Agent Tesla is a dangerous Trojan used by criminals to collect banking information, logins, Wi-Fi passwords, and other credentials

Agent Tesla is a Trojan infection, which exhibits traits of an info-stealer, spyware, keylogger, and RAT[1]. Its history stretches back to 2014 when it has first been introduced as a commercial project or remote access tool on the official download website. Despite attempts to prove legitimacy, a thorough analysis of Agent Tesla malware has proved the fact that it exhibits malicious traits and is usually employed by criminals to steal credentials on the host machine.
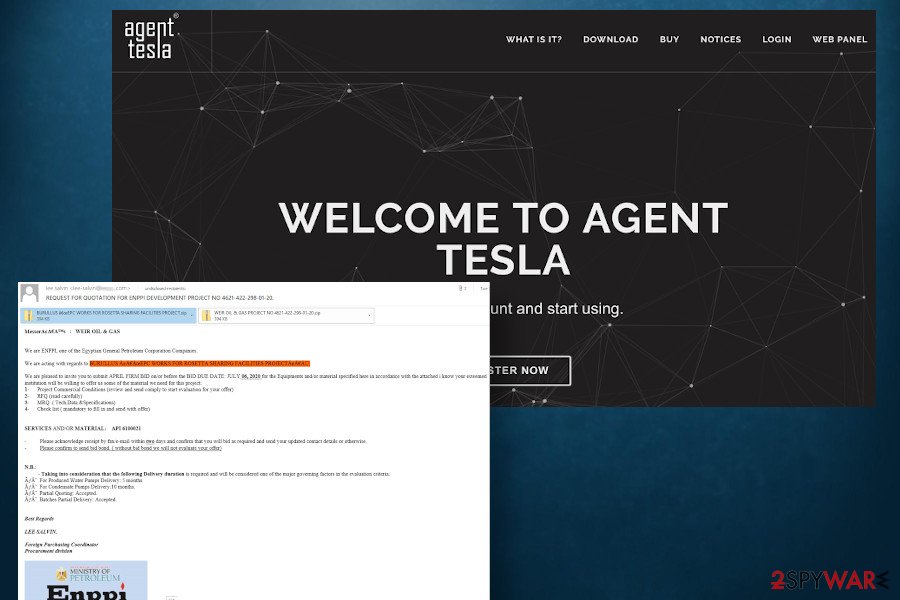
Agent Tesla virus is written on Microsoft’s language targeting Microsoft Windows. Throughout six years of its existence, there were silent and active periods of this trojan, though it manifests a strong tendency to prevail and grow into a cyber threat causing damage to the business, manufacturing, and other public sectors, not only random PC users. At the end of April 2020, the cybersecurity community reported an attempt at Agent Tesla virus attack over OPEC+ related companies settled in U.S., Malaysia, Iran, South Africa, Turkey, Oman, and The Philippines[2]. Using a well-prepared phishing email impersonating shipping company’s report, criminals push delivery_express.exe, which subsequently launches a Trojan and connects to the C2 server for commands.
The primary purpose of the Agent Tesla spyware is to grant access to the victim’s PC and steadily collect login details, passwords, credit card information, and other personally identifiable information. The data stealer is connected to the remote server continuously and, therefore, harvested data is directly transmitted to criminals. Despite that, the latest variant is equipped with a variety of functions for stealing WiFi passwords[3] and extensive information about FTP clients, file downloaders, technical details of the infected machine, web browser information, and others. It is assumed that such information is sought for shifting a trojan to a RAT allowing it to compromise systems connected on the same wireless network.
| Name | Agent Tesla |
| Launched in | 2014 |
| Type of malware | Info-stealer trojan |
| Countries currently targeted | U.S., Malaysia, Iran, South Africa, Turkey, Oman, and The Philippines |
| AV detection | TrojanDropper:Win32/Scrop.7775a842, Trojan.GenericKD.31825418, Malware@#3lamjr6l2l59w, Trojan.Autoit (A), Trojan-Dropper.Win32.Scrop.uod, Artemis!89A43838A083, Troj/Inject-DYW, Trojan.Agent.FA, Trojan.TR/AD.Inject.ejntp[4] |
| Related files | Myfile.exe, RegSvcs.exe |
| Danger level | High. This trojan seeks to gain full access to the target system and subsequently harvest the most sensitive data, such as credit card details and passwords. It is capable of registering keystrokes and transmitting information to C2 server regularly. Besides, it accumulates system and WiFi information helping to initiate future attacks |
| Distribution | Agent Tesla can be downloaded from the official website paying a monthly/yearly subscription fee. However, random PC users are not very likely to use the service for everyday activities. Criminals are using malspam campaigns to spread bulk Agent Tesla trojan payloads. Typically, spam emails contain .exe attachment that asks for the user’s permission to open. The latest attack mimics a famous forwarder, contains tracking numbers, original logos, and other credentials that seem trustworthy |
| Symptoms | A trojan is a very deceptive infection, which runs silently in the system to prolong its persistence. In most of the cases, the system exhibits the following symptoms: high CPU consumption, error messages, longer boot period, unresponsive AV program or other security programs, fake websites on the web browser, etc. |
| Removal options | There is no way to remove Agent Tesla virus manually. Trojans have loads of supportive files that have to be terminated at once. For that, you need to boot into Safe Mode and enable a full scan with SpyHunter 5Combo Cleaner or another professional AV engine. |
| Damage fix | It’s important to restore the system to a state prior to virus infection. Take advantage of the Reimage Reimage Cleaner Intego optimization program. |
Agent Tesla trojan is an extremely dangerous info-stealer, which has been distributed via massive malspam campaigns since 2014. Criminals prepare obfuscated attachments and append them to tricky email messages that are subsequently sent to random PC users. Based on the information collected, it seems that Agent Tesla virus spreads in disguise with the following spam emails:
- Requests for urgent quotations;
- New order excel sheets asking for permission to enable it;
- Rogue TNT Express delivery notifications;
- DHL Express tracking information;
- Bank swifts for balance checking;
- On-Demand delivery confirmations;
Opening an attachment grants Agent Tesla keylogger access to the system. Right after successful infiltration, the malware launches its payload and drops RegSvcs.exe process, which is responsible for enabling both RAT and keylogging functions. Criminals exploit vulnerabilities and start stealing the user’s credentials, system-related information, and WiFi information.
The Agent Tesla removal may be a difficult task to perform. There is no way to eliminate this data-stealing trojan as it attempts to gain administrative privileges, can disable Windows User Account Control, Task Manager, cmd.exe, msconfig.exe, Start menu items, and other functions. Besides, it is cable of causing regular shutdowns preventing the victim from launching the AV engines.
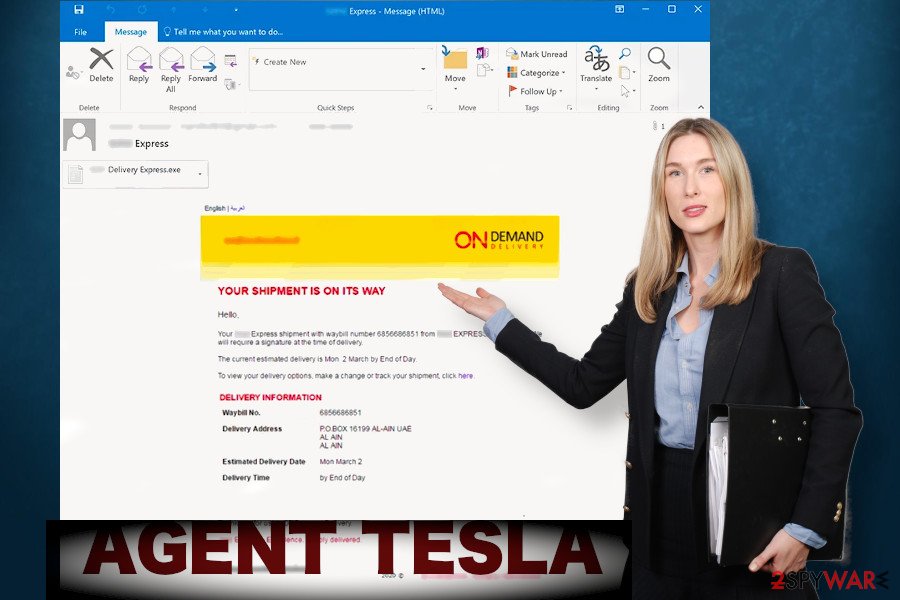
Agent Tesla spreads via malicious spam email attachment. The user has to give permission to open the attachment

Agent Tesla spreads via malicious spam email attachment. The user has to give permission to open the attachment
Even though the above-mentioned activities may not be initially manifested, it may be difficult to detect and remove Agent Tesla because it replaces legitimate system files and keep entries within C:\windows\system32\.
Manual Agent Tesla is not possible in any way, experts from virukset.fi stress[5]. It’s critical to eliminate it as soon as possible to minimize the amount of data leaked. The longer the RAT remains on the system, the more credentials, system logs, WiFi connections it can transmit to criminals. The safest way to get rid of it is to restart the system into Safe Mode and run a full system scan with a powerful anti-virus program.
Initiating active malspam campaigns the malware ranks second in most prevalent threats ranking of 2019
Agent Tesla malware has been actively spreading since 2014 and does not lose ground up until now. It has been ranked second by Any.Run research and labeled as the most proliferate virus of 2019. As the analysis has shown, cybersecurity researchers detected over 10,000 Agent Tesla samples.
Moreover, it keeps exhibiting great performance within March and April 2020. During these two months, experts revealed multiple malspam campaigns targeting not only regular users but also giant companies, such as OPEC and other oil and gas producers.
The virus receives updates regularly and shifts its target. Currently, experts stress the tendency of this new Agent Tesla virus variant to steal WiFi password, VPN, FTP credentials, system registries, and similar. Such a shift raises anxiety since a focus on the WiFi module indicates plans of criminal to rearrange the info-stealer malware into a WiFi worm.
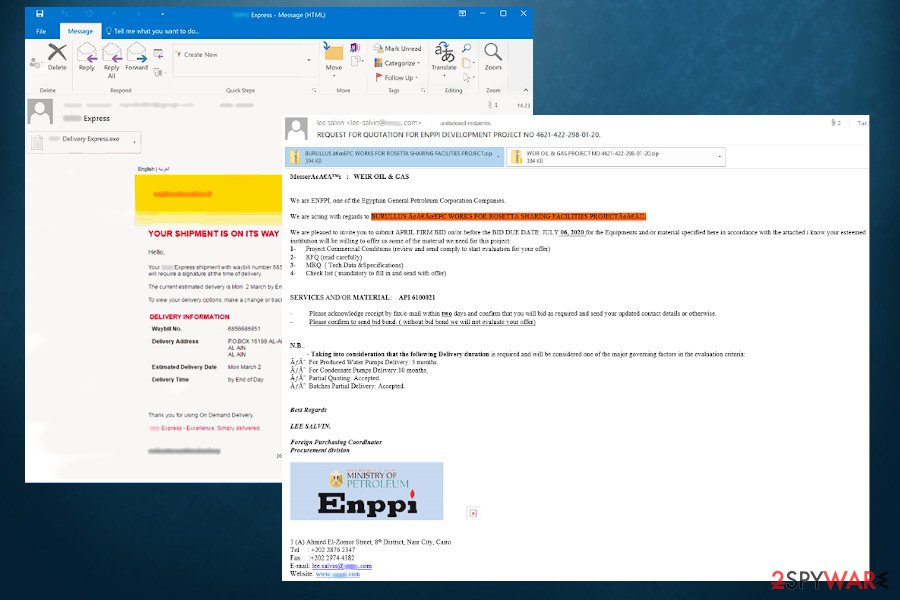
Agent Tesla is being distributed in the disguise of well-known companies, such as DHL, FedEx, Red-Cross, and similar

Agent Tesla is being distributed in the disguise of well-known companies, such as DHL, FedEx, Red-Cross, and similar
Advanced malspam campaigns allow the trojan to attack thousands of unsuspecting users
The criminals behind this malware are taking advantage of malspam campaigns, which rely on botnets. Having a database of leaked email addresses, crooks launch catchy email messages and transmit them to thousands of users. Currently, the trojan is targeting Aerofox Foxmail, Claws Mail, Microsoft Outlook, Opera Mail, IncrediMail, Pocomail, Becky! Internet Mail, ICQ Transport, Mozilla Thunderbird, The Bat! Email, though others are not safe either.
Typically, spam emails come as order confirmations, delivery notes, invoices for payments, and similar. Crooks prepare them identical to well-known companies, such as DHL, TNT, FedEx, health care institutions, and similar. Spam will always contain an attachment in one of the following formats:
- ZIP
- CAB
- MSI
- IMG
- Office document
The campaign detected last week by FortiGuard Labs misuses On-demand delivery notification from a freight forwarder. The notification says:
ON DEMAND DELIVERY
YOUR SHIPMENT IS ON ITS WAYHello,
Your *** Express shipment with waybill number 6856686851 *** EXPRESS is on its way. We will require a signature at the same time of delivery.
The current estimated delivery is Mon 2 March by End of Day.
To view your delivery options, make a change or track your shipment, click here.
DELIVERY INFORMATION
Waybill No
Delivery Address P.O.BOX 16199 AL-AIN UAE
AL AIN
AL AIN
Estimated Delivery Date Mon March 2
Delivery Time by End of Day
Thank you for using On Demand Delivery
*** Express – Excellence. Simply delivered.
This rogue email contains a *** Delivery Report.exe attachment, which once clicked asks for permission to edit. Permission granting enables AutoIt executable, Exe2Aut, and myAut2Exe tools, which subsequently enables the malware.
Unfortunately, these messages are really credible, and more gullible people can easily fall for opening them. Therefore, to keep the system from malware infections via spam emails is to ensure the full protection of the system. Typically, professional antivirus programs are offered in a pack with email filters, IPS services, and AV engines.
Thus, make sure to update your security tool with the latest virus definitions so that it would lapel phishing emails as spam, block *** Delivery Report.exe attachment due to malicious traits, and detect traffic (Spyware.Agent.Tesla) where stolen information is set to be sent,
A guide on how to eliminate Agent Tesla from the infected PC
As we have explained above, the info-stealer trojan features the traits of keylogger, and RAT is very dangerous and requires immediate forces for its removal. Agent Tesla removal may be very difficult since it can disable Task Manager, cmd.exe, msconfig.exe, Start menu items, disable the antivirus program to hide its traces, and prevent detection.
The sooner you remove Agent Tesla, the lower is the risk of exposing your credentials to criminals. The only way to get rid of it is to launch an AV scanner. It’s very likely that you will not be allowed to launch it due to compromised processes and files, so you should restart the system into Safe Mode and try again. In case of a failure, try to download an alternative AV program while in Safe Mode. We recommend relying on tools like SpyHunter 5Combo Cleaner or Malwarebytes.
Keep in mind that the latest variant of this trojan has a feature os a RAT, meaning that it may spread via WiFi network and affect PCd that are connected on the same network. A full guide on how to remove Agent Tesla malware from Windows.
This entry was posted on 2020-05-05 at 05:28 and is filed under Trojans, Viruses.

