Trojan:Win32/Occamy.C is the malware that can open backdoors on the infected system for other hackers or load malware
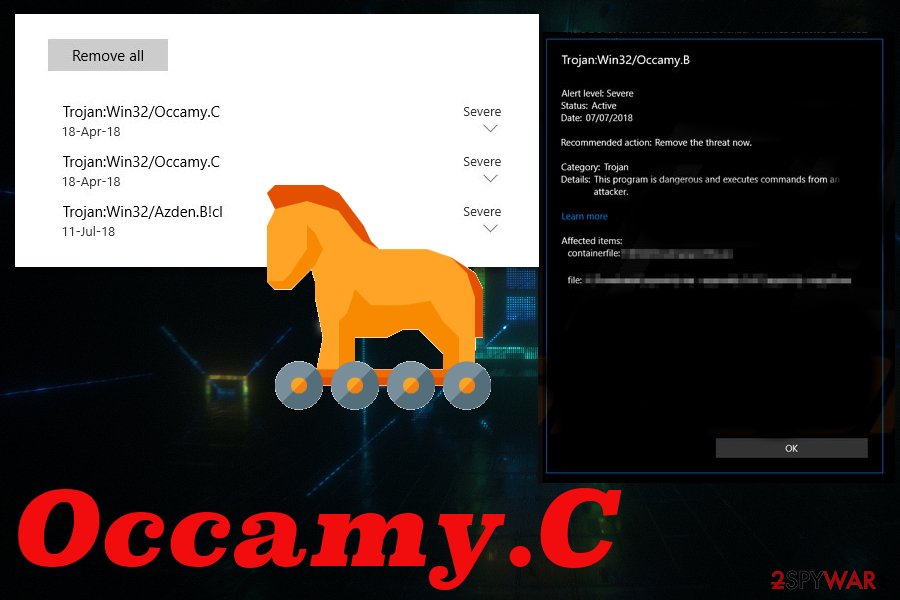

Trojan:Win32/Occamy.C is the malware that can be set to steal passwords or even spy on the victim but that depends on the particular version you encountered. This trojan is designed to stealthily infiltrate the computer and remain silently running in the background. This is why there are no visible symptoms, and the threat can run on the machine for a long time before the user even notices anything. A trojan is a type of the very devastating malware that can corrupt files on your computer or even causes system errors, damage files on the hard drive.
Since Occamy.C trojan drops copies of the malware in various folders, it becomes more difficult to remove. You encounter various system interruptions out of nowhere because of the changes trojan makes. Malware like this can be also used to deliver other malicious programs like ransomware.[1] You need a thorough malware termination so all the additional infections can get completely removed.
| Name | Trojan:Win32/Occamy.C |
|---|---|
| Type | Trojan |
| Purpose | Open backdoors for other malicious actors, install threats, steal information |
| Main danger | Can lead to privacy issues or even identity theft |
| Associated files | nc.exe |
| Associated programs |
|
| Distribution | Spam email attachments, software cracks, infected files |
| Elimination | Install professional anti-malware programs to remove Occamy.C |
This trojan, in particular, can be also called Occamy.C backdoor because it gives remote access to various other threat actors and infiltrates devices with malware like crypto miners or even ransomware. Many antivirus engines can detect this trojan and possibly remove it from the machine.
Trojan:Win32/Occamy.C can be one of the detection names that anti-malware displays after the system scan. However, many different programs have databases of their own, and heuristic names may differ from tool to tool. Make sure to get a reliable tool and scan the system entirely, then follow suggested steps and delete malware from the computer.
Occamy.C virus additionally can cause various issues and errors appearing on the screen:
- 0x00000124;
- 0x000000A4
- 0x000000FA;
- 0x00000054;
- 0x80244030 WU_E_PT_ECP_INIT_FAILED;
- The external cab processor initialization did not complete.;
- 0x80244010 WU_E_PT_EXCEEDED_MAX_SERVER_TRIPS;
- 0x8024001A WU_E_POLICY_NOT_SET A policy value was not set.;
- received an invalid response from the upstream server it accessed in attempting to fulfill the request.
Trojan:Win32/Occamy.C can affect various parts of the machine and since this threat infects Windows devices it even alters DLL files, other files of the system, Widoens registry entries. This is a common method to affect the infected device in general as much as possible so the virus can get launched each time the PC is rebooted.
Occamy.C trojan is the cyber threat that often gets used to deliver other malware.

Occamy.C trojan is the cyber threat that often gets used to deliver other malware.
The virus itself can come to the machine via infected DLL or EXE file which comes from maliciously infected email attachments, software cracks, or other malware that delivers Occamy.C directly on the machine. Trojan also can come via questionable freeware like MI-SUGAR 0.5.8, SoraView 1.0pr4, Functional 1.2, Parnian XTension 3.0, Cribbage Plus! 1.1.6, Small Business Tracker Deluxe 2.0. Make sure to remove these applications, especially if you haven’t installed them on purpose yourself.
Occamy.C is also called spyware because it allows attackers to gather data from the system or use different methods to tracks and collect data as banking credentials, logins, and passwords. In most cases, this data gets used for blackmailing purposes or in later scams.[2]
Occamy virus is the umbrella term for various trojans that has the same heuristic name. You may encounter Occamy.C, Occamy.A, or Occamy.B. However, the trojan is a complex malware which has many different purposes that may differ from developer or distributor or even the particular target. Trojan operates in the background silently, so you are not alerted about the presence of the malware.
Occamy.C trojan drops files onto the computer and launches executables or other tasks to send gathered data, download additional files, and accept commands from the remote attacker. Thanks to this fact, you can sometimes notice suspicious processes running in the background when you open the Task Manager.
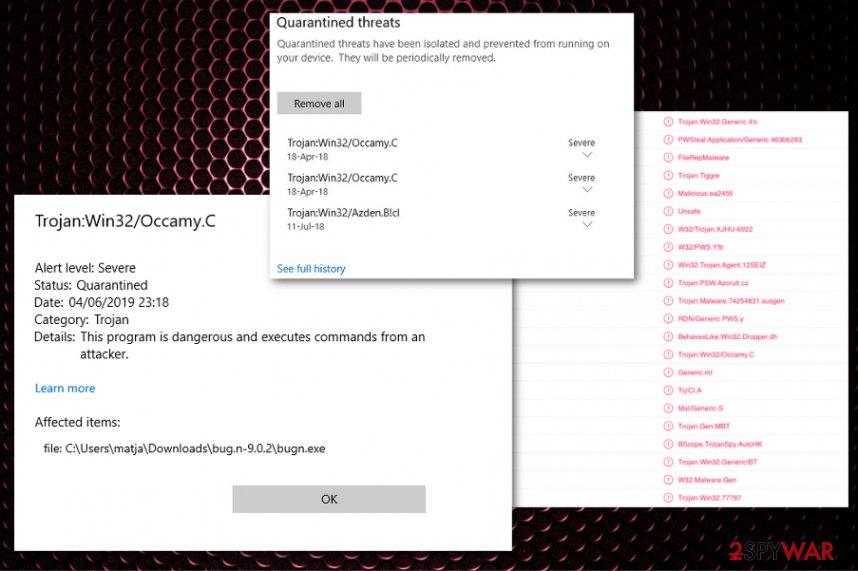
Trojan:Win32/Occamy.C is the name of a threat identified by Microsoft Security Software. It targets the core system of Windows and can launch various tasks.

Trojan:Win32/Occamy.C is the name of a threat identified by Microsoft Security Software. It targets the core system of Windows and can launch various tasks.
When you notice two similar processes or even identical EXE files running on the Task Manager, you can try to remove Trojan:Win32/Occamy.C by ending the task. Additionally, experts[3] note that when the suspicious file or process runs causing high usage of CPU and other resources, you can be sure that the process is not legitimate or safe.
Then, you can employ professional anti-malware for Occamy.C removal. Ending the malicious task to disable the virus and get an opportunity to launch your anti-virus is only a first step that allows ending the malicious background process. Additionally, scan the system with reputable anti-virus and finally run Reimage Reimage Cleaner to ensure that no corrupted files and similar system changes have been made.
Malicious code hidden in file attachments delivers malware
Sources of trojans can vary as functions of such threats are decided by the developer. However, typical trojan distribution involves spam emails disguised as letters from institutions or services, companies. Emails stating about financial information, receipts, order details or invoices deceive people, and they get tricked into opening such emails with file attachments or hyperlinks.
Once the document attached on the email gets downloaded and opened on the machine or link gets clicked, the malicious script gets either launched on the computer directly or triggers macros and payload carriers that distribute trojans or ransomware.
You can avoid these cyber infiltrations by paying close attention to emails you receive and messages on social media with suspicious links or file attachments. When the email contains a document or executable attached, it should raise your attention, especially when the sender is not a familiar service or company you use at the time.
Delete Trojan:Win32/Occamy.C with malware removal tools like anti-malware
There are many techniques of how such infections come to the system, but you shouldn’t forget about the dangerous side of Occamy.C virus infiltration – installation of other malware. Because of this additional payload dropping feature, you need a thorough system scan.
Employing professional anti-malware for Trojan:Win32/Occamy.C removal gives the advantage of cleaning other threats that you were not knowing about because when using the tool like this you can scan the machine entirely and remove all indicated programs or even system issues.
Get SpyHunter 5Combo Cleaner or Malwarebytes to check if they can remove Trojan:Win32/Occamy.C. Remember that there are a few different versions and possibly related viruses that may lure in the system. You may need to enter the Safe Mode before scanning the computer or find a more powerful tool for this task. Finally, checking the system for virus damage is highly recommended.
This entry was posted on 2020-02-18 at 08:53 and is filed under Trojans, Viruses.

