DoppelPaymer ransomware is crypto-locking malware that employs targeted attacks to reach high-profile targets
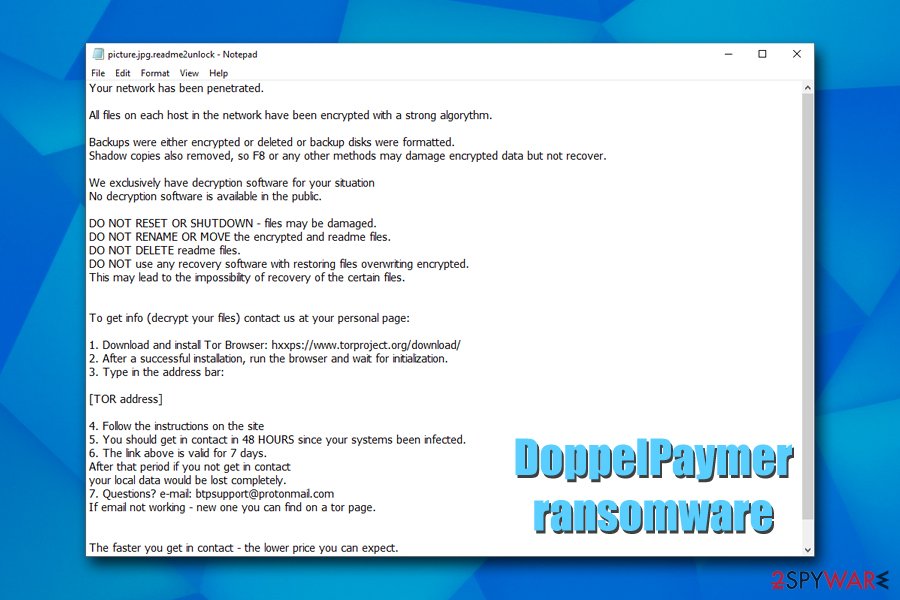
DoppelPaymer ransomware is a file locking virus that derived from a well-known BitPaymer, which was previously used in various high-profile targeted attacks
DoppelPaymer is ransomware-type of computer infection that stems from another file-locking malware that first emerged in August 2017 – BitPaymer. This ransomware strain was developed and distributed by the INDRIK SPIDER cybercriminal group, which was famous for first using the infamous Dridex banking Trojan in its Big Game Hunting[1] attacks against such targets like Chilean Ministry of Agriculture, Texas, and City of Edcouch.[2]
In July 2019, researchers at CrowdStrike spotted a new variant which they dubbed DoppelPaymer ransomware – it was possessed multiple similarities with its predecessor. According to Croudstrike experts’ findings,[3] they believe that the developer of BitPaymer left the cybercriminal gang and started distributing its own version of the malware – DoppelPaymer.
The actor uses targeted attacks to infect companies from various industries and infect full networks and all the connected drives. DoppelPaymer ransomware uses the RSA-2048 and AES-256 encryption algorithm[4] to encrypt data on the infected machine and appends .locked extension to each of the files. Additionally, every modified file also receives a separate ransom note, which goes by the name [filename].[file extension].readme2unlock.txt.
| Name | DoppelPaymer |
| Type | Ransomware, file locking virus |
| Associated with | Researchers believe that the distributor of DoppelPaymer virus initially came from the INDRIK SPIDER cybercriminal gang which specialized in the delivery of Dridex Trojan and BitPaymer ransomware |
| Related process name | Upon extraction, ransomware runs SpotLife WebAlbum Service Plugin in the background |
| Encryption algorithm | Malware uses a combination of sophisticated encryption algorithms RSA-2048 and AES-256 |
| File extension | Each of the the personal files is appended with .locked file extension |
| Ransom note | The virus drops one ransom note ([filename].[file extension].readme2unlock.txt) for each of the affected files |
| Contact | Victims are asked to download Tor and enter a unique URL that brings them to the payment page and other instructions. Additionally, hackers provide [email protected] as contact email address if any questions arise |
| Ransom size | There is no ransom demand provided, although hackers are known to ask for particularly high ransoms, such as 2 BTC, 40 BTC, and 100 BTC |
| Termination | The best way to terminate the infection is to install a reputable anti-malware software and perform a full system scan as per our instructions below |
| File decryption | Currently, there is no guaranteed way to decrypt locked files (unless backups are available). Nevertheless, victims can try using alternative solutions, such as third-party recovery software |
| System recovery | Ransomware might not only affect the existing system files but also install secondary payload, which might further damage the operating system. Due to this, after the virus elimination, users might experience system crashes and even will be forced to reinstall the OS. To avoid that, use PC repair tool Reimage Reimage Cleaner – it should be able to reverse all the damage done |
DoppelPaymer was released with multiple improvements over BitPaymer
Since its update from the BitPaymer, the DoppelPaymer virus has received several updates to increase the persistence and evasion of the computer threat. One of the main changes was made to the ransomware source code, which allows it to perform file encryption process at a much faster rate – it increases the chances of all or most files being encrypted before the machine operator can interrupt the process.
Additionally, DoppelPaymer ransomware crashes if some of the required conditions are not met – researchers believe that the process was programmed so that automatic sandbox[5] analyzing would be avoided. Finally, the malware also kills several processes and services once it gets executed in order to prevent termination of the encryption process of the data.
However, instead of using service names, DoppelPaymer ransomware utilizes lists of CRC32 checksums, which prevents security researchers from performing reverse-engineering techniques. The malware incorporates the ProessHacker with custom DLL (a legitimate open-source administrative utility tool) as well as a kernel driver, which consequently allows the shut down of the predetermined services and processes.
Croudstrike researchers wrote the following in their report:[3]
Both BitPaymer and DoppelPaymer continue to be operated in parallel and new victims of both ransomware families have been identified in June and July 2019. The parallel operations, coupled with the significant code overlap between BitPaymer and DoppelPaymer, indicate not only a fork of the BitPaymer code base, but an entirely separate operation. This may suggest that the threat actor who is operating DoppelPaymer has splintered from INDRIK SPIDER and is now using the forked code to run their own Big Game Hunting ransomware operations.
Due to these modifications, DoppelPaymer ransomware removal might become complicated. Nevertheless, accessing Safe Mode with Networking and running a full system scan with the most recently-updated security software should do the job.
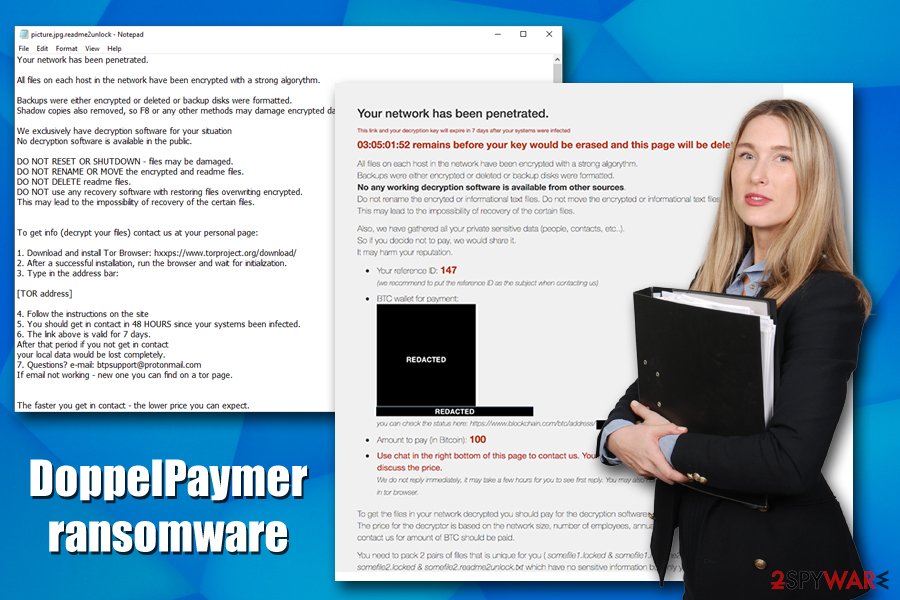
DoppelPaymer is a ransomware virus thap appends .locked extension to each of the files and then demands ransom to be paid for data decryption
DoppelPaymer ransomware does not provide the ransom amount
Upon infiltration and the necessary system modifications such as loading of several modules, DoppelPaymer ransomware begins the encryption process of databases, documents, pictures, and all the other relevant files that are stored on corporate computers. After encryption, each of the affected files receives .locked marking – for an example, a picture.jpg is transformed into picture.jpg.locked and is no longer accessible. Note, .locked extension has been used by several other ransomware strains, including Unlock92 and Luxnut.
Once the data encryption process is complete, DoppelPaymer creates a multitude of ransom notes (one per file) and places them into the same folder. All the notes are identical, and state the following:
Your network has been penetrated.
All files on each host in the network have been encrypted with a strong algorythm.
Backups were either encrypted or deleted or backup disks were formatted.
Shadow copies also removed, so F8 or any other methods may damage encrypted data but not recover.We exclusively have decryption software for your situation
No decryption software is available in the public.DO NOT RESET OR SHUTDOWN – files may be damaged.
DO NOT RENAME OR MOVE the encrypted and readme files.
DO NOT DELETE readme files.
DO NOT use any recovery software with restoring files overwriting encrypted.
This may lead to the impossibility of recovery of the certain files.To get info (decrypt your files) contact us at your personal page:
1. Download and install Tor Browser: hxxps://www.torproject.org/download/
2. After a successful installation, run the browser and wait for initialization.
3. Type in the address bar:[TOR address]
4. Follow the instructions on the site
5. You should get in contact in 48 HOURS since your systems been infected.
6. The link above is valid for 7 days.
After that period if you not get in contact
your local data would be lost completely.
7. Questions? e-mail: [email protected]
If email not working – new one you can find on a tor page.The faster you get in contact – the lower price you can expect.
DATA
Crooks behind the DoppelPaymer virus claim that rebooting the system or using a recovery program can damage the encrypted files. Because data corruption can indeed happen when trying such actions, experts highly advise to backup all the encrypted files before proceeding with file recovery. Nevertheless, victims should first remove DoppelPaymer ransomware with the help of powerful anti-malware software in Safe Mode with Networking – we provide the instructions below. We also recommend using Reimage Reimage Cleaner to repair the corrupted system files and ensure normal PC operation.
Once DoppelPaymer is deleted, users can attempt to retrieve files with recovery software or by using automated Windows backups, although both methods might not bring any positive results. Nevertheless, paying cybercriminals the high amount of ransom (they might ask for 2 BTC, 40 BTC, or 100 BTC) might be extremely risky due to the shady business model. After all, cybercriminals are engaging in illegal activity, so trusting them is not recommended.
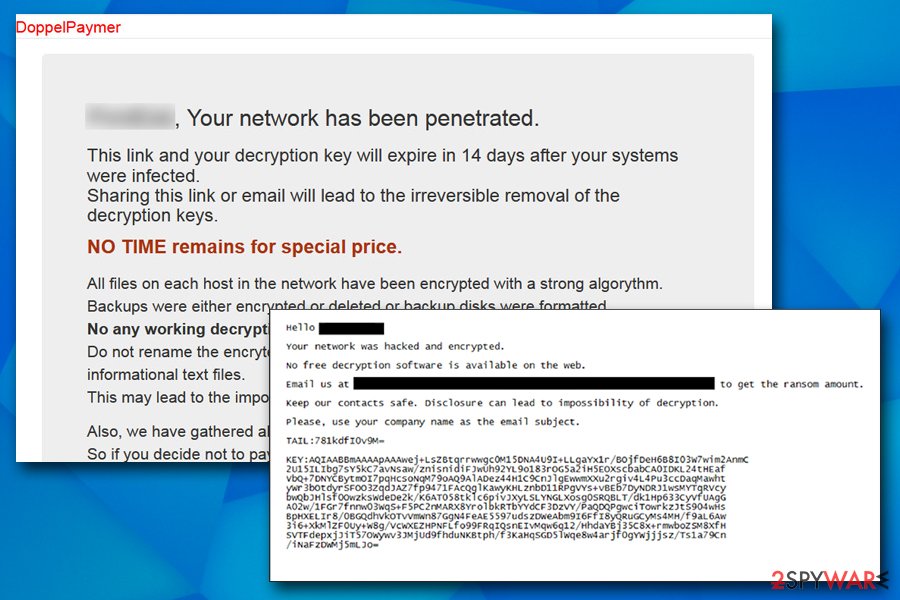
DoppelPaymer ransomware drops a .txt ransom note that later directs users to Tor page – they can communicate with the attackers via the online chat there
Infection vectors include software vulnerabilities, brute-force attacks, as well as targeted malicious emails
DoppelPaymer ransomware authors use targeted attacks to penetrate companies’ networks. In most of the cases, targeted attacks can be preformed with the help of the following methods:
- Targeted malicious emails that contain a hyperlink or an attachment that would initiate the infection process;
- Criminals might abuse outdated computer system vulnerabilities if the security updates are not applied on time (especially outdated OS that is no longer supported by Microsoft, such as Windows XP);
- Corporate intrusions by hackers are often performed with the help of brute-force attacks via weak RDP (Remote Desktop Protocol) connections.
To avoid ransomware infiltration in organizations, it is important to train the employees about cybersecurity, employing complicated passwords with the two-factor authentication feature, keeping all the operating systems and the installed software updated, as well using cybersecurity solutions that would be able to detect and stop the incoming payloads.
DoppelPaymer removal steps
DoppelPaymer virus is a modular threat, and its developers are known to be the same individuals who created Dridex Trojan and were also affiliated to GameOver gang[6] – Zeus criminal network. Therefore, there is a chance that, besides the ransomware, there might be other payloads present on the infected network or the machine. For that reason, DoppelPaymer ransomware removal is mandatory. Nevertheless, the backups of each of the files should be performed, as the process of malware elimination or even system reboot might corrupt all the encrypted data, and it might not be recoverable at all.
To remove DoppelPaymer ransomware, users should access Safe Mode with Networking, as explained below, and perform a full system scan. Advanced security solutions should be able to find all the malicious components of malware along with any secondary payloads that might be present on the device/network.
Additionally, we also recommend contacting the local authorities and report the cybercriminal incident. For further information and DoppelPaymer decryptor software that might emerge in the future, visit the following websites:
This entry was posted on 2019-11-18 at 07:43 and is filed under Ransomware, Viruses.

