NanoCore virus is a sophisticated trojan that threat actors utilize to remotely control the infected machine
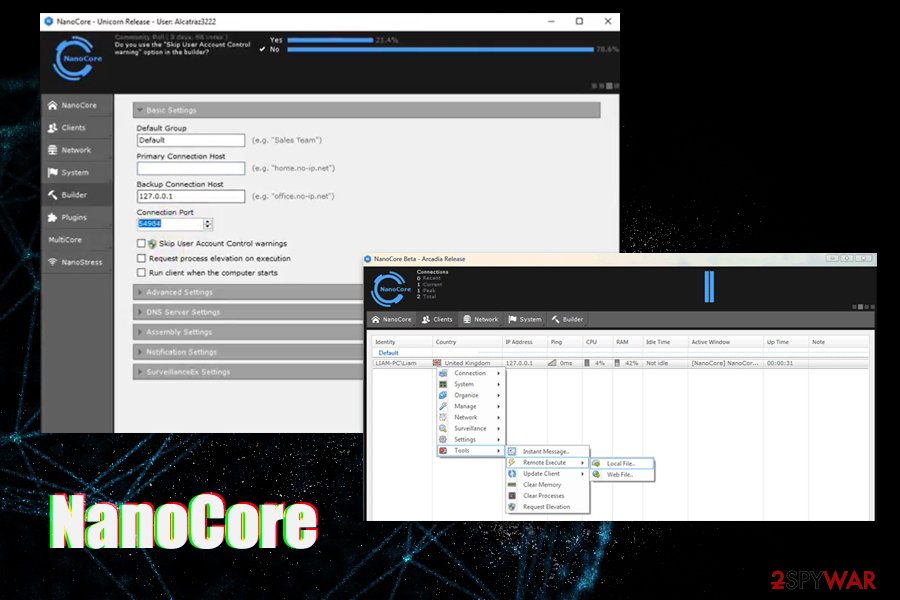
NanoCore virus is a remote access trojan (RAT) that allows the attackers to take over the host machine
NanoCore virus is a backdoor and a remote access trojan that is used in a variety of campaigns by various cybercriminal groups. The malware is typically distributed with the help of malicious spam email attachments,[1] where hackers use botnets to send thousands of emails to malicious victims, although users could also get infected with it once they download an infected file from a third-party site. Some variants of NanoCore RAT were spotted using a fileless infection[2] method – malicious files are embedded into memory instead of writing them on the disk, which provides the malware with increased stealth capabilities.
The main function of NanoCore virus is to grant remote access to the computer to threat actors. Once that is achieved, they can control the machine in many different ways, such as take screenshots, record keystrokes, collect passwords, gather technical information, steal emails, and much more. NanoCore is one of the most dangerous RATs, available to buy or even get for free, as the source code has been leaked multiple times online.
| Name | NanoCore virus |
| Type | Remote Access Trojan |
| Operation | Deactivates Windows recovery functions like startup repair and restore points, disables the Task Manager and UAC, modifies Windows registry, opens a backdoor, etc. |
| Activities | NanoCore allows malicious actors to take complete control over the infected machine: take screenshots, steal passwords, record keyboard inputs, send spam, steal files, and perform other actions |
| Similar RATs | NjRat, NetWire, Orcust, Poison-Ivy, DarkComent, etc. |
| Distribution methods | Malicious spam email attachments and infected files downloaded from various websites |
| Main malware components | ufj=ked, cxf.exe, qnb.jpg |
| Related process | Default Document Handler (32 bit) |
| Detection |
AV detection on Virus Total:
|
| Termination | Access Safe Mode with Networking as explained below and perform a full system scan |
| System recovery | RATs heavily modify Windows settings and alter various system files. Post-removal, the files might remain damaged, resulting in the computer malfunction, crashes, errors, etc. To recover from malware infection without having to reinstall the operating system, you can use Reimage Reimage Cleaner repair tool |
Besides gathering information, NanoCore is also capable of opening a backdoor – meaning, that the threat actors can use the machine for other malicious purposes, such as sending spam emails from it (basically, including it into the already existing botnet) and proliferating other malware. As a result, the trojan can spread to other victims much faster, and also infect hosts with devastating malware like ransomware. NanoCore virus removal is necessary for the safety of any machine and as well as its owner.
To remove NanoCore virus from the system, infected users should access Safe Mode with Networking and perform a full system scan with powerful anti-malware software. For more details, please refer to the bottom section of the article.
NanoCore is a modular malware – it incorporates various modules, each of which is responsible for different tasks on the infected computer. Upon initial execution of the malicious payload, the malware performs a variety of Windows system changes, including:
- Checks for the prescience of anti-virus software;
- Checks whether it encountered a sandbox environment or a virtual machine – exists if that is the case;
- Places a randomly-named executable into the %APPDATA% folder, which is set to “read-only” and “hidden” setting;
- Deletes certain settings profiles within the %APPDATA% folder;
- Heavily modifies various keys within the Windows registry.
For persistence, NanoCore virus disables the User Account Control (UAC), disables the Task Manager, removes system restore points, and adds a Windows Update key to the registry to boot with every system launch.

NanoCore is a type of malware that disables several Windows functions in order to spy on the infected users
During the analysis of NanoCore virus, the researchers from Morphisec[3] found that the malware is written relatively badly, as it contains a variety of useless code lines, bad values, and meaningless comments, which required cleaning. Nevertheless, much of the malware code was obfuscated or encrypted.
Currently, NanoCore is one of the most sophisticated and dangerous RATs available to threat actors – they also more often than not use legitimate Windows processes in order to inject malicious files into the machine’s memory instead of the disk, remaining undetected during the whole process.
Fileless infection methods might prevent AVs to stop the intrusion of NanoCore
NanoCore trojan is a multi-stage malware, which means that it uses several different stages to infect the machine. This functionality is particularly useful as it helps the virus to evade detection, disable certain vital Windows functions, and remain on the system undetected.
NanoCore virus has been mainly distributed by malicious email attachments – these usually use social engineering in order for the victim to open the malicious document. Most commonly, threat actors copy the attributes of an official company and try to make users believe that the attachment contains important information, which prompts them to open it. In most of the cases, hackers leverage malicious macros and scripts embedded within .docx, .vbs, .pdf, and other files.
There are three different ways NanoCore virus starts its infection process:
- Changing the original Autoit3.exe into a malicious cxf.exe
- Using PowerShell commands.
- Using the malicious AutoIT script.
While all of these methods differ in the background, they all result in the download and execution of the malicious NanoCore trojan. In some cases, the usage of a malicious AutoIT script, which is a legitimate tool which allows the administrators to automate Windows GUI and general scripting, allows the attackers to bypass the User Account Control and infect the malicious payload directly into memory, preventing anti-virus tools from spotting the entry of malware.
NanoCore is known to use fileless infection – a method where data is written into memory instead of the hard disk
Delete NanoCore virus for your own safety
The main danger of remote access trojans is that they rarely emit any obvious symptoms that less experienced computer users would notice. Nevertheless, the presence of NanoCore virus on the computer can be immediately spotted after notifying that several Windows functions don’t work as intended (for example, pressing Ctrl + Shift + Del would not call up a Task Manager since it is disabled by malware) and several processes and other entries are present on the system. Therefore, if you notice that Windows does not do what it is supposed to do, you should scan your machine with anti-malware software and remove NanoCore at once – refer to the instructions below.
Note that stopping the malware might prove difficult for many anti-virus programs, as it often uses a fileless infection method – this prevents AVs from detecting the initial malicious activity. Nevertheless, most of the advanced security solutions should be capable of performing NanoCore virus removal as soon as it starts to perform its post-infection activities. Therefore, it is vital to keep a powerful anti-malware running on the system at all times.
Once you get rid of NanoCore trojan, you might find that Windows is broken – it crashes, errors pop-up often, programs don’t launch, etc. This is very common after a malware infection, as it heavily modifies system files, and, once anti-virus removes malicious entries, the infected files remain broken. To fix that, we highly recommend using Reimage Reimage Cleaner – it can repair the OS without the need to reinstall it.
This entry was posted on 2020-01-22 at 05:25 and is filed under Trojans, Viruses.

