ONIX ransomware – a malware form that comes from Major ransomware and adds the .ONIX appendix next to each filename after the encryption process
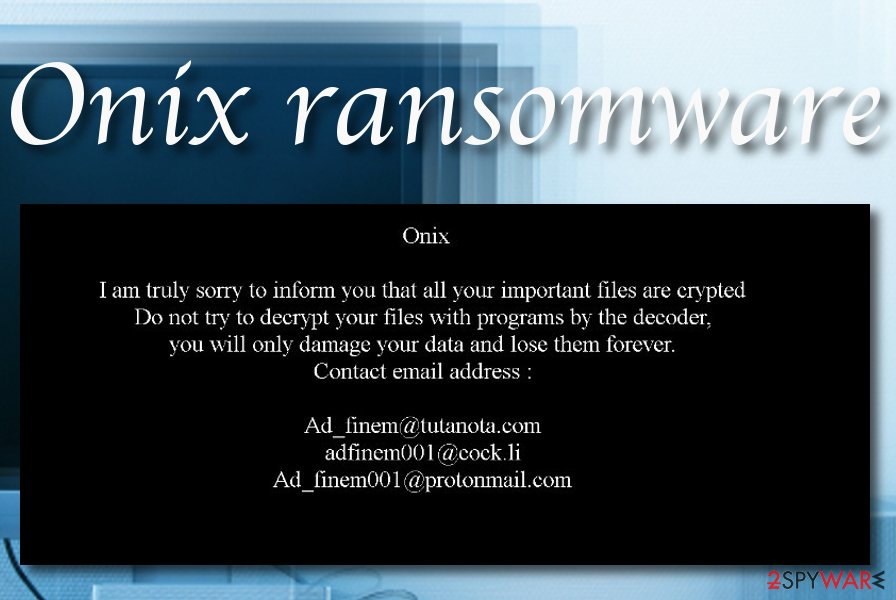
ONIX ransomware – a virtual threat that replaces the default computer wallpaper with the ransom note and also provides the ransom-demanding message in an HTML format

ONIX ransomware – a virtual threat that replaces the default computer wallpaper with the ransom note and also provides the ransom-demanding message in an HTML format
ONIX ransomware is a virtual parasite that has been discovered to come from Major ransomware family. The first to announce about this ransomware infection on Twitter was a computer security researcher named Amigo-A.[1] The dangerous malware enters Windows computer systems unknowingly and aims to lock up all the documents and files that are placed on the device by marking all of them with the .ONIX appendix. For the encryption, ONIX ransomware employs ciphers such as AES, RSA, or SHA which hold specific codes that differ for each infected computer.
Right after that, the ransomware virus provides ransom demands via TRY_TO_READ.html message and also changes the desktop’s background to the ransom note. The messages warn users not to try to unlock files by themselves as this can relate in permanent data loss. However, the main goal of ONIX ransomware is to encourage users to write via [email protected], [email protected], and [email protected] email addresses and discuss all the ransom price matters with the cybercriminals.
| Name | ONIX ransomware |
|---|---|
| Type | Ransomware virus/malware |
| Appendix | Once all of the files are locked, the ransomware virus appends the .ONIX extension to each filename of encrypted data |
| Ransom note | The virtual parasite provides the ransom note in the TRY_TO_READ.html message format and also replaces the default computer background as the ransom message |
| Cipher | Developers employ encryption ciphers such as AES, RSA, or SHA for locking up files. Each of this code differs for every computer |
| Spreading | Most of the time, ransomware viruses are delivered through email spam, malicious attachments, infectious advertisements, software cracks, and hacked RDP |
| Founder | Amigo-A |
| Family | This dangerous virus belongs to the Major ransomware family |
| Removal | If you have been dealing with the malware lately, you should not postpone its removal process. Try to get rid of the parasite with the help of reliable antimalware software |
| Fix software | If you have discovered any damage on your Windows computer system, you might have a chance of repairing corrupted areas by downloading and employing Reimage Reimage Cleaner |
ONIX ransomware is a dangerous malware string that has been detected as a virus by 58 antivirus engines out of the total 71. According to VirusTotal information,[2] some of the detection names include ML.Attribute.HighConfidence, Win32:Trojan-gen, Gen:Heur.Ransom.Imps.1 (B), A Variant Of Win32/Filecoder.NSN, Ransom:Win32/Crowti.P!MSR, and others.
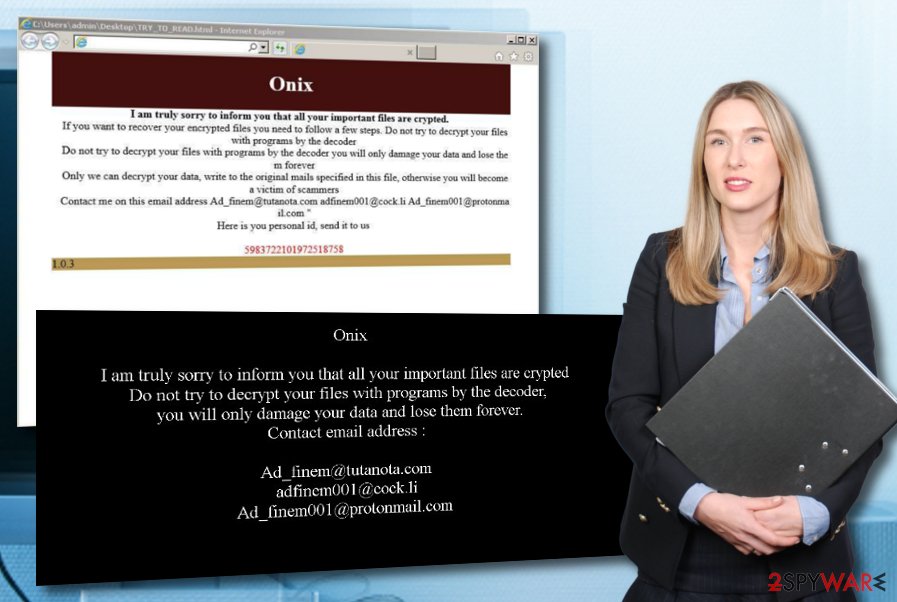
ONIX virus uses stealth distribution techniques for appearing on the targeted computer system. This malware infects Windows operating systems only and looks for people who are using the English language. This is also the language in which the TRY_TO_READ.html ransom message is written in:
Onix
I am truly sorry to inform you that all your important files are crypted.
If you want to recover your encrypted files you need to follow a few steps. Do not try to decrypt your files with programs by the decoder
Do not try to decrypt your files with programs by the decoder you will only damage your data and lose them forever
Only we can decrypt your data, write to the original mails specified in this file, otherwise you will become a victim of scammers
Contact me on this email address [email protected] [email protected] [email protected] ”
Here is you personal id, send it to us
5983722101972518758
1.0.3
ONIX ransomware manipulates locations such as the Windows Registry and Task Manager in order to fill these areas with malicious processes and keys. All of these tasks are planted to help the malware to operate smoother and reach its goals.
For example, ONIX ransomware might disable your antivirus protection to avoid getting detected and to stay in your computer system for a longer period of time. This way the program could prevent some particular software from deleting the malware itself and all the malicious components that it has brought to the computer system.
Furthermore, ONIX ransomware includes some type of an executable to the Windows computer that scans the entire device for encryptable files and documents. This happens in certain periods of time, for example, half an hour, an hour, and so on in order to make sure that all components were properly locked by the malware.
When ONIX ransomware applies the .ONIX encryption appendix to all of the files and documents found, the content gets locked and cannot be opened properly anymore. The only way to reverse the data back to its previous position is to get the decryption tool that would work. However, we suggest denying the option of buying the tool from the cybercriminals as these people might ask for inadequate amounts of money.
ONIX virus is a damaging virus that can be distributed through email spam messages and their infectious attachments, software cracks, malvertising, etc.

ONIX virus is a damaging virus that can be distributed through email spam messages and their infectious attachments, software cracks, malvertising, etc.
ONIX ransomware developers do not provide any particular information about the ransom demands, however, all of the conditions are likely to be discussed via email. We recommend avoiding any type of communication with the criminals. You might not even notice how they will scam you and run off with your money.
Most of the time, malicious actors are likely to urge large amounts of money starting anywhere from $100 and ending up with $2500 or even more. Always be careful with demands that come from malware such as ONIX ransomware and overthink everything twice before deciding whether the price is worth to pay or not.
Keep in mind that you are likely to be asked for cryptocurrency transfers by ONIX ransomware such as Bitcoin. These types of payments allow the cybercriminals to stay untrackable and anonymous so no one could discover the transactions.
ONIX ransomware might try to harden the data recovery process for the victims by running the vssadmin.exe delete shadows /all /Quiet command via PowerShell. This way the malware will erase the Shadow Copies of all of the encrypted data and the users will not be able to employ software that could restore at least some of the locked files with the help of the deleted Shadow Copies.[3]
To add, ONIX ransomware might target the Windows hosts file and aim to totally wreck them for their own purposes. This way the virus seeks to prevent the victim from accessing security-related networks, websites, and forums, where he/she could get reliable information on the malware removal process and data recovery task.

Furthermore, ONIX ransomware acts as a backdoor for other malware forms. The ransom-demanding threat makes the Windows computer vulnerable to other infections and increases the risk of getting attacked by dangerous virtual parasites such as Trojan viruses, spyware, worms, and others.
ONIX ransomware removal is the first step you should take the same minute you find the ransomware virus operating on your computer system. Keep in mind that you should not try to eliminate the cyber threat on your own as you can make damaging mistakes and hurt your computer system even more.
When you remove ONIX ransomware and all the bogus products that the malware has brought with the help of antimalware software, you should start looking for possible damage that might have been performed on your Windows computer. If you discover any affected areas, try repairing them with the help of software such as Reimage Reimage Cleaner .
Note that you need to uninstall ONIX ransomware before you start taking any data recovery steps, otherwise, all of your files will be encrypted again. If you have terminated the cyber threat properly, you can start opting for file restoring solutions some of which we have provided at the end of this article.
Different techniques used for ransomware distribution
Cybersecurity experts from NoVirus.uk[4] state that ransomware-related payload gets onto Windows computer systems through email spam and the malicious attachments that come clipped to the suspicious messages. Crooks pretend to be from reliable healthcare, shipping, or banking companies.
You should not open any attached component without scanning it with antimalware software. Also, if the email message has a hyperlink included, you should not enter it if the content of the email and the sender looks suspicious to you. Things to search for:
- A bogus sender email address such as [email protected].
- The content is filled with grammar mistakes.
- You have received an email from a non-existing company.
Furthermore, ransomware infections can be pushed through malicious adverts that are also known as malvertising. The same can happen with hyperlinks that have a tendency to appear on third-party networks. The main thing to do here is to avoid entering suspicious-looking websites and closing all bogus pages that appear.
To add, ransomware viruses can get distributed through software cracks that are placed in peer-to-peer networks such as The Pirate Bay. Regarding this fact, use only reliable downloading sources for getting your wanted products and services.
Also, malicious actors search for vulnerable RDP configuration (one that includes weak passwords or none at all) and hack the port or brute force the password into the system and connect to the computer remotely. So, make sure that you always think of strong and reliable passwords that include some symbols, letters, and numbers.
Know about ONIX ransomware removal possibilities
If you are looking for ways to remove ONIX ransomware from your Windows machine, you have come to the right place. Our security experts claim that you should not try to eliminate the malware on your own as you might skip some malicious components and accidentally leave them on the computer system.
ONIX ransomware removal should be completed with the help of reliable antimalware software that is capable of detecting and eliminating the ransomware virus from your device. Afterward, scan the entire system for possible damage with SpyHunter 5Combo Cleaner or Malwarebytes. If these tools find any compromised areas, you can try repairing them with Reimage Reimage Cleaner .
When you uninstall ONIX ransomware properly, it is time to start thinking about data recovery possibilities. Rather than taking risks to get scammed and paying the cybercriminals, you should try some other file restoring alternatives like the ones that we have provided at the end of this article.
Keep in mind that if ONIX ransomware has damaged your Windows hosts files, these components need to be eliminated too, otherwise, access to cybersecurity websites might still remain blocked even if the ransomware virus is no longer active.
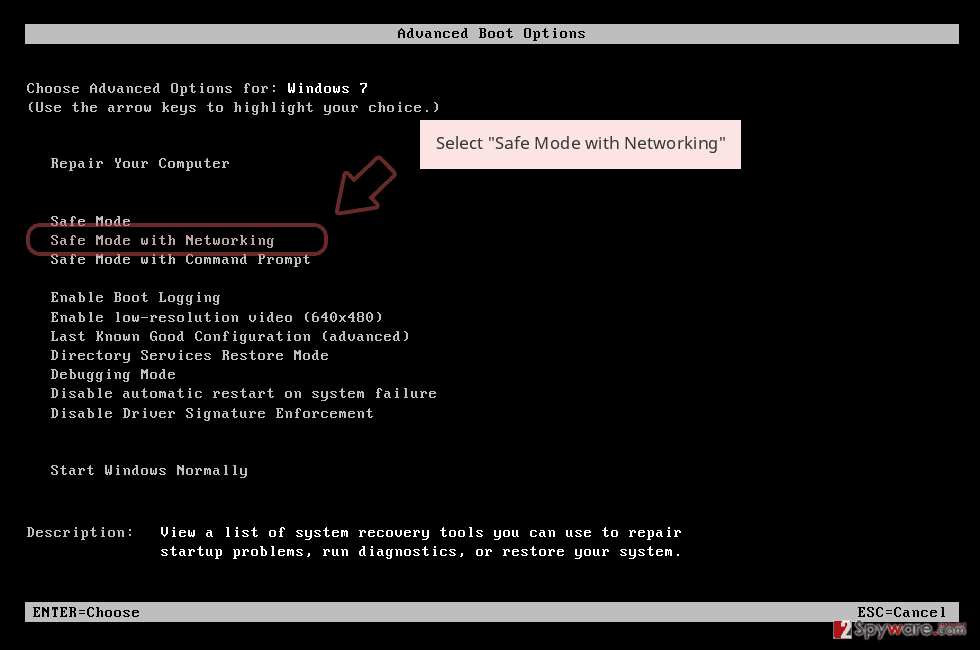
Remove ONIX using Safe Mode with Networking
To deactivate malicious settings on your Windows computer system and reverse the device back to how it was before the ransomware attack, you should follow the below-provided steps and boot your machine in Safe Mode with Networking.
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
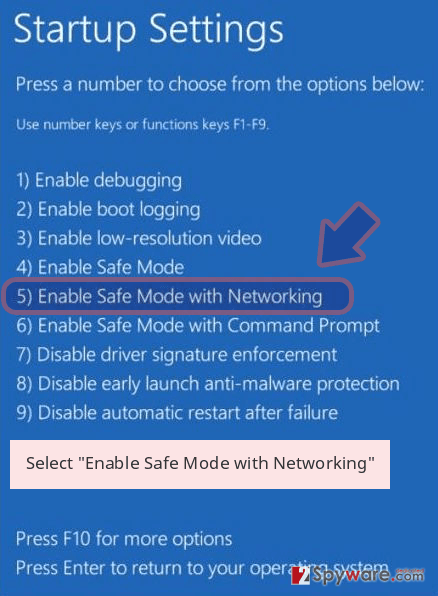
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete ONIX removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove ONIX using System Restore
To disable the malware on your device and get rid of all malicious processes that were brought by the ransomware virus, use the following instructions and activate the System Restore feature.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove ONIX from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If you have discovered files with the .ONIX appendix, do not rush to pay the crooks the price that they demand as all of this can be just a scam and will bring profit for the cybercriminals only. Rather than taking such as risk, you should try other data recovery alternatives like the ones that are provided below.
If your files are encrypted by ONIX, you can use several methods to restore them:
Using Data Recovery Pro might help you with file restoring purposes.
If you have been looking for a tool that would help you to recover the files and documents that were encrypted by the ransomware virus, you can try employing this piece of software.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by ONIX ransomware;
- Restore them.
Windows Previous Versions feature might be helpful software for file restore.
If you have enabled the System Restore function on your Windows computer, you can give this tool a try.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Shadow Explorer might be able to recover some data.
You can try using this piece of software for restoring at least some of your files. However, keep in mind that this tool might not work if the ransomware virus has eliminated or permanently damaged the Shadow Volume Copies of your locked data.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Cybersecurity experts are currently working on the .ONIX files decryption tool.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from ONIX and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner , SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2020-02-17 at 06:05 and is filed under Ransomware, Viruses.

