Corona-virus-map.com.exe – a malicious file that exploits the COVID-19 outbreak to infect users with malware
Corona-virus-map.com.exe is an executable file that runs in the background of Windows operating systems and can be found on the Task Manager. The file indicates that the computer has been infected with the well-known Trojan AZORult, and users are in danger of having their personal information, such as credit card information, banking data, login credentials, etc., stolen by cybercriminals.
Malicious actors behind the Corona-virus-map.com.exe virus are abusing the coronavirus pandemic status around the globe, which was declared by the World Health Organization (WHO) on March 12, 2020. Naturally, concerned people are trying to track the outbreak and find out about the infections in a local area, which prompts them to look for online tools. Unfortunately, Corona-virus-map.com.exe, which provides users with an interactive COVID-19 infection map, secretly gathers user sensitive information in the background.
| Name | Corona-virus-map.com.exe |
| Also known as | Coronavirus map |
| Related | Corona.exe, Bin.exe |
| Type | Malicious files, Trojan |
| Related malware | AZORult banking Trojan, which was first spotted making rounds in 2016 |
| Peculiarities | This version of the AZORult was being sold for $200-$700 on the underground forums |
| File size | 3.26 MB[1] |
| Distribution | The main source for the malicious software distribution was found to be a website www.corona-virus-map.com, although researchers say that spam emails are also used to deliver malware |
| Activity | Just as other versions of AZORult, this virus is programmed to steal various information from the infected machine, including credentials, credit card numbers, cookies, crypto-wallet data, etc. |
| Dangers | The prolonged functionality of malware on the machine can result in various negative ramifications, including financial losses, installation of other malicious software, and even identity theft |
| Termination | To remove the infection from the computer, users need to perform a full system scan with a sophisticated anti-malware software, such as SpyHunter 5Combo Cleaner or Malwarebytes |
| Further actions | Victims should monitor their online banking in order to avoid unsolicited transactions and reset all the passwords that they used during the infection. Also, the browser reset should be performed to get rid of pre-set settings. Finally, if Windows suffers from various malfunctions, Reimage Reimage Cleaner Intego could fix the damaged registry entries and other issues to repair the machine |
This version of AZORult Trojan that runs Corona-virus-map.com.exe executable was reportedly found being sold on the underground hacking forums, with prices being as low as $200, although buyers that wish to include a working certificate are asked to pay $700 for the kit. Threat actors selling the Coronavirus map described it as follows:[2]
It loads [a] fully working online map of Corona Virus infected areas and other data. Map is resizable, interactive, and has real time data from World Health Organization and other sources. Users will think that PreLoader is actually a map, so they will open it and will spread it to their friends and it goes viral!
Unsurprisingly, Corona-virus-map.com.exe virus was found by security researchers on a website www.corona-virus-map.com. Nevertheless, security experts also speculate that the malicious payload is also delivered with the help of malicious spam email attachments.
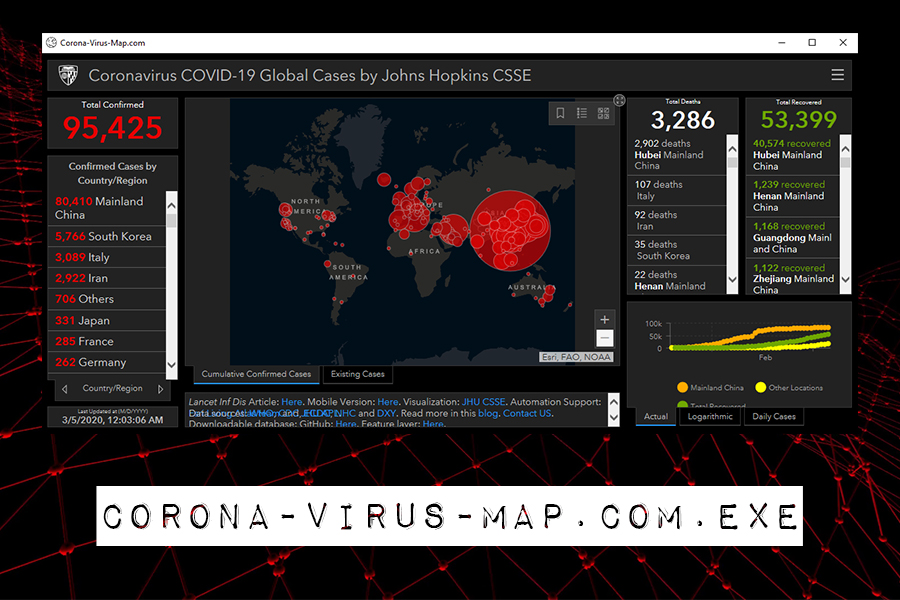
It looks rather convincing, as it displays viral outbreaks marking them with different sizes red does around the world map. Additionally, it also includes statistics that are relevant to the coronavirus outbreak, such as a number of total infected and recovered cases, as well as death count. As its source, Corona-virus-map.com.exe names Johns Hopkins University’s Center for Systems Science and Engineering.
For the Corona-virus-map.com.exe malware to be executed, the victims have to have Java software installed on the system, as the Corona map is based on Java. Those who use even patched versions of Java will not avoid the exploitation of the malicious map.
Once executed, Corona-virus-map.com.exe will create another binary under the name of Corona.exe and placed into several different locations inside the %AppData% folder. This process then executes several other processes, including bin.exe, .timeout.exe, and build.exe. Additionally, the malware will perform several other system modifications, including alternation to the Windows registry, to begin its malicious tasks. To revert these changes after Corona-virus-map.com.exe removal, we recommend using Reimage Reimage Cleaner Intego.
According to security researchers from Reason, Corona-virus-map.com.exe operates as follows:[3]
When the victim gets infected, the malware extracts data and creates a unique ID of the victim’s workstation. It then applies XOR encryption using the generated ID. This ID is used to tag the workstation in order to start C2 communication. The C2 server responds with configuration data, which contains target web browser names, web browser path information, API names, sqlite3 queries, and legitimate DLLs.
In addition, malware can steal various other data, including Steam account credentials, crypto-wallet data, browser cookies, and much more. This data is later sent over to malicious actors inside a file PasswordList.txt via the Command & Control server.
Those who run sophisticated and powerful anti-malware programs can catch and remove Corona-virus-map.com.exe virus from their systems. According to Virus Total, almost 60 different engines recognize the file under the following names:[3]
- Trojan.Agent.Wacatac
- Malware@#1z88bc8nipk8n
- Trojan:Win32/Covitse!MSR
- Trojan[PSW]/Win32.AZORult
- Troj/MSIL-NZP
- Trojan.AzorUlt.CoronaMap
- Trojan.GenericKD.33504379
- Win32:Trojan-gen, etc.
Note that deleting Corona-virus-map.com.exe manually will not bring any results, as the malware makes changes all over the system, creates new scheduled tasks, and modifies the Windows registry. However, it is crucial to remove the Coronavirus map malware as soon as possible, as personal safety is at a high risk of being compromised.
Be careful when employing random tools from the internet
Cybercriminals are always trying to abuse the latest news, popular events, and even pandemics. Without a doubt, COVID-19 is a hot topic right now that affected the lives of most people all over the world in one way or another. Therefore, the problem is highly sensitive, although it does not stop cybercriminals from proceeding with their illegal business ideas.
Coronavirus map may seem like a simple app that could help users track the outbreak, providing the most important statistics. The fact that victims are provided the functional feature, while a malicious program is launched in the background, will prevent many users from suspecting anything sinister.
Therefore, you should be more careful online, and only trust official sources for tracking various events or virus outbreaks. Ensure that your system is equipped with most advanced security software – it can repel the deceptive attacks like these.
However, you should also keep in mind that cybercriminals might deliver AZORult or any other malware in multiple other ways, including spam emails, exploits, web injects, fake updates, software cracks, etc. Hence, remember to keep your eyes open at all times when browsing the web or checking your email.
Terminate Corona-virus-map.com.exe malware from your machine
To remove Corona-virus-map.com.exe from your computer, terminating the file manually will not suffice. The infection process is much more sophisticated than that, and removing just one file will achieve nothing. As mentioned before, malware substantially modifies the Windows registry, imports malicious files, establishes network communication, creates new services, etc. Thus, for a comprehensive Corona-virus-map.com.exe removal, employ anti-malware software can recognize this threat.
Because the Corona-virus-map.com.exe virus brings in a banking Trojan, it is essential to take further actions after removing it from the infected machine. You should immediately change your passwords on various accounts, such as email, Steam, online banking, etc. Additionally, you should also cancel your credit card in case of unsolicited transactions starts flooding it.
This entry was posted on 2020-03-18 at 07:24 and is filed under Files, Spyware related.
