Quasar – a Remote Access Tool that has its legitimate and malicious uses

Quasar virus is a Remote Access Tool/Trojan that can be used for legitimate and malicious purposes

Quasar virus is a Remote Access Tool/Trojan that can be used for legitimate and malicious purposes
Quasar virus is a Remote Access Trojan (RAT) that is often abused by cybercriminals to take remote control over users’ computers for malicious purposes. It is often used by various Advanced Persistent Threat (APT) groups for cyber espionage in international campaigns against governmental institutions and business networks, although it can also be employed to target regular consumers.
Quasar is not malicious by design, but rather by purpose itself – it happens with most Remote Access Tools. The application was first released in July 2014 by a user MaxXor for Windows operating system and was initially known as xRAT.[1] Its code was placed on the Github platform, allowing everybody to use it for free – such tools are called “open-source.” Quasar RAT has multiple legitimate purposes (such as assisting employees with tasks remotely), although malicious actors employ it as malware as well.
In most cases, the affected users have no idea that they are infected with the Quasar virus. In the meantime, malware can perform a variety of tasks, including information stealing, installing other malware, accessing personal files, elevating permission access, capturing screenshots and passwords, etc.
| Name | Quasar virus |
| Type | Remote Access Tool, Remote Access Trojan |
| Infiltration | RATs can be distributed in various methods, although this particular tool was spotted being delivered via malspam campaigns several times |
| Installation folder | Program Files, %AppData% and Windows\SysWOW64 (main executable is Client.exe, although can be named as anything else) |
| Programming language | C# (known as C Sharp) |
| Release date | July 2014 as xRAT, August 2015 as Quasar |
| Supported OS | Windows XP Service Pack 3, Windows Server 2003, Windows Vista, Windows Server 2008, Windows 7, Windows Server 2012, Windows 8/8.1, Windows 10 |
| Functionality |
|
| Removal | To eliminate malware, download and install powerful security software and perform a full system scan |
| System fix | Malware might seriously damage some Windows system files, rendering the whole operating system defective. To remediate the OS, scan the PC with Reimage Reimage Cleaner Intego or similar repair software |
Remote access tools can be either legitimate or malicious, depending on their usage. Quasar was licensed under the MIT License, which means that it can be used for personal and commercial use, as well as code modification. Employers can use the RAT for day-to-day administrative tasks in a workplace, and even help to spy on employees if so desired.
Unfortunately, malicious cybercriminal groups like Stone Panda, APT 33, APT 10, Dropping Elephant, Gorgon Group, and many other previously employed Quasar in their campaigns. Most recently, the malware was distributed in a phishing campaign, where scam emails backed with social engineering are delivered to an organization or business member. With special techniques like email spoofing, the email seems like it is coming from somebody within the company, so many open it without thinking twice.
If the payload is executed, the Quasar virus can infect not only Windows computer (several versions of the OS, as well as Servers, are supported) but an entire network in the organization. As a result, threat actors can spread the infection laterally and then steal highly sensitive information. This is why Quasar removal is crucial for privacy and sensitive information compromise.
To remove Quasar, a reputable anti-malware software should be employed. It is also important to disconnect the infected machine from the network and then perform a full system scan. Eliminating virus damage is also possible with repair software like Reimage Reimage Cleaner Intego.
Quasar is a type of malware that allows hackers to perform several actions on the infection users’ machines, including installing other malicious software and stealing sensitive information

Quasar is a type of malware that allows hackers to perform several actions on the infection users’ machines, including installing other malicious software and stealing sensitive information
Quasar functionality and malicious campaigns
Quasar RAT is possibly one of the most dangerous malware types to be affected by, as it allows the attackers to perform a variety of actions remotely. Technically, it simply grants hackers a takeover of the machine, all while being almost invisible to users or organizations.
Quasar malware can be used for a variety of purposes, including:
- Downloading and installing other malware, such as ransomware
- Logging everything what is typed on the keyboard (keylogging)
- Performing actions with built-in tools like Registry Editor
- Starting a new scheduled task
- Stealing account names and passwords from web browsers, online banking accounts, FTP clients, digital-wallets, etc.
- Restarting the system on the attacker’s command, etc.
While functions of Quasar are quite typical for a Remote Administration Tool, there is one trait that makes it a more attractive choice for cybercriminals rather than other RATs – it works on Windows 10. Many other tools of this kind do not support the latest version of Windows, limiting the number of machines that can be infected with malware.
Without a doubt, extensive functionality of the Quasar virus, its open-source availability, as well as its compatibility with Windows 10 attracted the attention of multiple cybercriminal groups over the years, and it was used in multiple campaigns.
In late 2016, the Gaza cybercriminal group used a modified version of Quasar RAT, which employed an obfuscator and packer in order to remain hidden on the infected users’ machines. While the attack vector(s) of the campaign remain unknown, security researchers from PaloAlto said[2] that Downeks downloader was used for the proliferation.
In the spring of 2017, malware made its appearance in the Chinese cybercriminal gang (ATP10) that used several Remote Access Trojans in its campaigns, Quasar malware, among them. The same group did not stop using the tool for a while, as new campaigns were spotted in late December of 2018, targeting healthcare, mining, aerospace, and other industries.[3]
Dropping Elephant, also known as Patchwork group, used spear-phishing emails, drive-by-download, website redirects, and other methods to infect businesses and governmental institutions with Quasar virus during 2017.
In August 2018, PaloAlto researchers wrote a publication about Gorgon Group and its usage of Quasar.[4] The cybercriminal gang is Pakistan-based and uses the tool for cyberespionage campaigns against governmental institutions in the United Kingdom, Spain, Russia, and the United States. The group employed other RATs in their campaigns, including well-known malware like NanoCore and njRat.
One of the latest appearances of Quasar was in August 2019, when a large-scale phishing campaign was delivering fake job applications to random users. Cofence security experts, who observed and analyzed the campaign, said that it used several obfuscation methods and social engineering techniques in order to proliferate victims’ computers.[5]
Without a doubt, Quasar will be used in future campaigns for monetary gains and the intelligence-gathering purposes around the world.
APT groups and random hackers can deliver malware in several different ways
Since Quasar RAT was used in several different campaigns over the years, there are many different ways of getting infected with it. While governmental agencies, industries, and businesses are typical targets of malware, regular consumers can be affected by the threat as well. Therefore, it is important to take adequate precautionary measures to avoid infiltration of a Remote Access Tool that can be installed without victims noticing the infiltration.
Since Quasar was spotted being delivered with the help of vulnerabilities such as CVE-2018-8373[6] in conjunction with browser redirects, it is vital to patch all the software located on the system. Additionally, content management applications like Drupal can also be extremely susceptible to bugs,[7] so their timely updates within organizations are mandatory to repel various malware.
Spear-phishing[8] is also common when trying to infect companies with malicious software. In most cases, the phishing email is sent to one of the employees and often looks like it has been sent from a colleague’s other trusted source’s address. Users often click on malicious attachments and let macros run for malware to be downloaded and installed in just a few minutes. This attack vector is extremely successful, is it usually bypasses traditional security implementations thanks to users’ inputs.
Remote Desktop connections should be adequately protected with a VPN and other security measures applied when it is used. Limit the usage to only those who actually need it, and protect it with a secure password.
Finally, all organizations, along with regular users, should employ next-gen security software in order to protect computers and company networks from unsolicited hacker intrusions.
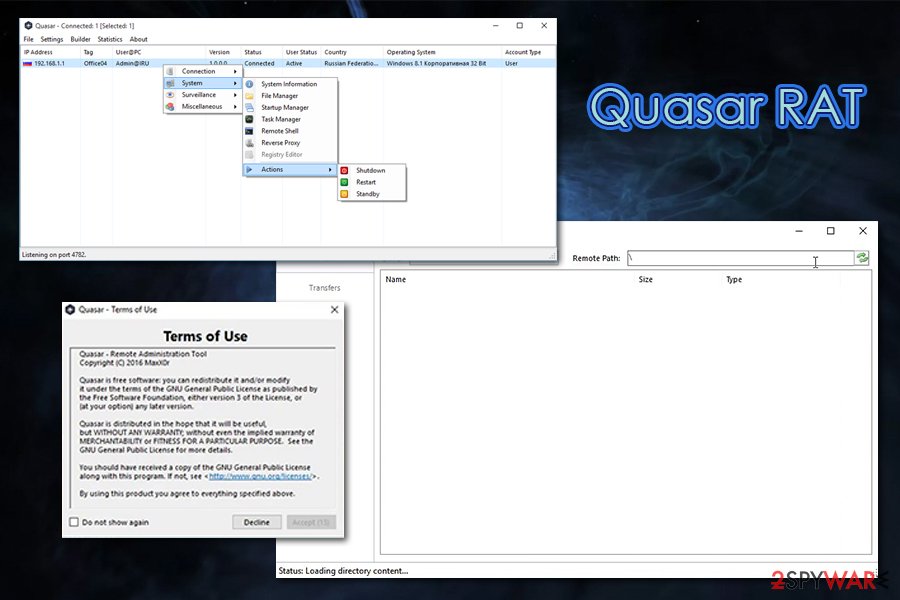
Quasar can also serve as a keylogger and capture information from browsers, FTP clients, management software, etc.

Quasar can also serve as a keylogger and capture information from browsers, FTP clients, management software, etc.
Terminate Quasar virus to protect your machine from unauthorized access
Multiple APT groups modify the source code of the Quasar RAT in order to remain undetected on the host machine, as well as the infected network. Therefore, users might not even know that the malware is operating in the background, stealing sensitive information, installing other malicious software, and performing other actions without permission. Due to this, users might not even be aware that they need to remove Quasar virus in the first place.
However, most advanced cybersecurity software can spot the intrusion in the first place, and also assist with Quasar removal. Since malware is used by sophisticated groups, they can employ various persistence techniques, which could complicate the Quasar virus’s termination.
Thus, if the infected machine is connected to a network, it should be segregated from other machines immediately, and Safe Mode used to eliminate the infection of the RAT. You will find the instructions on how to reach the mode below.
This entry was posted on 2020-05-08 at 04:06 and is filed under Trojans, Viruses.

