Zoom virus is the term used to describe various methods that hackers tend to misuse the name of a legitimate video conferencing platform


Zoom virus is the generic name that defines unwanted programs, trojans and phishing campaigns delivered with the help of content related to the Zoom application or services. The platform is legitimate and safe to use video communications service, but the popularity of this site also made it more popular among malware creators. Since the bigger part of the world turned to online services due to the COVID-19 pandemic in 2020, the popularity of this platform raised to the top.[1] The accessibility, free services, cross-platform features made the product and company a target of malicious campaigns. As users turn to the platform, malicious actors do the same but in a different way.
There are many campaigns spreading trojans that fall to the category of Zoom virus and phishing campaigns that use the name of the platform to mimic the legitimacy and deliver wanted remote tools and infect the machine with different malware. Due to more common research and analysis, it got revealed that hackers manage to hack this program and can proliferate various attacks using flaws in the service. Zoom-bombing also is a huge issue that even government institutions note users all over the world.[2] There are various ways how you can get exposed to malicious content or even encounter hackers during the video conference on the Zoom platform, but there are also ways to avoid such exposure and keep yourself safe while studying or working remotely online.[3]
| Name | Zoom virus |
|---|---|
| The relation | Zoom video conferencing platform that is completely legitimate and not containing malware. Criminals create various campaigns and spread their products using hacked sites with the same name or can hijack video chats to send links to malware delivery services |
| Possible types |
Trojans, malware, phishing emails, potentially unwanted applications |
| Variants |
|
| Danger | People fall for scams and campaigns claiming to be associated with the legitimate Zoom product and can install trojans, password-stealing malware or useless programs without even noticing. Not paying attention to the content and senders of emails or chat messages can lead to issues with privacy and the computer, in general |
| Distribution | Malicious emails, deceptive or hacked pages, mimicking the official Zoom platform site. Links placed in chatrooms and on emails, other intruders, fake installers |
| Elimination options |
Zoom virus removal differs from the type of malicious campaign you have encountered, but the best option is the full system scan using anti-malware tools that can detect and delete various intruders and clean the computer from any additional malware or possibly dangerous content |
| Ways to avoid |
You should always check if the source of the program or the site you are using is the legitimate and official website to be sure that there is nothing even potentially dangerous associated with the service. |
| System repair | You should go through the system folders with Reimage Reimage Cleaner Intego too, so any virus damage or additional malware traces and changes get fixed. Alterations in such parts of the device can affect the performance significantly |
Mimicking the legitimate page and providing users with malware is typical behavior of malicious actors, so such a version of the Zoom virus was released when the platform started to gain recognition. However, additional campaigns surfaced when quarantine in the bigger part of countries was announced, and people started to work, study and live online.
Social engineering is the method that allows criminals to spread their phishing sites and other versions of Zoom virus. When the person believes that the page is a legitimate platform and manages to register the needed account the victim gets exposed. The name, email address, phone number, location, credit card credentials, and other private details are revealed during the account setup. In most cases, this information is automatically collected, the person is not getting any Zoom services, and data gets used by third-party companies yr criminals in later campaigns, targetted attacks.
Another issue that people may be frustrated about and look for ways to remove Zoom virus is direct video conference hijacking and bombing that hackers may start. Phishing links or even remote hacking triggering hyperlinks can get dropped directly in the chat.[4] Also, hackers can show various material in hijacked conference calls and expose kids and minors to pornographic content. This is one of the few flaws in the platform itself that can get exploited by malicious people.
There is nothing malicious about the Zoom platform, but you need to consider these possibilities to get a virus installed instead of the machine yourself but not paying enough attention. Also, some of the security flaws that the service has might get exploited, but you can manage the safety and control your connections, ensure the security of the internet and maintain the device, so there are fewer ways for the hackers to end up on the computer.
These recent Zoom virus campaigns focus on people that are at home during the COVID-19 quarantine, so make sure to keep yourself safe and pay more attention online than before. Criminals try to take advantage of various people that turn to shop sites online and use platforms like Netflix and Hulu, rely on social media more than before. Don’t lose your attention span during the lockdown and try to stay calm and protect your privacy with professional AV tools and tools like Reimage Reimage Cleaner Intego that can provide an area of optimization ad repair functions. 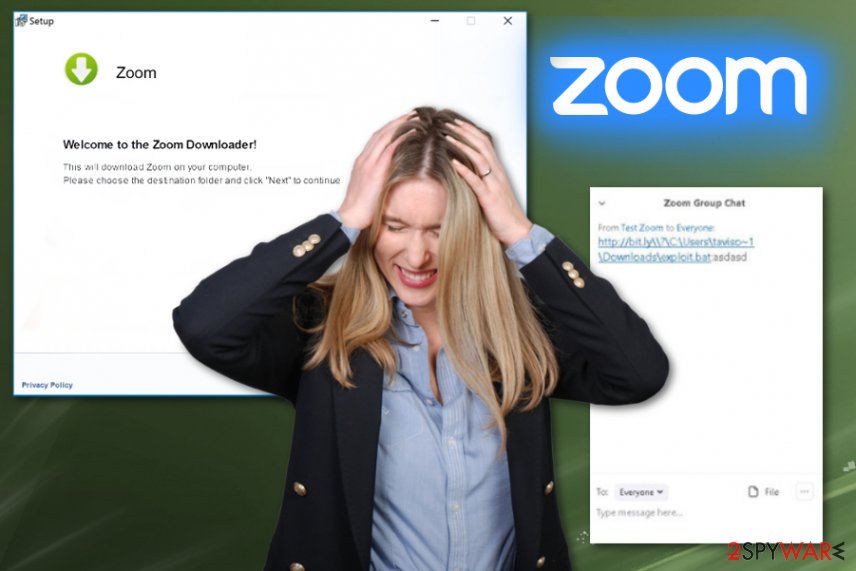
Zoom virus is not the threat that the platform has it is the way malicious actors managed to misuse the name of legitimate service.

Zoom virus is not the threat that the platform has it is the way malicious actors managed to misuse the name of legitimate service.
Zoom malware variations depending on criminals’ goals
Zoom virus version was noticed to spread around via fake application installers and sites that supposedly delivers the Zoom program. The executable file of the installer named zoom-us-zoom.exe[5] with variations of additional characters for identification is launched via InstallCore installer which then installs the software. This is how adware, browser hijackers, and other programs like trojans or ransomware land on the computer.
It is known that such Zoom applications are used to spread info-stealing malware and get distributed around via fake Zoom websites. The number of similar domains registered with Zoom name rising every day. In most cases, disguised as official third-party sites pages claim to offer free downloads of the legitimate app. Once the user falls for the scam and allows the download, the person receives malicious content.
These phishing Zoom virus sites also use methods that allow stealing passwords directly from the website when people register their accounts with names, emails, credit card information links banking account details. Malicious installers and pages can resemble the legitimate platform because actors use official logos, colors, claims that the company has on the official domains and installer setups. The only official site of the free ZOOM platform is zoom.us.
Do not fall for any promotional ads that offer free services or suggest to install the app. You may install the Zoom virus without noticing it. Always rely on official sites, App Stores, and software providers that state all the important information in their Privacy Policy where you can read about the company and the product.
Take note of sites that claim to provide Zoom application that also has:
- advertisements of various different products or unrelated sites;
- creates redirects, pop-ups with ads;
- a domain that includes more than the name of a company or app;
- encourages to allow or agree to additional content or triggers the download right away.
You may notice that zoom.us is listed as the developer or that the program is certified wy Windows OS or macOS providers, developers. There are many claims that malicious actors can use to trick you into installing the rogue app or trojan, so you will need to perform Zoom virus removal in the future without knowing that the malware is on the PC. 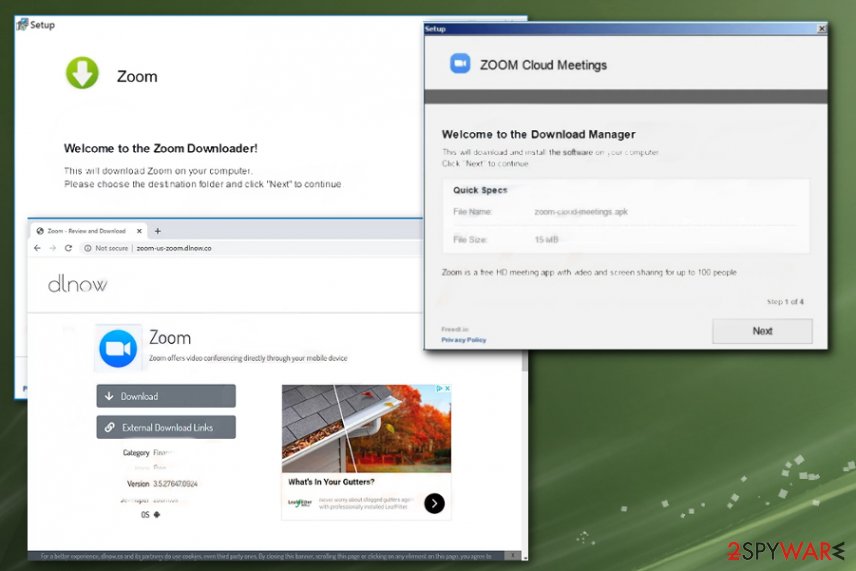
Zoom virus is the malware that uses the legitimate name of a video conferencing page to attract all the users since the service gained more popularity.

Zoom virus is the malware that uses the legitimate name of a video conferencing page to attract all the users since the service gained more popularity.
Ways to keep yourself safe online
These campaigns that deliver malware can go various ways because paying attention to sources where you download programs and use the service can determine the security and ensure privacy. Use only official sources, providers’ sites, and real EULA and other statements. Do not reveal your personal data on sites that you are not sure about and avoid clicking on any links and files attached to suspicious emails.
Since emails can contain malicious file attachments and hyperlinks to direct phishing pages, you need to pay attention to senders, avoid clicking on any suspicious notifications, do not open the email that is not expected. Clean the email box more often and pay attention to anything that appears on the screen out of nowhere.
Additional tips for your virtual meetings:
- use private meeting options and do not allow other people to get on the conference;
- share the link to meeting directly to participants only;
- limit screen sharing to avoid unwanted content appearing on the screen;
- make sure to update software and tools to avoid any bugs.
Get rid of any traces of the Zoom virus or another threat with AV tools
You should consider that your machine is affected by the Zoom virus if you encounter any strange activities and notice that the machine is not running as it supposed to. The full cleaning process with SpyHunter 5Combo Cleaner or Malwarebytes can detect all the threats that manage to affect your device, including trojans and other programs that run in the background.
Zoom virus removal is the process that anti-malware tools are designed for, so when the program finds the malware and suggest to delete that from your computer or even mobile device – do so. Follow the suggested sets and eliminate any possibly dangerous intruders. This method works for rogue tools and for ransomware infections.
To remove Zoom virus from the mobile device, you only need to get an official AV tool from the App store that is compatible with your OS. After all these malware termination procedures, run Reimage Reimage Cleaner Intego for the double-checking and virus damage repair. Follow the guide for additional tips.
This entry was posted on 2020-04-03 at 04:47 and is filed under Malware, Viruses.

