Mzlq ransomware – a file locking malware that aims to extort money by locking all personal files on the system
Mzlq ransomware is a data locking malware that asks to pay 490$/980$ ransom in Bitcoin to return encrypted personal files

Mzlq ransomware is a data locking malware that asks to pay 490$/980$ ransom in Bitcoin to return encrypted personal files
Mzlq ransomware is a malicious program that might access your PC and lock all personal files on it, including pictures, music, videos, documents, databases, etc. Belonging to the most prominent crypto-malware family Djvu, it was first spotted in mid-May, 2020, attacking users all over the world via software cracks. Once installed, the ransomware will append .mzlq extension to each of the files with the help of the RSA encryption algorithm, preventing user access.
To recover data, victims need to acquire a unique key that is stored on cybercriminals’ servers. However, the attackers behind Mzlq virus are not willing to give it away for free, and blackmail users into paying ransom instead. Inside a ransom note, titled _readme.txt, which can be found on the desktop and other places on the computer, crooks specifically mention that victims should contact them via [email protected] or [email protected] if they want to acquire the decryptor. Security experts discourage users from paying and instead recommend using alternative methods for data recovery after Mzlq ransomware removal.
| Name | Mzlq ransomware |
| Type | Crypto-malware, file locking virus |
| Family | This data locker belongs to one of the most prominent ransomware families – Djvu/STOP |
| Cipher | This ransomware uses one of the safest encryption algorithms to lock data – RSA |
| File extension | All non-system and non-executable files are appended with .mzlq extension and can no longer be accessed. Example of an encrypted file: picture.jpg.mzlq |
| Ransom note | As soon as malware is done with modifying Windows system and encrypting data, it drops a ransom note _readme.txt and places it on the desktop, along with folders were the locked data is located |
| Ransom size | If the contact is made within the first 72 hours of the infection, users are asked for $490; this price doubles to $980 afterward |
| Contact | [email protected] or [email protected] |
| Data recovery | Files might be recovered with the help of Emsisoft’s Decryptor for STOP Djvu if an offline key was used for data locking. Otherwise, only restoring files from backups is a secure way of recovery, as there is no guarantee that the attackers will deliver the decryptor or that third-party tools will work. Nevertheless, we provide the instructions and download links for the latter below |
| Malware removal | Download and install a reputable anti-malware software, and the preform a full system scan (do not forget to backup the encrypted data before this process if you do not have working file copies ready) |
| System fix | If your computer is crashing, lagging and returning errors after malware termination, repair Windows system with the help of Reimage Reimage Cleaner Intego |
Djvu ransomware is one of the most prominent and successful crypto-malware families in the wild. Even though it is primarily using one attack vector for its propagation (pirated software installers and software cracks), Mzlq ransomware authors already released over 220 different versions, including Mpal, Qewe, Lezp, Lalo, and many others.
Since the family is huge, it obtains much attention from the security community and industry experts. Prior to August 2019, the malware used a weaker encryption method, which allowed security firm Emsisoft to release a decryption service that would allow users to regain data for free.
However, all the versions released past that date are no longer decryptable, although Emsisoft provided another tool (a successor for STOPDecrypter), that would help victims whose data was locked with an offline ID. Nevertheless, one victim of Mzlq ransomware has to first pay the attackers the ransom to retrieve the offline key first in order for it to work for other users infected with the same malware version. Thus, you should not rush to pay the virus authors, as there is still a chance that your files where locked with an offline ID.
If you were hit by Mzlq ransomware, it is highly likely to happen due to a download from a pirated software distribution website. Quite often, the attackers insect malicious versions of illegal software or cracks, so users click on the executable without thinking that it is malicious.
Once inside the system, Mzlq file virus does not immediately locks data. Instead, it performs a series of changes to the Windows machines. For example:
- the malware inserts the additional module into the web browsers to steal sensitive information as long as it is present on the machine;
- modifies Windows hosts file located in C:\Windows\System32\drivers\etc\ – this prevents users from visiting security-related websites and forums where they could seek help with malware removal and data recovery options;
- creates a variety of entries in the %AppData% and %User% folders, where the main executable is also placed;
- opens and modifies Windows registry keys in order to launch itself with each Windows launch;
- creates new and terminates some built-in processes, etc.
Mzlq ransomware is a cryptovirus that uses RSA encryption algorithm to lock all data on the infected computer

Mzlq ransomware is a cryptovirus that uses RSA encryption algorithm to lock all data on the infected computer
Once the preparations are complete, Mzlq ransomware will begin to scan the system for files to encrypt. Just as many other data-locking viruses, it targets the most common file types, such as .jpg, .rar, .mp4, .gif, .doc, .xls, .txt, and many others. During the encryption process, users will be shown a fake Windows update screen so that they would not stop it before all data is locked.
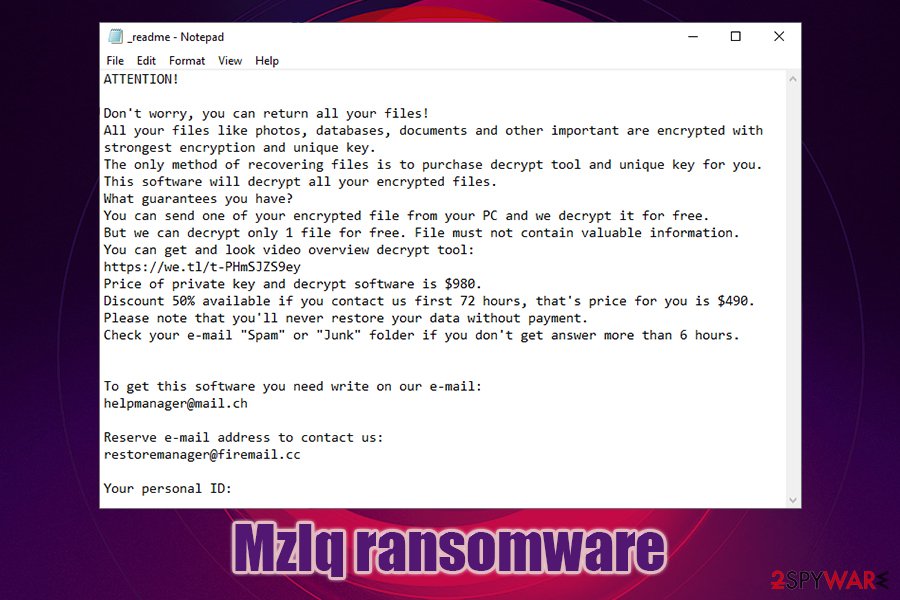
At the end of data locking process, users are also presented with the _readme.txt ransom note which reads the following:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-PHmSJZS9ey
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
[email protected]Reserve e-mail address to contact us:
[email protected]Your personal ID:
As evident, Mzlq ransomware authors are trying to convince users to pay the ransom and also offer a 50% discount if the payment is transferred within the first 72 hours of the infection. They also say that they can perform test decryption for a selected file for free. However, these are mere tricks to create a false sense of security among victims. Keep in mind that trusting cybercriminals is not something that you should do – they might take your money and never send you the Mzlq ransomware decryption tool.
Instead, backup all the encrypted data first and then remove Mzlq ransomware from your system. The best way to do it is by employing a reputable anti-malware software, such as SpyHunter 5Combo Cleaner or Malwarebytes for the process. Once complete, you can then proceed with alternative data recovery methods listed below.
If you decide to pay the ransom despite the risks, do not forget to contact Emsisoft researchers that could then provide help to other victims. Finally, if you find that your computer is slow and unstable after you eliminate the virus, we suggest using Reimage Reimage Cleaner Intego repair software instead of performing a full Windows reinstall.
Avoid software cracks like a plague
While in some cases, users choose to underestimate precautionary measures against malware infections, others are simply unaware of dangers that can be encountered online. Regardless of the reason, hundreds of users are infected with ransomware each day, and many of them lose access to their files forever. This is the main reason why ransomware is so devastating and is also treated as a data breach as of recently when it hits a business or organization.[1]
However, Djvu operates a scheme which mainly targets private users, so illegal websites that distribute pirated software is a perfect spot for malware propagation. Pirated software installers and cracks are often used to bypass the registration process of the app to acquire its full features for free. While this activity is illegal and might result in fines from authorities, users are still keen on pirating programs, video games, and other software.
While some software installers can be scanned for malware with security software prior to the installation, software cracks are tools that cannot be properly checked, since, by design, they exist to break something within the program’s code. As a result, most anti-malware applications will flag it as malicious, regardless if it actually is and will result in ransomware or other malware infection. Therefore, stay away from software cracks, they are extremely dangerous, as they are often boobytrapped with malware.
You should also equip the computer with comprehensive security software, apply the most recent software updates immediately, create safe passwords (and never reuse them!), and regularly backup your data in case ransomware does manage to break into your machine.
Mzlq ransomware is a version of Djvu ransomware, and has a relatively low detection rate

Mzlq ransomware is a version of Djvu ransomware, and has a relatively low detection rate
Mzlq ransomware removal process
Before you remove Mzlq ransomware, there are a few things that you need to take care of. First of all, we recommend going to the following location and deleting the Windows hosts file:
C:\Windows\System32\drivers\etc\
Once done, you will be able to access all the security-related websites once again without restrictions, as a new hosts file will be created by Windows automatically. Additionally, you should backup all the encrypted data before the Mzlq ransomware removal process, as it might permanently damage the already encrypted files.
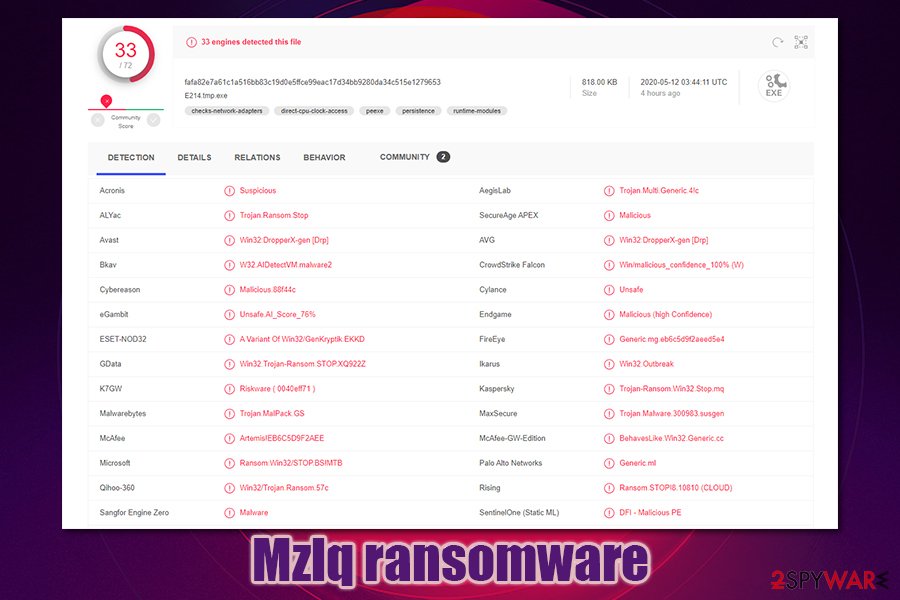
To get rid of Mzlq virus, you will have to employ a powerful security software (if needed, you can also access Safe Mode with Networking and perform the scan from there – instructions below). There are many options available, and most of them recognize malware under the following names, according to Virus Total:[2]
- A Variant Of Win32/GenKryptik.EKKD
- W32.Trojan.Gen
- Trojan.Multi.Generic.4!c
- Mal/Generic-S
- Win32.Trojan-Ransom.STOP.XQ922Z
- Win32:DropperX-gen [Drp], etc.
Overall, the detection rate of Mzlq ransomware is currently relatively low, which is pretty common to the newly-released malware samples. Also, most of the detections are performed using generic or heuristic analysis techniques[3] – this highlights the importance of next-gen anti-malware applications.
This entry was posted on 2020-05-12 at 05:10 and is filed under Ransomware, Viruses.

