Cuba ransomware – a ransom-urging malware form that targets English-speaking people
Cuba ransomware is a file-encrypting cyber threat and ransom-demanding virus that targets English-speaking people
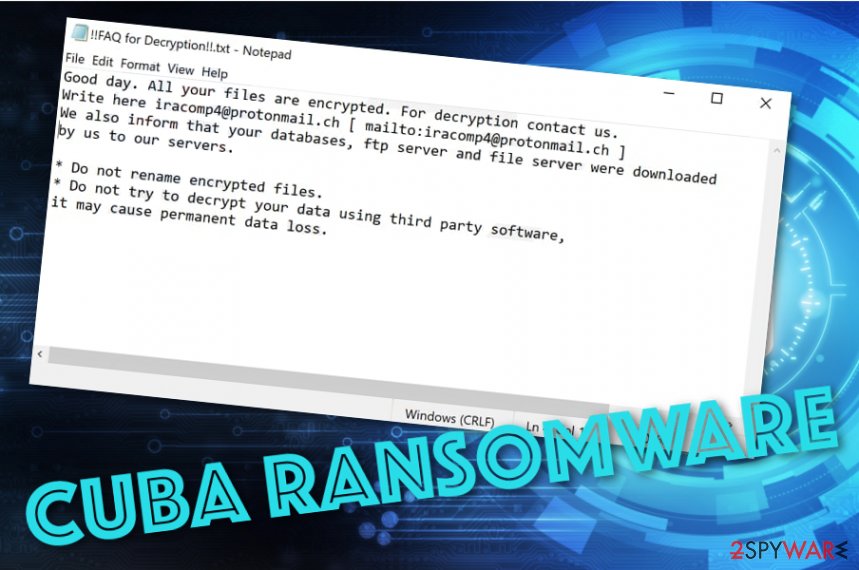
Cuba ransomware is a notorious parasite that uses the RSA-2048 encryption[1] cipher to lock up all the files and documents that are found on the infected Windows computer system. Users have been complaining about this malware adding the .cuba appendix to the filenames of the encrypted documents and including FIDEL.CA as the header of the files. Afterward, Cuba ransomware delivers the ransom note named !!FAQ for Decryption!!.txt or !!! ALL YOUR FILES ARE ENCRYPTED !!!.txt that is written in the English language. The criminals encourage the victims to contact them via [email protected] email address and discuss all the conditions that are related to the ransom price and transfer process. These people also state that the victim’s databases, ftp server, and file server were downloaded to their own servers.
Cuba ransomware tries to gather as many ransom payments as possible. The malware developers claim that the users should not rename their encrypted files or try to recover them with the help of other programs as this can result in permanent information loss. However, note that this type of information is false and using other software might help you to save your files. Nevertheless, you should think if it is worth paying the criminals as they can easily scam you.
| Name | Cuba ransomware |
|---|---|
| Type | Ransomware/malware |
| Danger level | High. The ransomware virus targets personal files and locks them by using a unique key. Also, it can include other malicious pieces of software such as trojans into the computer system |
| Encryption | This piece of malware locks up valuable files and documents by employing the RSA-2048 encryption cipher. It might execute specific commands that search for encryptable components once in a while |
| Ransom note | The infection provides the !!FAQ for Decryption!!.txt or !!! ALL YOUR FILES ARE ENCRYPTED !!!.txt ransom note that is written in the English language |
| Ransom demands | Even though the cybercriminals do not provide particular ransom demands as more information should be revealed after contacting the crooks, these people are likely to urge for anything between $50 and $2000 in Bitcoin or another cryptocurrency that ensures the anonymity of the entire process |
| Contacts | [email protected] email address is provided as a way to contact the cybercriminals |
| Removal | If you have been dealing with this cyber threat lately, you should take action against it as quickly as possible. For the deletion process, use trustworthy antimalware software only |
| Data recovery | Paying the cybercriminals is not the best option as you can get scammed very easily. Rather than taking such a risk, you can travel to the end of this article where you will find some alternative data recovery tips |
| Fix tool | If you have discovered any damaged areas on your Windows computer, you can try repairing them with a tool such as Reimage Reimage Cleaner |
Cuba virus does not provide any particular information related to the ransom demands. However, hackers can ask for a price anywhere from $50 to $2000 or even more. Besides, these people are likely to urge for a cryptocurrency transfer, mostly, Bitcoin. These types of payment processes do not require any personally-identifiable information and the cybercriminals can stay anonymous all the time. This is how the entire ransom message looks like:
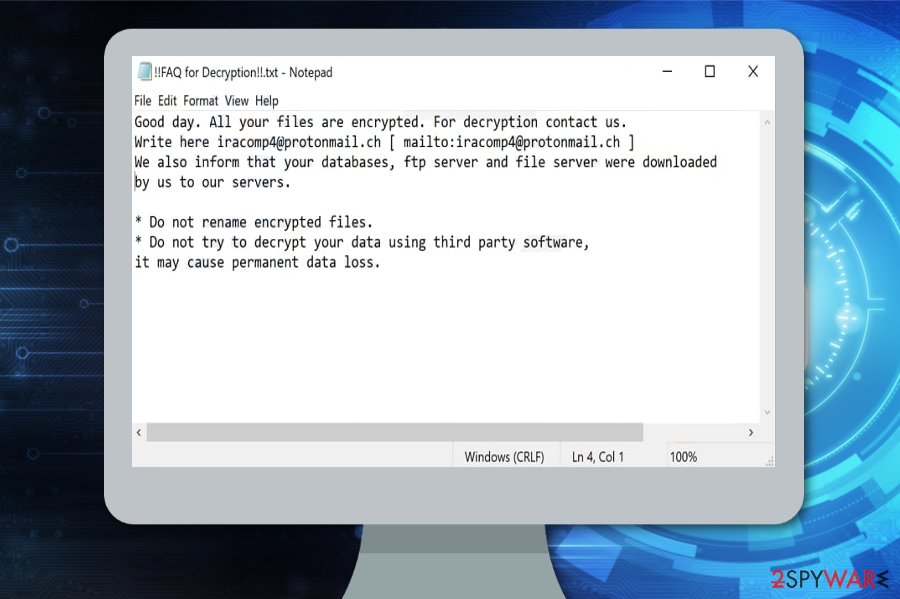
Good day. All your files are encrypted. For decryption contact us.
Write here [email protected] [ mailto:[email protected] ]
We also inform that your databases, ftp server and file server were downloaded by us to our servers.* Do not rename encrypted files.
* Do not try to decrypt your data using third party software,
it may cause permanent data loss.
Cuba ransomware developers cannot be trusted as they might seek to scam you. These people do not care about your needs as their main goal is to collect income from you and distribute their malicious creation towards others.
Cuba ransomware can include malicious processes in the Windows Task Manager and camouflage itself as a legitimate task so that it could remain unrecognized for a longer period of time. Furthermore, you might also see other directories filled with suspicious entries (Windows Registry) and malware-laden files (AppData folder, the User’s folder, desktop, etc.).
Continuously, Cuba ransomware might run a module that scans the entire system for encryptable files once in a while to be sure that no components are missed and kept unlocked. The ransomware virus uses the RSA 2048-bit encryption system to lock up components with the .cuba appendix. For example, if you recently had a file named work.docx, it will be renamed to word.docx.cuba after the encryption process.
Cuba ransomware is a dangerous malware form that uses the RSA-2048 encryption cipher to lock up all the documents and files found on the infected Windows computer system
To harden the recovery of your files, Cuba ransomware might run the vssadmin.exe delete shadows /all /Quiet command via PowerShell service. This task allows permanently removing the Shadow Volume Copies of your locked files and you are disabled to use any type of data recovery software that requires the Shadow Copies to remain available.
Furthermore, Cuba ransomware might try to damage the Windows hosts file[2] to prevent the victim from accessing any security-related websites and forums where he/she might get reliable information on the malware removal process or some data recovery tips. Do not forget to eliminate the hosts file while you are uninstalling the ransomware virus, otherwise, the access will remain blocked.
Cuba ransomware stores both encryption and decryption keys on remote servers that are unreachable for anyone else except the developers themselves. However, this is still not a reason to pay the demanded ransom price. You can check other alternative data recovery techniques that our security experts have added to the end of this page.
Note that Cuba ransomware can be even more dangerous than expected. The malware can be capable of disabling the antivirus protection on the infected Windows computer and turning it vulnerable to other infections. This way you can get your device easily attacked by another ransomware or cyber threats such as trojans.
If you remove Cuba ransomware as soon as you see the first signs of the infection, you will have a bigger chance of avoiding additional malware appearance. The elimination process requires getting rid of all malicious content that has been added by the ransomware virus. For this purpose, employ only reliable security software.
After Cuba ransomware removal, you should try scanning your computer system and looking for possibly-damaged objects. If the malware has included other infections to your computer system, there might be some altered areas or software residing on it. If you are looking for a tool that could help you to fix things, you can try employing Reimage Reimage Cleaner .
The delivery possibilities of malicious payload
Technology specialists from LosVirus.es[3] claim that ransomware viruses are sneaky cyber threats that are hidden in software cracks that are loaded to peer-to-peer networks such as The Pirate Bay, eMule, and BitTorrent. You should avoid visiting these types of web sources and get all of your software and services from reliable developers only.
Furthermore, ransomware infections are intensively pushed through email spam messages and their malicious attachments that come in the format of word documents, excel sheets, and others. The criminals target random people by pretending to be from reliable healthcare, banking organizations, shipping companies, and other well-known firms.
You have to take your security seriously when it comes to email spam.[4] Always try to identify the sender (if the email address is not some type of a questionable one), check the message’s text for possible grammar and style mistakes. Note that reliable companies would not send letters that are filled with writing mistakes. Also, do not open any unknown attachments. If you have already downloaded one, scan if with a malware detection tool at first.
Continuously, the malicious payload is delivered through hacked RDPs. The malware developers can easily access RDP that contains weak security passwords or none at all. So, it is very important to think of strong and reliable passwords that include different letters, symbols, and numbers. In addition, ransomware infections can also be spread through malvertising advertisements, infectious hyperlinks, exploit kits, fake flash player or JS updates.
Cuba ransomware removal instructions
If Cuba ransomware has shown up on your Windows computer system, you should deal with this cyber threat as soon as possible before it brings other malicious infections to your device. If you are having some trouble to detect this infection, it might be blocking your antivirus software. In order to diminish all malicious tasks that are executing on your computer, you should boot it to Safe Mode with Networking or activate the System Restore feature as shown below.
Afterward, you can continue with the Cuba ransomware removal process. It is best to use a trustworthy product as manual elimination includes the risk of making more damage to your computer system or skipping some crucial components that need to be deleted, otherwise, the ransomware infection will show up soon again.
When you remove Cuba ransomware from your Windows PC, you should check the entire system for possible damage that might have been brought by the malware. Accomplish such a task by scanning the entire machine with [d2[ or Malwarebytes. If these products find any corrupted areas, you can try fixing them with repair software such as Reimage Reimage Cleaner .
Remove Cuba using Safe Mode with Networking
To deactivate all of the malicious changes on your Windows computer system and disable the ransomware virus, you should boot the System in Safe Mode with Networking. The entire process is explained below:
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
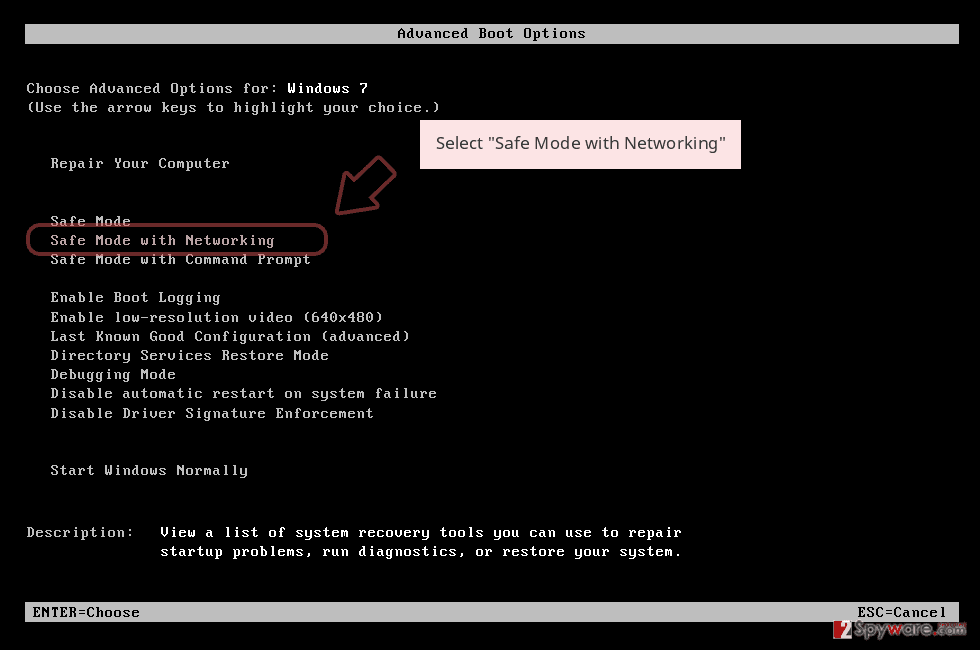
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
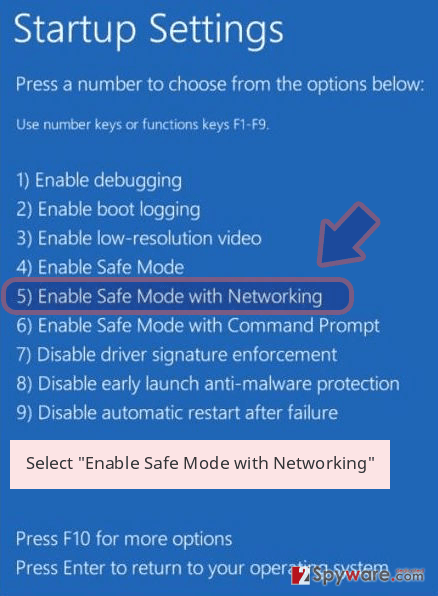
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete Cuba removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove Cuba using System Restore
To diminish malicious settings on your Windows device and bring it back to its previous position, opt for the System Restore feature. If you do not know how to complete this type of step, look at the following guide:
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Cuba from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If your files are encrypted by Cuba, you can use several methods to restore them:
Employing Data Recovery Pro might help you to restore some of your files.
If you have been looking for something that would help you to restore some of your files back to their previous positions, you can try employing this piece of software.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Cuba ransomware;
- Restore them.
Use Windows Previous Versions feature to recover data.
If you have enabled the System Restore function in the past, this method might seem very useful to you. However, you have to complete every step exactly as required in order to reach the best results possible.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
The Shadow Explorer tool might help you to recover some components.
Try using this software if the ransomware virus has made an effect on your files and documents. Keep in mind that this method will not work properly if the malware had erased the Shadow Volume Copies of your encrypted files.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Cybersecurity experts are currently working on the decryption key.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Cuba and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner , SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2020-02-04 at 04:51 and is filed under Ransomware, Viruses.

