Zloader – a dangerous banking Trojan that is based on the notorious Zeus malware

Zloader is a banking Trojan that is used to exfoliate sensitive information from its targets

Zloader is a banking Trojan that is used to exfoliate sensitive information from its targets
Zloader, otherwise known as Zeus Sphinx or Tredot, is banking malware that first emerged in August 2015, and since then keeps coming back with new campaigns. Malware is based on a well-known Zeus Trojan – its source code was leaked in 2011, so malicious actor groups quickly found ways to utilize it.
Zloader malware is being sold on underground forums for everybody willing to use it – for as low as $500. Since its release, the Trojan kept a relatively low profile but soon resurfaced again with COVID-19 malspam campaigns,[1] imitating the pandemic relief payment emails. Nonetheless, it can also be distributed in different ways, such as fake updates or scam messages placed on malicious websites, as well as exploit kits (Sundown).[2]
Once installed, Tredot will hijack built-in processes (Windows Explorer) and patch executables of Google Chrome, Mozilla Firefox, and Internet Explorer in order to capture user information, such as banking credentials, email and social media logins, etc. While its main purpose on the host system is to steal data, it will also download and install another well-known malware Zbot.
| Name | Zloader |
|---|---|
| Type | Banking Trojan |
| Aliases | Zeus Sphinx, Tredot |
| Origins | The malware was introduced into the cyberspace in 2015 and is based on the source code of Zeus banking malware |
| Distribution | Zloader was seen in many malicious campaigns and uses multiple attack vectors, including phishing spam, hacked websites, fake updates, exploits, drive-by downloads, etc. |
| Related files | Forwardhou.dll, cnfnot32.exe, ChiefCo.dll, vsmsoui.dll, myvtfile.exe, etc. |
| Infection symptoms | Trojans are typically very difficult to detect as they are programmed to not emit any symptoms to a regular user |
| Associated risks | Infected computers can be used to install more malware, such as Zbot Trojan, which can compromise user safety and computer security further. Ultimately, data-stealing malware infection can result in financial losses, further malware infection, Windows system damage, and even identity theft |
| Malware removal | To eliminate the malicious payload, along with secondary ones, you should employ powerful anti-malware software and perform a full system scan (access Safe Mode if required – we explain how below) |
| System fix | Malware can leave the operating system damaged after it is terminated. To fix this damage and issues that come with it, you can employ a PC repair tool Reimage Reimage Cleaner Intego |
When it comes to malware, there are several different sources that it can come from and end up on your machine. If the system is not adequately protected with security software and other tools, there is nothing that could stop malware, such as Zloader, from spreading throughout the PC, and even laterally if it is connected to a network.
Therefore, it is really important to protect your machine adequately. In fact, you can altogether avoid Zloader removal process and the compromise of your sensitive data if you employ a robust anti-malware application, which detects malware under the following names (note that there are thousands of malicious files that can initiate the download of Tredot malware, hence the executable, as well as detection names vary):[3]
- TR/AD.ZLoader.avl
- Trojan-Downloader.Win32.Zload.bl
- Trojan:Win32/Zloader.SA!MSR
- RDN/Generic.dx
- Trojan.TR/AD.ZLoader.avl
- W32.Trojan.Gen
- Trojan.Agent (A)
- A Variant Of Win32/GenKryptik.EIDM, etc.
You can remove Zloader by employing reputable anti-malware software, such as SpyHunter 5Combo Cleaner or Malwarebytes. However, in some cases, you might have to access Safe Mode with Networking in order to suppress its activities, since it is known to use persistence techniques. Unfortunately, in many cases, you might not even be aware the Tredot is sneakily operating in the background, as Trojans are designed to be stealthy and not show symptoms of the infection.
Despite that, you might see some strange computer behavior due to various actions by Zloader malware, such as random PC shutdowns/restarts, increased CPU usage, errors, BSODs, and similar. This behavior might also persist after you remove Tredot – you could employ tools like Reimage Reimage Cleaner Intego to fix the damage done to the operating system instead of reinstalling it completely.
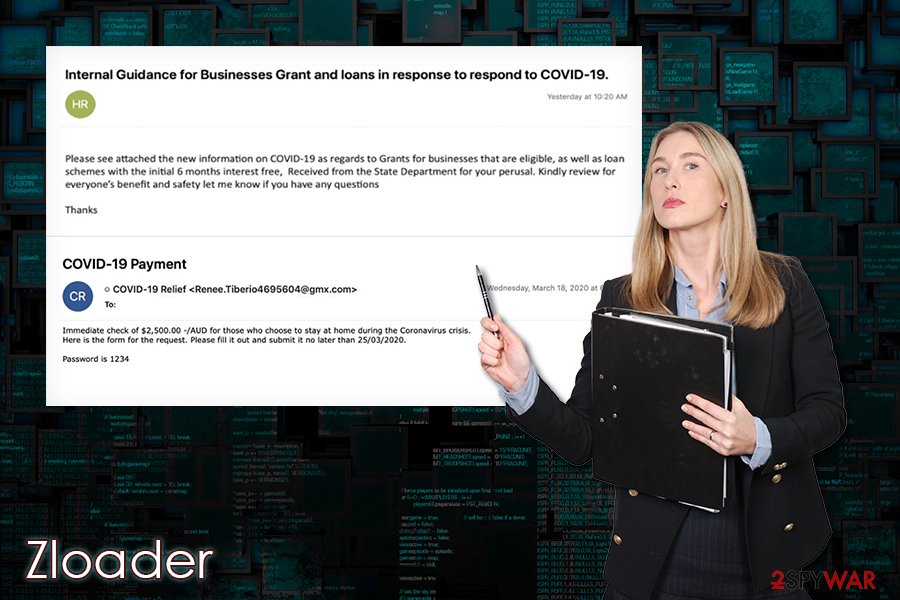
Zloader is malware that was based on a notorious Zeus Banker

Zloader is malware that was based on a notorious Zeus Banker
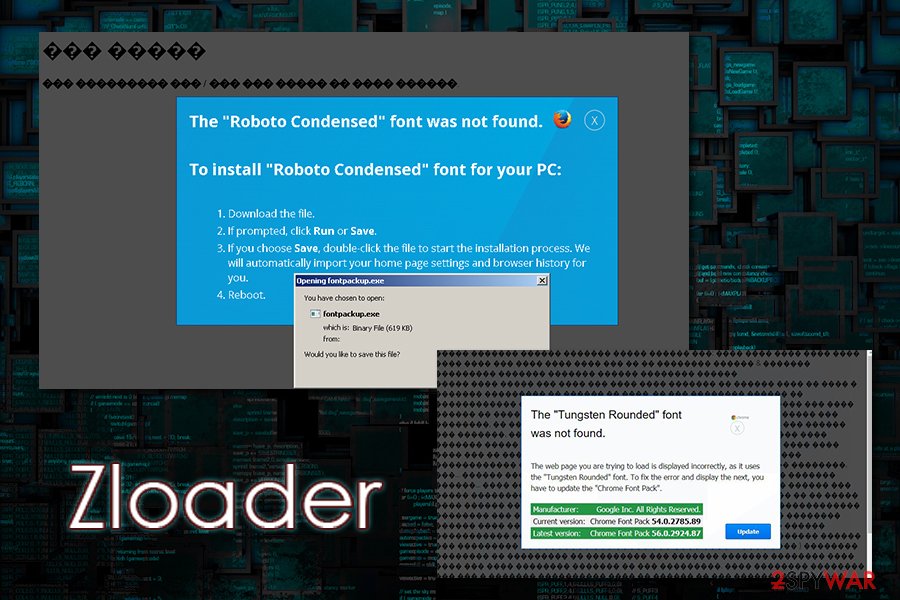
Fake warnings about a missing font – one of the tactics used to spread Zloader malware
A very popular tactic used by threat actors to distribute the Zloader virus is by using fake messages that claim that the contents of the website are not recognized due to a missing font. This popular technique is not new and has been used by many different malware developers, such as Spora ransomware or Ursnif banking malware.
This tactic allows the attackers to exploit the human mind and make them believe that what they are doing is not harmful. To achieve that, Zloader malware operators first need to ensure that users visit fake message websites, and it is often done via malicious advertisements, JavaScript processes, and much more.
Once users land on the site, they are typically presented with the following text:
The “Roboto Condensed” font wasn’t found.
The website you are trying to load is displayed incorrectly, as it uses the “Roboto Condensed” font. To fix the error and display the text, you have to update “Chrome Font Pack”.
Manufacturer: Google Inc. All Rights Reserved
Current Version: [version]
Latest version: [version]
This makes users believe that they need to download a font pack in order to view the contents of the page. Typically the downloaded file is named “Chrome_Font.js” or “Mozilla_Font.js” – the name differs depending on the web browser used. The JS extensions mean that the file is a JavaScript file, which would download and execute the malicious payload on the host computer.
However, this is not the only way Tredot malware is propagated since it is distributed by various groups of cybercriminals thanks to its malware-as-a-service scheme. It means that everybody wanting can use the malicious code, as long as they pay a particular sum of money. The services of malware strains are typically advertised on the dark web’s hacking forums, and those willing to use malware to their advantage do not even need to be proficient hackers.
Thus, pro protect yourself from malware, consider using these precautionary measures:
- Install comprehensive anti-malware software with real-time web protection feature;
- Update Windows along with all the installed applications as soon as security patches are released;
- Use strong passwords for all your accounts;
- Enable two-factor authentication (2FA) where possible;
- When dealing with emails, never allow the clipped attachments to run macros (“Allow content”) on your machine;
- Do not download software cracks and pirated software installers;
- If used, protect your Remote Desktop adequately: never use a default TCP/UDP port, employ VPN, limit usage to only people who actually need it, etc.
Zloader/Tredot is spread in various different ways, including the “Font was not found” scams encountered online

Zloader/Tredot is spread in various different ways, including the “Font was not found” scams encountered online
Zloader and its infection routine
As mentioned above, the Zloader virus uses a variety of techniques to proliferate the system. Since there are multiple different variants of the malware, it might also posses different features that might not be present in other versions. However, as explained by researchers, the malware does not change much since its initial release back in 2015 and simply resurfaces in different campaigns.
Once the infection is triggered in one way or another, Tredot Trojan hijacks WScript.exe process to contact its Command & Control server in order to retrieve the malicious DLL file (it is often self-signed – a technique used to evade detection by anti-malware tools) and placing it into %SYSTEMDRIVE% folder, and later launched with the help of a legitimate Regsvr32.exe. Malware then places thousands of files into %AppData% folders and modifies the Windows registry for persistence.
Zloader malware then proceeds to apply a patch to various processes on Windows, such as Windows Explorer (explorer.exe), Google Chrome (chrome.exe), Mozilla Firefox (forefox.exe), and Internet Explorer (iexplorer.exe). These changes to the processes allow the malware to inject code into web browsers and capture users’ credentials and other sensitive data, later sending it off to a remote server controlled by the attackers via the “Tables” function:[4]
Once a connection to the Tables panel has been established, Sphinx will fetch additional JavaScript files for its web injects to fit with the targeted bank the user is browsing. Injections are all set up on the same domain with specific JS scripts for each bank/target
Zloader will also download and install Zbot from a Command & Control server after configuring proxies. Also, malware is capable of injecting malicious payloads into memory, making it so much more difficult to detect and remove.
All in all, Tredot, along with its secondary payloads such as Zbot, serves as a deadly combo that is capable of comprehensively stealing data from the compromised computer, performing man-in-the-middle attacks,[5] and compromising the host machine/network even further.
Zloader can use different files to begin the infection routine

Zloader can use different files to begin the infection routine
Ways to terminate Zloader/Tredot from the system effectively
Malware can target regular consumers, as well as corporations/businesses. Thus, you should immediately segregate the infected machine from the network before performing Zloader removal, as it can spread laterally and reinfect the system once deleted.
Note that malware also can inject payload into memory, so security software might not recognize it prior to infection – until all the malicious files are populated. Thus, to remove Zloader properly, you should access Safe Mode with Networking and perform a full system scan from there. Ensure that anti-malware is up-to-date before performing a scan, however, as new variants of Tredot virus are emerging regularly.
Once you eliminate the Zloader virus, remember to deal with the aftermath of the infection. First of all, if your machine is lagging and returning errors, use tools like Reimage Reimage Cleaner Intego to fix the damage done to the system files. Also, do not forget that info-stealing malware can cause tremendous damage, even if it is removed. Thus, you should monitor your online banking to ensure that no unsolicited transactions were performed. It is also recommended to change all the passwords that were used within the browsers of the infected computer.
This entry was posted on 2020-05-15 at 05:40 and is filed under Trojans, Viruses.

