Remk ransomware – dangerous malware that will lock up all your files and demand a ransom for their return
Remk ransomware is a file locking virus that demands a ransom of $490 in BTC for a decryption tool

Remk ransomware is a file locking virus that demands a ransom of $490 in BTC for a decryption tool
Remk ransomware is a malicious program that was designed by cybercriminals to lock up pictures, music, databases, documents, and other data on the host machine. For that, malware employs a sophisticated encryption algorithm RSA,[1] which also appends a .remk marker to each of the files. A unique key that is required to unlock data is stored on a remote C&C server that this only accessible to the Remk virus authors, and they offer it in exchange for $490 ransom, which should be paid in Bitcoin cryptocurrency.
Besides locking all files on the system, Remk ransomware also drops a _readme.txt file on the desktop and most of the folders on the computer. In the note, virus authors explain to users what happened to their files and what they need to do in order to recover the locked files. After the payment is made, crooks ask users to contact them via [email protected] or [email protected] email to recover Remk ransomware decryptor.
| Name | Remk ransomware |
| Type | File locking virus, cryptomalware |
| Malware family | Remk is a variant of Djvu/STOP |
| Related files | 1c20.tmp.exe |
| File extension | All non-system and most of non-executable files are appended with .remk marker after the encryption process is complete |
| Ransom note | The attackers want victims to know what happened, so _readme.txt file is added to almost each folder on the computer, as well as the desktop |
| Contact | Crooks ask users to email them at [email protected] or [email protected] for further communication |
| Ransom size | Initially, threat actors ask for $490 (to be paid in Bitcoin) for decryption software, although this sum doubles to $980 after 72 hours of the infection |
| File recovery | Emsisoft’s decryptor might be able to help victims if the virus used an offline ID to lock their data. In all other cases, the only secure method to recover files is by using backups. Dr.Web might also be helpful in some cases with certain file types. Finally, data recovery software might also be used – we explain how below |
| Malware removal | To get rid of the infection and all the other malicious modules/payloads on the system, perform a full system scan with the help of anti-malware software |
| System fix | In case you noticed that your machine is lagging, crashing or returning errors after you terminate the infection, fix virus damage with Reimage Reimage Cleaner Intego – you will not have to reinstall the OS |
Remk ransomware is almost exclusively distributed with the help of software cracks or pirated installers. These tools are employed to bypass the licensing of the application and use it for free. Previously, cracks used the popularity of tools like KMSPico or KMSAuto (used to avoid MS Office and Windows licensing process) to populate malware worldwide. Additionally, the virus was also spread with other malware, such as data-stealer AZORult. Without a doubt, this is just another reason to remove Remk ransomware from the system as soon as possible (but not before copying the compromised data).
Nevertheless, it does not mean that the malicious actors behind Remk ransomware can not employ other distribution methods common to malware, including:
- Spam email attachments and hyperlinks
- Malicious ads
- Software vulnerabilities and exploits[2]
- Unprotected Remote Desktop connections
- Fake updates, etc.
Remk ransomware belongs to the notorious malware family – Djvu/STOP. This virus has been around since at least December 2017, and over time more than 200 variants have been released. This massive project proves to be extremely successful, as the strain was deemed to be the most prominent one in the cybercriminal world, as daily infections reach hundreds. Remk virus is just another addition to the widespread family and marks the 214th release.
Throughout the time, security experts were ready to battle this malware, and released tools like STOPDecrypter – it could sometimes help users to retrieve data for free. However, the attackers were well aware of that, so they switched from AES to a more secure RSA method of file encryption, making the tool obsolete.
Luckily, Emsisoft security experts managed to create a decryptor that would work for at least 148 versions, and further releases, including Remk ransomware, may sometimes be unlocked with the help of Emsisoft Decryptor for STOP Djvu.
Remk ransomware is a data locker that belongs to STOP/Djvu virus family

Remk ransomware is a data locker that belongs to STOP/Djvu virus family
Remk ransomware modifies Windows files and settings in order to perform a successful data encryption
As soon as Remk ransomware gains access to the Windows system, it begins the modifications that are needed in order to perform data encryption without interruption. Most users will not notice and will not know what is happening in the background, as operations performed by the malware are extremely fast.
Thus, after the infiltration, Remk file virus will perform the following:
- Places an executable into %AppData% or %Temp% folder to begin an infection process
- Deletes Shadow Volume Copies by using the following command:
vssadmin.exe delete shadows /all /quiet
- Modifies certain system files or their attributes
- Inserts a module that is capable of recording information from Google Chrome or another web browser
- Creates new processes and amends services
- Modifies Windows “hosts” file located in C:\Windows\System32\drivers\etc\ to prevent victims from seeking help on security-focused websites
- Deletes some and creates new entries in Windows registry database, etc.
With the preparations complete, Remk ransomware will begin a scan that looks for files with predetermined file extensions, including .pdf, .html, .zip, .jpg, .mp4, .dat, and many others. Nevertheless, the virus will skip files that are related to the system, as well as executables – its goal is not to corrupt the infected machine but rather make file owners pay the ransom for encrypted data.
Suchlike modified files, appended with .remk extension, are not corrupted but simply locked with a key that only the attackers have access to. Each of the files will no longer have their original icon and will be impossible to open. In the meantime, victims will be presented with the following text message:
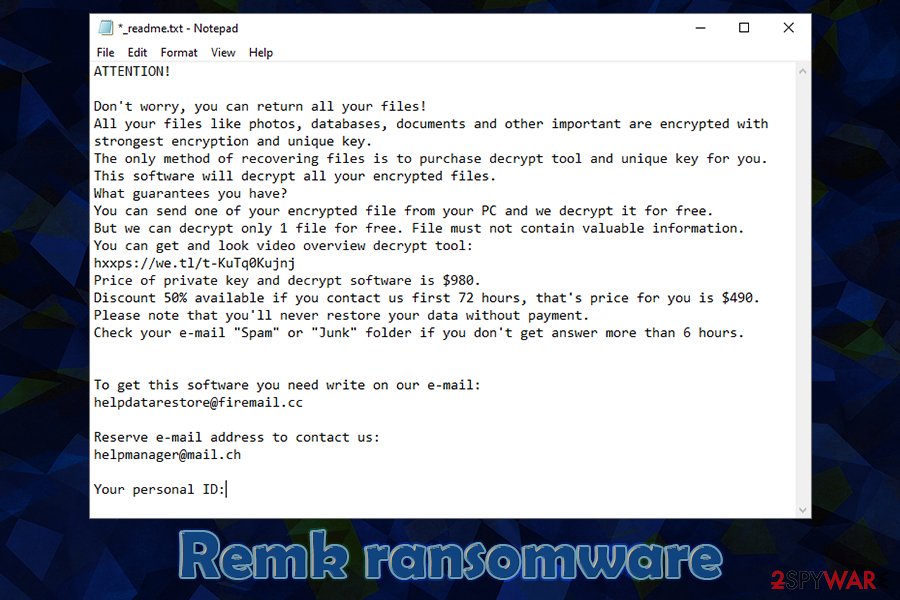
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-KuTq0Kujnj
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
[email protected]Reserve e-mail address to contact us:
[email protected]Your personal ID:
We highly advise you to contact cybercriminals, as they might never send you the required Remk ransomware decryption tool. As a result, you might lose access not only to your files but also your money. Besides, security experts are constantly working on new tools that could help users with recovering their data for free. Please do not forget to backup files before performing Remk ransomware removal, as they might permanently get corrupted.
After you delete malware from your system, you can then attempt to recover your files with Emsisoft’s decryptor or other methods listed below. If you continue having troubles with Windows after you get rid of malware, you could scan it with Reimage Reimage Cleaner Intego to fix virus damage.
In some cases, decryption tool from Emsisoft might be able to decode files for free

In some cases, decryption tool from Emsisoft might be able to decode files for free
Stay away from pirating – it might cost you more than you think
Software pirating is an issue that has been around since P2P networks, and similar websites were established. Initially not governed by copyright laws, users could share applications and multimedia for free. Nevertheless, that soon changed, and now downloading a cracked software installer is considered to be illegal.
Besides the legal side of this issue, websites that distribute software cracks, keygens, loaders, and similar tools are usually filled with malware.[3] And, while most of the infections occur when users open a malicious file downloaded to crack software, some malware might be inserted directly into ads that pop-up automatically as soon as users visit a site. If the circumstances are right, and software vulnerabilities are present on the system, malware intrusion can happen automatically.
Additionally, cracks cannot be checked by anti-malware tools properly, as, due to their functionality, almost all AV engines will flag it as malicious, despite if it actually is infected with malware or not. Thus, better stay away from such tools altogether.
Also, it is recommended to employ reputable anti-malware, backup files regularly, avoid spam email attachments, and paying close attention when installing new apps from third-parties. Being more attentive and aware could prevent you from suffering the devastating consequences of a ransomware infection.
Remk ransomware removal and file recovery
Please do not remove Remk ransomware immediately if you do no have backups ready. This is because if you delete malware without copying encrypted files, they might get corrupted permanently, and even a working decryptor will not help. Thus, make sure you copy over locked data to a remote server or an external drive, such as a DVD or a USB flash.
Nevertheless, it is also important to note that delaying Remk ransomware removal can be dangerous due to its ability to steal information that is typed in via the keyboard. Thus, as soon as you notice the infection, make sure you do not visit websites that ask you to enter your personal information, such as online banking.
To get rid of the Remk virus, you will have to use a powerful tool that can recognize the infection – we suggest employing SpyHunter 5Combo Cleaner or Malwarebytes, although please keep in mind that none of the security programs is capable of deleting all malware in existence. Once you terminate the malware, you can attempt to recover your data by using the methods listed below.
Remove Remk using Safe Mode with Networking
In case Remk file virus is tampering with your anti-malware software, delete the infection via the Safe Mode:
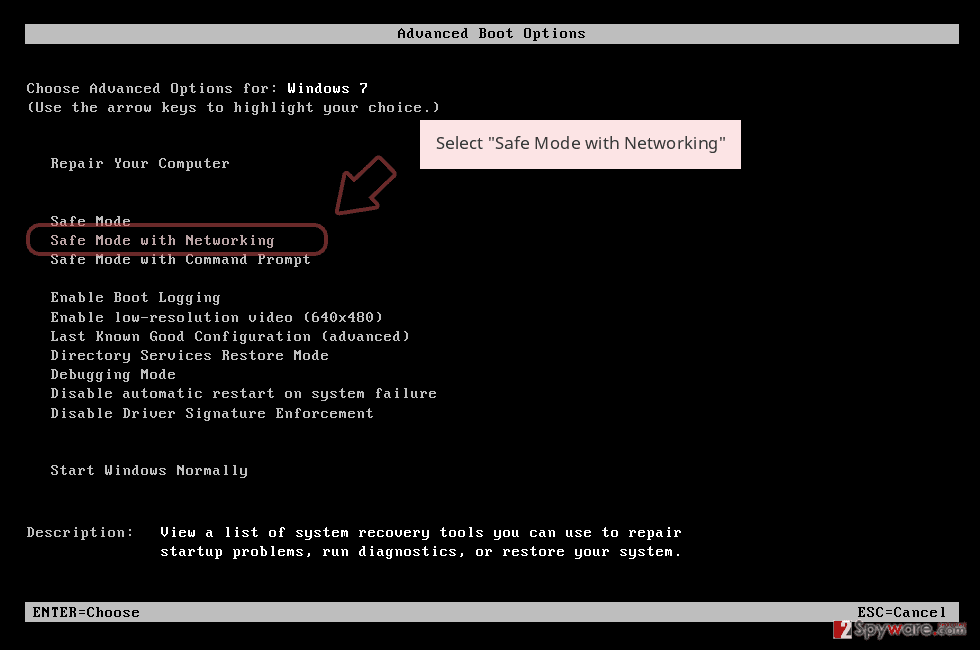
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
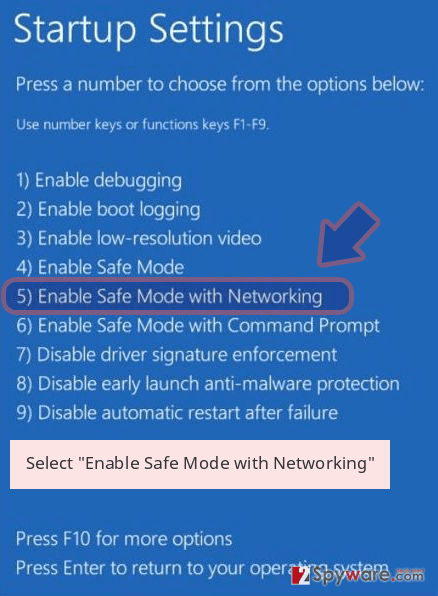
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner Intego or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete Remk removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove Remk using System Restore
System, Restore might be useful when trying to remove malware from the machine:
Bonus: Recover your data
Guide which is presented above is supposed to help you remove Remk from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If your files are encrypted by Remk, you can use several methods to restore them:
Data Recovery Pro method may work
Data Recovery Pro might be able to reach files from your hard drive memory that have not yet been permanently deleted. Thus, if you have not used your computer much after the infection, a portion of your data may be recovered.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by Remk ransomware;
- Restore them.
Make use of Windows Previous Versions feature
This method will only work if you had System Restore enabled before the infection occurred.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer might help you
If the virus failed to delete Shadow Volume Copies, ShadowExplorer should be able to help you.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Use Emsisoft’s decryption tool
If an offline ID was used to encrypt data on your machine, Emsisoft’s decryptor might be useful for you. Additionally, Dr.Web might be able to help you in some cases, although this service is not free.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from Remk and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner Intego, SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2020-03-17 at 09:10 and is filed under Ransomware, Viruses.

