Paymen45 ransomware – dangerous malware that asks for Bitcoin in exchange for file decryption software
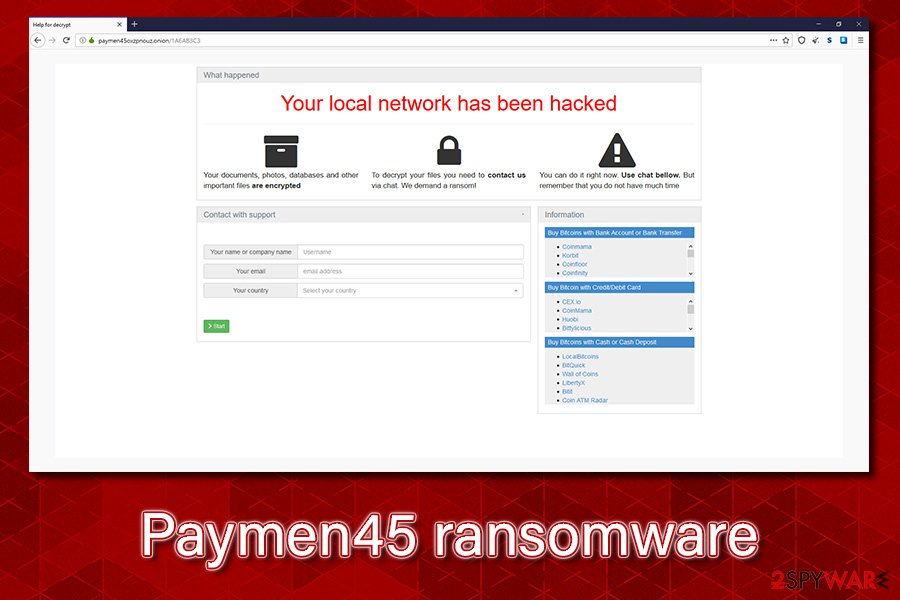
Paymen45 ransomware is a data locker that also threatens to expose your files if ransom is not paid

Paymen45 ransomware is a data locker that also threatens to expose your files if ransom is not paid
Paymen45 ransomware is a data locking virus that stems from Oled/Makop malware strains. It was first identified in late April 2020, when multiple users started to complain about the infection, which prevents them from opening pictures, music, documents, databases, and other files located on local or networked/NAS devices. Soon after the infiltration, the Paymen45 virus uses a combination of AES and RSA encryption algorithms to lock files and appends a randomized extension to each. Currently, there are two different versions identified by the researchers: g8R4rqWIp9 and KJHslgjkjdfg.
After encrypting data, Paymen45 ransomware also drops a ransom note readme.txt or readme-warning.txt (depending on the version), which explains what happened to users’ files and asks them to download a Tor web browser in order to be able to visit a dark web onion webpage. Users are asked to provide the personal ID, and then they are provided with a personal ransom size, which can be as low as $10 in some cases. Threat actors behind Paymen45 ransomware also threaten to publicly disclose the stolen files if the ransom is not paid.
| Name | Paymen45 ransomware |
| Type | File locking malware, cryptovirus |
| Origination | The malware is a new variant of Oled and Makop ransomware |
| Distribution | Malicious actors can use a variety of methods to deliver the threat to users, e.g., spam email attachments/hyperlinks, fake updates, exploits, software vulnerabilities, weakly protected RDP connections, brute-force attacks, software cracks, and other attack vectors |
| Related | lok.exe, paymen45oxzpnouz.onion |
| Encryption algorithm | The attacks use AES + RSA to encrypt all non-system and non-executable files on the local and networked drives |
| Ransom note | readme.txt or readme-warning.txt is dropped on the desktop, as well as other places on the machine |
| File extensions | Paymen45 uses a randomized 10 character file extension which is appended at the back of the file name: .g8R4rqWIp9 or KJHslgjkjdfg. Examples of encrypted files: picture.jpg.g8R4rqWIp9, document.doc.KJHslgjkjdfg |
| Data recovery | Since the cryptovirus uses sophisticated encryption algorithms, recovering data without paying criminals or restoring it from backups is almost impossible. However, in some cases, users might be able to restore at least some data with the help of third-party tools – we provide the instructions below |
| Removal | Before removing Paymen45 ransomware from the computer, users who do not have backups should make a copy of all encrypted files and only then use anti-malware software to eliminate the infection safely (note: it will NOT recover your files) |
| System fix | Make use of PC repair software such as Reimage Reimage Cleaner Intego if you want to avoid reinstallation of the entire Windows system |
Since Paymen45 ransomware belongs to a relatively new malware strain, there are no clear indications of what methods the attackers sue for its propagation. While some ransomware families, such as the notorious Djvu, use a single attack vector, most cybercriminals resort to multiple techniques when it comes to malicious payload delivery. Thus, Paymen45 ransomware might be delivered in one (or multiple) of the following ways:
- Spam email attachments or embedded hyperlinks;
- Fake updates or scam websites;
- Drive-by downloads and software vulnerabilities;[1]
- Brute-forcing combined with weakly protected RDP (Remote Desktop) attacks;
- Illegal program installers and software cracks;
- Etc.
Most of these techniques can usually be prevented by using security software and other precautionary measures – you can find more tips in our article below. As for now, you should focus on Paymen45 ransomware removal and data recovery.
Before performing data encryption, Paymen45 ransomware firs needs to prepare the system for the process. Thus, the malware modifies the Windows registry database by setting new keys for persistence, creates new processes that help malware function during the infection, starts a new service, deletes Shadow Volume Copies to prevent easy data recover, etc.
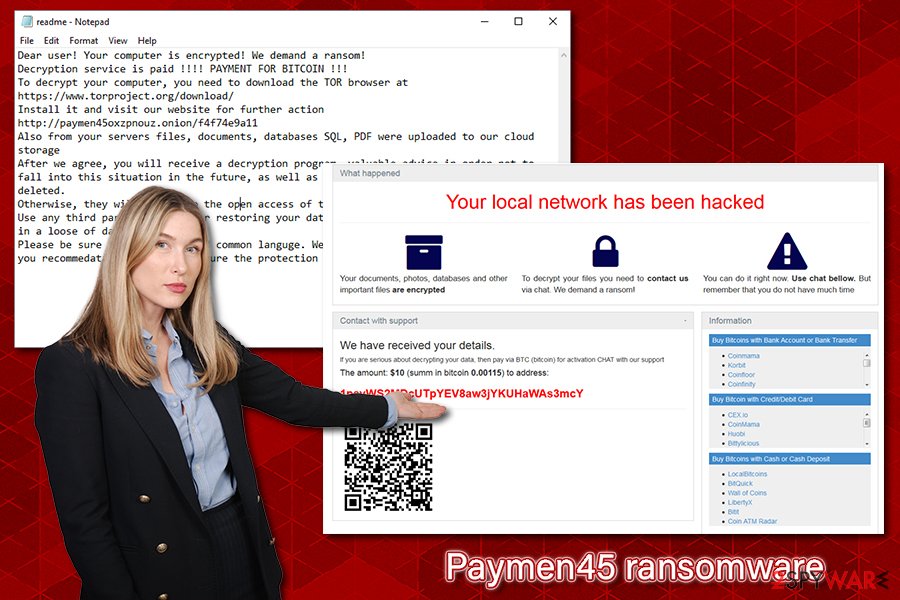
Paymen45 ransomware is crypto-malware that encrypts all personal files on local drive and networks with AES + RSA encryption algorithms

Paymen45 ransomware is crypto-malware that encrypts all personal files on local drive and networks with AES + RSA encryption algorithms
Once the preparations are complete, Paymen45 ransomware begins the data encryption task. In most cases, users do not notice how the process is performed, and only realize that something odd happened after they try to open a personal file or see a ransom note. Malware targets most common file types, such as .pdf, .sql, .doc, .rar, .jpg, and many others. After the process, each of the files receives one of the following extensions: g8R4rqWIp9, KJHslgjkjdfg, or another randomized string.
After data is locked, users can see a ransom message from the attackers, which states:
Dear user! Your computer is encrypted! We demand a ransom!
Decryption service is paid !!!! PAYMENT FOR BITCOIN !!!
To decrypt your computer, you need to download the TOR browser at https://www.torproject.org/download/
Install it and visit our website for further action http://paymen45oxzpnouz.onion/f4f74e9a11
Also from your servers files, documents, databases SQL, PDF were uploaded to our cloud storage
After we agree, you will receive a decryption program, valuable advice in order not to fall into this situation in the future, as well as all your files on our server will be deleted.
Otherwise, they will fall into the open access of the Internet!
Use any third party software for restoring your data or antivirus solutions will result in a loose of data.
Please be sure that we will find common languge. We will restore all the data and give you recommedations how to configure the protection of your server.
Paying cybercriminals is not recommended, as they might not contact you after the payment. We suggest not paying the attackers unless it is an absolute last choice and none of the alternative methods we provide below work for you. Note that you should make a copy of your hard drive, including the registry database and the encrypted files (unless you have backups – then you can remove Paymen45 ransomware as soon as possible).
To eliminate the malware, use powerful security tools, such as SpyHunter 5Combo Cleaner or Malwarebytes. Nevertheless, some file locking viruses eliminate themselves after encrypting files, so your anti-malware may not find anything if that is the case. However, keep in mind that other malicious software might have been installed along with Paymen45 ransomware, so a scan is a mandatory process. After you are sure that the infection is gone, you can also use Reimage Reimage Cleaner Intego to remediate Windows computer and fix virus damage.
Paymen45 ransomware versions
While first sightings of Paymen45 virus were spotted on April 30, two different versions have been released within the first two weeks of its operation – g8R4rqWIp9, and KJHslgjkjdfg. The naming is based on the file extension that is generated to encrypt data, although researchers believe that the string is random and can consist of 10 randomly-generated alphanumeric characters.
g8R4rqWIp9 ransomware
Once inside the system, g8R4rqWIp9 ransomware performs several changes to the Windows system and encrypts all data on local and networked drives. This way, PDF files, MS Office documents, databases, and other files are appended with .g8R4rqWIp9 extension, and can no longer be accessed. Once that is complete, users are asked in readme.txt file to download the Tor browser and visit the http://paymen45oxzpnouz.onion/ address for further communication. In some cases, users were also provided a contact address – [email protected] email.
We do not recommend contacting or paying g8R4rqWIp9 ransomware authors, and instead of performing g8R4rqWIp9 virus removal with anti-malware, and then using alternative methods for data recovery.
KJHslgjkjdfg ransomware
KJHslgjkjdfg ransomware showed up just a week later after the initial Paymen45 release. Users reported that all their personal files were appended with .KJHslgjkjdfg file extension and even NAS backups were encrypted as well. In other words, if malware manages to penetrate a company, it will most likely to encrypt all servers and machines connected to the same network. If that is the case, each of the infected computers and other devices should be immediately isolated from the network.
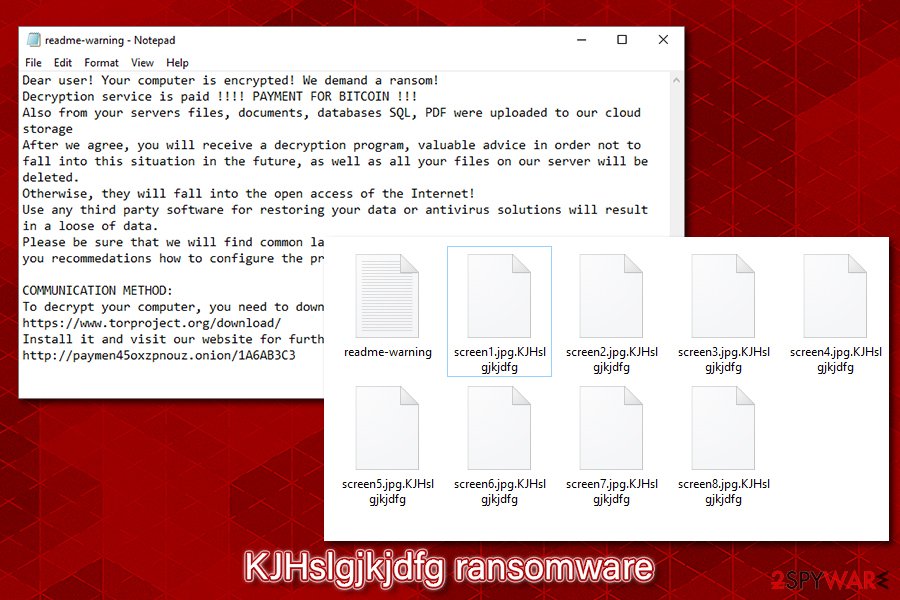
KJHslgjkjdfg ransomware drops a differently-named ransom note (readme-warning.txt) which consists of a slightly different text than its previous version g8R4rqWIp9

KJHslgjkjdfg ransomware drops a differently-named ransom note (readme-warning.txt) which consists of a slightly different text than its previous version g8R4rqWIp9
One of the malware samples analyzed by researchers was an output.159342821.txt file, which is highly likely to trigger the infection. It is detected by various security solutions under the following names:[2]
- Gen:NN.ZexaF.34108.kq0@aOdJGsfG
- Trojan.Encoder.31793
- Win32.Packed.Kryptik.5Y4AR0
- VirTool:Win32/Obfuscator.KK!MTB
- Packed-GBC!7668CABB5A3F
- Trojan.MalPack.GS, etc.
Also, KJHslgjkjdfg ransomware is using a different ransom note – readme-warning.txt, contents of which slightly vary from the initial version:
Dear user! Your computer is encrypted! We demand a ransom!
Decryption service is paid !!!! PAYMENT FOR BITCOIN !!!
Also from your servers files, documents, databases SQL, PDF were uploaded to our cloud storage
After we agree, you will receive a decryption program, valuable advice in order not to fall into this situation in the future, as well as all your files on our server will be deleted.
Otherwise, they will fall into the open access of the Internet!
Use any third party software for restoring your data or antivirus solutions will result in a loose of data.
Please be sure that we will find common languge. We will restore all the data and give you recommedations how to configure the protection of your server.COMMUNICATION METHOD:
To decrypt your computer, you need to download the TOR browser at https://www.torproject.org/download/
Install it and visit our website for further action http://paymen45oxzpnouz.onion/1A6AB3C3
Malware prevention measures and security tips
File locking viruses are possible one of the most devastating types of malware due to their functionality. Once files are encrypted, only a unique key, which is generated during the infection process, can decipher them and allow users to reaccess them. Unfortunately, this key is sent off to a Command & Control server that is controlled by the attackers, and they are not willing to giveaway it for free. While sums can vary, regular consumers are typically asked for lesser sums than corporations, where ransoms can reach hundreds of thousands of dollars.
Ransomware authors also came up with another devastating tactic (started by Maze ransomware gang) to make users and companies to pay ransoms. Before encrypting data, they copy everything located on the network/server/computer and place copies to their own server.[3] This allows the attackers to threaten victims by claiming that the data will be publicly exposed if the demands will not be met on time.
Thus, getting infected with this type of infection can cause various negative consequences, such as permanent data loss on private information exposure to malicious parties. To avoid such outcomes, it is crucial to take care of cybersecurity and not ignore industry experts’ advice.[4]
First of all, the computer should be equipped with comprehensive security software that has real-time protection feature and can protect the whole network from the intrusion. However, careful online behavior is just as important as security tools, so users should also:
- backup data on a regular basis;
- apply Windows and application updates as soon as new patches are released;
- never download software crackers or pirated program installers;
- employ VPN for RDP connections and limit the access to individuals who actually need it;
- use secure passwords for Remote Desktop connections;
- never reuse passwords for different accounts;
- do not click on random links on social media or other platforms;
- never allow spam email attachment to run macro function;
- scan unknown files with anti-malware software or online scanning services like Virus Total.
Terminate Paymen45 ransomware correctly
As previously mentioned, some crypto-malware might erase themselves after the file encryption process, so Paymen45 ransomware removal might not be necessary. However, since there might be other payloads installed on your system (ransomware is sometimes distributed with info-stealers like AZORult), you should still perform a full system scan with a powerful anti-malware program. While we recommend using SpyHunter 5Combo Cleaner or Malwarebytes, there are several other security tools that could also help you with the process.
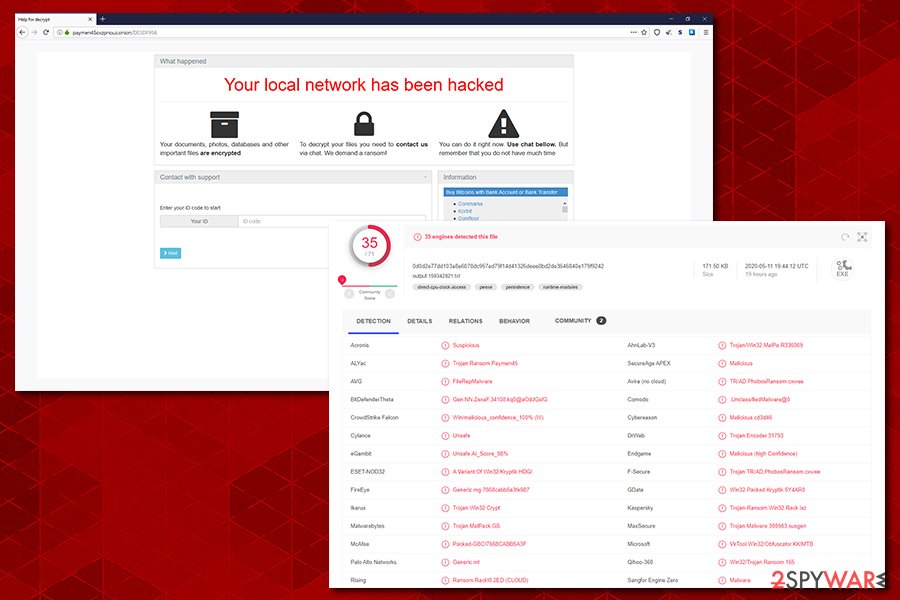
A powerful anti-malware software can detect and prevent Paymen45 ransomware infection

A powerful anti-malware software can detect and prevent Paymen45 ransomware infection
However, you should not remove Paymen45 ransomware before you backup all the files that were encrypted, along with the Windows registry database. If you do not perform these backups, malware might reinstall itself even after its termination in some cases.
In case the Paymen45 virus is tampering with your security software, you can access Safe Mode with Networking, and perform the scan from there. After that, you can proceed with data recovery methods we provide below (note that there is no guarantee that any of them will work, but you should try them out regardless).
This entry was posted on 2020-05-12 at 11:05 and is filed under Ransomware, Viruses.

