PwndLocker ransomware is the threat that targets networks and demands payments depending on the size of the company
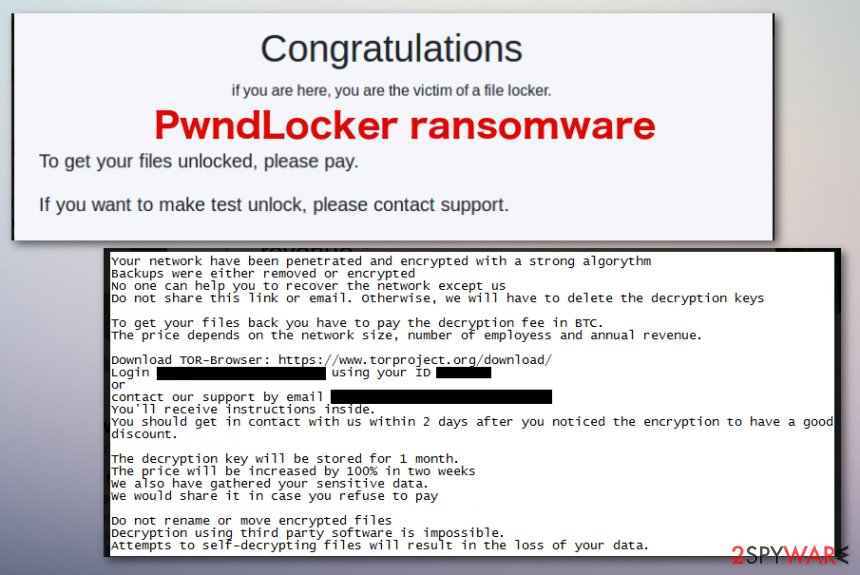

PwndLocker ransomware is the cryptovirus that uses the AES encryption algorithm to lock files for the purpose of maximizing ransom extraction. Developers of the virus keep the ransom amount as a variable and make the amount of Bitcoins bigger or smaller by analyzing a number of employees and machines, or the revenue. This is the threat that was spotted at the end of 2019, but more recently, in 2020 it was deeply analyzed, and the research revealed particular details, coding specifications.
PwndLocker ransomware virus starts with the encryption process as any other file locker virus, so data gets encoded and marked with a specific file appendix. Two particular ones that are already known .key or .pwnd, hence the name of this threat. The marker comes after the original name of the file and after the file type-indicating extension. After this procedure, the ransom note file gets placed on the desktop and in other folders containing the affected data. H0w_T0_Rec0very_Files.txt contains brief information about the encryption procedure and possible steps that you as a victim can take. Unfortunately, those mainly include contacting developers and paying for the alleged decryption. Researchers haven’t released a proper decryption tool for users, so other options are removing the threat and recovering from data backups.
| Name | PwndLocker ransomware |
|---|---|
| Type | Cryptovirus |
| File marker | .pwnd and .key are known extensions that this threat uses for marking affected files on the infected systems |
| Ransom amount | The amount of cryptocurrency that gets demanded from the particular victim depends on the size of the enterprise because criminals figure out how much the company can pay by analyzing the size of the network, amount of people working and revenue |
| Ransom note | H0w_T0_Rec0very_Files.txt is the file that appears after encryption to inform victims about the attack. Also, an additional message from virus developers appears on the desktop and as a program window that politely offers to pay and unlock files this way |
| Encryption method | AES[1] army grade algorithm gets used for the encryption during attacks of this particular threat |
| Distribution | The threat gets distributed around the world, and virus developers can use various methods for such procedures, including spam email attachments that get injected with malicious scripts or hyperlinks redirecting straight to malicious sites. These threats can also be included in pirated software packages from torrent sites and other p2p sharing services |
| Elimination | PwndLocker ransomware removal requires more attention and professional tools or even security experts when the large network gets affected. The best way to clean the system from cush cryptovirus is anti-malware tools based on malware detection[2] |
| Repair | You need to consider the ransomware as one of the more dangerous threats, so PC repair tools like Reimage Reimage Cleaner are needed to fix virus damage that can affect your machine even when the virus itself is terminated |
PwndLocker ransomware was reported by researchers[3] as the threat that targets high-value companies and enterprises that can pay larger amounts in Bitcoin, so criminals make more money from one or two victims. When such cryptocurrency extortionists affect everyday users’ devices ransom demands are as little as hundreds or thousands. However, when companies suffer from crypto virus attacks, payments start at the range of thousand dollars worth of Bitcoin.
Bitcoin is the preferred cryptocurrency that PwndLocker ransomware developers would like to get from their victims, so in the ransom note file H0w_T0_Rec0very_Files.txt criminals listed places where you can create the wallet and exchange dollar or another currency in the most popular crypto.
According to the ransom message, when you access the particular account that criminals provide you, you can contact them and receive further payment instructions. You need to follow the steps in PwndLocker ransom note in two days or less, as the following note states:
Your network have been penetrated and encrypted with a strong algorythm
Backups were either removed or encrypted
No one can help you to recover the network except us
Do not share this link or email, otherwise, we will have to delete the decryption keys
To get your files back you have to pay the decryption fee in BTC.
The price depends on the network size, number of employess and annual revenue.
Download TOR-Browser: https://www.torproject.org/download/
Login ***** using your ID ***
or
contact our support by email ***
You’ll receive instructions inside.
You should get in contact with us within 2 days after you noticed the encryption to have a good discount.
The decryption key will be stored for 1 month.
The price will be increased by 100% in two weeks
We also have gathered your sensitive data.
We would share it in case you refuse to pay
Do not rename or move encrypted files
Decryption using third party software is impossible.
Attempts to self-decrypting files will result in the loss of your data.
You shouldn’t consider paying criminals and remove PwndLocker ransomware from the system instead. Criminals say that the key for decryption of your data gets stored for a month, but you need to get rid of the virus as soon as possible because the ransom amount can get increased, and your machine affected even more in the meantime. 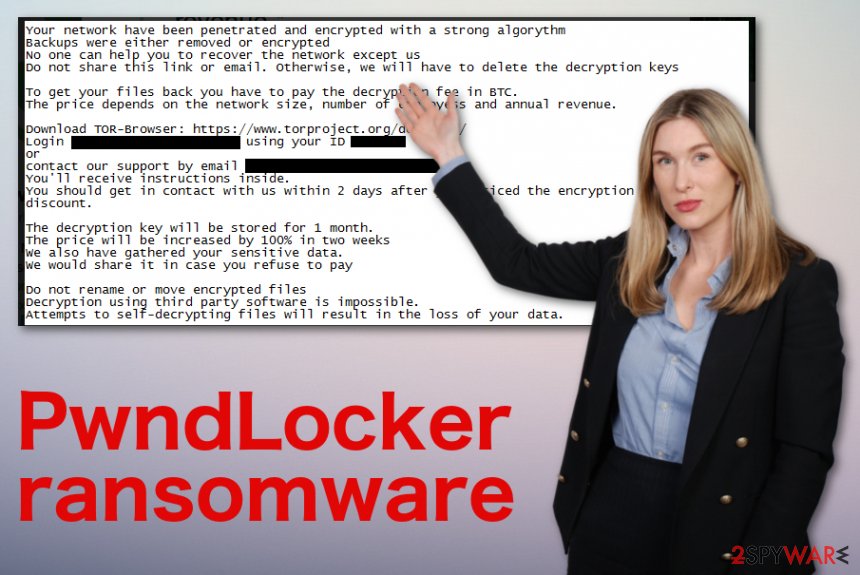
PwndLocker ransomware is the virus that creates a ransom-demanding message which gets delivered to people immediately after encryption procedures.

PwndLocker ransomware is the virus that creates a ransom-demanding message which gets delivered to people immediately after encryption procedures.
PwndLocker ransomware can delete Shadow Volume Copies to interfere with data recovery procedures, disable security tools, programs, and other system features that can help victims to restore their encrypted data or remove the malware itself. Due to these changes, the virus termination process becomes barely possible. We have a few methods below to go around these changes.
Since PwndLocker ransomware removal can get difficult in time, you need to react as soon as possible and run the anti-malware program on your affected machine, so all the parts of this threat get eliminated during one system cleaning process. Anti-malware tools that run on your device already may get blocked or disabled, so reboot the machine in a Safe Mode before launching the AV tool.
PwndLocker ransomware is not the threat that only focuses on locking images, documents, video, audio files, or databases. It deletes various files and adds programs or damages existing data to make the machine more affected and malware persistent. Unfortunately, when malware hits enterprises, anti-malware tools may not be enough for the whole network, so you should rely on IT specialists who can manage the security and cleaning fo you.
However, as for everyday computer users that have encountered PwndLocker ransomware on their machines, you should get a program like Reimage Reimage Cleaner that could at least search for affected data in the system folders and other parts of crucial functions and files on the machine. This program can repair damaged registry entries or affected OS files for you.
As for files encrypted by PwndLocker ransomware, there are not many options. Official decryption tools get rarely developed for such powerful versions of ransomware because these threats are technically secure and methodically crafted. Your other options revolve around data backups. The best way to tackle encrypted files is to replace an encoded file with a safe copy from the external device. When you don’t have such an option, you can go through bonus solutions below the article. 
PwndLocker virus is the ransomware-type threat that spreads around the world and encrypts files, so it can successfully demand money from victims.

PwndLocker virus is the ransomware-type threat that spreads around the world and encrypts files, so it can successfully demand money from victims.
Ransomware targets the ones who can pay quickly
Malware in this cryptovirus category can spread using various methods. In most cases, stealthy techniques get employed for such distribution campaigns, especially when a virus targets large businesses and companies. Various organizations receive emails on a daily basis, and when the network connects many employees and users it becomes extremely dangerous to open the questionable file or an email itself.
Malicious macros, in most cases, get injected on Microsoft files like Word, Excel documents, PDF files. Once you receive the email with the attached file, you should consider the legitimacy of the sender and the notification itself before you go for the attachment.
Opening such a document leads to the form of enabling additional content – macros or direct payload drop. This is the way that malware gets on the machine or the whole system of machines. Trojans, malware, worms, and other viruses can get on the device this way and spread ransomware as a secondary payload.
Also, file with direct cryptovirus can get installed after you click the Enable or Allow button. Avoid any emails from shipping companies, shopping sites, and similar services, when you are not expecting to get any information from them.
Terminate all parts of the PwndLocker ransomware virus by scanning the system fully
Before you for the PwndLocker ransomware removal, you need to consider all the options. It is possible that researchers could develop the decryption tool after a while or when the vulnerability of encryption gets exposed. Base on such things, you can try to keep some virus-related files and encrypted data on external devices for later use.
However, you still need to remove PwndLocker ransomware from the system if you want to use the machine ever again. Any traces of the encryption-based threat can trigger secondary file locking and other malicious activities on the device, so it is not advised to use a computer that still has some sort of malware on it.
PwndLocker ransomware virus can get detected by many anti-malware tools, so choose SpyHunter 5Combo Cleaner or Malwarebytes and run it on the machine. Once the scan is done, you should receive the list of malicious files, indicated files, and similar issues. Then, then the best step is to follow suggestions and delete all possible intruders and malware. To clean the machine ven further, rely on Reimage Reimage Cleaner and fix virus damage.
This entry was posted on 2020-02-28 at 06:39 and is filed under Ransomware, Viruses.

