Gen.wwz
- Trojan.TR/FileCoder.diule
- W64/Trojan.QVCE-6605, etc.
Just as other crypto-malware of such kind, Qensvlcbymk ransomware mainly uses Remote Desktop connections to penetrate corporate networks. This happens when RDPs are exposed via the default port and are not protected with adequate measures, such as strong passwords.
Attackers typically infiltrate the networks to perform surveillance, remaining undetected for weeks before releasing Qensvlcbymk ransomware manually. Looking at the latest ransomware trends, they are highly likely to exfoliate sensitive information during this time, which they can later publish online if the victims declined to pay the ransom.[4]
Once malicious actors gain access to the network, they release the main executable such as qensvlcbymkx64.exe, which begins the infection routine and reboots Windows PC into Safe Mode. In this mode, most security solutions are non-functional, which would otherwise prevent Qensvlcbymk virus infection and file encryption.
Qensvlcbymk ransomware is a file locking virus that spreads via weakly protected Remote Desktop connections

Qensvlcbymk ransomware is a file locking virus that spreads via weakly protected Remote Desktop connections
After data is locked, Qensvlcbymk ransomware boots in normal Windows mode and launches a ransom note titled as HOW TO RESTORE YOUR FILES.TXT, which reads:
Hello!
All your files are encrypted, write to me if you want to return your files – I can do it very quickly!
Contact me by email:
[email protected] or [email protected]The subject line must contain an encryption extension or the name of your company!
Do not rename encrypted files, you may lose them forever.
You may be a victim of fraud. Free decryption as a guarantee.
Send us up to 3 files for free decryption.
The total file size should be no more than 1 MB! (not in the archive), and the files should not contain valuable information. (databases, backups, large Excel spreadsheets, etc.)
!!! Do not turn off or restart the NAS equipment. This will lead to data loss !!!To contact us, we recommend that you create an email address at protonmail.com or tutanota.com
Because gmail and other public email programs can block our messages!
As evident, the attackers are asking for victims to include the name of the file extension (.qensvlcbymk, although this can vary) and the company name that the ransomware has infected for identification purposes. Snatch ransomware authors were previously seen asking for ransoms reaching 1-5 Bitcoin, although this can greatly vary depending on the size of the organization and the number of encrypted workstations/servers.
Crooks behind Qensvlcbymk ransomware are also offering free decryption of one file that is no larger than 1 MB, and should not contain any important information. This is a typical trick to make victims believe that they can trust the attackers and that they are guaranteed a Qensvlcbymk ransomware decryption tool as soon as the ransom is paid. However, there were several instances where attackers failed to fulfill their promise, or the tool simply did not work.
Before performing Qensvlcbymk ransomware removal, users should make a copy of all the important files and the registry database, as some relevant information might be stored in there. Also, the process would eliminate additional modules that the malware might install, such as publicly available test penetration tools and data-stealing components.
Once backups are prepared, the infected machine should be segregated from the infected network and then cleaned with anti-malware solutions. To restore normal functions of the Windows machine, we recommend using Reimage Reimage Cleaner Intego.
Paying cybercriminals for the Qensvlcbymk ransomware decryptor is not recommended

Paying cybercriminals for the Qensvlcbymk ransomware decryptor is not recommended
Companies should ensure a secure usage of Remote Desktop connections
Remote Desktop connections, otherwise known as RDPs, are very useful tools that allow remote access to a computer. Another reason why is RDP is so widely used is because it is built into Windows OS and can be used for free by, e.g., system administrators to reach the workstation of interest.
However, because the RDP is so popular and widely used (and also commonly poorly protected), it became one of the main attack vectors for malicious actors for surveillance and malware injection purposes. The attack is also often combined with brute-forcing – another technique that abuses weak passwords used to protect RDP connections.
The attackers typically spend weeks on the infected networks, all while gathering the necessary information and moving laterally via the network and accessing administrator accounts. After the malware is launched, the whole network should be considered compromised.
To protect your company from RDP attacks, practice the following precautionary measures:
- Never use a default TCP/UDP port 3389;
- Use a strong password fro connection and never reuse it for anything else;
- Enable Network Level Authentication (NLA) via System Properties;
- Employ a reputable VPN service for the computers that use RDP services;
- Limit the number of employees that can access the service;
- Disconnect from RDP as soon as it is not used for anything;
- Protect your network with endpoint security solutions.
Eliminate Qensvlcbymk ransomware correctly
Since the Qensvlcbymk virus is a part of Snatch ransomware, it may run a component called SuperBackupMan in Safe Mode (it is typically established during the infection routine). Thanks to this feature, rebooting the system into Safe Mode with not stop the malware from operating, although performing a full system scan with most up-to-date security software (we recommend using SpyHunter 5Combo Cleaner, Malwarebytes, or another reputable security tool) should help you perform Qensvlcbymk ransomware removal without problems.
However, before you remove Qensvlcbymk ransomware from the system, there are several steps that need to follow. First of all, all the affected machines should be disconnected from the infected network and a full backup of the hard drive performed (if important files are present). After that, you can use security software to terminate the infection, along with all the malicious files and modules that were inserted by the attackers.
The best way to recover encrypted files is by restoring them from backups. If you do not have backups ready, there are very few chances currently to recover data for free. Paying cybercriminals remains an option, although it is very risky and discouraged by most security researchers. Unfortunately, that might be the only choice in some cases.
This entry was posted on 2020-05-20 at 07:21 and is filed under Ransomware, Viruses.

