Ouroboros is yet another major player in the ransomware business circulating on the Internet for more than a year

Ouroboros ransomware is a malicious cryptovirus[1], which is actively circulating on the Internet for about a year. Experts claim that it has already infected thousands of PCs and earned its developers millions of dollars. Ouroboros ransomware is not a stand-alone cyber infection, but rather the family of file-encrypting virus. Odveta, King, Zeropadypt NextGen, RX99, are the most prominent Ouroboros variants, while Boruta Virus File is the freshly detected versions. While Zeropadypt, .Lazarus, and .Lazarus+ viruses have already been cracked down[2]; the other versions are regularly evolving, leaving thousands of PC users on a crossroad paying the ransom or not.
The Ouroboros ransomware virus has been distributed by various means, including but not limited to exploits, spam emails, fake software updates, illegal third-party software, web injects on malicious websites, cracks, and similar. As soon as the executable file Runtime Broker.exe hosting the Ouroboros virus is launched, the attack is being initiated by multiple changes in the core system’s files and enabling the AES 256 CSB algorithm to encrypt files. As a consequence, personal files on the affected computer become completely locked. Encrypted files get one of the following fixe extensions depending on the ransomware variant: .teslarvng, .rails, .encrypt, .encrypted, .kraken, .vash .bitdefender, .harma, .rx99, .Lazarus, .Lazarus+, .lol, .hiddenhelp, .angus, .limbo, or .KRONOS, and others.
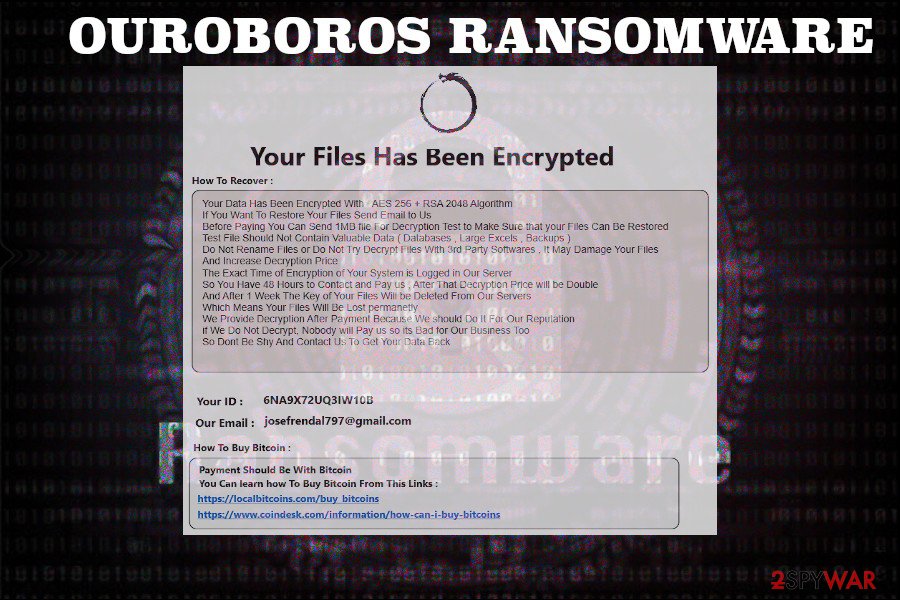
In addition to file encryption, the Ouroboros crypto-malware creates several ransom notes on the desktop. Typically, these files are named as Read-Me-Now.txt and contain the following information:
Your All Files Encrypted with High-level Cryptography Algorithm
If you need your files, you should pay for decryption
You can send 1MB file for decryption test to make sure your files can be decrypted
After 48 hours if you don’t contact us or use 3rd party applications or recovery tools decryption fee will be doubled
After test you will get decryption tool
Your ID for decryption: xxxxxxxxxx
Contact us: xxxxxx
Just like any other ransomware virus, Ouroboros virus developers seek financial profit. They demand victims to pay a ransom in BTC in exchange for a unique decryption key. To raise people’s “trust,” cybercriminals allow victims to send a 1MB file to ensure the Ouroboros decryptor is working. Typically, crooks provide the following contact email addresses: [email protected], [email protected], [email protected], [email protected], and other @protonmail.com, etc.
According to security experts, people who use older PCs (launched earlier than 2010) that feature older CPU models can take a breath since the Ouroboros ransomware cannot be launched due to the lack of instructions to run encryption algorithm. Unfortunately, that’s just a small relief.
| Name | Ouroboros |
| Family members | Odveta, King, Zeropadypt, Zeropadypt NextGen, RX99, Boruta Virus File |
| Possible file extensions | .eslarvng, .rails, .encrypt, .encrypted, .kraken, .vash .bitdefender, .harma, .rx99, .Lazarus, .Lazarus+, .lol, .hiddenhelp, .angus, .limbo, .KRONOS, .boruta, .odveta |
| Contact emails | [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], [email protected], and others |
| Main symptoms |
The virus installs multiple malicious files and roots deep into the operating system. Then it runs the command to enable file encryptor and locks all available files. Consequently, victim’s personal documents get an unusual file extension and become inaccessible. Finally, the virus generates a ransom note on a desktop that provides basic information on what has happened and what steps have to be taken. |
| Ransom note file | Read-Me-Now.txt, INFO.exe or ReadMe.txt |
| Distribution | Pirated third-party software, unprotected Remote Desktop, phishing websites, spam email attachments, and similar |
| Removal | The only way to get rid of Ouroborus and other ransomware viruses is to run a system scan with a professional antivirus program. For this purpose, try using SpyHunter 5Combo Cleaner or Malwarebytes. |
| Fix virus damage | It may not be enough to remove the ransomware. It is very likely that you will notice additional side effects, such as serious system’s slowdowns, damaged or missing system files and similar. Reimage Reimage Cleaner Intego is a tool that can help to fix such and similar problems. |
Even though Ouroboros removal may be a tough nut to crack, most of the reputable antivirus programs can do that. As outlined by VirusTotal, the ransomware detection rate is 51 out of 70[3]. Therefore, those who have been attacked by this virus and have copies of files on a cloud or elsewhere should install SpyHunter 5Combo Cleaner, Malwarebytes, or another antivirus tool and run a full system scan.
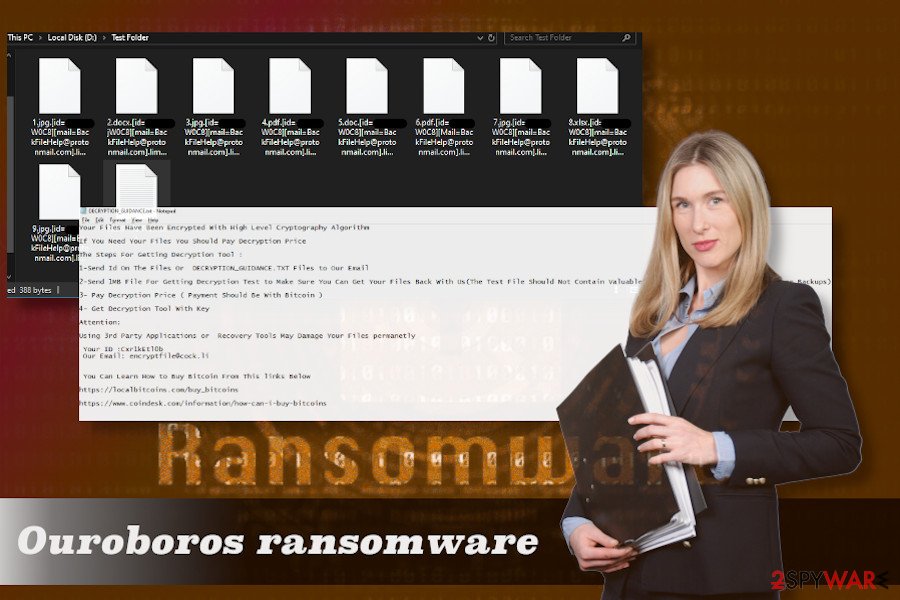
Ouroboros crypto malware encrypts files and demands to pay the ransom.

Ouroboros crypto malware encrypts files and demands to pay the ransom.
In any way, it is not recommended to pay the ransom for cybercriminals for a decryption tool. You will have to pay a considerable amount of money. Besides, even if crooks will provide you with a key, it will not remove Ouroboros ransomware. Therefore, there’s no guarantee that your PC will not be re-attacked soon.
Take all security measures online to prevent ransomware attacks
Ouroboros ransomware family can be distributed in many ways. While Odveta virus is known for taking advantage of weakly protected Remote Desktop connections, Zeropadypt NextGen ransomware usually infiltrates PCs via insecure port 3389. In other words, crooks look for various security breaches that allow them to use brute force attacks and run malicious files on a host PC.
Nevertheless, the Ouroboros virus can be disseminated via illegal software installers. Using torrent file-sharing offers people take the risk of downloading software bundles, which may not only contain PUPs but also run malicious executables that can download ransomware in the background.
Malicious emails or spam is by far the most popular way to spread viruses. Crooks develop trustworthy looking email messages and attach .zip, .exe, .pdf, and similar files. To trick less experienced PC users, criminals name the records in relation to taxes, payments, shipment information, and similar. Therefore, it’s essential to sort the emails on the inbox carefully and delete questionable content right away.
It’s vital to install a reliable security tool with a real-time protection and update it regularly to keep the system and files safe from sever viruses. Besides, no matter how attractive the content online may seem, think twice before clicking on it.
Ouroboros ransomware developers are actively working on updating the virus and presenting it as new variants
King ransomware
Going back to the very beginning of Ouroboros ransomware outbreak, the King Ouroboros virus is the first version that comes to the surface. It emerged in 2018 and hasn’t been cracked down up until now. Nevertheless, it seems that it’s spread is no wider. KingOuroboros ransomware can be distinguished from the others from the suffix that it uses to corrupt files, i.e. it adds .king_ouroboros string and and renders files useless by locking them with EAS cipher. The initial price that hackers ask for the decryption key starts from $30, $50 or $80 by Bitcoin and increases after 72 hours. The virus has echoed due to its developers attempt to get rid of substantial allegations by saying that they ‘helped loads of people solving any of their issues regarding the decryption of their files, as well as spending time to code a stand-alone decryption tool.”
Odveta ransomware
Odveta is the second infamous version of the Ouroboros ransomware. It encrypts files with RSA+AES-256 encryption algorithms and appends .odveta suffix to the corrupted files. The virus creates a ransom note called HowToDecrypt.txt or Unlock-Files.txt. On the desktop, which contains information on how people have to make the payment to get a decryption key. People are asked to set the contact with [email protected] or [email protected] email owners to get further instructions.
Zeropadypt NextGen
Zeropadypt NextGen is the new version of Zeropadypt ransomware, which has been updated right after a caber security researcher BloodDolly revealed a decryption key for it. The improved version showed up in August 2019 and had been actively spreading via RDP connections using a default port (3389). It exploits RSA encryption, which turns the data of all affected files to zeros. Zeropadypt NextGen encrypted files end up with a .lazurus or .limbo file extension, and the Read-Me-Now.txt ransom note appears on a prominent PCs place. Not surprisingly, criminals ask to pay the ransom in Bitcoin cryptocurrency.
Harma file virus
Previously known as a member of the notorious Dharma family member, Harma ransomware has reborn as a new Harma Ouroboros ransomware variant. Just like its ancestor, it exploits unprotected Remote Desktop[4] and runs an executable file on a host computer. It renders a composition of RSA and AES ciphers to encrypt files and append a .harma file extension to .jpg, ,png., .doxs, .doc, and other file formats. Furthermore, it creates either INFO.exe or ReadMe.txt file as a ransom note, which contains the following information:
Your Files Has Been Encrypted
How To Recover:
Your Data Has Been Encrypted Due to The Security Problem
If You Want To Restore Your Files Send Email to Us
Before Paying You Can Send 1MB file For Decryption Test to guarantee that your Files Can Be Restored
Test File Should Not Contain Valuable Data ( Databases Large Excels, Backups )
Do Not Rename Files or Do Not Try Decrypt Files With 3rd Party Softwares, It May Damage Your Files
And Increase Decryption Price
Your ID : xxxxxxxx
Our Email : [email protected] Or [email protected]
How To Buy Bitcoin :
Payment Should Be With Bitcoin
You Can learn how To Buy Bitcoin From This Links :
hxxps://localbitcoins.com/buy_bitcoins
hxxps://www.coindesk.com/information/how-can-i-buy-bitcoins
RX99 ransomware
RX99 was noticed at the start of January 2019. This variant of Ouroboros is still using a combination of AES and RSA encryption algorithm. However, it exhibits a different file extension, which is .rx99. Therefore, the corrupted files turn out as [NAME_OF_FiLE].Email=[[email protected]]ID=[GTLBXNIVTRSBVESAJQEL].rx99. Victims receive a text file named How_to_Unlock-Files.txt, which urges people to contact [email protected] email the owner and pay the ransom within two days. After that, the price of the decryption doubles. The text file also contains information on how to purchase Bitcoins and how to create a cryptocurrency wallet.
Boruta file virus
Boruta ransomware or .boruta file extension virus is yet another member of an infamous Ouroboros ransomware family. Since it has been traced recently, there are not many technical details about it. However, it is known that it is actively distributed via spam emails as a .zip and .exe attachment. Besides, it can infect PCs via unprotected Remote Desktop just like its predecessors.
Upon the success of malicious Boruta Virus File ransomware launch, the virus multiplies malicious files within the system and starts file encryption using RSA and AES 256 ciphers. Corrupted data can easily be distinguished from the others by the .boruta file extension, and the fact that none of the files can be opened, deleted, or otherwise modified makes it clear that the system has been infected with Boruta Virus File ransomware.
The victim is also presented with a ransom note called New Text Document.txt. It is a simple text document filled with instructions on how to pay the ransom, the contact information, time during which the victim has to take actions, the number of Bitcoins to be transferred, Bitcoin wallet number and similar.
Ouroboros ransomware removal can not be done without a professional antivirus software
The word “manual” does not fit when we talk about ransomware removal. It is not possible to remove Ouroboros ransomware without a professional anti-virus tool. That’s because ransomware initiates multiple indestructible system changes, installs tens of malicious files, and runs various difficult-to-detect background processes.
Therefore, if ransomware has infected your PC, you should immediately run the PC in Safe Mode with Networking and run a full system scan with a reliable anti-virus tool. For this purpose, you can use SpyHunter 5Combo Cleaner or Malwarebytes tools.
However, Ouroboros removal using anti-virus software poses a risk of permanent loss of the encrypted files. Those who are not going to contact criminals and, even more, give away their money to crooks are very unlikely to decrypt files on their own. At the moment, there’s no Ouroboros ransomware decryptor, except for Zeropadypt ransomware. Thus, victims have to decide to pay the ransom or remove Ouroboros and try to recover at least some files using Windows Previous Version or third-party software recovery tools. If after Ouroboros removal is not enough to restore the system to the state prior to the infection, try fixing the damage with Reimage Reimage Cleaner Intego software.
This entry was posted on 2020-04-07 at 02:35 and is filed under Ransomware, Viruses.

