EvilQuest – a rare Mac ransomware virus that is capable of locking data, recording keystrokes, and wiping away sensitive data

EvilQuest, a.k.a. OSX.ThiefQuest or ThiefQuest – a multifunctional ransomware virus targeting macOS machines has been detected by Dinesh Devadoss[1], a researcher from K7 Labs, at the end of June 2020. MacOS is still a tough nut to crack for hackers, though it seems that a group of hackers that has previously been responsible for arranging KeRanger and FileCoder Mac malware attacks has improved their Mac hijack skills.
According to the researchers, the EvilQuest ransomware[2] virus is believed to be or become successful as it circulates in the wild in the disguise of legitimate software, such as Ableton, Little Snitch, Mixed in Key, etc. These programs are accessible by millions of people who are visiting torrent sites, such as The Pirate Bay, 1337x, Torlock, YTS[3], and others.
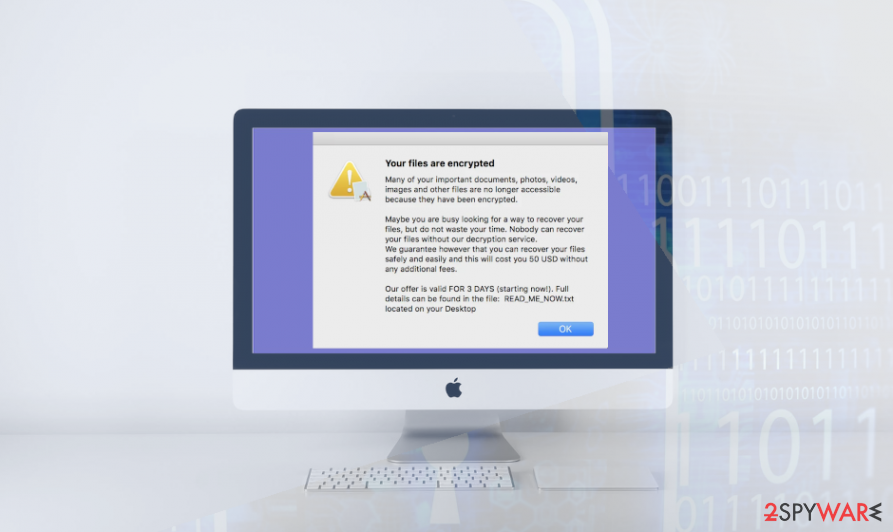
The trojanized app installers are obfuscated to disguise the presence of the malicious .PKG installer (ransomware runner), which spreads listed alongside the installer and uninstaller of the downloaded app. If the payload of the EvilQuest file-locking virus is successfully launched, the virus locks files using the BEBABEDD file marker, drops a READ_ME_NOW.txt note with ransom instructions, and downloads data wiper as a secondary payload.
The virus can lock data and steal credentials
The success of the EvilQuest Mac malware is not yet clear. However, the fact that it spreads in the disguise of legitimate apps via torrent sites is worrying and allows presumptions that this time many Macs may get infected.
According to cybersecurity researchers who have been very active in analyzing this threat in details claim that it stands from the crowd due to the whole package of additional functions. As ransomware it primarily aims at locking files. However, it’s capabilities in this sphere is rather limited. It turns out that it can lock Mac files with BEBABEDD file marker only 31 extensions, including:
.pdf, .doc, .jpg, .txt, .pages, .pem, .cer, .crt, .php, .py, .h, .m, .hpp, .cpp, .cs, .pl, .p, .p3, .html, .webarchive, .zip, .xsl, .xslx, .docx, .ppt, .pptx, .keynote, .js, .sqlite3, .wallet, .dat
After the success of data encryption, the EvilQuest ransomware establishes the remote connection with the C2 server by connecting to the http://andrewka6.pythonanywhere[.]com/ret.txt. This domain is subsequently used for the regular transmission of recorded data.
A closer analysis shows that the file encryption is just the tip of an iceberg. It looks like EvilQuest virus developers have set higher goals, such as to steal people’s credentials and leave their cryptocurrency pockets empty.
When the ransomware gains persistence on the Mac machine, it runs shell commands under administrative privileges to download Python[4] scrips and activate them. These scripts are used for scanning /Users folder and sending files less than 800kb to Command & Control server.
Do not pay the ransom – locked files won’t be decrypted anyway
The macOS EvilQuest wiper is a dangerous piece of malware, which should not be underestimated. While many people still consider macOS to be resistant to malware attacks, they are not rendering AV programs, so downloading torrent files poses a huge risk.
It turns out that the EvilQuest ransomware cannot be decrypted. The encryption model it applies for locking data is AES-256 and flaws haven’t yet been found. The ransom note that the virus drops demands the victims to pay $50 ransom within 3 days. The payment should be done in Bitcoins and transferred to the 13roGMpWd7Pb3ZoJyce8eoQpfegQvGHHK7 wallet,
The problem is that criminals behind the EvilQuest ransomware forgot to provide victims with a unique identifier and provide with the email. Currently, there’s no way for the victim to contact the criminals and inform them about the payment. Thus, the payment will have no response. Victims should not believe in claims that the decryption will start automatically after the payment since criminals because they are bogus.
Those whose Macs have been attacked by EvilQuest ransomware wiper should contact cybersecurity researchers that are working on this cyber threat, for instance, K7 Labs[5], and inform them about the attack.
