ABCD ransomware is a file locking malware that mostly attacks businesses via weakly-protected Remote Desktop connections
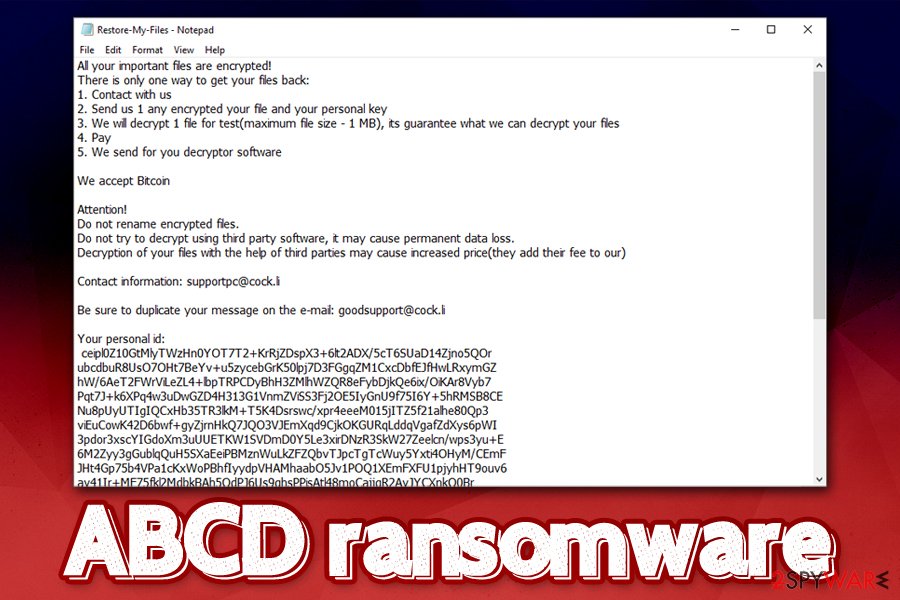
ABCD ransomware is a type of malware that locks all data on the host machine and the connected networks and then demands ransom of up to 3 BTC for the decryption tool
ABCD ransomware is an emerging crypto-malware that has been spotted attacking several companies around the world since mid-October 2019. Initially, security researchers could not identify the ransomware correctly, although later, it became apparent that the malware stems from MegaCortex and LockerGoga ransomware – threats that have been operated by successful hacking groups.
Since the main targets of ABCD ransomware are organizations, its primary distribution method is RDP (Remote Desktop Protocol). Once the malicious executable is executed, the malware starts its infection routine, consequently encrypting all local and networked files with the help of AES,[1] and appending .abcd marker to each of them. To recover data, victims are informed via the ransom note Restore-My-Files.txt that they need to contact threat actors via the email (depends on the version, but so far, the provided contacts were [email protected], [email protected], [email protected], [email protected], and [email protected]) and pay the ransom in Bitcoin.
While some victims claimed that they received ABCD ransomware decryptor from the attackers after paying the demanded sum, it is best not to trust the attackers and instead use alternative methods provided in the bottom section of this article.
| Name | ABCD ransomware |
| Type | Cryptomalware, file locking virus |
| Family | After initial confusion, it was determined that this malware is a variant of MegaCortex and LockerGoga |
| Distribution | Usually spread via unprotected or poorly protected RDP connections |
| Malware launcher | Ricks75.exe (may vary) |
| Secondary payloads | Infected machines are injected with a legitimate application Process Hacker 2 |
| Encryption algorithm | Malware uses AES cipher to encrypt all data on the machine and its networked drives, skipping system and executable files |
| Appended extension | Each file receives .abcd extension. Example of an encrypted file: picture.jpg.abcd |
| Ransom note | Restore-My-Files.txt text file is dropped into most folders on the system |
| Contact | Victims are asked to contact criminals for ransom negotiations via [email protected], [email protected], [email protected], [email protected], or [email protected] emails |
| Detection |
Multiple AV vendors detect malware sample on Virus Total as follows:
|
| File decryption | The only secure and free possibility of retrieving the locked data is via backups. Paying ransom to criminals is not recommended, although some might have no other choice. Nevertheless, a small chance exists to recover data with the help of third-party recovery software |
| Malware removal | Download reputable anti-malware software and perform a full system scan in Safe Mode as explained below |
| Recovery | Ransomware modifies system files – this could cause issues after it is eliminated, such as errors, crashes, and similar. To fix virus damage, we suggest using Reimage Reimage Cleaner |
While it is most likely that ABCD ransomware is spread via the RDP connections, it does not mean that other methods are not used by hackers as well, such as spam emails, fake updates, software cracks, exploits,[2] etc. Thus, it is important to understand that securing just one point of entry is not enough, and comprehensive security solutions should be applied to avoid infiltration.
Upon infiltration, ABCD ransomware does not immediately begins the infection routine, but first performs the necessary preparations:[3]
- Deletes Shadow Volume Copies with the help of “vssadmin delete shadows /all /quiet” command.
- Disables Windows startup repair function.
- Installs Process Hacker 2 – originally a legitimate application that is used to monitor system resources, detect malware, and debug software.
- Modifies registry files.
- Spawns many different processes, etc.
It was reported that ABCD ransomware attempts to infect all the computers on the connected network and encrypt data on all the connected servers. Besides, it also tries to access virtual backup systems like Dropbox and deleting backups from there. Considering the Shadow Volume Copies are deleted as well, encrypted data recovery becomes even more complicated. Due to its advanced functionality, even ABCD ransomware removal might not be successful.
After that, ABCD ransomware all data located on the machine, as well as all the networked drives, and drops the ransom note for information purposes. Ransom note contents are as follows:
All your important files are encrypted!
There is only one way to get your files back:
1. Contact with us
2. Send us 1 any encrypted your file and your personal key
3. We will decrypt 1 file for test(maximum file size – 1 MB), its guarantee what we can decrypt your files
4. Pay
5. We send for you decryptor softwareWe accept Bitcoin
Attention!
Do not rename encrypted files.
Do not try to decrypt using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price(they add their fee to our)Contact information: [email protected]
Be sure to duplicate your message on the e-mail: [email protected]
Your personal id:
Some victims who paid for ABCD ransomware decryptor claimed that their files were successfully recovered their data. However, there is always a risk when communicating with malicious actors, as they are not always willing to cooperate, and might ask for even more substantial sums. As reported by affected users, hackers are eager to ask as much as 3 BTC, regardless of how many computers or servers were encrypted.
ABCD ransomware is crypto-malware that stems from MegaCortex and LockerGoga families, both of which are known from targeted attacks against organizations and businesses
Thus, you should backup all the encrypted files, remove ABCD ransomware with anti-malware, and then attempt to recover data by using alternative methods provided in our recovery section below. Additionally, if you experience system crashes and frequent error messages post-removal, you could use Reimage Reimage Cleaner to fix virus damage and avoid the re-installation of Windows operating system.
Poorly protected RDP connections serve as an entry point for malware authors
Remote Desktop Service is a great feature implemented by Microsoft – it allows users to connect to computers remotely over a network connection. The system is often used by various businesses, although regular users can also find it useful in certain situations. However, many companies still fail to protect such connections correctly. Due to its prevalence and weak protection practices, RDP became a go-to choice for malicious actors who are planning targeted attacks against organizations and businesses.[4]
In most of the cases, the required credentials to bypass authentication are either acquired on the underground forums, or by applying the brute-forcing technique with automated software. Once inside, attackers typically disable all the defenses and delete backups (if accessible), deploying ransomware payload after.
To adequately protect your RDP, industry experts[5] advise the following:
- Do not use default TCP and UDP port 3389.
- Limit the access to RDP to only those who actually need it via Group Policy Management Console.
- Protect the connection with a strong password to prevent brute-forcing.
- Disable RDP when it is not used.
- Enable Network Level Authentication (NLA) via System Properties.
- If possible, use Remote Desktop Gateway Server for extra security.
As evident, general security practices like comprehensive security solutions, regular system patching, backups, and other precautionary measures should always be adhered to as well.
ABCD ransomware removal and file recovery solutions
When it comes to ABCD ransomware decryption, there is not much that the infected users can do if no backups were prepared and isolated before the attack. It is always worth trying third-party recovery software, but there are no guarantees that it will work (in some cases, at least a portion of locked files can be recovered if the host computer was not used as much post-infection). Before trying alternative methods, ABCD ransomware removal should be executed to void repeated data encryption.
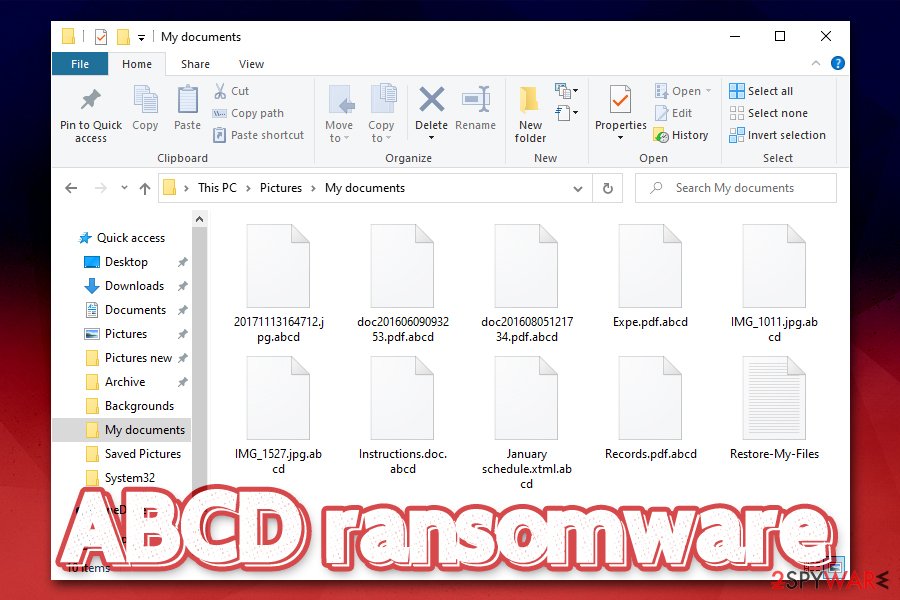
Once files are appended with .abcd, the only secure way to recover them is via data backups
Note that, when you remove ABCD ransomware infection, you might permanently damage encrypted files, and even a working decryptor would no longer function. Thus, make sure you backup all the encrypted data before doing everything else. For that, you might have to access Safe Mode with Networking, as ABCD virus might try to prevent its termination by disabling AV software.
Besides using recovery software, the other two options are paying criminals or waiting until security researchers discover bugs within the ransomware code and create a working ABCD decryption tool. Depending on many different factors, this might or might not happen. Therefore, it is always up to you to device what is the best solution in this rather difficult situation. As evident, if backups are available, it is the only recovery method you should go for.
Remove ABCD using Safe Mode with Networking
In case of ABCD ransomware is interfering with your anti-virus, you can enter Safe Mode with Networking to bypass malware’s functions:
- Windows 7 / Vista / XP
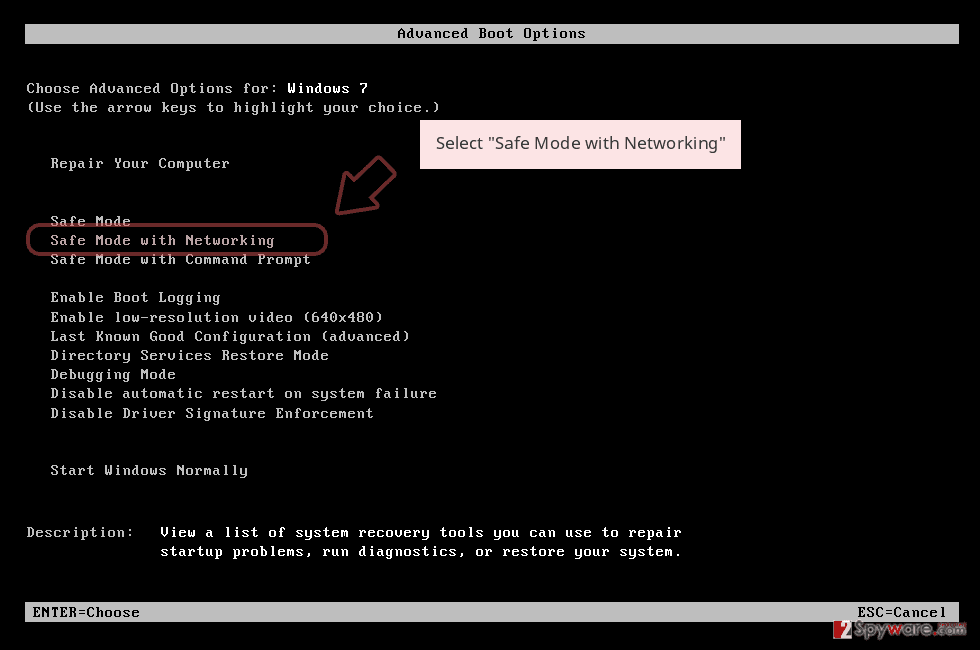
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
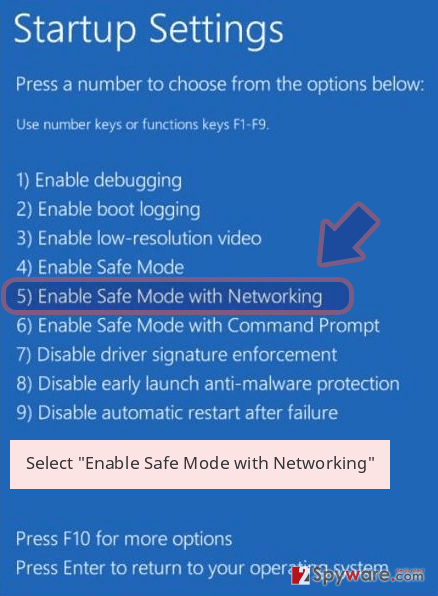
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete ABCD removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove ABCD using System Restore
System Restore is another way to delete malware:
Bonus: Recover your data
Guide which is presented above is supposed to help you remove ABCD from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If your files are encrypted by ABCD, you can use several methods to restore them:
Data Recovery Pro is a tool that may work
As previously mentioned, the less you have used your computer post-infection, the more chances are to retrieve healthy copies of files from the hard drive with tools like Data Recovery Pro.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by ABCD ransomware;
- Restore them.
Make use of Windows Previous Versions Feature
This method can only work if you had System Restore enabled.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer might recover all the encrypted data
ABCD file virus is programmed to delete Shadow Volume Copies. If this process fails, there is a high chance of restoring all files with the help of ShadowExplorer.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
No decryption tool is currently available
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from ABCD and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner , SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2019-12-19 at 07:34 and is filed under Ransomware, Viruses.

