Two websites providing misleading protection software were investigated by cybersecurity specialists
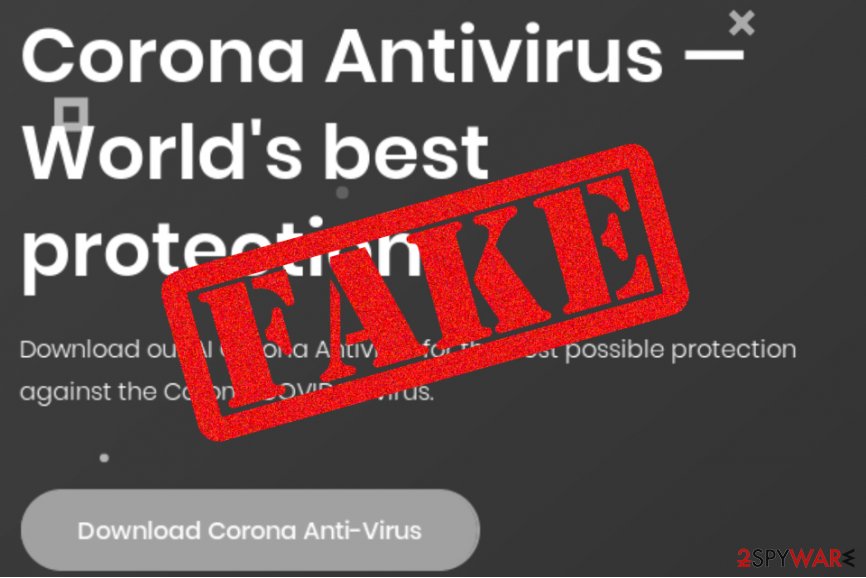

Hackers decided to play a joke on the users and created two suspicious websites named corona-antivirus.com and antivirus-covid19.site aiming to advertise some type of antivirus tool that is supposed to protect the users from the widespread Corona disease. As you should have thought already, this type of goal is completely unrealistic and the authors of the software outline features that are not truly possible to develop:
Active protection from your mobile device. Your mobile device actively protects you against the Coronaviruses (Cov) while the app is running.
You should definitely keep in mind that there is no “cyber way” to protect yourself from the COVID-19 infection. The only things you can do are precautionary measures such as limiting your time outside, wearing masks, washing your hands, etc.
The suspicious corona-antivirus.com website was first spotted by cybersecurity researchers named MalwareHunterTeam who announced their findings on Twitter at the start of March.[1] These domains, including antivirus-covid19.site were both also discovered by Malwarebytes specialists[2] and the secondly-mentioned one is already inactive. However, the first one still remains accessible but all malware-laden hyperlinks were eliminated directly from it.
BlackNET botnet can initiate multiple malicious activities on the infected machine
The main goal of the people who created the antivirus software-based websites is not to help users to protect themselves from the Coronavirus disease but to install the BlackNET RAT. When the malicious hyperlink was still active, the potential victims would have downloaded the malware via antivirus-covid19.site/update.exe payload.
This executable includes a commercial packer known as Themida that changes the computer system to a botnet-based one[3] that is programmed to take orders from the instaboom-hello.site that is employed by the BlackNET malware.
There are many activities that the botnet can initiate once it appears on the infected computer. For example, performing DDOS attempts, stealing passwords that are saved on the machine and cookies from the Firefox web browser, installing a key-logging feature, screenshotting, running malicious codes, the theft of Bitcoin wallets, managing the device’s turn on and off functions, upgrading or deleting the bot client, executing hidden domains.
The best way to protect yourself from such malware is to avoid downloading and installing unknown files from the Internet. If you have already downloaded some type of component to your computer, you need to scan it with antimalware to make sure that it does not hold any malicious content inside.
Be aware of hackers who want to misuse the terrible Coronavirus incident
BlackNET is not the only RAT that has been pushed to users by abusing the name of the Coronavirus disease. Since COVID-19[4] started, a lot of hackers have been releasing phishing campaigns seeking to infect users with dangerous malware forms.
One of the recent attempts was to distribute the Crimson RAT payload to potential victims.[5] This campaign was initiated by a well-known hacking group named ATP36. Cybercriminals were pushing fake health advisories in formats of executable files through phishing email messages that included the malware. Once the user enabled the macros of the file, the malicious content would execute and install on the targeted computer system by checking if the OS is running on a 32-bit or 34-bit variant.
