Void ransomware is a malicious cyber infection that uses a combination of encryption algorithms to render files on a host machine useless
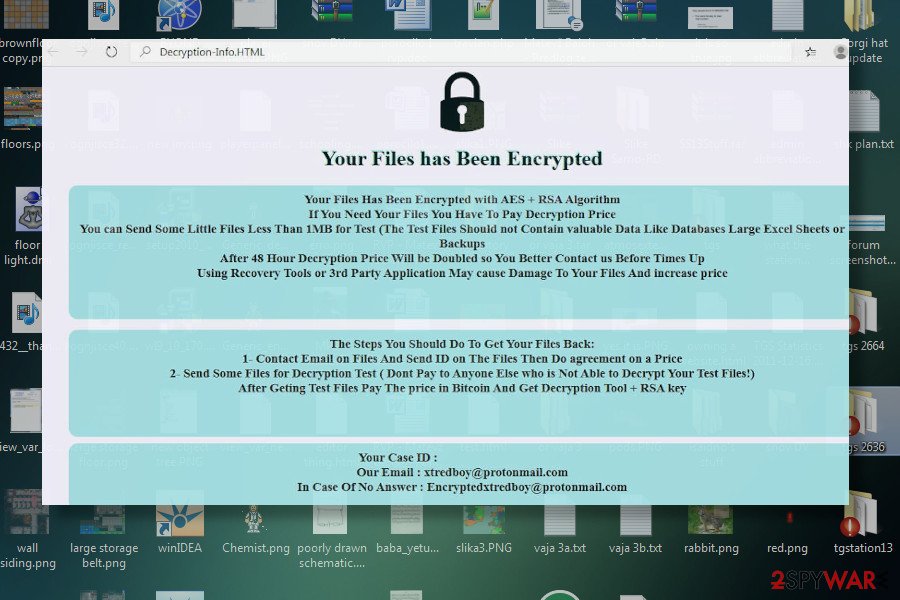

Void is a dangerous ransomware virus that has been detected at the beginning of April 2020. The name of the ransomware suggests that it may stem from the also known file-encrypting ransomware VoidCryp. However, the ransomware is still under investigation and shows some relations with Ouroborus. The two share some malicious files, which is why AV engines tend to recognize it as Ransom:Win32/Ouroboros.d16a998c and Trojan[Ransom]/Win32.Odveta.gen[1]. The current Void version is known for attaching .void file extension to most of the files, which are encrypted using a combination of AES and RSA-2048[2] ciphers. Aside from .void extension, locked files also contain a related email address, most frequently [email protected] or [email protected].
The distribution of the Void ransomware virus complies with the typical ransomware distribution methods. Usually, ransomware payload is launched via unprotected insecure RDP configurations,[3] spam email attachments, botnets, fake software updates or infected installers. However, the most frequently exploited distribution technique remains spam email attachments. Upon infiltration, Void malware initiates multiple system’s changes withing the following system’s folders:
%SystemDrive%\ (C:\)
%SystemRoot% (C:\Windows, %WinDir%)
%UserProfile%
%UserProfile%\AppData\Roaming\
%AllUserProfile%
%AppData%
%AppData%\Local\Temp\
%LocalAppData%
%ProgramData%
%Temp% (C:\Windows, %UserProfile%\%AppData%\Local)
| Title | Void |
| Type | Cryptomalware, file locking virus |
| Family | Currently not specified |
| Related files | [email protected] |
| Extension | [ID].void file extension is appended to all non-system files |
| Ransom note | Decryption-Info.HTA, IDo.txt or pubkey.txt |
| Contact email | [email protected] or [email protected] |
| Encryption | Combination of AES and RSA-2048 |
| File decryption |
The official Void descriptor is not available. The ransomware locks files using a combination of difficult-to-crack ciphers, which is why it may be difficult to get files back without paying the ransom. Nevertheless, upon full Void removal with SpyHunter 5Combo Cleaner or another AV engine, you can use:
|
| Tip |
In most of the cases, ransomware viruses seriously damage Windows files and may lead to abnormal OS performance (prolonged boot process, crashes, errors, BSOD, etc.). If you encounter any of these problems or if you want to prevent them in the future, you should repair the system with Reimage Reimage Cleaner Intego utility. |
According to researchers, one of the main executables that Void runs is [email protected]. The file starts running in the background and can hardly be disabled manually. Once the background processes are implemented, the ransomware manifests its presence by corrupting all files kept on the host machine. Each affected file is marked by .void suffix. Besides, each folder that contains encrypted files contains a ransom note in the form of a Decryption-Info.HTA, IDo.txt or pubkey.txt. The ransom note contains the following information:
Your Files has Been Encrypted
Your Files Has Been Encrypted with AES + RSA Algorithm
If You Need Your Files You Have To Pay Decryption Price
You can Send Some Little Files Less Than 1MB for Test (The Test Files Should not Contain valuable Data Like Databases Large Excel Sheets or Backups
After 48 Hour Decryption Price Will be Doubled so You Better Contact us Before Times Up
Using Recovery Tools or 3rd Party Application May cause Damage To Your Files And increase price
The Steps You Should Do To Get Your Files Back:
1- Contact Email on Files And Send ID on The Files Then Do agreement on a Price
2- Send Some Files for Decryption Test ( Dont Pay to Anyone Else who is Not Able to Decrypt Your Test Files!)
After Geting Test Files Pay The price in Bitcoin And Get Decryption Tool + RSA key
Your Case ID :EJHPFWKYCNQ5***
Our Email : [email protected]
In Case Of No Answer : [email protected]
Unfortunately, Void decryption software is not yet available. Security experts revealed that the malware exploits AES + RSA-2048 ciphers that blend diverse coding methods and render files on the victim’s PC’s permanently locked without a specific descriptor. Currently, the only way to get files encrypted by Void ransomware is to pay the ransom. Paying the ransom is not an easy task for less IT-savvy people because they have to create a Bitcoin wallet and purchase Bitcoins at first.
As evident that actors behind Void virus own a personal decryption key, criminals offer a free decryption test. For this purpose, the victim has to send 1MB file within 48 hours to [email protected] or [email protected] email address and indicate the ID number which is provided on the ransom note.
However, we do not recommend supporting criminals for their illegal activities. Even though they are trying to scare their victims into believing that their files will be permanently removed if they try alternative data recovery tools or attempt to remove Void ransomware with an antivirus, such claims do not have a clear ground. It is not clear yet what the cost of the Void decryption key is. However, based on the analysis of ransomware viruses it is presumed that the cost may vary from $300 to $2000 in Bitcoin[4].

Upon infiltration, void locks non-system files and appends .void file extension

Upon infiltration, void locks non-system files and appends .void file extension
Those unwilling to have deals with criminals are recommended to boot the system into Safe Mode with Networking and make a copy of locked files. After that, run a full system check with SpyHunter 5Combo Cleaner, Malwarebytes or another reliable AV engine and remove Void ransomware permanently. It’s important to note that ransomware-related files may be hidden in folders like %AppData%, which by default are hidden by the operating system. Therefore, before checking the system for the virus you may need to configure Windows to show hidden files & folders.
Tip: it is advisable to initiate a full system repair right after Void removal. As we have already pointed out, ransomware is extremely malicious in general since it is capable of compromising multiple settings and files on a host machine. A scan with an AV engine can hardly restore these changes. Therefore, to prevent the system’s crashes, BSOD, errors and other side effects try using Reimage Reimage Cleaner Intego repair tool.
Sort emails carefully and avoid pirated software to prevent files from encryption
According to researchers who are dedicated to cybersecurity issues like ransomware attacks, the straightest way to launch ransomware payload is to open malicious email attachments or leave RDP connections unprotected,
Although there are many other means to attack PCs, fake software downloads, software cracks, and similar methods do not work as efficiently as, for example, well-prepared spam emails work. Criminals exploit botnets to distribute phishing emails to a huge number of email addresses. Malicious spam emails typically contain a hyperlink or an attachment, which is either leads to a website that impersonates reliable vendors (bank, Microsoft, PayPal, DHL, etc.) or asks to open a shared document, which is of high importance. Opening the attachment or clicking on the provided link leads to the execution of ransomware payload and immediate encryption of files.
Remote Desktop sessions is yet another widely exploited medium for ransomware dissemination. This technique most successfully works when attacking businesses and organizations. Remote Desktop Protocol (RDP) is an encrypted channel used to prevent third parties from viewing the sessions. Unfortunately, RDP has multiple vulnerabilities, which gives a fairground for man-in-the-middle attacks. Therefore, it is advisable to take care of the RDP and put the access behind VPN and make sure to use additional software tools to ensure a full RDP’s protection.
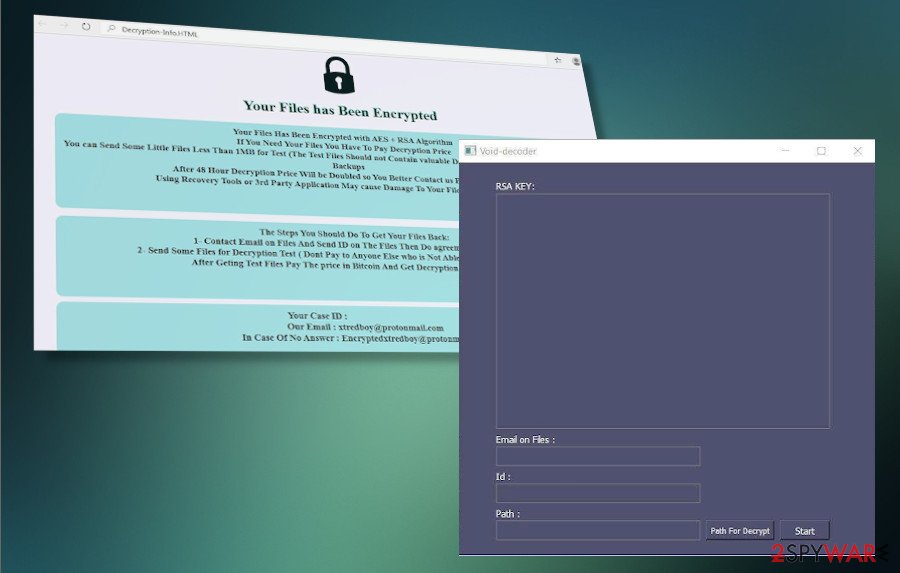
There is no free Void decryptor yet, though criminals provide victims with a Void decoder in exchange for a redemption

There is no free Void decryptor yet, though criminals provide victims with a Void decoder in exchange for a redemption
In general, it’s very important to take all security measures to keep the system protected from virus attacks. Software cracks, unpatched vulnerabilities, pirated software and similar means that are well-known for bad actors can easily turn to a backdoor for ransomware attacks. Therefore, make sure to update your OS regularly, as well as rely on a powerful AV tool.
Explaining Void removal peculiarities
Void ransomware is a misleading type of threat that can root into the OS and initiate multiple changes on the system to prevent detection and removal. Therefore, the only possible way to get rid of ransomware files is to launch a professional AV utility. We recommend using SpyHunter 5Combo Cleaner or Malwarebytes, though you can any tool that has an updated virus database and a powerful malware scanner.
Do not fall for manic if any attempt to remove Void virus is terminated. This ransomware may run malicious processes that block AV engines. Therefore, success in Void removal can be achieved while in Safe Mode with Networking only. The guide below will explain how to change the environment and how to launch the AV scanner step-by-step.
Remove Void using Safe Mode with Networking
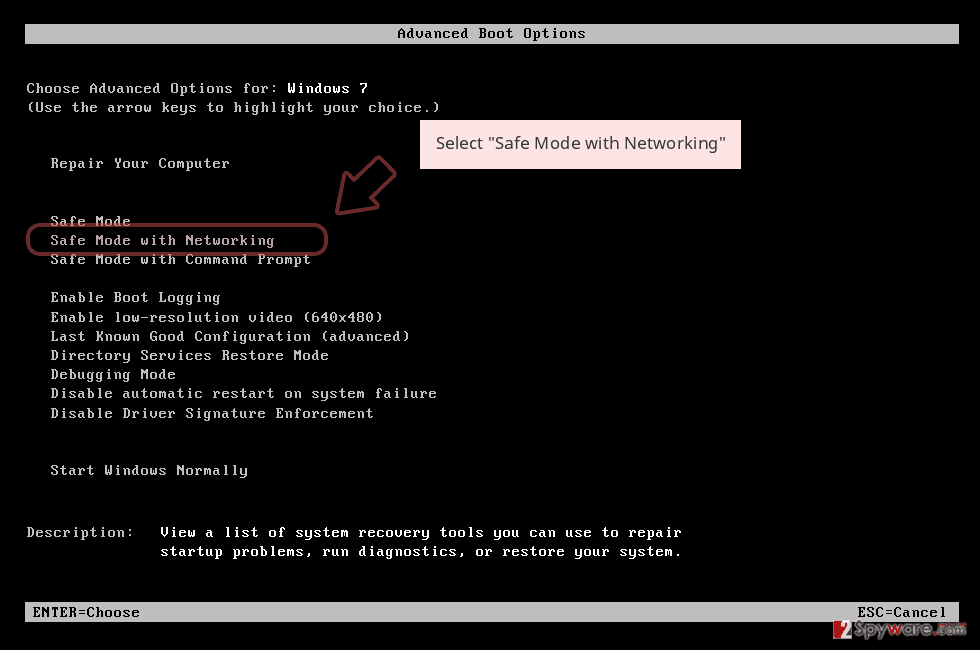
To remove Void ransomware from Windows, boot the system into Safe Mode with Networking
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
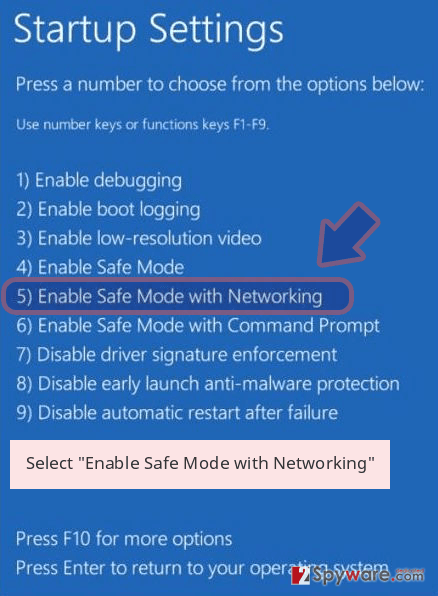
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner Intego or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete Void removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove Void using System Restore
An alternative to Safe Mode, System Restore feature can also be used to terminate Void
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Void from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If your files are encrypted by Void, you can use several methods to restore them:
Try Data Recovery Pro
Data Recovery Pro is a utility that is primarily used for data recovery after the system’s crash. However, it turned out to be a powerful tool in decrypting files locked by ransomware.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Void ransomware;
- Restore them.
Windows Previous Version feature can help to get some files back
If your OS have a feature of the Previous Version enabled, try to retrieve files encrypted by Void using this funcion.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Check for Volumes Shadow copies
The latest ransomware tends to eliminate Volume Shadow Copies. However, the are many examples when crooks failed to eliminate Shadow Copies and the Void virus may be the case. Therefore, try to perform the following steps to decrypt files locked by this ransomware.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No Void descriptor available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Void and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner Intego, SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2020-04-14 at 05:38 and is filed under Ransomware, Viruses.

