AlphaBetaCrypt ransomware – file locking malware that borrowed ransom note contents from Scarab virus developers
AlphaBetaCrypt ransomware is a file locking virus that uses three different encryption algorithms to lock all personal files on the system
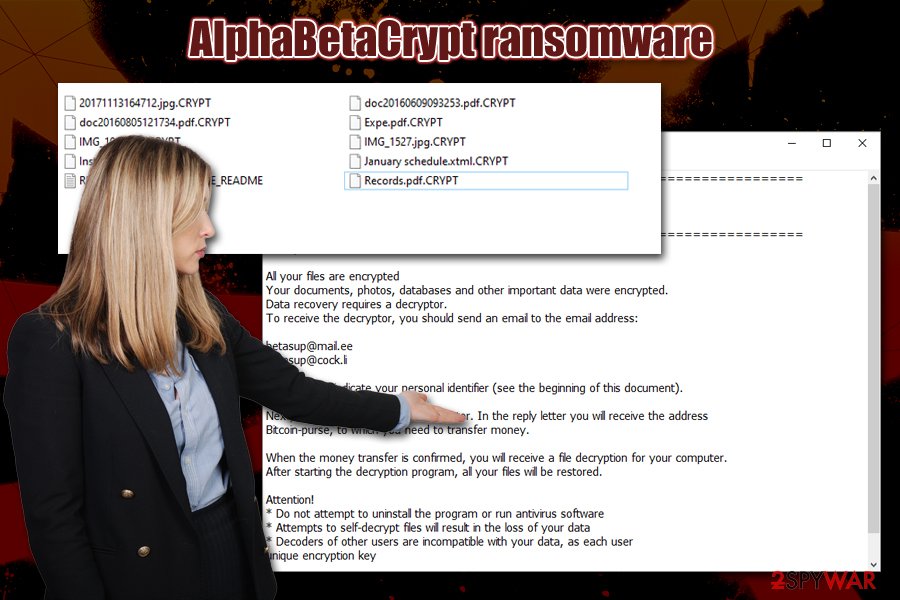
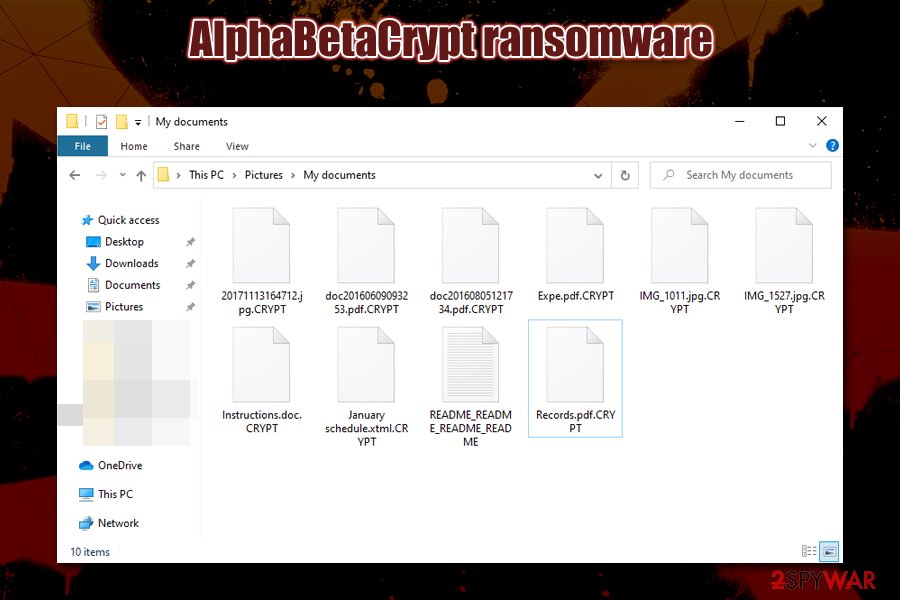
AlphaBetaCrypt ransomware is a file locking virus that emerged in late January 2020. Just as other malware of the same type, upon entry, it modifies the Windows operating system so to prevent an easy recovery and then locks all pictures, documents, databases, videos, and other files. AlphaBetaCrypt virus uses a combination of AES, RSA and Salsa20[1] encryption algorithms to lock data, and appends a .CRYPT extension to each of the modified files. Note that data is not destroyed, but it needs a uniquely-generated key that lies within the attackers’ reach only.
Due to this, hackers can attempt to extort money from users – as long as they are willing to recover the locked data, they are asked to contact crooks via [email protected], [email protected], [email protected], or [email protected] and then transfer the demanded sum into a Bitcoin wallet. While no AlphaBetaCrypt ransomware decryptor is currently available, victims should not rush to pay criminals, as there is a chance of recovering data using alternative methods.
| Name | AlphaBetaCrypt ransomware |
| Type | Cryptovirus, File locking virus |
| Also known as | Alphasup ransomware, Betasup ransomware |
| Relation | It is believed that one of the Scarab ransomware distributors is now delivering this malware |
| Cipher | The malware uses several encryption algorithms during the encryption process – AES, RSA and Salsa20 |
| File extension | Each of the encrypted files is appended with .CRYPT marker, although system and executables are spared from this process |
| Ransom note | README_README_README_README.txt – this file is used to deliver the most crucial information to the victim in order to make the payment smoother |
| Contact | Malicious actors ask users to contact them via [email protected], [email protected], [email protected], or [email protected] emails, attaching the personal identifier |
| Malware removal | Use reputable anti-malware software to get rid of ransomware (in some cases, accessing Safe Mode is required so please check the instructions below) |
| Data recovery |
Due to a combination of various encryption algorithms AlphaBetaCrypt ransomware uses, decrypting the locked files is almost impossible. Options for data recovery include:
|
| System fix | In case your Windows OS is crashing and/or hanging after you get rid of malware, there is a chance that system files were damaged. To fix that, you could use PC repair software Reimage Reimage Cleaner – you would avoid reinstallation of Windows |
While the contents of a ransom note README_README_README_README.txt are seemingly copied from Scarab ransomware, there is no proof that the malware stems from same developers, although researchers believe that one of the distributors of this family is now propagating new ransomware, which was named AlphaBetaCrypt, alternatively known as Alphasup, or Betasup ransomware.
Due to relatively low prevalence, it is yet unknown what distribution methods AlphaBetaCrypt ransomware developers use. Due to possible relation to Scarab, however, we could assume that crooks could use similar tactics, including malspam, exploits, spam emails, etc.
Talking about AlphaBetaCrypt ransomware removal and prevention, we must note that using a comprehensive anti-malware software would stop the malware from entering the system. Currently, over 50 anti-virus engines recognize the threat as follows:[2]
- Trojan:Win32/Skeeyah.A!MTB
- Ransom_Crypren.R002C0GL519
- Mal/Generic-L
- Generic.mg.3c59f8f3d699d368
- Trojan.AgentWDCR.YEH (B)
- Other:Malware-gen [Trj]
- Trojan.MulDrop11.30131, etc.
Once inside the system, AlphaBetaCrypt virus creates an executable that is named randomly and places it into the %TEMP% folder. From there, it launches the malicious file, which begins the infection process of the Windows machine. There are several changes performed on the system that are typical to any ransomware virus, including modification of Windows registry, removal of Shadow Volume Copies, creation of malicious files, termination of certain processes, etc.
Once the system is ready, AlphaBetaCrypt ransomware scans the machine for files to encrypt – it targets most commonly used file types, such as .pdf, .doc, .xlsx, .sql, .mdb, .mp4, .avi, .txt, .jpg, .gif, and many more. Nevertheless, the virus spares system and executable files for it to run, as the main goal of Alphasup ransomware authors is not to corrupt the machine but rather make victims pay for AlphaBetaCrypt decryptor.
AlphaBetaCrypt ransomware is cryptomalware that holds files hostage until ransom in Bitcoins is paid
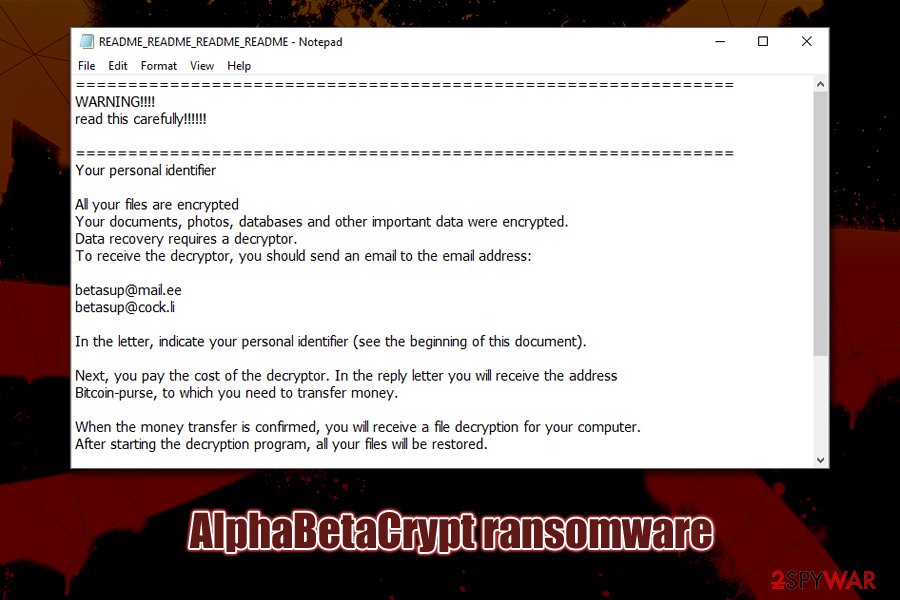
After the data locking process, AlphaBetaCrypt ransomware drops the note which reads:
===============================================================
WARNING!!!!
read this carefully!!!!!!===============================================================
Your personal identifierAll your files are encrypted
Your documents, photos, databases and other important data were encrypted.
Data recovery requires a decryptor.
To receive the decryptor, you should send an email to the email address:[email protected]
[email protected]In the letter, indicate your personal identifier (see the beginning of this document).
Next, you pay the cost of the decryptor. In the reply letter you will receive the address
Bitcoin-purse, to which you need to transfer money.When the money transfer is confirmed, you will receive a file decryption for your computer.
After starting the decryption program, all your files will be restored.Attention!
* Do not attempt to uninstall the program or run antivirus software
* Attempts to self-decrypt files will result in the loss of your data
* Decoders of other users are incompatible with your data, as each user
unique encryption key===============================================================
While some users may think that paying crooks is the only choice, keep in mind that they are criminals who locked your computer files and now demand money – they might never send you the required decryption tool. Therefore, many security researchers[3] recommend avoiding contacting hackers and rather opt for other ways to recover AlphaBetaCrypt ransomware encrypted files.
Before you remove AlphaBetaCrypt ransomware, you should backup all the encrypted data, however, as using third-party tools may permanently damage files. Then, scan your computer with anti-malware software (in Safe Mode if required), and then retrieve your data from backups or make use of recovery tools. If your system keeps malfunctioning after that, you can use repair software Reimage Reimage Cleaner to fix virus damage on your Windows machine.
Malicious actors can use multiple malware distribution methods – protect yourself adequately
Protecting your computer with anti-malware software is a must – those who do not have security tools installed are at the most considerable risk of being infected with malware, including ransomware. Additionally, outdated applications and the operating system can serve as a great way in for hackers – they can abuse vulnerabilities and implant ransomware without users taking any actions. That being said, these two basic protection measures are not enough to avoid most of the malware found on the web.
AlphaBetaCrypt ransomware encrypts data with a combination of secure algorithms, which leaves very little chances victims of recovering data without paying the ransom
The most prevalent techniques for ransomware distribution involve social engineering – spam email (malspam) campaigns infect thousands of users when they open malicious attachments and allow a macro function to run. Therefore, it is imperative not to open attachments or click on embedded links inside suspicious emails. Note that some emails can be compiled well and resemble legitimate ones from high-profile companies like UPS, Amazon, etc., and crooks may also employ email spoofing[4] techniques in order to make the scam more believable.
Another most commonly used tactic is malicious executable files upload to hacked sites, as well as software cracks on warez and torrent sites. Djvu ransomware, which is the most common file locking malware in the wild, uses pirated installers and software cracks as the main distribution method. Thus, never download such dangerous files or always scan them with anti-malware before executing.
You should remove AlphaBetaCrypt virus by using a powerful anti-malware program
Because ransomware rarely uses any persistence mechanisms, AlphaBetaCrypt ransomware removal should not cause most security applications any troubles. In fact, some file locking viruses are known to terminate themselves after performing a file locking process. However, regular users will not know for sure whether the malware is still present on the machine, so it is always recommended to perform a full system scan.
As mentioned above, you should first copy all the encrypted files onto the USB flash or a virtual drive; otherwise, you are risking losing your files forever. If you had backups before the ransomware struck you, however, there is no need to do that, as you can completely recover from this attack (as long as you remove AlphaBetaCrypt ransomware before recovering your data).
This entry was posted on 2020-01-30 at 05:41 and is filed under Ransomware, Viruses.

