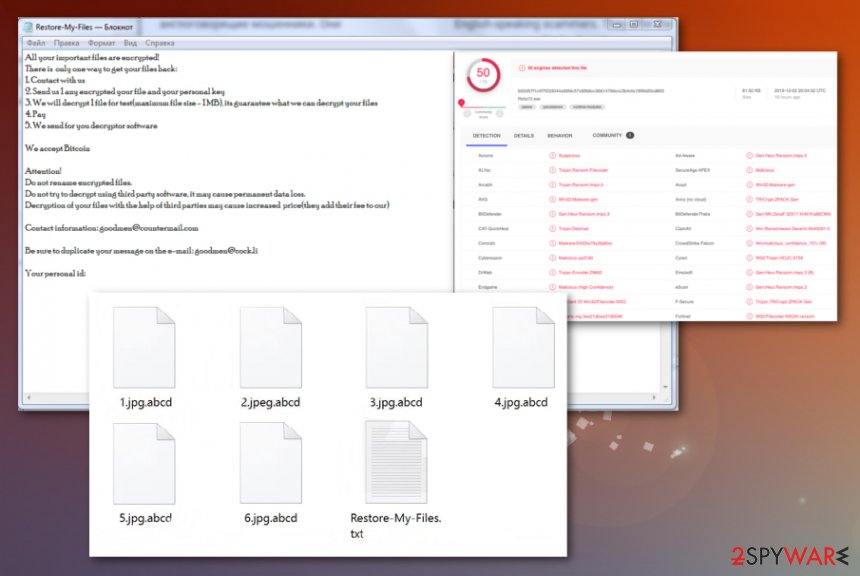
LockBit ransomware – a harmful parasite that has been flagged as malicious by 42 AV engines out of the total 68
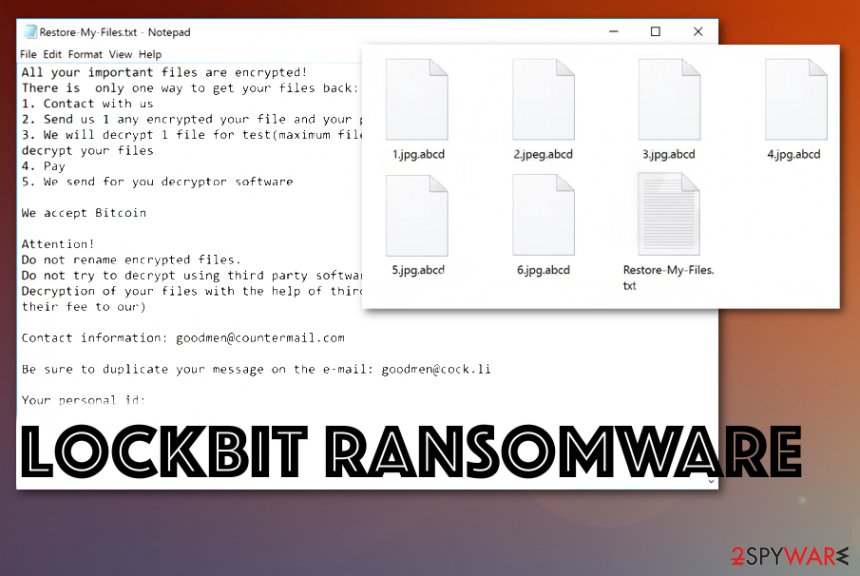
LockBit ransomware is a cyber infection that targets all types of data files on Windows computers. First found by MalwareHunterTeam, this malware encrypts files, folders, and documents with a unique cipher and leaves them with the .abcd appendix added. Then, the “Restore-My-Files.txt” ransom message appears and places a Bitcoin ransom demand. As evidence of the decryption tool’s existence, crooks allow victims to send them one small file for free encryption via [email protected] or [email protected] email addresses. Be aware that many other system changes in the Registry and Task Manager might also be performed and allow LockBit virus to execute other malicious modules.
| Name | LockBit ransomware |
|---|---|
| File marker | .abcd is the extension that comes at the end of each file encrypted by the malware. This appendix indicates locked files from other data on the machine |
| Ransom note | Restore-My-Files.txt is the ransom note file that delivers a direct message from virus developers that states about encryption and ransom payment options. This file also includes contact information of developers |
| Contact emails | [email protected] and [email protected] |
| Main symptoms | The virus infiltrates the machine and starts file-locking immediately. Once the chosen data gets encrypted and marked using the file appendix, photos, documents, archives, and videos or audio files become useless and unopenable. The ransom note delivered after that displays the options for file recovery, including paying the ransom. The threat also manages to access system folders and alter those files, disable functions, add programs to affect the persistence of the malware |
| Distribution | Infected files delivered as email attachments, part of the pirated software package or spread via corrupted or hacked websites |
| Elimination | LockBit ransomware removal should be performed using an anti-malware program that can detect and remove all the intruders and associated files |
| Tips for system repair | Your machine gets affected by the virus significantly, including system folders and files, programs, directories. You need to repair this virus damage and fix other issues to ensure that there are no vulnerabilities on the device. Get a system optimization tool like Reimage Reimage Cleaner or a different repair application and run the scan that may indicate and fix corrupted, damaged or differently affected files for you |
| Detection names | This ransomware virus has been detected as malicious by 42 AV engines out of the total 68. Some of the detection names include TR/Downloader.Gen, Gen:Heur.Ransom.Imps.3, UDS:DangerousObject.Multi.Generic, etc. |
According to information provided by VirusTotal,[1] LockBit ransomware has been discovered my 42 antivirus programs. This dangerous virtual parasite that likes attacking vulnerable computer systems. Once it gets in, there are many alterings made to different system locations so that the virus could plant itself properly. First of all, it will ensure that is malicious code will run every time you turn on your computer.
Then, LockBit ransomware will supposedly include another module that allows scanning the entire system for new files to encrypt once in a while (for example, every half an hour). This way the cyber threat ensures that no valuable data has been left free from encryption and increases its luck in receiving ransom payments.
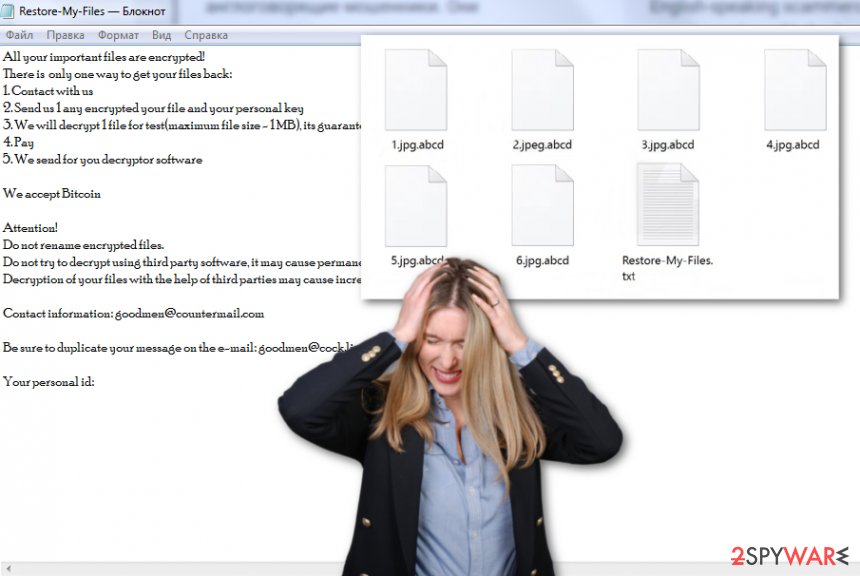
Afterward, LockBit ransomware will intensively urge for a ransom demand via a specific text message. The criminals aim to threaten people that using other recovery tools might cause permanent damage and the only way to restore the locked data is by paying the crooks and receiving the tool from them directly:
All your important files are encrypted!
There is only one way to get your files back:
1. Contact with us
2. Send us 1 any encrypted your file and your personal key
3. We will decrypt 1 file for test(maximum file size – 1 MB), its guarantee what we can decrypt your files
4. Pay
5. We send for you decryptor softwareWe accept Bitcoin
Attention!
Do not rename encrypted files.
Do not try to decrypt using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price(they add their fee to our)Contact information: [email protected]
Be sure to duplicate your message on the e-mail: [email protected]
Your personal id:
–
LockBit ransomware supposedly keeps both encryption and decryption keys safely hidden on remote servers that are reachable only for the criminals themselves. This way the hackers decrease the victims’ chances of recovering their data. However, we still do not recommend listening to the provided ransom demands.
LockBit ransomware is a dangerous virus that drops a ransom message and urges for a BTC transfer
The crooks who stand behind LockBit ransomware might scam you very easily and leave you with an absolute nothing. Besides, these people often urge for some type of cryptocurrency ransom as it is the best way to stay anonymous and avoid getting caught in case a victim reports the malware attack.
Besides encrypting data and providing ransom demands, LockBit ransomware might be capable of delivering other malware to the Windows computer system. It is not surprising for this to happen as malware often comes in packages of two or more rather than entirely on its own.
LockBit ransomware removal is the best way to avoid the risk of additional infections. You should scan your computer system with reliable antimalware software and get rid of the threat. Afterward, if you have found some damaged components on your system, try repairing them with a tool such as Reimage Reimage Cleaner .
After you remove LockBit ransomware from your machine, you can start thinking about possible data recovery solutions. Almost anything is better than paying the demanded ransom that can vary between $200 and $2000. Scroll to the end of the page where you will find some file restoring possibilities which might be helpful in your case.
LockBit ransomware – a computer parasite that has been flagged as malicious by 42 AV engines
Hiding places of ransomware remain similar for years
As long as ransomware[2] has been spread, these malicious parasites are distributed by using the same techniques from year to year. According to security specialists from NoVirus.uk,[3] criminals use email spam as a way to distribute their malware. The virus is often hidden in a hyperlink or attachment that comes looking like an ordinary shipping message from a reliable company such as DHL or FedEx.
The most important part about managing your received email is checking the sender, his/her email address, and searching the written texts for possible grammar mistakes. If the message comes from an unidentifiable deliverer or includes a lot of mistakes, you should delete it right away without even considering to open it. Also, scan all received attachments with reliable antimalware software in case the clipped document appears to be malware-laden.
Additionally, ransomware infections can get delivered via other sources such as p2p networks[4] (The Pirate Bay, eMule) that include a lot of software cracks. Also, malware camouflages as fake software updates (JavaScript, Flash Player), so better get all required program upgrades only from their official websites. Last but not least, vulnerable RDPs that do not include passwords or include weak ones are also targets of cybercriminals.
LockBit ransomware removal guidelines
LockBit ransomware removal should be carried out only with antimalware software, otherwise, big damage can be brought to your computer system or you might skip some crucial steps. However, you should diminish malicious processes first so that the malware does not interrupt your elimination process.
You can disable LockBit ransomware processes by booting your computer system in Safe Mode with Networking or activating the System Restore feature. If you do not know how to accomplish such tasks, scroll to the end of this article and take a look at the steps provided there.
When you are ready to remove LockBit ransomware from your Windows system, make sure to check the entire machine for malicious strings. You can do that by running a full checkup with SpyHunter 5Combo Cleaner or Malwarebytes. If these antivirus programs find some corrupted components, try fixing the damage with Reimage Reimage Cleaner software.
Remove LockBit using Safe Mode with Networking
To stop malicious processes on your Windows machine, apply the following guiding steps and activate Safe Mode with Networking.
- Windows 7 / Vista / XP
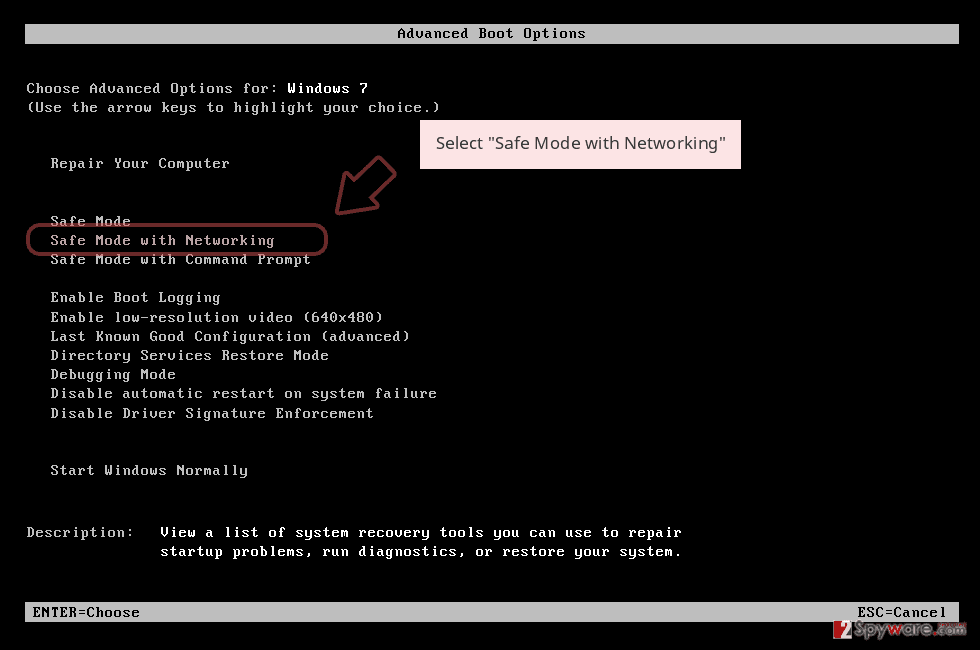
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
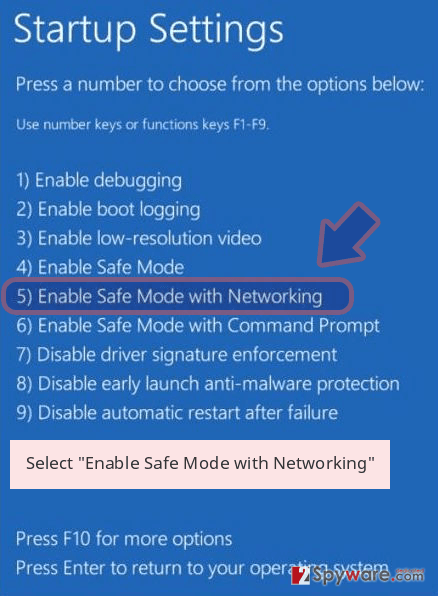
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete LockBit removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove LockBit using System Restore
To diminish malicious activity on your computer, you should enable System Restore. Apply the following steps to turn this feature on.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove LockBit from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If your files are encrypted by LockBit, you can use several methods to restore them:
Use Data Recovery Pro to restore some locked data.
Try employing this software for file repair after a ransomware attack.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by LockBit ransomware;
- Restore them.
Windows Previous Versions feature might help with file restore.
Apply this feature to corrupted/locked data and you might have a chance of recovering it.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Try Shadow Explorer and restore some files.
If the ransomware virus did not touch Shadow Copies of your data, try employing this software for file recovery.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Currently, no official decryption tool has been released.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from LockBit and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner , SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2019-12-04 at 06:01 and is filed under Ransomware, Viruses.

