Nefilim ransomware – a file locking malware that threatens to publish the data publicly
Nefilim ransomware is a re-branded name of Nemty ransomware – it operates ransomware-as-a-service scheme for propagation

Nefilim ransomware is a re-branded name of Nemty ransomware – it operates ransomware-as-a-service scheme for propagation
Nefilim ransomware is a data locker that uses extortion tactics in order to make you hand over the money to cybercriminals. Just like most other ransomware, this virus locks all personal files with the help of the RSA + AES encryption algorithm[1] and then demands a ransom payment in Bitcoin cryptocurrency. Each of such encrypted files receives a .NEFILIM extension and can no longer be accessed without the generated key that is stored on cybercriminals’ C&C server.
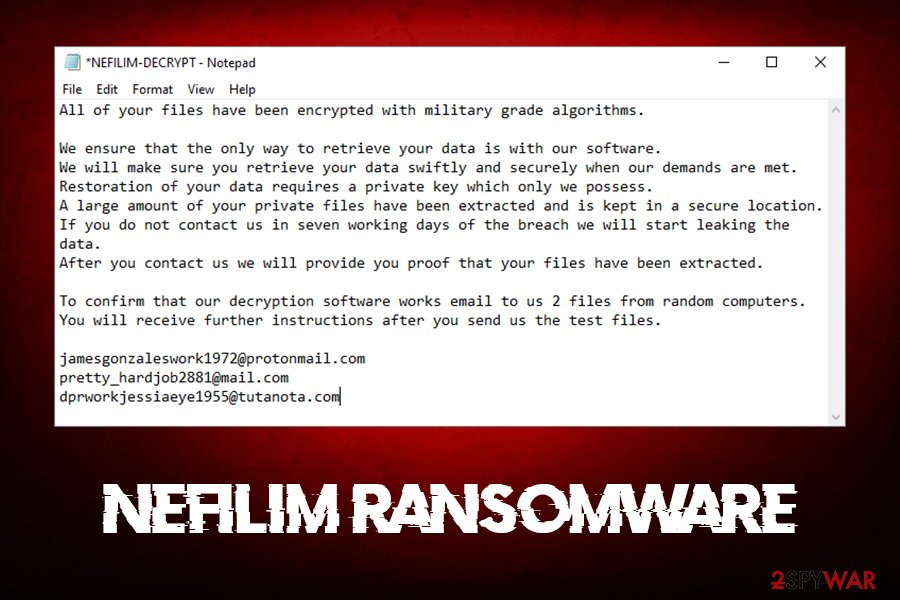
Additionally, the Nefilim virus also drops a ransom note NEFILIM-DECRYPT.txt, which explains what happened to the infected computer. In this note, crooks explain that they keep copies of all files on their servers. In case the ransom will not be paid within seven days, the data will be leaked and exposed online. This is a new tactic that increases the chances of a successful endeavor for cybercriminals.
For communication purposes, malicious actors ask victims to contact them via one of the following e-mails: [email protected], [email protected], or [email protected]. According to Nefilim ransomware developers, as soon as users send the email, they will be provided a proof cybercriminals indeed have copies of files.
| Name | Nefilim |
| Type | Ransomware, file locking virus |
| Encryption method | All local and networked files are encrypted with AES-128 + RSA-2048 cipher |
| A successor to | Nemty ransomware |
| File extension | All non-system and non-executable files are appended with .NEFILIM extension, e.g., a “picture.jpg” is turned into “picture.jpg.NEFILIM”. Another version of the ransomware uses .OFFWHITE! extension for encrypted data |
| Ransom note | NEFILIM-DECRYPT.txt or OFFWHITE-MANUAL.tx. Ransom note gets dropped into most folders located on the system, as well as the desktop |
| Contact | [email protected], [email protected] or [email protected], [email protected], [email protected], [email protected] |
| Main executable | The file is signed by Sectigo RSA Code Signing CA |
| Demands | Cybercriminals threaten to publicly disclose all the encrypted files, which can be devastating for any business |
| Data recovery | As Nefilim ransomware is the newest version of Nemty, no decryption tool has yet been developed. Other methods include using third-party recovery software or built-in Windows tool to attempt to retrieve at least |
| Malware removal | Use reputable anti-malware software to scan your machine (access Safe Mode if required – we provide the instructions below) |
| System fix | If your computer seems to be unstable after you terminate the virus, you make use of Reimage Reimage Cleaner Intego in order to fix the damage done and recover the normal operation of the device |
Nefilim is a re-branded name of an already known strain – Nemty ransomware/Nemty Revenge 2.0, which mostly targeted high profile organizations and businesses, although regular users can be affected as well. It is yet unknown why the cybercriminal group decided to change the name, but they are using a similar pattern for file encryption and naming of the ransom note. Nevertheless, it is highly likely that malicious actors behind Nefilim ransomware changed the name due to a new scheme that they operate now
As of now, there are several tools that you could use for Nefilim ransomware removal, as over 40 engines detect the virus as follows:
- Win32:Malware-gen
- Ransom.NEFILIM!1.C3E7 (CLOUD)
- Ransom.Nefilim
- Win32/Filecoder.Nemty.D
- Mal/Generic-S
- Trojan-Ransom.Win32.JSWorm.d
Therefore, employ a sophisticated anti-malware software and perform a full system scan to remove Nefilim ransomware from your machine. Additionally, if your computer seems to lag, crash or suffer from similar stability issues after you get rid of malware, we suggest you repair it with Reimage Reimage Cleaner Intego.
Nefilim ransomware is a data locker that also threatens to publish stolen data from the computer and the connected networks if the ransom is not paid within seven days

Nefilim ransomware is a data locker that also threatens to publish stolen data from the computer and the connected networks if the ransom is not paid within seven days
Nefilim ransomware operation and data encryption
Nefilim ransomware authors are known to be sophisticated individuals who put their knowledge in coding for malicious deeds. The malware is spread by utilizing various exploits (RIG and Radio), fake websites, weakly protected RDP connections, as well as other methods – using several different attack vectors increases the chances of users being infected.
Security researchers previously noticed already that Nefilim virus’ previous versions – Nemty – strangely used various clues hidden inside its code. For example, several references to experts were previously found within the written code – the new version now mentions SophosLabs and AhnLab in a particularly vulgar way.[2]
Another interesting feature of Nefilim ransomware is that the main executable used to infect the machine is signed by a valid certificate, which allows cybercriminals to prevent Windows from showing a warning about the file being potentially unsafe – this is another trick to avoid users from being suspicious during the initial infiltration process.
Once inside the system, Nefilim ransomware will implement the necessary changes to ensure that the encryption process would be successful. The virus performs the following:
- Exits if the keyboard language is set to one of the following: Russia, Belarus, Ukraine, Kazakhstan, Tajikistan, Azerbaijan, Armenia, Kyrgyzstan, and Moldova;
- Deletes all Shadow Volume Copies to prevent recovery;
- If available, it accesses backups and removes them;
- Gathers sensitive information about the company or the computer user;
- Modifies the Windows registry[3] for persistence, etc.
Once the necessary changes are complete, Nefilim ransomware begins the file encryption process, turning all normal data into inaccessible once – it targets the msot commonly-used files such as .jpg, .dat, .xlsx, gif, .pdf, and others, and appends each of them with .NEFILIM marker.
After that, malware drops the following ransom note:
All of your files have been encrypted with military grade algorithms.
We ensure that the only way to retrieve your data is with our software.
We will make sure you retrieve your data swiftly and securely when our demands are met.
Restoration of your data requires a private key which only we possess.
A large amount of your private files have been extracted and is kept in a secure location.
If you do not contact us in seven working days of the breach we will start leaking the data.
After you contact us we will provide you proof that your files have been extracted.To confirm that our decryption software works email to us 2 files from random computers.
You will receive further instructions after you send us the test files.
As evident, crooks behind Nefilim ransomware are threatening to release the stolen data to the public, which can ultimately compromise any organization or business. However, this increases the chances of ransom payment to be made. If you decide to pay, keep in mind that hackers might never send you the required Nefilim ransomware decryptor, so you may up losing all your money, and they might still publish your data regardless.
Instead, we suggest you recover your data from backups and ensure that no future infections happen. For that, check the tips provided in the following section. Note that, if you did not have backups or they got encryption, you should copy all .Nefilim files over before trying to apply third-party software or using other methods.
While there is no Nefilim ransomware decryptor currently available, paying cybercriminals is risky as they might never send the promised tool

While there is no Nefilim ransomware decryptor currently available, paying cybercriminals is risky as they might never send the promised tool
Prevent your computer from being infected with ransomware
Nefilim ransomware developers use Ransomware-as-a-Service (RaaS) scheme in order to propagate the malware and receive profit from it. As a result, different cybercriminals who take on the task use different methods to infect users and companies worldwide. As mentioned above, various techniques were used, including exploit kits, web injects, drive-by downloads, unprotected Remote Desktop connections, etc.
If you are already infected, there is not much you can do apart from trying to remediate the situation. Nevertheless, you need to ensure that this devastating situation would not happen in the future. For that, you should:
- Employ sophisticated anti-malware software and keep it updated;
- Keep all the software and the operating system up to date at all times;
- Use strong passwords to protect your RDP connections and other accounts;
- Disable RDP as soon as it is not needed and use non-default port to establish the connection;
- Do not allow email attachments to run macro function (“Allow content”);
- Educate your staff about cybersecurity and safe computer handling practices;
- Enable Firewall and install ad-block on all web browsers;
- Do not download pirated software installers or software cracks.
Additionally, it is essential to keep backups separated from your computer and the network it is connected to. In such a case, you could restore all the files without paying cybercriminals, although they might still publish the stolen information online.
Nefilim ransomware eliminate and data recovery
It is important to note that the infection of the computer or the network and data encryption are completely separate procedures, although it is possible to do the latter with the help of the former one only. Therefore, Nefilim ransomware removal will not retrieve access to your data – you need to use backups instead. If you had no backups, ensure that you make a copy of the encrypted data before you do anything, as further actions may permanently damage the files.
Then you need to remove Nefilim ransomware from the computer and the infected network. To do that, employ reputable anti-malware software and perform a full scan to ensure that all the malicious files are eliminated. If the procedure was unsuccessful, you can access Safe Mode with Networking as explained below and then initiate a scan – we provide the instructions on how to do that below.
Finally, after Nefilim virus elimination, you can attempt data redemption. For that, you can try third-party software like Data Recovery Pro or ShadowExplorer. If you were lucky enough, you could potentially recreate at least some of your files embedded in your hard drive. Note that security researchers created a decryptor for previous ransomware versions so that it might be possible for Nefilim ransomware as well.[4]
This entry was posted on 2020-05-04 at 23:58 and is filed under Ransomware, Viruses.

