Sekhmet ransomware – crypto-malware that targets organizations and threatens to publish confidential information online
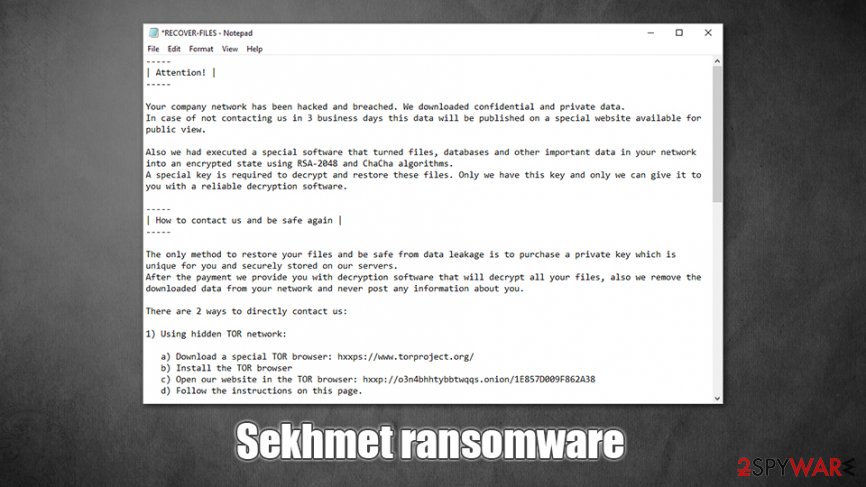
Sekhmet ransomware is malware that encrypts all personal files with a combination of RSA and ChaCha and then demands Bitcoin payment for their redemption

Sekhmet ransomware is malware that encrypts all personal files with a combination of RSA and ChaCha and then demands Bitcoin payment for their redemption
Sekhmet ransomware is a new crypto-locking virus strain that was first spotted by cybersecurity experts in late March 2020. Just like similar malware of such type, it uses a strong encryption algorithm (this time, a combination of RSA and ChaCha) to lock pictures, music, videos, documents, databases, and other files on local and networked drives for blackmail purposes. Each of the locked files is appended with a random extension (e.g., .WNgh, .DtiV) and can no longer be accessed, unless a ransom in Bitcoin from Sekhmet virus authors.
Threat actors behind the Sekhmet ransomware strain joined the terrifying trend among cybercriminals – they harvest sensitive information during the infection process and then threaten to publish it on a specific portal online, which would be accessible for everybody. Allegedly, victims only have three business days before that happens. To recover the Sekhmet ransomware decryption tool, users have to either visit a TOR site or visit a skhmet.top website. All this information is conveniently compiled into ransom RECOVER-FILES.txt, which is dropped on the infected machines’ desktops.
| Name | Sekhmet ransomware |
| Type | File locking virus, crypto-malware |
| Related files | f55.dll, sekhmet.dll.exe, regsvr32.exe |
| Encryption method | All non-system files are encrypted with the help of RSA-2048 + ChaCha |
| File appendix | Unlike most ransomware, Sekhmet appends a random extension to each of the files on the same device. Example of two different files on the same system: picture1.jpg.WNgh and picture2.jpg.DtiV |
| Ransom note | RECOVER-FILES.txt |
| Contact | Malicious actors indicate two methods of contact: either by downloading a TOR client and visiting a provided link or by visiting sekhmet.top website |
| Threat | Hackers claim that they harvested sensitive information from the infected computers and will publish it if the ransom is not paid within three days |
| Data recovery | Without secure backups, retrieving data is almost impossible. Alternative ways for file recovery include using third-party software or trying to use built-in Windows backups. Paying cybercriminals might be the only choice in some cases (although it is not recommended) |
| Malware removal | To get rid of malware, users need to perform a network-wide scan with reputable anti-malware software |
| System fix | Malware can often damage Windows system files, resulting in crashes and other issues. To fix virus damage, employ repair tools like Reimage Reimage Cleaner Intego |
Since Sekhmet ransomware targets organizations mainly, it is clear that attack vectors do not include random targets. To perform a targeted attack, malware developers often choose to use spear-phishing[1] emails or insecure Remote Desktop connections. The latter can be reached simply by scanning the internet for all RDP connections that use a default TCP/UDP port 3389.
Due to the targeted nature of the attacks, threat actors behind Sekhmet virus could be able to disable implemented defenses, such as employed anti-malware tools. Nevertheless, most up-to-date security solutions might be the tools one needs to detect unauthorized access. There many AVs that detect malware under the following names:[2]
- Trojan.GenericKD.42872102
- Win32:Malware-gen
- Ransom.Win32.SEKHMET.A
- Win32.Trojan.Cryptor.Pgwr
- Trojan-Ransom.Win32.Cryptor.ddu
- Trojan.GenericKD.42872102 (B), etc.
Sekhmet ransomware removal can also be achieved with the help of anti-malware tools, although it could be possible that the infection neutralized itself after performing file encryption. Many ransomware is programmed to do so, although it is best to check the machine(s) with security software regardless. If you remove Sekhmet ransomware before backing up the encrypted data, it may get compromised for good, however.
Sekhmet ransomware does not immediately begin the file encryption process, as many system modifications need to be performed before that. For example, the Windows registry is modified, remote server connections established, malicious files dropped, Shadow Volume Copies, and multiple other files deleted, etc. For a startup, regsvr32.exe process is used – malware boots each time the Windows is started. These Sekhmet ransomware changes can sometimes damage the system, although it can be later reverted with tools like Reimage Reimage Cleaner Intego.
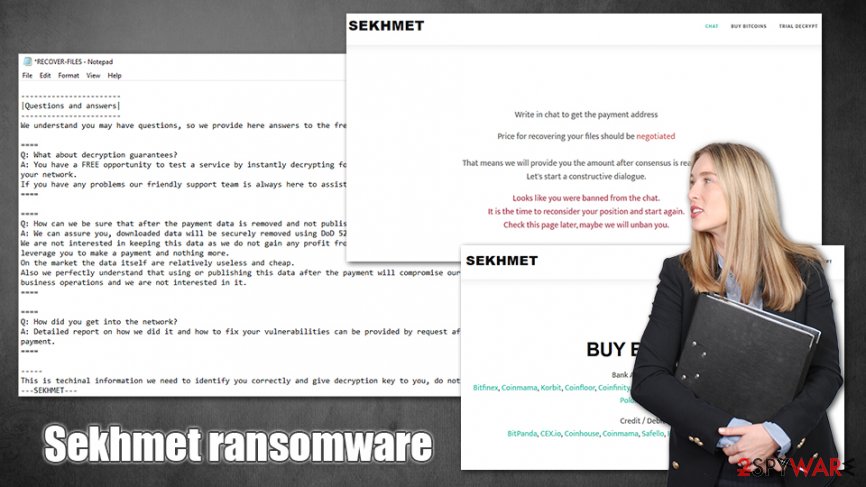
Sekhmet ransomware is a file locking virus that mainly targets companies

Sekhmet ransomware is a file locking virus that mainly targets companies
With the system preparations complete, the Sekhmet virus begins to look for files on local and networked drives. It targets the most commonly used types, such as .pdf, .jpg, .zip, .mkv, .doc, and many others. With the help of sophisticated encryption, the malware locks all data and appends a different extension to each file, making them unusable.
After that, a lengthy ransom note is dropped, which explains that Sekhmet ransomware encrypted all files and, allegedly, the only way to recover data is by paying cybercriminals. Here’s an extract from the note:
| Attention! |
—–Your company network has been hacked and breached. We downloaded confidential and private data.
In case of not contacting us in 3 business days this data will be published on a special website available for public view.Also we had executed a special software that turned files, databases and other important data in your network into an encrypted state using RSA-2048 and ChaCha algorithms.
A special key is required to decrypt and restore these files. Only we have this key and only we can give it to you with a reliable decryption software.—–
| How to contact us and be safe again |
—–The only method to restore your files and be safe from data leakage is to purchase a private key which is unique for you and securely stored on our servers.
After the payment we provide you with decryption software that will decrypt all your files, also we remove the downloaded data from your network and never post any information about you.There are 2 ways to directly contact us:
1) Using hidden TOR network:
a) Download a special TOR browser: hxxps://www.torproject.org/
b) Install the TOR browser
c) Open our website in the TOR browser: hxxp://o3n4bhhtybbtwqqs.onion/1E857D009F862A38
d) Follow the instructions on this page.2) If you have any problems connecting or using TOR network
a) Open our website: hxxps://sekhmet.top/1E857D009F862A38
b) Follow the instructions on this pageOn this web site, you will get instructions on how to make a free decryption test and how to pay.
Also it has a live chat with our operators and support team.
It is yet unknown who is behind Sekhmet ransomware strain, but it seems like these criminals are serious about what they do. Looking at ransom note and the way communication system is established, it becomes clear that these people are not new in ransomware scene, and they are aiming to infect organizations and businesses for increased ransom payments.
Keeping that in mind, sensitive information disclosure becomes even more devastating than the loss of files, in some cases. For a company to have its secrets revealed possibly to other malicious actors or competitors might prove detrimental, resulting in the company shut down. This is why Sekhmet ransomware might be so efficient in collecting ransom payments, as business owners do not want to lose their source of income.
Ransomware prevention measures
It is currently unknown that type of distribution methods ransomware developers are using, although, considering the nature of the ransom note, they most likely rely on targeted attacks. In most cases, these are executed via unprotected RDP connections or phishing emails. Nevertheless, it does not mean that cybercriminals cannot use other methods, including:
- web injects
- fake updates
- exploits
- pirated software installers
- etc.
Therefore, to ensure the safety of the company, staff training and dedicated IT teams are essential for cybersecurity. It is especially important to secure remote desktop connections with the help of such tools like VPN, as well as strong passwords and correct settings.
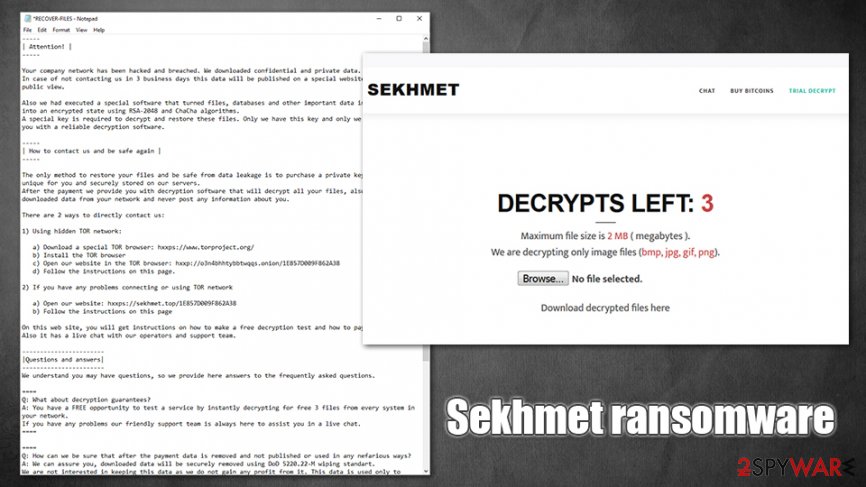
Sekhmet ransomware virus authors offer users to either download Tor client and visit particular site or access the payment panel via sekhmet.top

Sekhmet ransomware virus authors offer users to either download Tor client and visit particular site or access the payment panel via sekhmet.top
Additionally, email attachments should never be allowed to run macro function, i.e., “Allow content.” Typically, PDF or .doc files, boobytrapped with malicious macros, are employed to execute commands and begin the infection routine. Also, with the help of spoofing techniques,[3] hackers might make it look that the email is coming from within the company, so caution should be practiced at all times.
Finally, comprehensive anti-malware software, regular backups, system patching, and other safety measures should always be practiced.
Get rid of Sekhmet ransomware and try to recover your data
It is up to you to decide whether you want to pay for Sekhmet ransomware decryptor, although keep in mind that it is very risky – cybercriminals behind the strain might simply ignore victims as soon as Bitcoins are transferred. Therefore, security experts advise against paying criminals, although the fact that they could disclose sensitive company information publicly is a considerable threat. The tactic has been developed by Maze ransomware authors and is now being adopted across other strains.
If you decide not to pay, you have to ensure that Sekhmet ransomware removal is performed correctly. Since malware drops a multitude of files across the system and changes various Windows settings, it is best to be done with the help of anti-malware software.
In case you have struggled when trying to remove Sekhmet ransomware, you can access Safe Mode with Networking and perform a full scan from there. Only then you should attempt to recover your data, although do not forget to backup the encrypted files first.
This entry was posted on 2020-04-02 at 03:54 and is filed under Ransomware, Viruses.

