Search Daemon is a browser hijacker targeting Mac users in particular
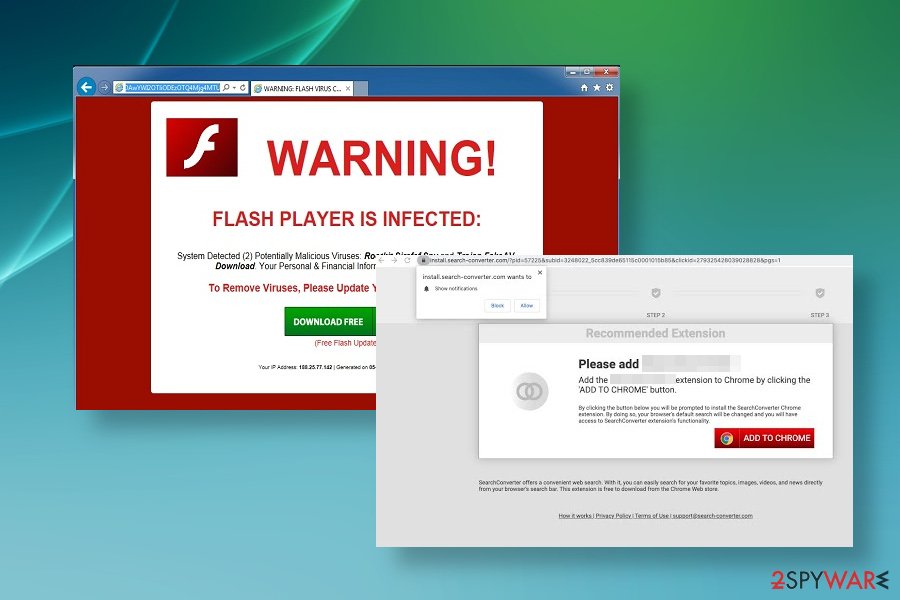

Search Daemon is the name of a browser-injectable Mac malware[1] that is typically distributed via freeware. The misleading name should not be associated with the virtual drive and optical disc known as Daemon. In fact, some references can be traced since the browser hijacker might be distributed bundled with some of the Daemon versions that are accessible for free on third-party download sources.
The Search Daemon Mac virus – that’s the main reference to this tool that can be found on various cybersecurity blogs and forums. Although it’s non-malicious, intrusive behavioral traits induce users to call it malicious. Upon installation, which, by the way, happens via freeware bundles and users are not aware of the upcoming browser’s hijack, the start page and search engine on Safari, Google Chrome, Mozilla Firefox, and others are replaced by an unknown search, such as search.anysearch.com, search.yahoo.com, searchmine.net, Search.myspeedtestxp.com, and others.
Such a web browser’s modifications are usually initiated for marketing purposes, i.e. pay-per-click revenue and traffic boosting. Therefore, the site aims at triggering continuous Search Daemon redirects to the sites of its affiliates. These redirects can be initiated in several ways, i.e. displaying sponsored ads on random sites, injecting scripts onto the browser’s settings, which automatically reroutes the traffic once the user types in the search query or URL address. Anyway, these redirects are potentially dangerous due to the uncontrolled third-party content.
| Name | Search Daemon |
| Type | Browser hijacker |
| Sub-Type | Potentially Unwanted Program (PUP) |
| Compatibility | Targeting Mac OS users |
| Distribution | The browser-based malware is typically distributed via freeware downloads |
| Compatible web browsers | It can be injected onto Safari, Google Chrome, Mozilla Firefox, Opera, and other browsers used on Macs. Nevertheless, it can be installed on Internet Explorer, Microsoft Edge, and other Windows browsers as well |
| Symptoms | Altered start page, search engine, new tab URL, and other settings; Unknown extensions installed on the web browser; Intrusive ads generated on random websites; Ongoing redirects via Search Daemon servers. |
| Danger | The extension is not dangerous itself, though it can expose your machine to potentially dangerous third-party sites engaged in malware dissemination or phishing |
| Elimination | Manual and automatic removal options are possible. A free guide is given at the end of the article |
| Fixing malware damage | Browser hijackers are potentially dangerous applications that are capable of initiating some system changes. To fix any unwanted changes, we recommend using Reimage Reimage Cleaner Intego repair tool |
Do not download the Search Daemon app for Mac no matter what features it claims to have. Note that it’s a heavily ad-supported application that is capable of hijacking web browsers and initiating various advertising campaigns to gain revenue.
Even though it may have a direct download on sources like Mac App Store[2], usually is spread bundled with freeware and shareware as an “optional download” that is supposed to provide additional features (faster web browsing experience, filtered web search results, handy quick access links, etc.). Unfortunately, upon the installation the Search Daemon virus may alter web browser’s settings in an unwanted way and initiate pre-default commands without your permission:
- This PUP may change a default start page, search engine, and new tab window;
- Typing search queries into the search bar automatically redirect the browser to suspicious third-party sites;
- Random websites display banner ads with the obviously sponsored content;
- The web browser may load websites asking you to submit personally identifiable information (name, email address, home address, telephone number, etc.) to claim a prize or similar;
- You may notice personalized ads (corresponding to your recent web searches). That’s because this application may use tracking cookies to gain information about your browsing preferences and harvest browsing history.
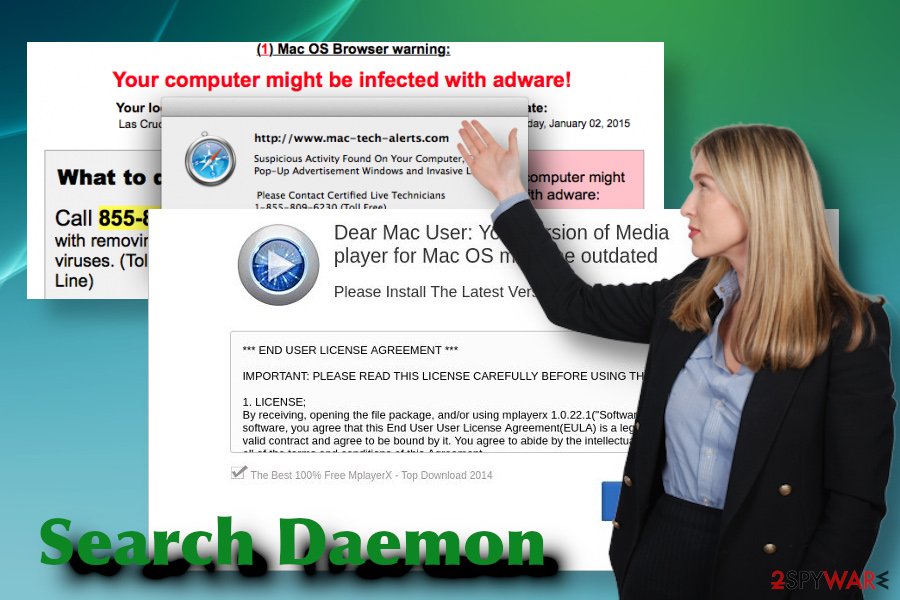
Search Daemon is a deceptive third-party app that seeks advertising revenue

Search Daemon is a deceptive third-party app that seeks advertising revenue
Therefore, even though the application is not harmful, it’s important to understand that it is used for affiliate marketing. It means that it’s purpose – to promote third-party content and, thus, gain commission for that. For this reason, there’s no reason to postpone Search Daemon removal.
Those who have installed the app bundle with freeware, NoVirus.lt[3] experts recommend the automatic Search Daemon removal option. Freeware bundles usually consist of several constituents, so there’s a risk that your machine contains more than one unwanted application. You can use any security software that is designed to protect and clean Macs.
Once you remove Search Daemon from Mac, a thorough system scan with Reimage Reimage Cleaner Intego is recommended as an additional precautionary measure ensuring that the system is fully optimized. PUPs tend to inject supporting objects into the system’s libraries, which may cause slowdowns or crashes over time.
Do not skip steps during the installation of free apps
Software bundling is a legitimate distribution method that is widely used by many app developers. However, this method is not entirely fair, especially when untrustworthy parties are misusing it. Bundling allows developers to disguise setup windows that inform users about the installation of additional apps. The problem is that these apps are pre-selected, so inadequate disclosure leads to the automatic installation of the whole bundle right after clicking the “Finish” button.
Although bundling is useful in its nature as it allows people to use new apps for free, most of the promoted apps are ad-supported and used for their own purposes. Upon installation, these apps tend to hijack web browsers, generate intrusive third-party apps, trigger web-browser redirects, and other unwanted behavior.
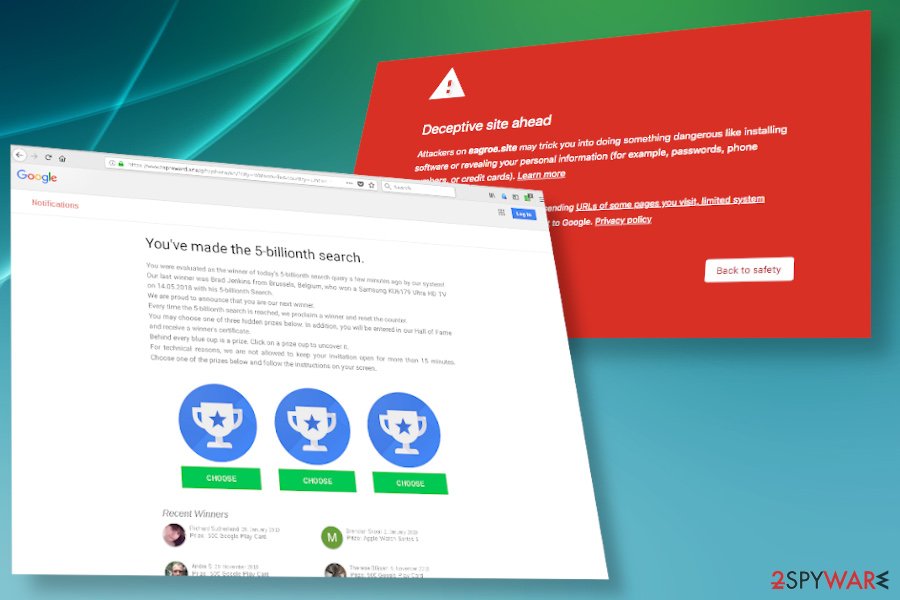
Search Daemon may fill web browser’s pages with intrusive ads that misled users into downloading malware

Search Daemon may fill web browser’s pages with intrusive ads that misled users into downloading malware
Therefore, to prevent this from happening, it’s important to select the Advanced or Custom installation technique. Then carefully monitor the installation steps, paying attention to pre-selected and grayed out checkboxes. Deselect all additional applications before clicking the Next button, thus opting out of unwanted apps.
Delete Search Daemon app or other potentially unwanted programs from Mac
The Search Daemon Mac virus is a term used by many people. However, its behavior is more like a potentially unwanted program as it cannot harm the machines itself, except display misleading content. Therefore, experts recommend removing this app to prevent redirect to dangerous websites that may be involved in malware distribution.
For the Search Daemon removal, you can either use a professional anti-malware tool or rely on a manual removal guide that is listed at the end of this article. Make sure to perform all steps in the right order. Unwanted apps may be installed in various locations, so check all possible folders and delete each suspicious application.
However, it might be slightly complicated to remove Search Daemon virus from the Mac system and web browsers as it may install various components within libraries and remain active even after the removal of the main installer. That’s why automatic removal using an anti-malware tool is recommended. Besides, a scan with Reimage Reimage Cleaner Intego utility might solve future problems due to overfilled registries.
You may remove virus damage with a help of Reimage Reimage Cleaner Intego. SpyHunter 5Combo Cleaner and Malwarebytes are recommended to detect potentially unwanted programs and viruses with all their files and registry entries that are related to them.
When you work on the domain, site, blog, or different project that requires constant management, content creation, or coding, you may need to connect to the server and content management service more often. It is a hassle when your website is protected from suspicious connections and unauthorized IP addresses.
The best solution for creating a tighter network could be a dedicated/fixed IP address. If you make your IP address static and set to your device, you can connect to the CMS from any location and do not create any additional issues for server or network manager that need to monitor connections and activities. This is how you bypass some of the authentications factors and can remotely use your banking accounts without triggering suspicious with each login.
VPN software providers like Private Internet Access can help you with such settings and offer the option to control the online reputation and manage projects easily from any part of the world. It is better to clock the access to your website from different IP addresses. So you can keep the project safe and secure when you have the dedicated IP address VPN and protected access to the content management system.
While much of the data can be accidentally deleted due to various circumstances, malware is also one of the main culprits that can cause loss of pictures, documents, videos, and other important files. Potentially unwanted programs may clear files that keep the application from running smoothly.
More serious malware infections lead to significant data loss when your documents, system files, or images get locked. Ransomware is the one that is focused on such functions, so your device gets useless without access to needed data. Even though there is little to no possibility to recover after file-locking threats, some applications have features for such recovery in the system.
In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.

