Win64:malware-gen – heuristic detection of some antivirus providers that is used to describe a Trojan
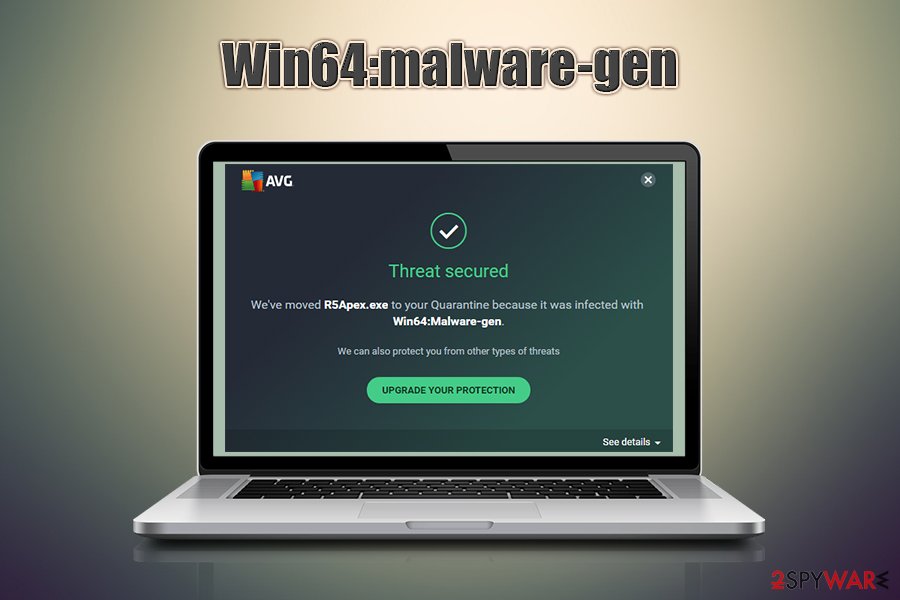
Win64:malware-gen is malicious software that can steal information, install other malware, and perform a variety of other harmful tasks on the infected system

Win64:malware-gen is malicious software that can steal information, install other malware, and perform a variety of other harmful tasks on the infected system
Win64:malware-gen is a detection name for a type of malware known as a Trojan. Trojans are among one of the most prevalent and versatile threats around, as their nature and working mechanisms can deffer vastly, although all of them have one thing in common; users get infected with a Trojan when they open a malicious file, believing that it is actually legitimate, e.g., a software crack or a spam email attachment.
In most cases, users encounter Win64:malware-gen pop-up via their security tools, most commonly, various Avast products. While most of such threats are quickly eliminated by the anti-malware, there are several issues with heuristic-based detection. For example, many users complained that legitimate files are being tagged as malicious or that the detection reoccurs on a regular basis.[1] These inconsistencies are common when it comes to generic malware analysis as Win64:malware-gen, and each of the cases which provides some types of difficulties should be investigated carefully.
| Name | Win64:malware-gen |
| Type | Trojan, false-positive |
| Infiltration | Trojans can be spread in many different ways, including spam emails, pirated software installers, software cracks/keygens/loaders downloaded from torrent sites, malicious links, fake updates, etc. |
| Capabilities | Trojans can perform a variety of malicious tasks on the infected machines, including sending spam, stealing sensitive information, taking screenshots, injecting other malware, and much more |
| Risks | In most cases, the infection can lead to financial losses, infiltration of other malware, data loss, sensitive data disclosure and even identity theft |
| Similar heuristics | Win32:Malware-gen, Trojan.genericKDZ, Other:Malware-gen [Trj], IDP.Generic, Trojan.Win32.Generic, etc. |
| Removal | Perform a full system scan with anti-malware software |
| Recovery | Reset all the installed web browsers, change passwords, monitor your online banking and fix Windows issues with tools like Reimage Reimage Cleaner Intego |
Anti-virus software uses several methods to detect malicious software on your computer, including signature-based, machine learning, sandboxing, application whitelisting, heuristics, etc. Win64:malware-gen belongs to the latter category. This method looks at software behavior rather than checking signatures within the database, which ensures higher detection rates and stopping of the newest malware samples.
However, due to the principle of its operation, Win64:malware-gen detection also falls victim to a relatively high rate of false-positives.[2] This means that legitimate files can get flagged as malicious as soon as it introduced to the system or after an update to security software or the detected app is applied. In such a case, it is worth making an exclusion within the security application and updating it, which would remove Win64:malware-gen from the list of malicious files.
If you have doubts about a particular file that you believe to be legitimate, you should either contact the developer of software, as well as the anti-virus and clear things out about it. Additionally, you could also perform a scan with alternative anti-malware software to check whether Win64:malware-gen Trojan detection is correct. Finally, you can also use free analysis tools like Virus Total – simply upload a file and check its detection rate.
Win64:malware-gen removal should be performed as soon as possible if the detection is not a false-positive. Trojans are particularly dangerous, as they can be equipped with an array of different functions. There are thousands of new malware samples released each day, so heuristics are one of the best ways to determine malware of such type.
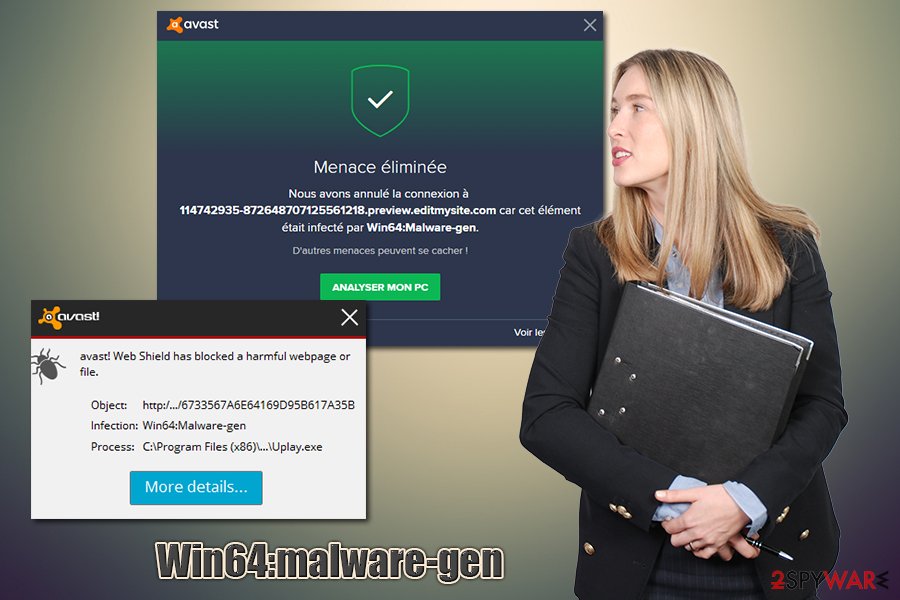
Win64:malware-gen is a heuristic detection of a Trojan horse, although can also identify a false-positive

Win64:malware-gen is a heuristic detection of a Trojan horse, although can also identify a false-positive
In case no anti-malware software is installed on the targeted system Win64:malware-gen can cause significant damage to it, as well as the end-user. Here’s what Trojans are capable of:
- Install other malware;
- Give cybercriminals a remote access via the compromised PC;
- Use the infected computer as a spam tool;
- Take screenshots;
- Steal sensitive information such as logins, banking details, Social Security Numbers, etc.;
- Deliver intrusive advertisements;
- Include the host into a botnet, etc.
Repeated detection might also occur when an anti-malware app is incapable of eliminating all the malicious files, when particular background connections are established, or when the Win64:malware-gen virus attempts to destroy the security app’s functionality. In such a case, you should access Safe Mode with Networking and perform a full system scan from there.
Additionally, since Trojans are considered to be serious types of infection, you should also take care of fixing your operating system post-infection – you can use automatic tools like Reimage Reimage Cleaner Intego for the purpose. Additionally, since Win64:malware-gen is a Trojan, it could have stolen your personal information, so we advise you to monitor your online banking and change passwords for all your accounts.
Prevent Trojan infections by following these tips
As mentioned above, Trojans are very flexible and can perform a variety of different actions, based on what the attackers program it to do. The ramifications of a malware infection can be significant, as personal information theft can destroy credit scores, result in monetary losses, and result in identity theft/fraud. Therefore, it is extremely important to protect your computer from such infections, and there are several methods that would help you with that.
Of course, no methods can provide 100% security, as any machine can be breached if enough effort is put into it. However, the more security measures are applied, the less likely it is to happen. Thus, follow these useful tips provided by security experts from dieviren.de:[3]
- Employ powerful security software that uses various analysis methods;
- Patch your computer with the latest security updates (as well as the installed software);
- Do not download software cracks or pirated applications;
- Never allow spam email attachments to run macro function;
- Upload unknown files to free sandbox analysis services like Virus Total;
- Enable Firewall and ad-block;
- Use strong passwords for all your accounts;
- Disable Remote Desktop connection as soon as you don’t need it and never use a default port for it.
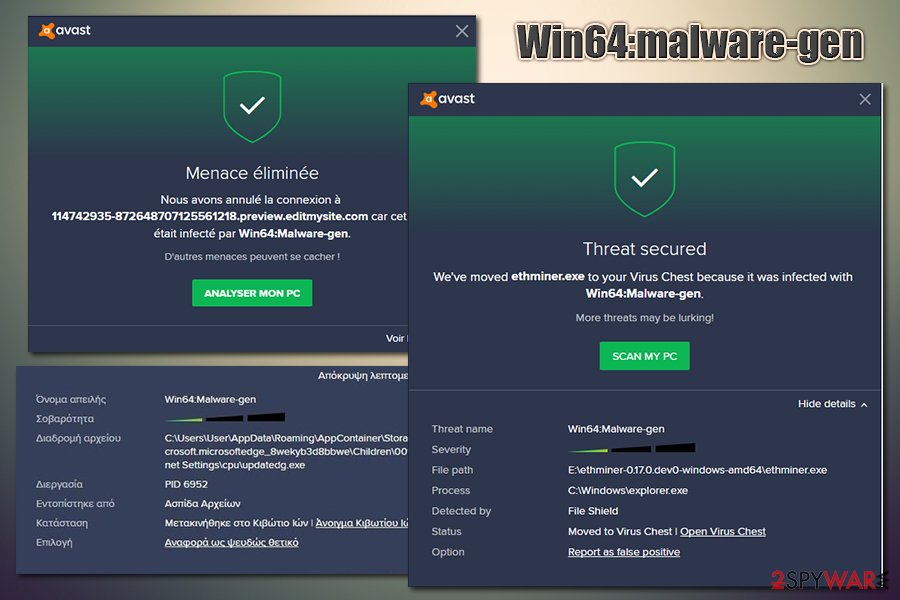
Win64:malware-gen detection can be seen as soon as suspicious file is opened

Win64:malware-gen detection can be seen as soon as suspicious file is opened
Remove Win64:malware-gen if it is not a false-positive
As previously mentioned, there are several scenarios where you can encounter the Win64:malware-gen virus alert. In most cases, you should not think about it is much, as your security software should get rid of it automatically. However, difficulties arise when a legitimate file is flagged as malicious, and you should investigate further. If you are not sure whether the file is connected to malware, you should first make sure that your anti-malware is up to date. If that does not help, you should scan the device, an alternative security tool, or upload it to virustotal.com. In case it is flagged by many other AVs, you should not hesitate to remove Win64:malware-gen as soon as possible.
If, for some reason, you are unable to perform Win64:malware-gen removal smoothly, you can access Safe Mode with Networking, as we explain below. If you are experiencing repeated detection constantly, we recommend you reset all the installed web browsers and reset Chrome’s Sync to ensure that malicious settings are eliminated from your Google account.
Online spying has got momentum in recent years and people are getting more and more interested in how to protect their privacy online. One of the basic means to add a layer of security – choose the most private and secure web browser. Although web browsers can’t grant a full privacy protection and security, some of them are much better at sandboxing, HTTPS upgrading, active content blocking, tracking blocking, phishing protection, and similar privacy-oriented features.
Nevertheless, there’s a way to add an extra layer of protection and create a completely anonymous web browsing practice with the help of Private Internet Access VPN. This software reroutes traffic through different servers, thus leaving your IP address and geolocation in disguise. Besides, it is based on a strict no-log policy, meaning that no data will be recorded, leaked, and available for both first and third parties. The combination of a secure web browser and Private Internet Access VPN will let you browse the Internet without a feeling of being spied or targeted by criminals.
While much of the data can be accidentally deleted due to various circumstances, malware is also one of the main culprits that can cause loss of pictures, documents, videos, and other important files. Potentially unwanted programs may clear files that keep the application from running smoothly.
More serious malware infections lead to significant data loss when your documents, system files, or images get locked. Ransomware is the one that is focused on such functions, so your device gets useless without access to needed data. Even though there is little to no possibility to recover after file-locking threats, some applications have features for such recovery in the system.
In some cases, Data Recovery Pro can also help to recover at least some portion of your data after data-locking virus infection or general cyber infection.
This entry was posted on 2020-06-26 at 03:20 and is filed under Malware, Viruses.

