Sodinokibi ransomware – a major player in current cybercriminal scene that threatens to publish exfoliated data if ransom demands are not fulfilled
Sodinokibi ransomware virus is the threat that comes to the system via security vulnerabilities and encrypts photos, videos or documents.

Sodinokibi ransomware virus is the threat that comes to the system via security vulnerabilities and encrypts photos, videos or documents.
Sodinokibi, also known as REvil or Sodin, is a file-locking malware that uses Salsa20 and AES to lock data on the targeted machine, appending a random file extension[1] in the process, and then demanding high sums of ransoms (between $2,000 to $5,000) in Bitcoin which range. A new ransomware family was first spotted in late April 2019 by Cisco Talos researchers,[2], and soon became one of the major players in the illegal ransom-demanding business.
Just as its predecessor – the retired GandCrab – Sodinokibi runs a ransomware-as-a-service (RaaS) scheme, where various smaller criminal groups can pick a code of the malware and distribute it via various channels. In most cases, the affiliates retain from 60% or 70% of profits from ransom payments. Due to this, the malware used a variety of attack vectors, such as Oracle WebLogic vulnerability CVE-2019-2725.[3][4] and later, Rig exploit kit, weak Remote Desktop connections, spam email attachments, and other methods.
Once on the system, Sodinokibi virus gains system privileges, shuts down several processes, encrypts files on local and networked drives, extracts sensitive information, among other changes, and delivers a ransom note Random-ID-HOW-TO-DECRYPT.txt/Random-ID-readme.txt. Victims are then directed to the Tor site, where they can gain access to all type of support for the ransom execution process.
Similarly to GandCrab, Sodinokibi would not attack users that originate “friendly” countries (mostly ex-Soviet states) by checking their keyboard language. Additionally, since January 2020, malware authors started threatening business owners with disclosing sensitive company data online if ransom demands are not fulfilled.[5]
| Name | Sodinokibi ransomware |
|---|---|
| Alternative names | REvil, Sodin |
| Type | Cryptovirus, file locking malware |
| Detection | Malware/Win32.RL_Generic.R267978, Trojan.MalPack.GS, Ransom:Win32/Sodinokibi.A, Trojan-Ransom.Win32.Sodin.a, Trojan.Encoder.28004, Win32:MalwareX-gen [Trj], A Variant Of Win32/Kryptik.GSON, W32.Ransom.Gen (Virus Total results) |
| Development and operation | The developer, who goes by the name UNKN or Unknown and is a member of ex-GandGrab group, operates Ransomware-as-a-Service (RaaS) scheme |
| Privilege escalation | Malware abuses kernel privilege escalation vulnerability CVE-2018-8453 to gain system level access |
| Persistence | Uninstalls anti-malware solutions and executes 64-bit code in 32-bit environment (Heaven’s Gate technique) |
| Distribution | Exploit kits, vulnerabilities, spam email attachments, Managed Service Provider hacks, unprotected Remote Desktop (RDP) connections, etc. |
| File marker | An appendix is a combination of alphanumeric characters that is also used in the name of the ransom note and for other purposes. Example of an encrypted file: picture.jpg.fpe8183b2u |
| Ransom note | file-marker-HOW-TO-DECRYPT.txt or file-marker-readme.txt |
| Elimination | For a secure malware removal, a network-wide scan should be performed using advanced anti-malware software |
| System fix | To fix damaged Windows system files and repair Windows registry, use tools like Reimage Reimage Cleaner Intego |
Initially being distributed via CVE-2019-2725, the malware soon spread globally – the Sodinokibi virus campaign was spotted when fake foreclosure messages delivered around Germany containing malicious macro-filled documents. Emails with subject lines “Announcement of foreclosure” (Ankündigung der Zwangsvollstreckung) works with the help of typical phishing techniques – recipients simply do not recognize the deception on time and open a malicious document, beginning the infection routine immediately.
As a secondary payload, threat actors also used GandCrab 5.2 as a means to receive double profits. While Sodinokibi ransomware remains undecryptable without backups, GandCrab has been long decrypted by security experts at Bitdefender, so there is no point in wasting money and paying the ransom.
Before starting file encryption, Sodinokibi ransomware will perform a variety of checks and changes on the system. These alterations are performed in order to help cybercriminals reach their goals, and malware is continually updated with new functions.
- Deletes Shadow Volume Copies to prevent data recovery from automatic Windows backups.
- Disables Windows startup repair function.
- Escalates privileges to those of a SYSTEM with the help of vulnerability CVE-2018-8453.
- Disables anti-malware software, which can complicate Sodinokibi ransomware removal.
- Disengages from systems that are located in one of the following countries: Armenia, Azerbaijan, Belarus, Estonia, Georgia, Iran, Kazakhstan, Kyrgyzstan, Latvia, Lithuania, Romania, Russia, Syria, Tajikistan, Turkmenistan, Ukraine, Uzbekistan.
- Changes the desktop wallpaper with a customized .bmp image that tells the victim to access the ransom note.
- Modifies Windows registry to retain persistence.
- Establishes an HTTP connection with dozens of different domains for communication purposes, etc.
Once the file encryption process starts, Sodinokibi ransomware marks encoded files on the targeted computer and all the connected networks with a random file extension and prevent user access. The ransom note, which follows the naming pattern [user ID]HOW-TO-DECRYPT.txt or [user ID]readme.txt pattern, is also delivered, which explains to victims what to do next.
Sodinokibi message delivers the following information:
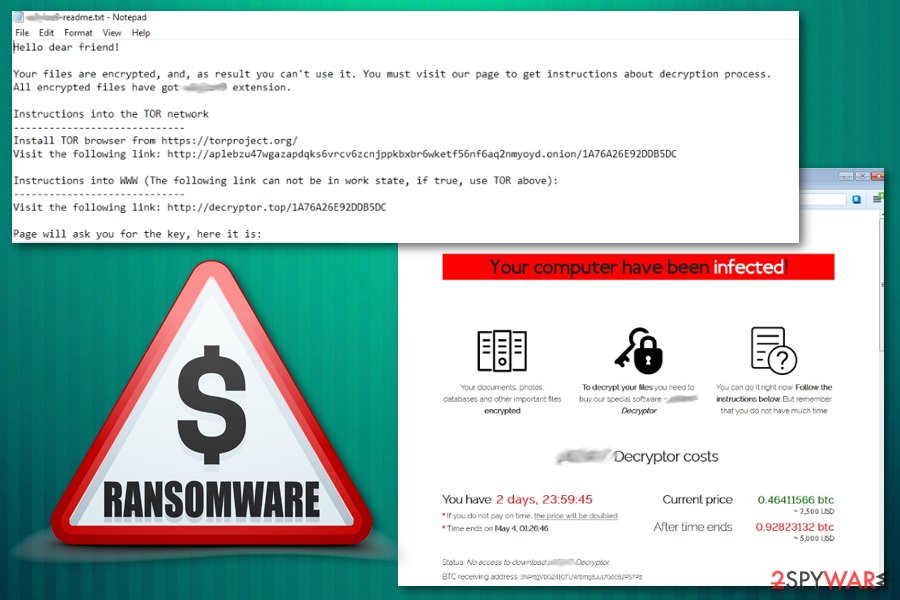
Hello dear friend! Your files are encrypted, and, as result you can't use it. You must visit our page to get instructions about decryption process.
All encrypted files have got * extension. Instructions into the TOR network
-----------------------------
Install TOR browser from https://torproject.org/
Visit the following link: http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/[id] Instructions into WWW (The following link can not be in work state, if true, use TOR above):
-----------------------------
Visit the following link: http://decryptor.top/[id] Page will ask you for the key, here it is:
***
Once the victim follows the suggested instructions to access the website provided by Sodinokibi ransomware developers, the page asks to enter the unique victims’ ID and provided key. Then, the ransomware page displays a particular ransom amount and address to create the Bitcoin wallet needed for the payment transfer.
Sodinokibi ransomware is the cryptovirus that is distributed when the attacker exploits the zero-day vulnerability and later installs another ransomware.

Sodinokibi ransomware is the cryptovirus that is distributed when the attacker exploits the zero-day vulnerability and later installs another ransomware.
Criminals behind Sodinokibi give 48 or 72 hours for this payment for the alleged decryption tool. In case the demands are not fulfilled within 72 hours, the ransom is doubled and can reach sums that are higher than $5,000. While playing criminals is highly discouraged by most security researchers, it might be the only choice victims have in some cases. Nonetheless, keep in mind that, due to an extensive affiliate program, there is no guarantee that that Sodinokibi ransomware decryptor will be provided even after the payment is made.
Sodinokibi: the ever-changing distribution methods
According to the latest news, cybersecurity experts found out that fake Booking.com emails have been spreading Sodinokibi ransomware.[6] This Booking.com virus spreads via email spam that includes malicious macros embedded into suspicious documents. Those who open the document and allow content to be executed will infect their machine with a variant of Sodinokibi.
Soon after, researchers spotted another campaign of Sodinokibi, which was now delivered with the help of malvertising that utilizes the Rig exploit kit.[7] Keep in mind that outdated apps make the system vulnerable to such exploits. So, you should always make sure that your programs are regularly updated, this also includes your Windows operating system. If you take these precautionary measures seriously, you might be able to avoid Sodinokibi ransomware successfully.
Sodinokibi ransomware removal should be performed as soon as possible because it affects the system significantly besides the fact that it installs another cryptovirus or different malware programs later on. Fortunately, antivirus engines can detect this threat and remove it altogether. Since AV engine databases differ from program to program there are many different detection names:
- Trojan.GenericKD.31927370;
- HEUR/AGEN.1041110;
- Ransom.Sodinokibi;
- Win32.Trojan.Raas.Auto;
- etc.[8]
You must remove Sodinokibi ransomware from the machine with a professional anti-malware tool. However, since the malware might disable security software, you should access Safe Mode with networking Since this is the threat that mostly affects Windows devices, use Reimage Reimage Cleaner Intego for the system repair and cleaning functions.
May 2019 Sodinokibi ransomware campaign targeted German users
In May 2019, a new Sodinokibi malspam campaign targeting Germany was spotted by security researchers. These emails are boobytrapped with malicious macros, which begin chain events that result in malware infection. CFC Underwriting cyber security incident responder Tom Bennett said the following about the campaign:[9]
Ransomware groups tend to target people in the Anglosphere, who are seen as able to pay and deserving of what they get. They tend not to target poorer countries
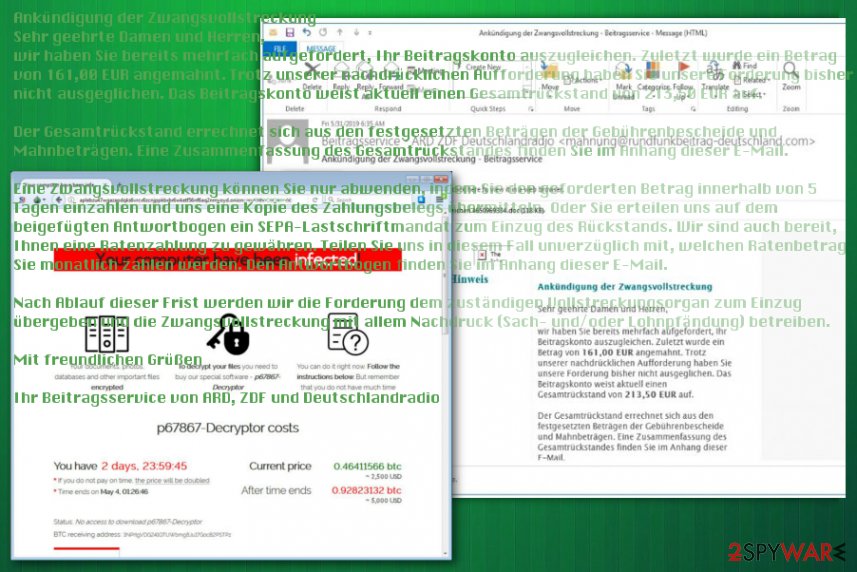

By using emails with the subject line – “Announcement of foreclosure” (Ankündigung der Zwangsvollstreckung), malicious actors trick people into opening the infected document. The email contains a lengthy message about alleged cyberattacks and company data compromise. The attachments that were clipped to the email are often named as “Mahnbescheid – Antwortbogen – Aktenzeichen 4650969334.doc,” or similar.
Unlike previous Sodinokibi campaigns, this version of malware used the “Living off the Land” technique, which utilizes legitimate Windows processes and APIs to avoid detection.
The initial email faking to be a foreclosure notification delivers the following (in German):
Ankündigung der Zwangsvollstreckung
Sehr geehrte Damen und Herren,
wir haben Sie bereits mehrfach aufgefordert, Ihr Beitragskonto auszugleichen. Zuletzt wurde ein Betrag von 161,00 EUR angemahnt. Trotz unserer nachdrücklichen Aufforderung haben Sie unsere Forderung bisher nicht ausgeglichen. Das Beitragskonto weist aktuell einen Gesamtrückstand von 213,50 EUR auf.Der Gesamtrückstand errechnet sich aus den festgesetzten Beträgen der Gebührenbescheide und Mahnbeträgen. Eine Zusammenfassung des Gesamtrückstandes finden Sie im Anhang dieser E-Mail.
Eine Zwangsvollstreckung können Sie nur abwenden, indem Sie den geforderten Betrag innerhalb von 5 Tagen einzahlen und uns eine Kopie des Zahlungsbelegs übermitteln. Oder Sie erteilen uns auf dem beigefügten Antwortbogen ein SEPA-Lastschriftmandat zum Einzug des Rückstands. Wir sind auch bereit, Ihnen eine Ratenzahlung zu gewähren. Teilen Sie uns in diesem Fall unverzüglich mit, welchen Ratenbetrag Sie monatlich zahlen werden. Den Antwortbogen finden Sie im Anhang dieser E-Mail.
Nach Ablauf dieser Frist werden wir die Forderung dem zuständigen Vollstreckungsorgan zum Einzug übergeben und die Zwangsvollstreckung mit allem Nachdruck (Sach- und/oder Lohnpfändung) betreiben.
Mit freundlichen Grüßen
Ihr Beitragsservice von ARD, ZDF und Deutschlandradio
Known versions of Sodinokibi ransomware
REvil ransomware
REvil ransomware is one of the versions that uses Salsa20 encryption algorithm and changes the original code of the files on the system to have a reason for $2500 ransom demands. It generates a random extension and marks those files with such appendix, which indicates which data was encrypted.
The initial money demand appears on the desktop wallpaper or in the text file, in most cases, named after the random file marker or HOW-TO-DECRYPT.txt. From there, you may be redirected to Tor or another browser that shows the ransom amount determined for you in particular and guides you through the payment. However, paying the ransom is not recommended. This threat spreads around by getting on the system through particular vulnerabilities on Windows devices (CVE-2019-2725, CVE-2018-8453), or by using exploit kits such as Rig.
Sodin ransomware
Sodin ransomware – version of the Sodinokibi that uses random file marker too, although .mc9530 extension was spotted several times. Since this is the same family, it also shows the ransom amount on the browser window when the payment suggestion appears. This particular version is demanding a ransom that starts at $2,000 but can go up to $5,000 in Bitcoin for the alleged file recovery.
You shouldn’t trust these people in any instance because cybercriminals are focusing on file encryption and money extortion. The more unique fact about this particular version of the threat is the specific region that ransomware targets. It was reported a few times that the Asia-Pacific region is mainly targeted but researchers also saw victims in Europe, North America, and Latin America too.
Sodinokibi is known to have REvil and Sodin versions out in the wild already.

Sodinokibi is known to have REvil and Sodin versions out in the wild already.
RaaS-based malware uses multiple attack vectors
Attackers use the WebLogic vulnerability to deliver this ransomware. Unauthorized access and exploitation of such flaws occur when the patching is not performed in time – the updates should be applied as soon as possible by the server administrators.
This particular vulnerability was recently discovered and reported as the Oracle WebLogic Server that allows criminals to gain access to the targeted server and install malware manually. It was also used to spread bots, trojans, and other malware to launch further attacks.
Other common crypto-malware distribution techniques can be used to spread ransomware – they include spam email messages with attached files, infected documents, and hyperlinks leading to direct downloads of the malicious payload.
Such infiltration can be avoided by deleting emails from suspicious senders or eliminating file attachments instead of immediately downloading them and opening on the machine. If you are asked to enable content to trigger macros, be aware that the document is infected, and once you do, the malware infection process will be initiated.
Remove Sodinokibi ransomware and patch the related vulnerability to prevent further intrusions
Sodinokibi ransomware virus is distributed using the recently discovered vulnerability. However, the patch for this flaw was also released, so use it to secure the server and avoid infiltration of ransomware and other malware that may exploit the vulnerability.[10]
When it comes to Sodinokibi ransomware removal, we recommend getting a reputable anti-malware program and scanning the machine fully. This will ensure that all malware components are eliminated, and Windows operates normally again. In case the OS behaves erratically after termination, use PC repair software Reimage Reimage Cleaner Intego.
If you have no working backups, you should not remove Sodinokibi ransomware before you make a copy of the encrypted files. Otherwise, the application of third-party tools can render them permanently damaged, and even a working decryptor would not help in that case.
Visual guide for Sodinokibi ransomware removal
Sodinokibi ransomware is an advanced file locking threat that performs an array of Windows OS modifications and might even sometimes damage vital system files. Threat actors behind the malware are constantly improving infection and operation tendencies in order to expand the campaigns for maximum profits.
As the Sodinokibi file virus can disable anti-malware software, accessing Safe Mode with networking might be the only way to remove malware without many difficulties. If you are a novice when it comes to IT and malware removal, we suggest you check the visual guide we compiled to help users with cryptovirus infections such as Sodinokibi.
This entry was posted on 2020-04-21 at 06:29 and is filed under Ransomware, Viruses.

