CoreSync.exe is the trojan that uses processes and files that run in the background triggering cryptojacking functionalities
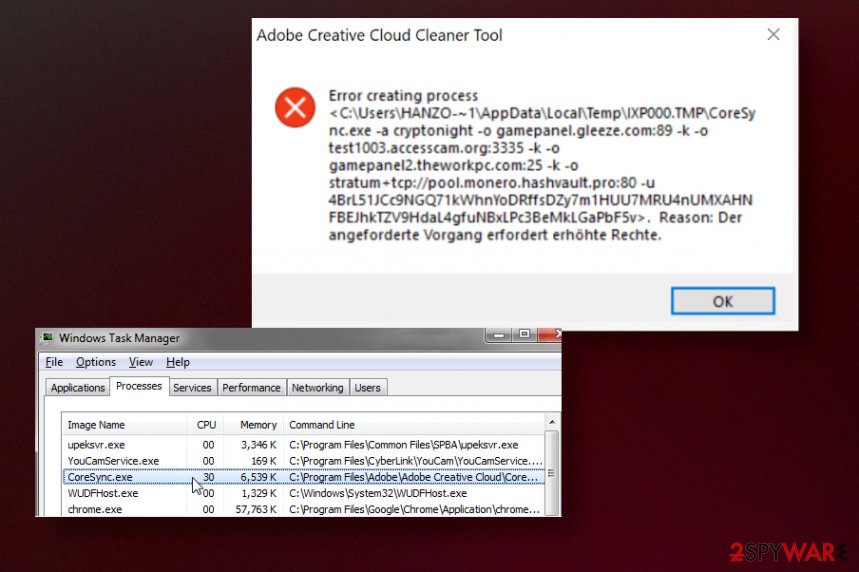

CoreSync.exe – malware that is designed to conceal cryptocurrency mining operations with executable files found in temporary folders. It manages to get on the machine unnoticed and trigger processes without any permissions needed. The trojan launches mining operations that use the resources of the infected computer and makes a profit without interfering with users at all.
However, the threat eventually is noticed by the owner of the computer because background processes cause issues with the performance and speed of a machine and trojan uses exhaustive power consumption, near 200% of CPU and causes attention to those powered.exe or CoreSync.exe files that continuously runs in the background out of nowhere. The rise in the usage of these resources like RAM or GPU triggers issues like overheating. Unfortunately, these issues become noticeable after a while, so malware can run for a long time until the person can guess that there is something wrong.
CoreSync.exe virus is not using your money, accounts, or cryptocurrency funds to get money. However, trojans spread using stealthy methods and can be included in the pack with other malware, act as a backdoor besides mining the cryptocurrency. When malware is present on the system it can lead to more serious infections without you even noticing, so the sooner you clean all the threats, the better.
CoreSync.exe, in general, is the name of a legitimate file belonging to Adobe software. However, users[1] complain about shady processes and CPU or RAM issues. Developers have stated that such symptoms like the high usage of resources and system problems cannot be caused by this software component and that the name is misused by malicious actors to hide the purpose and dangerous behavior.
| Name | CoreSync.exe Trojan |
|---|---|
| Type | Cryptocurrency miner |
| Issues | The file name is related to Adobe software, but more often gets misused as a process to hide malware behavior in the background. When the process uses high CPU or other resources it should be considered potentially malicious or dangerous |
| Distribution | The file can be distributed via torrent services and malicious sites or spam email campaigns when files can be automatically launched on the system and trigger background processes |
| Danger | The trojan relies on computer resources to mine cryptocurrency and makes a profit. It can run unnoticed for a long while and cause damage or even infiltrate other intruders silently |
| Elimination | CoreSync.exe removal is needed when the malware is still running and to ensure that other threats are not left behind. The best way to clean the machine is by using anti-malware tools |
| Placement | If the file is safe it should be found in C:\Program Files (x86)\Adobe\Adobe Creative Cloud\CoreSync. If not, you can be sure that file is disguising the trojan or is related to other shady programs |
| Repair | There is a high risk of system damage and virus-made changes in the system, so rely on Reimage Reimage Cleaner Intego and clear these issues, repair programs, and computer functions safely |
CoreSync.exe can be associated with a cryptojacking malware, but this is the name of the genuine software component. Adobe Acrobat uses this executable as a core synchronizer. When the file is legitimate it should be found in the Program Files folder under the Adobe directory. The first tell-all about malicious purposes should be the placement. If the executable is found somewhere else besides C:\Program Files (x86)\Adobe\Adobe Creative Cloud\CoreSync, you need to consider the file malicious and associated with the trojan.
The safe CoreSync.exe runs the process of synchronization and handles such issues, so you may see it in the background, but not all the time. This file is not an essential file of the Windows system, so you can remove it if it causes any issues or is related to questionable programs or trojan, in many cases. It is a common technique used by malware creators to misuse file names that are popular and ask their malicious activities. This is why crypto mining trojans rise in popularity of malware.[2]
In comparison to ransomware or other financial gains-based threats, cryptocurrency miners are more dangerous and should be considered seriously. Even though there is no blackmailing or direct interaction with the victim, CoreSync.exe makes huge amounts of money. Monero cryptocurrency is the preferred one for this trojan miner. Creators can make fortune and leave the system unnoticed if the process is silent and quick enough. 
CoreSync.exe – a virus that runs in the background and affects the performance because it uses resources of the machine.

CoreSync.exe – a virus that runs in the background and affects the performance because it uses resources of the machine.
That is unfortunate for the user because CoreSync.exe miner trojan can leave some damage or additional malware in the system once it leaves. It is especially dangerous when you cannot detect or find any particular program that causes all the problems and interferes with the performance and speed.
This is why many experts[3] offer to have anti-malware tools up and running more often. You can remove CoreSync.exe sooner and avoid serious damage if your AV tool is launched while the threat is active and not hidden deep in the system. If you experience issues with the speed and performance of the machine trojan may already be running for a while.
CoreSync.exe trojan is focusing on mining the Monero cryptocurrency by running on the processor resources, so constant freezes and crashes are inevitable. Trojan can also exploit some Microsoft processes and evade AV detection because the file is rarely detected as malicious. Especially, when the files dropped by brute-forcing the login credentials of targeted servers.
You still need to employ a professional anti-malware tool for proper CoreSync.exe removal because only such programs can find all related files and applications and fully clear them off of your device. You should also take into consideration that malware can inject malicious files in some folders:
- %AppData%
- %Local%
- %LocalLow%
- %Roaming%
- %Temp%
These changes are not the only ones that CoreSync.exe miner trojan can trigger, so any control that malware has over the system functions or programs can cause issues and errors. You need to repair these changes and recover from virus damage by fixing affected files and programs using something like Reimage Reimage Cleaner Intego.
Silent malware can spread using various ways
Trojans, worms, and other threats that focus on background processes can silently infect the machine and cause all the needs processes to launch without causing any symptoms for the victim to notice. Thrid-party installers and malicious sites can inject malicious payload automatically, so you do not know what happened. When you click on malicious pop-up or banner on the shady page the payload drop is automatic.
It also may happen when JavaScript file downloads actual malware on the computer instead of a pirated program or a game cheat, licensed version of the software. Such files like executables and malicious scripts can be injected and affect the machine from the first launch.
Some of the malicious files can also get on the computer via spam email campaigns when malicious scripts get triggered after downloading and opening the MS document on the machine. Such emails often get disguised as notifications from companies or services, online shopping sites, delivery services, and similar popular companies, so people do not think twice and open the document immediately.
Clear any traces of malware from the machine by running proper CoreSync.exe trojan removal tools
CoreSync.exe virus can run programs and disable existing applications to affect system performance, speed, and AV detection tools. There are some features like Safe Mode that allow bypassing some changes, so enter this mode by following the guide below before you run the anti-malware program.
To remove CoreSync.exe properly, get a professional anti-malware tool or security software like SpyHunter 5Combo Cleaner or Malwarebytes and run the full system scan using those. When all the places of the computer get checked for suspicious or malicious files and programs, you can easily get all the indications and delete threats quickly.
Besides this step of the CoreSync.exe removal, you also need to take care of all the startup and Windows registry alterations that trojans trigger. Some essential files and folders get affected behind your back, so run Reimage Reimage Cleaner Intego to fix the malware damage on the device.
This entry was posted on 2020-05-15 at 04:49 and is filed under Trojans, Viruses.

