Nodera ransomware – newly-discovered malware that aims to attack Node.JS platforms
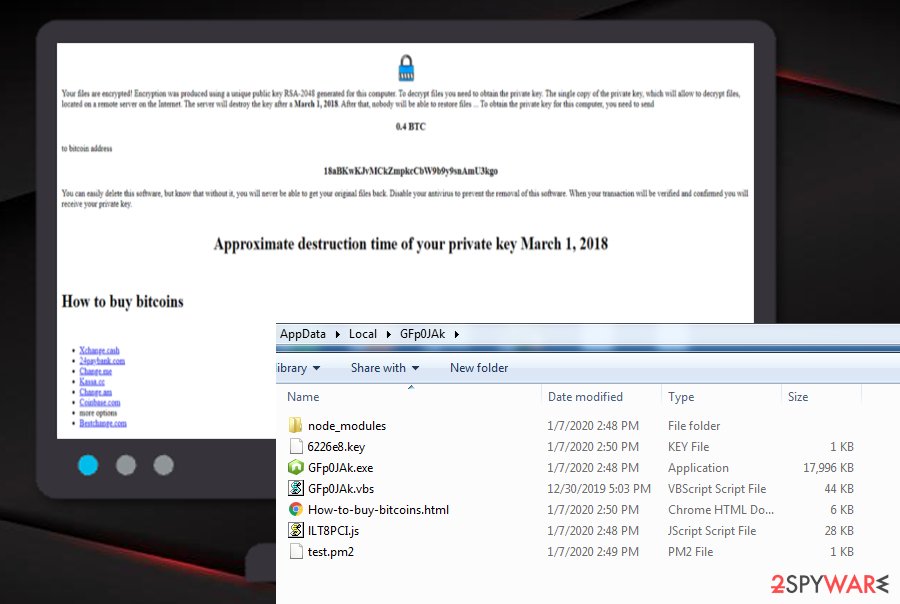
Nodera ransomware – malware that urges for 0.04 BTC in exchange for the decryption tool
Nodera ransomware is an advanced cyber threat that targets Node.JS servers and appears on the Windows operating system. Even though this is the current OS that remains vulnerable to these types of attacks, the malware developers can modify the operating module of the ransomware anytime and it might get capable of infecting other types of OS such as Linux and Mac some of which also support the Node.JS server. Node.JS is described as a run-time environment that holds all components necessary for executing any type of software that is written in JavaScript programming language.[1]
When Nodera ransomware plants itself on the computer system completely, it starts searching for encryptable files that hold specific extensions. Then, the malware executes the RSA-4096 encryption[2] cipher and starts locking each data component found even though the cybercriminals claim in their text message that they are employing RSA 2048-bit encryption. Afterward, the ransomware will generate an extension (mostly, it will be .encrypted) and append it to each filename of the encrypted documents.
Continuously, Nodera virus pastes the ransom message named How-to-buy-bitcoins.html, in the AppData folder, which includes information on how to purchase Bitcoins for the price transfer. Also, the cyber threat will place a BAT file named Decrypt-your-files.bat, on the computer’s desktop, which is the decryptor that should be executed by activating various specifications after the criminals receive their Bitcoin payment.
| Name | Nodera ransomware |
|---|---|
| Category | Ransomware/malware |
| Target | This dangerous cyber threat targets Node.JS servers that are running on the Windows operating system. However, if the cybercriminals develop the malware even more, it can also start functioning on other OS such as Linux and macOS |
| Encryption | The ransomware claims that the encryption process executes the RSA-2048 algorithm when it truly uses a 4096-bit cipher. When all files are locked, a random appendix such as .encrypted is added to all the filenames |
| Ransom note/price | The malicious string includes the ransom note named How-to-buy-bitcoins.html in the AppData folder where the cybercriminals urge for a 0,04 Bitcoin transfer |
| Delivery | It is known that this ransomware virus is most commonly delivered through infectious HTA files and malvertising advertisements that are met on unsecured online sources |
| Related files/folders | Files: fs.js, package.json, polyfills.js, graceful-fs.js, legacy-streams.js, ILT8PCI.js, GFp0JAk.exe, node.exe. Folders: node_modules |
| Termination | This dangerous cyber threat can be eliminated by purchasing and launching antimalware software that is capable of dealing with such advanced viruses |
| Repair software | If you have discovered any compromised areas on your Windows operating system, Reimage Reimage Cleaner might help you to fix them |
Nodera ransomware is a severe computer infection that has been already deeply analyzed by Quick Heal security specialists. These people have discovered the Node.JS framework that was linked to the malware.[3] Such a specific fact was found very interesting as the misusage of such a platform is not common across threat developers.
Continuously, the cybersecurity specialists have discovered that the easiest way to get infected by Nodera ransomware is during online surfing sessions. The user can easily execute the malware by stepping on an infectious HTA file or clicking on malvertising-based advertisements that carry the malicious payload around the Internet.
When entering the targeted Windows computer system, Nodera ransomware creates a subfolder named node_modules that holds all the Node.JS-based libraries. Afterward, the malware tends to activate JavaScript content that can be done through the node.exe executable which is included as GFp0JAk.exe file in the %userprofile%\AppData\Local\GFp0JAk section.
Nodera ransomware is a dangerous malware form that targets Node.JS platforms on Windows computers
Slightly after that, Nodera ransomware fills the node_modules directory with the mentioned libraries that are named fs.js, package.json, polyfills.js, graceful-fs.js, and legacy-streams.js. However, the main script that is responsible for loading all ransomware-related tasks such as encryption of files is named ILT8PCI.js.
Afterward, Nodera ransomware scans all system directories instead of the C: drive for encryptable files and documents as its main targets are components that are created and included by the victim. Before the encryption process begins, the ransomware virus runs specific tasks that permanently delete the Shadow Copies of all encrypted files.
This way Nodera ransomware tries to harden the decryption process for the victims in case they try to recover some of their files by using alternative software. However, the ransom note claims that the only way to restore files properly is by purchasing the decryption tool from the cybercriminals before the software’s expiry date:
Your files are encrypted! Encryption was produced by using a unique public key RSA-2048 generated for this computer. To decrypt files you need to obtain the private key. The single copy of the private key, which will allow to decrypt files, located on a remote server on the Internet. The server will destroy the key after a March 1, 2018. After that, nobody will be able to restore files … To obtain the private key for this computer, you need to send
0,4 BTC
to bitcoin address
18aBKwKJvMCkZmpkcCbW9b9y9snAmU3kgo
You can easily delete this software, but know that without it, you will never be able to get your original files back. Disable your antivirus to prevent the removal of this software. When your transaction will be verified and confirmed you will receive your private key.
Our recommendation would be to decline any offers to pay the payment in order to release files from the prison of Nodera ransomware. Do not listen to the crooks’ urges to disable your antivirus protection and so on. It is not worth risking to pay an inadequate amount of money as there is a big chance that you will get scammed by these hackers.
As you can see, Node ransomware developers generate unique keys for each computer they target. Continuously, both encryption and decryption codes are stored on remote servers that are reachable for the owners only. However, there still are some great alternative options that can help you to recover some data without big payments.
What you should do is remove Nodera ransomware with the help of an antimalware product that is capable of dealing with this dangerous parasite. Additionally, when you are done with the malware and it is gone for good, you should go to the end of this article where we have provided data recovery techniques some of which might allow you to restore locked files.
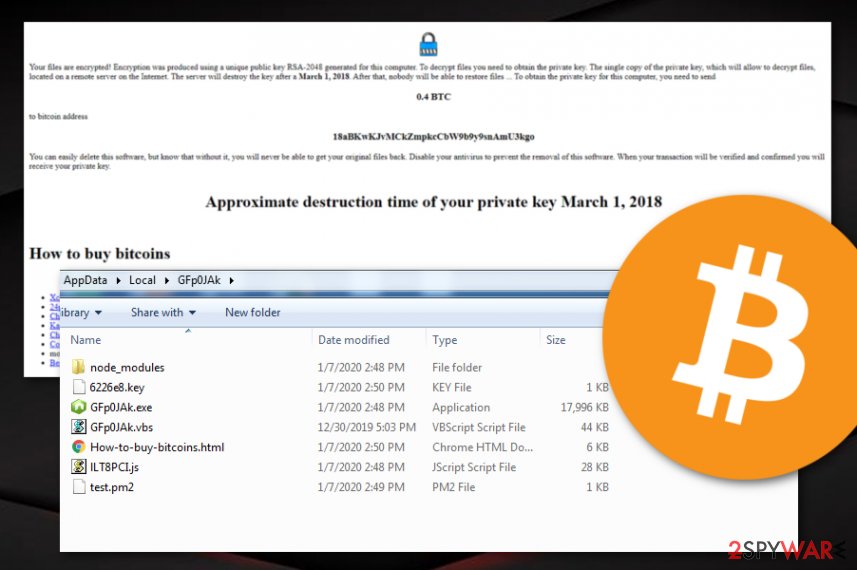
You have to be extremely careful with Nodera ransomware as it might also be programmed to bring other virtual parasites up to the surface. There are some ransomware viruses that distribute other malware such as Trojan viruses and these dangerous infections can relate to permanent data loss, software corruption, identity theft, money swindling, etc.
Nodera ransomware removal should be your primary goal while dealing with this cyber threat. The process will be a complex task to complete, that is why we do not recommend trying to eliminate the virus on your own. It will likely have also placed unwanted files and entries in your Windows Task Manager, Windows Registry, and other locations.
If you are having some trouble with uninstalling Nodera ransomware from your Windows operating system, the malware might be running specific processes to block antimalware software and interrupt the removal process. For this purpose, you should reboot your computer system in Safe Mode with Networking or activate the System Restore feature.
Malvertising is a popular way of spreading ransomware viruses
Computer specialists from NoVirus.uk[4] state that ransomware developers think of various ways how to distribute their products. One popular technique is known as malvertising. The execution of the malicious payload happens when a user steps on a malicious advertisement while browsing on an unsafe website.
Also, you might get ransomware downloaded from files and hyperlinks that you access online. A tip would be not to click on everything that looks attractive to you, avoid visiting unsecured sources, and use antivirus protection with safe-browsing.
Continuously, ransomware viruses often get delivered through email spam. Criminals pretend to be from reliable shipping organizations such as FedEx or DHL and aim to trick users by providing malicious attachments as “shipping information”. Be aware of random messages that fall into your inbox, always identify the sender, and do not open unknown files.
Furthermore, ransomware can get delivered through peer-to-peer networks such as The Pirate Bay, eMule, and BitTorrent that offer to download software cracks. These sources often get hacked and allow criminals to change the regular downloading links into ones that contain malicious products and services.
Get rid of Nodera ransomware ASAP
If you have been attacked by this virus lately, you have to remove Nodera ransomware as soon as possible before it causes any damage to your Windows computer system as it might bring other infections to your device too. The elimination process can be initiated with the help of antimalware software that is capable of deleting the parasite. Also, try using SpyHunter 5Combo Cleaner and Malwarebytes for detecting damaged areas on your computer and these tools find any compromised places, you can try initiating the fix process with another product such as Reimage Reimage Cleaner .
If you are having some trouble with the Nodera ransomware removal process it might be because the malware is evading antimalware detection and stopping you from terminating it. In this case, you should boot your Windows machine in Safe Mode with Networking or activate System Restore as shown in the below-provided instructions.
Additionally, if you are interested in data recovery techniques, there are also some methods added to the end of this article. We want to remind you all one more time that there is a big risk of getting scammed by Nodera ransomware developers so you should avoid paying the 0.04 Bitcoin ransom price, otherwise, you might face huge money losses for nothing.
Remove Nodera using Safe Mode with Networking
To diminish malicious processes on your Windows computer system and disable the ransomware virus, you should apply for the following steps that will allow you to boot your device in Safe Mode with Networking.
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
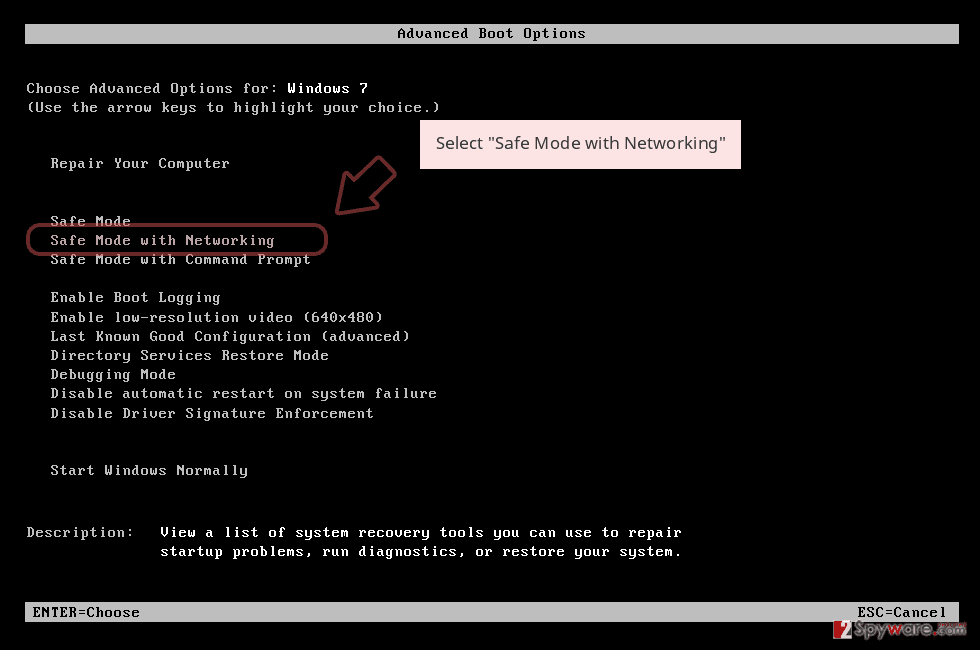
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
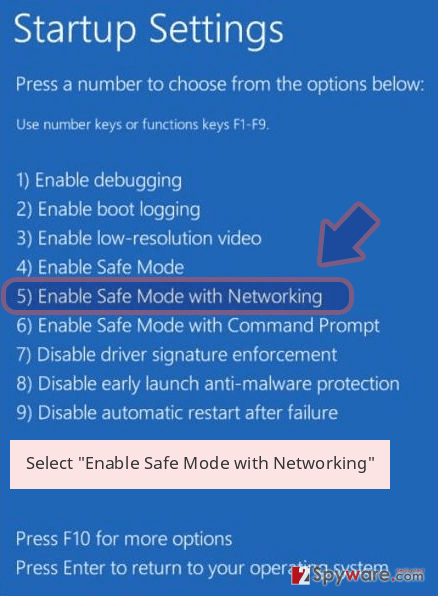
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete Nodera removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove Nodera using System Restore
To deactivate all the malware-laden tasks that were performed by the ransomware virus, you should opt for the System Restore feature. If you do not know how to activate such function, follow these steps.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Nodera from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If your files are encrypted by Nodera, you can use several methods to restore them:
Try employing Data Recovery Pro for file restoring.
If the ransomware virus has encrypted your files and documents, you can try to recover at least some of them by using this software instead of risking to get scammed by the hackers.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Nodera ransomware;
- Restore them.
Using Windows Previous Versions feature might help with data restoring.
If you have enabled the System Restore feature in the past, this type of technique might allow bringing some of your encrypted components back to their primary positions.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Shadow Explorer is also a tool for file recovery.
Even though this software might work great for other cases, this time the ransomware virus appears to permanently delete the Shadow Volume Copies of all encrypted data. Unfortunately, this piece of software does not function correctly without the Shadow Copies.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
At the time of writing, there is no official decrypter released for the files that got encrypted by Nodera ransomware virus.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Nodera and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner , SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2020-01-29 at 05:55 and is filed under Ransomware, Viruses.

