Trojan/Win64.Meterpreter is not a false positive detection – it’s an activity sign of a dangerous Meterpreter banking trojan


Trojan/Win64.Meterpreter is a generic threat detection name that can be brought by any reputable AV engine, but most frequently it’s triggered by Windows Defender, Ikarus, and Malwarebytes[1]. Although some discussion forums contain false discussions saying that this detection is false positive, seeing this detection is a serious warning about the presence of a malicious Trojan horse infection.
The Trojan/Win64.Meterpreter is a heuristic name displayed by AV tools, though it directly points to a password-stealing banking Trojan dubbed as Meterpreter. The malware can disguise under legitimate Windows system files, such as explorer.exe to create persistence and prevent removal.
Meterpreter Trojan is a cyber infection developed on the bases of the Metasploit Framework[2]. It may be distributed via infected HTTP servers, fake downloads, cracks, pirated software, or spam email attachments. Once the malicious payload is launched, the Trojan seeks to create persistence, connect to the C2 server, and regularly record data intending to steal passwords, credit card info, and other highly-sensitive credentials.
| NAME | Trojan/Win64.Meterpreter |
| CLASSIFICATION | Banking Trojan, Malware |
| ALSO KNOWN AS | Meterpreter Trojan |
| SYMPTOMS | If the Trojan is silently running on the machine, people should notice a significant decrease in PC’s performance, high CPU usage by suspicious processes, Internet speed slowdowns, etc. |
| FILES | Tend to misuse explorer.exe file. The main executable – trabajo.docm |
| DISTRIBUTION | The Trojan spreads via infected HTTP servers, fake software updates, malicious spam attachments, etc. |
| MAIN DANGERS | It seeks to leak users’ passwords, credit card details, and other credentials that are required for banking operations |
| REMOVAL OPTIONS | The only way to eliminate a Trojan – fully scan the system with a robust anti-virus program |
| Trojans initiate loads of unauthorized distortions on the machine, including registry removal, disabling of crucial processes, injection of useless files, etc. The system damage may be recovered by Reimage Reimage Cleaner Intego software. | |
The Trojan/Win64.Meterpreter detection can be found on the system by various AV tools automatically or when running a full scan with it. In case of a false-positive, you should receive the alert without noticing other system malfunctions, including slowdowns, high CPU, or unknown files running (explorer.exe, trabajo.docm, etc.).
In some rare cases, the Trojan/Win64.Meterpreter virus alarm can be triggered by software inconsistencies. Some people reported that the detection stopped from being reported after eliminating the remnants of security software, for instance, Avast. If you have been using a security tool and uninstalled it inappropriately (without eliminating its registries), the remnants can eventually trigger false positive detections by the new AV engine. In this case, Reimage Reimage Cleaner Intego repair tool might help.
However, we recommend people to take precautionary measures and protect their credentials by initiating a full Trojan/Win64.Meterpreter removal. If your AV tool brought you such detection, it’s most likely that the system is infected by a malicious Meterpreter Trojan horse, which seeks to steal usernames, passwords, other credentials, or information that is required to perform certain banking operations or launch particular commands.
If you cannot decide whether the Trojan/Win64.Meterpreter is a false-positive or Meterpreter virus, we strongly recommend downloading alternative security software and double-checking the machine. At the moment, the Meterpreter-virus related files are identified as malicious by 38 AV engines out of 61. Other detection names indicate the virus as:
- VBA:Downloader-EON [Trj] (AVG)
- VB:Trojan.Valyria.447 (B) (Emsisoft)
- Troj/FatRat-F (Sophos)
- VB:Trojan.Valyria.447 (BitDefender)
- VBA/TrojanDropper.Agent.UR (ESET)
- Trojan:Win32/Meterpreter.gen!C (Windows Defender), etc.
If this Trojan/Win64.Meterpreter virus infiltrates the Windows machine, it performs malicious processes in the background and connects to the remote server to provide the criminals behind the trojan with the collected data. Usually, banking trojans[3] are provided with features recording keystrokes, stealing browser’s data, harvesting credentials, installing other malicious programs, injecting intrusive content on the web browsers, and more.
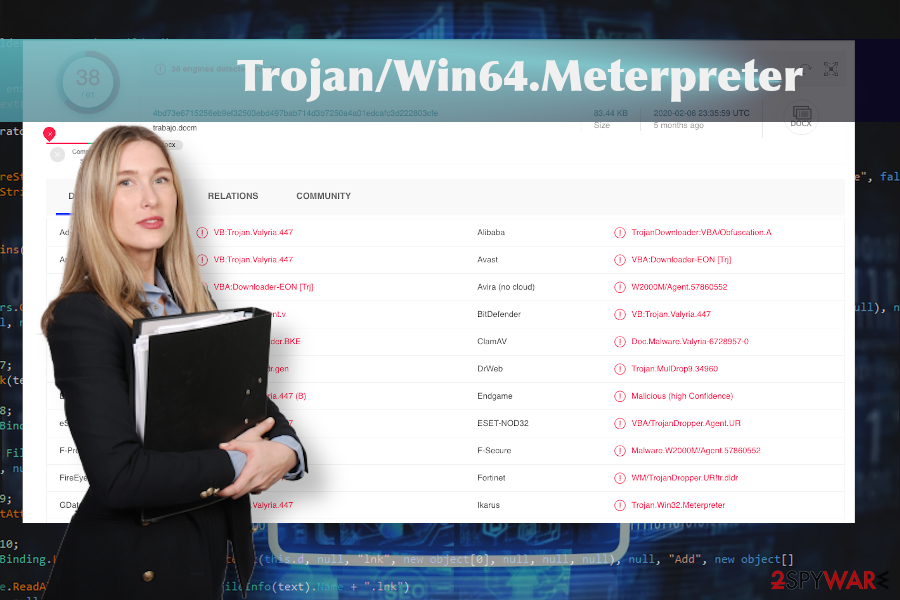
Trojan/Win64.Meterpreter related virus is detected by multiple AV tools

Trojan/Win64.Meterpreter related virus is detected by multiple AV tools
Nevertheless, if you have already noticed a suspicious system’s behavior and the symptoms of possible trojan infection, arm yourself with the reputable anti-virus, restart your machine into Safe Mode with Networking, and run a full scan to remove Trojan/Win64.Meterpreter from the machine completely.
You should remove Trojan/Win64.Meterpreter as soon as possible to prevent the malware from causing the damage. The longer it is kept, the more files or functions it can modify. Finally, check the system for any possible damage using a reliable optimization utility, such as Reimage Reimage Cleaner Intego. This program has been developed with an intention to maintain Windows OS stability and performance, so take advantage of its advanced scanner regularly.
Infected files and sites often work as a mediator between Trojans and the target machine
Most of the malicious programs that run in the background aim at performing some stealing and hacking activities. Thus, it would be naive that they will ask for permission to get installed directly. To hide malicious infections and inject them suspiciously hackers render various social engineering strategies.
One of the most common ways to seed Trojans onto the machines of unsuspecting users is to complement system cracks, keygens, or other pirated content with the trojan payload. If such a file is downloaded and launched, the virus is activated and starts performing in the background. For this reason, experts[4] recommend staying away from illegal software that is available on torrent sites, p2p platforms, pirating services, and other shady sites.
In addition, domains that are not certified do not feature a secure HTTPs protocol and proof of being protected is an easy target for hackers. Such domains can be injected with malicious javascript codes that can display fake software updates, display infected ads, click-to-download commercials, and other dangerous content.
Trojan/Win64.Meterpreter is a detection of a malicious Meterpreter credential-stealing trojan

Trojan/Win64.Meterpreter is a detection of a malicious Meterpreter credential-stealing trojan
Automatic Trojan/Win64.Meterpreter removal is the only way that can help
It’s important to remove Trojan/Win64.Meterpreter virus if the AV tool warns you about its presence unless you don’t mind hackers to be recording your credentials. Running SpyHunter 5Combo Cleaner or Malwarebytes while in Safe Mode with Networking should help to delete the malicious trojan from the system and other programs that pose danger to your PC’s security.
In fact, Safe Mode is not crucial, so you can try to launch the scanner while in the regular mode. However, there’s a high probability that the Trojan/Win64.Meterpreter removal simply won’t work because the AV tool may be left idle by malicious virus-related processes. In this case, Safe Mode disables non-core system files and allows launching the anti-virus.
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. It is a hassle when your website is protected from suspicious connections and unauthorized IP addresses.
The best solution for creating a tighter network could be a dedicated/fixed IP address. If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for server or network manager that need to monitor connections and activities. This is how you bypass some of the authentications factors and can remotely use your banking accounts without triggering suspicious with each login.
VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world. It is better to clock the access to your website from different IP addresses. So you can keep the project safe and secure when you have the dedicated IP address VPN and protected access to the content management system.
While much of the data can be accidentally deleted due to various circumstances, malware is also one of the main culprits that can cause loss of pictures, documents, videos, and other important files. Potentially unwanted programs may clear files that keep the application from running smoothly.
More serious malware infections lead to significant data loss when your documents, system files, or images get locked. Ransomware is the one that is focused on such functions, so your device gets useless without access to needed data. Even though there is little to no possibility to recover after file-locking threats, some applications have features for such recovery in the system.
In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
This entry was posted on 2020-07-08 at 04:56 and is filed under Trojans, Viruses.

