Maze ransomware is a cryptovirus that releases spam email campaigns targeting particular countries with false claims from government institutions
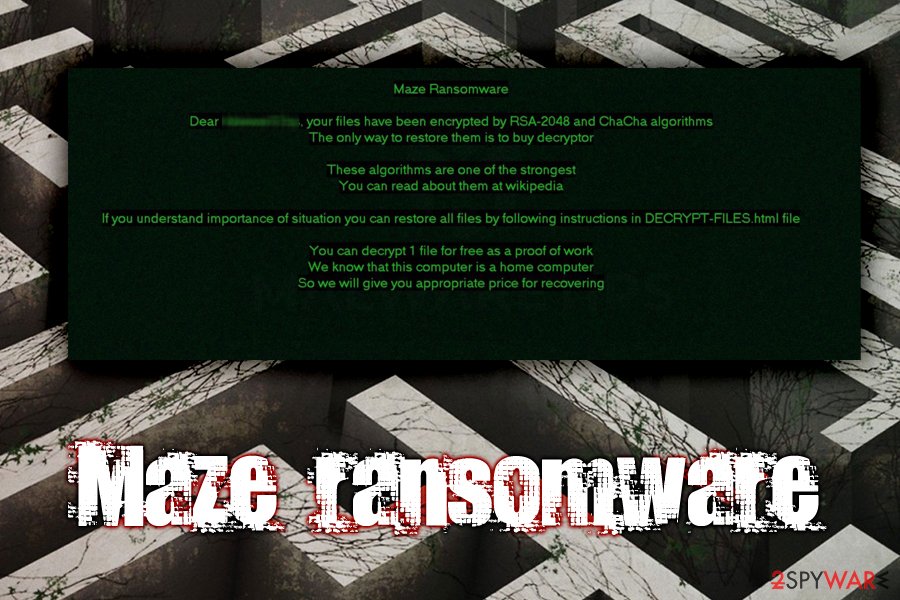 Maze ransomware, found by Jerome Segura, is a file-encrypting virus and also a successor to ChaCha ransomware. It uses a sophisticated RSA-2048[1] and ChaCha20 cipher to lock up data, and appends a string of random 4-7 characters at the end of each file, also using a marker within its structure – 0x66116166. The ransomware is known to have sophisticated methods of distribution because it creates emails with false claims and poses as agencies, government institutions, based on the more recent campaign against Italy.[2] The campaign revealed that users got spam emails pretending to be sent from the Italian Revenue Agency and the Agenzia Delle Entrate that is responsible for taxes and revenue for the government.
Maze ransomware, found by Jerome Segura, is a file-encrypting virus and also a successor to ChaCha ransomware. It uses a sophisticated RSA-2048[1] and ChaCha20 cipher to lock up data, and appends a string of random 4-7 characters at the end of each file, also using a marker within its structure – 0x66116166. The ransomware is known to have sophisticated methods of distribution because it creates emails with false claims and poses as agencies, government institutions, based on the more recent campaign against Italy.[2] The campaign revealed that users got spam emails pretending to be sent from the Italian Revenue Agency and the Agenzia Delle Entrate that is responsible for taxes and revenue for the government.
Maze ransomware is also known to be distributed via the help of a fake Abra site that hosts the Mobile Bitcoin Wallet app under the same name. Visitors who want to download the application will end up being redirected to a Fallout exploit kit,[3] which, under certain conditions, will implant the malicious payload without the users’ interaction whatsoever. After encrypting files, virus will drop a ransom note DECRYPT-FILES.html that asks victims to pay a ransom in BTC and contact bad actors via [email protected]. Additionally, the malware will also alter the background on the desktop, displaying another message from hackers.
| Name | Maze |
| Type | Ransomware |
| A variant of | ChaCha ransomware |
| Distribution | This malware strain is most commonly spread via the Fallout exploit kit. However, it also has a chance of showing through spam emails and their malicious attachments, fake updates, brute-forcing, and by employing other tactics. Recent campaigns were distributed via emails and infected word documents |
| Encryption algorithm | Bad actors use the RSA-2048 and ChaCha20 encryption algorithms to lock up all files and documents that are found on the targeted system |
| File extension | There is no accurate extension that is appended by Maze ransomware. Once the virus locks files, it adds a random 4-7 letter appendix to each filename |
| Related files | After successful infiltration, the file-locking virus brings the zprxqb.exe and Maze_Ransomware.exe files to the Windows computer system |
| Ransom note | Information about file encryption and ransom demands is placed in the DECRYPT-FILES.html which appears on the computer screen after data encryption |
| Contact | Criminals provide the [email protected] email address as a way to contact them and discuss all needed matters |
| New version | Maze ransomware developers have released a similar malware version that holds the exact same name. Even though the new variant also relies on successful encryption, the virus does not encrypt files if it finds the C:\hutchins.txt file in the computer system |
| Termination | Use a powerful anti-malware program to perform a thorough system checkup, detect all malicious strains, and remove Maze ransomware permanently |
| Decryption | File decryption is only possible via backups. However, third-party software might sometimes be helpful as well. We have provided and described three different tools at the end of this article |
Interestingly, the latest variant of Maze ransomware shows a different wallpaper based on computer type (for example, home computer, backup server, server in a corporate network, primary domain controller, etc.), which essentially changes the decryptor price.
While there is no free decryption tool that would be able to retrieve your data, you should not pay the ransom and instead focus on Maze ransomware removal and alternative file recovery methods, instructions for which we provide below. Keep in mind that you might get easily scammed if you transfer the money to the crooks.
While Maze ransomware was spotted being distributed with the help of Fallout Exploit kit, it does not mean that hackers do not employ other tactics, such as:
- Spam emails;
- Unprotected RDP;
- Fake updates;
- Pirated software and its cracks;[4]
- Torrent sites;
- Web injects, etc.
Therefore, even if your software and the Windows OS are patched with the latest updates to prevent Fallout EK, you might still be at risk if you do not use adequate security measures. To make sure you are protected from future Maze ransomware infections, check the second part of this article.
Maze ransomware in Italy
Independent researcher reported at the end of October 2019 that Maze virus released a campaign that targets Italy. The malicious malware attempted to infect systems with the help of a spam email campaign that delivers malicious word files and drops payload on the machine.
Emails came with legitimate-looking statements about new taxes, rules. The email is headlined “AGGIORNAMENTO: Attivita di contrasto all’evasione. Aggiornamento” and contains a word document called “VERDI.doc” which should involve the guidelines. However, the word document states about encryption of the content and then requires the reader to enable the content to read the text properly.
Once that is done, and the document is downloaded, opened on the machine, embedded macros get executed and downloads ransomware to the Temp folder on the system. Maze ransomware then gets launched and encrypts files, changes the wallpaper to an image with the guidelines on how to find a ransom note, and delivers a separate file DECRYPT-FILES.txt which includes instructions on contacting the virus developers.
The payment site that you should reach via the link provided in this ransom note shows the amount of ransom needed for the decryption key. It apparently differs from the type of device, a number of affected files, and other details about the victim. It can go up to $1200 or even more in Bitcoin. Unfortunately, decryption is not possible, paying is not an option, so you should remove Maze ransomware with anti-malware tool and recover files using backups.
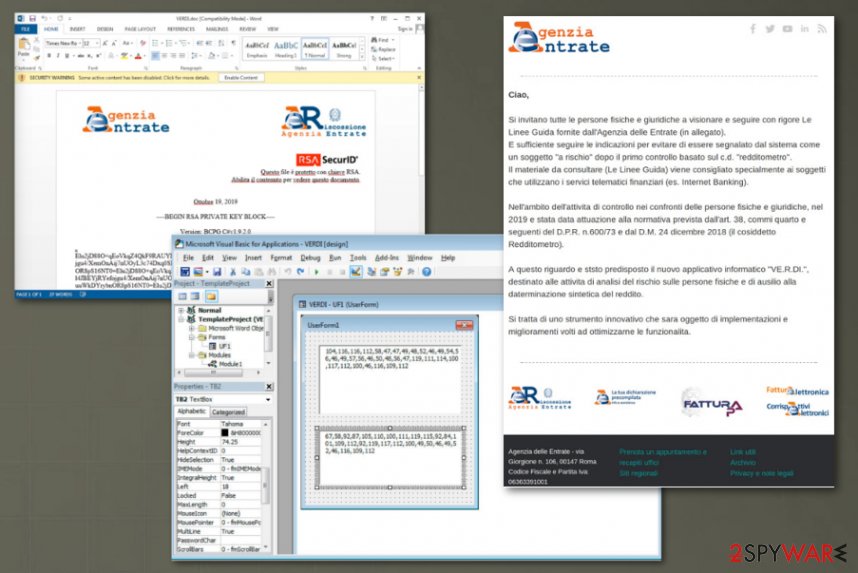
Maze ransomware is the threat that released a campaign targeting Italians and suggested people follow the instructions.
Once the payload of Maze ransomware is populated, it will contact 2 domains and 15 hosts, alter the Windows registry, delete Shadow volume snapshots to complicate the recovery process, and perform other malicious tasks required for its operation, for example, corrupting the Windows hosts file.
Ransomware viruses might seek to damage the hosts’ file in order to prevent the victims from accessing security-related websites and forums where they could get valuable information on the malware’s removal process. So, while you opt to remove Maze ransomware from your computer, make sure to delete the damaged file too.
After establishing itself and locking the files, Maze ransomware will display the following note:
0010 SYSTEM FAILURE 0010
*********************************************************************************************************************
Attention! Your documents, photos, databases, and other important files have been encrypted!
*********************************************************************************************************************The only way to decrypt your files, is to buy the private key from us.
You can decrypt one of your files for free, as a proof that we have the method to decrypt the rest of your data.
In order to receive the private key contact us via email:
[email protected]
Remember to hurry up, as your email address may not be avaliable for very long.
Buying the key immediatly will guarantee that 100% of your files will be restored.
Below you will see a big base64 blob, you will need to email us and copy this blob to us.
you can click on it, and it will be copied into the clipboard.
If you have troubles copying it, just send us the file you are currently reading, as an attachment.
At the bottom of the note, victims can locate a Base64 string that includes such information and user’s login name, Windows version, other technical data, and a private key. All this information is allegedly required for cybercriminals in order to decrypt files locked by Maze ransomware.
Speaking of Maze ransomware removal, various AV vendors recognize the threat under such names as TR/Kryptik.ijmxi, or Ransom.Maze, but such things differ based on the particular virus database.[5] This is why we suggest using professional anti-malware tools to terminate the malware entirely.
However, make sure to choose a reliable software. Note that manual elimination is not possible here as you risk damaging your system. You should remember that some system files get damaged too, Reimage may help you with those corrupted files after Maze virus removal.
Once you delete Maze virus entirely, you can connect your backup device to retrieve your data. In case you have no backups prepared, there are very little chances of recovering files for free, although you should try third-party software. We provide all the instructions and download links to such tools below.
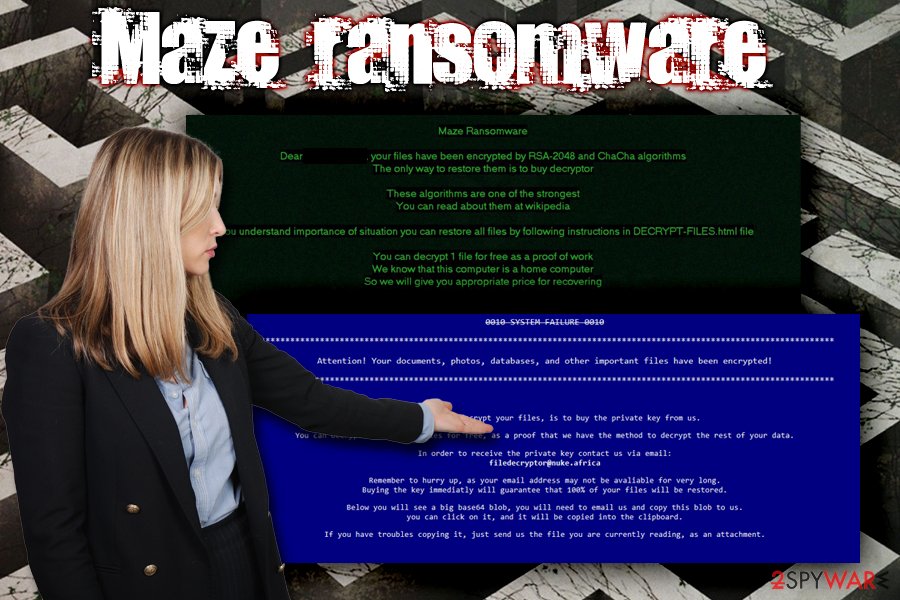
Maze ransomware is type of malware that enters the machine with the help of Fallout exploit kit and encrypts all data on the device by using RSA + ChaCha20 ciphers
The new version includes the same Maze ransomware name
A very similar, almost identical version to Maze ransomware was found by nao_sec researcher.[6] This variant comes from the same family and even holds the same name “Maze”. The new variant also locks up data with a random appendix, however, there is one exception here.
The new variant of Maze ransomware looks for the C:\hutchins.txt file and if it is found on the infected system, data locking does not happen in this scenario. However, if the file is not found, the malware successfully proceeds with the encryption and drops the DECRYPT-FILES.txt ransom message.
Even though there is not much information given on the demanded price, cybercriminals often urge for a ransom between $200 and $2000. However, paying the money might only lure you into a scam and you will receive no decryption tool at all.
Additionally, it is known that the new Maze ransomware version appears through an exploit kit known as SpelevoEK. However, that does not deny the possibility that the malicious payload might be brought through malicious hyperlinks/ads, infectious macros, and p2p networks.
Ransomware prevention tips
Hackers are sophisticated individuals who decided to put their knowledge for evil deeds. Therefore, they often employ a variety of advanced methods to distribute the payload of the malware, ensuring the high infection rates among victims.
Nevertheless, those who are careless are by far the most vulnerable and prone to infections. While such threats like adware or other PUPs might not be devastating, ransomware can result in permanent data loss. What is more, those who decide to pay for the decryptor might also end up losing money as well.
Therefore, follow these tips from industry experts to avoid malware infections in the future:
- Install security patches for your operating system, as well as all the installed applications;
- Use reputable anti-malware software with real-time protection feature;
- Be aware that spam emails that carry attachments (such as .doc, .html, .pdf, etc.) or include hyperlinks might be infected with malware, including ransomware;
- Do not fall for believing in suspicious emails that claim to be from FedEx, DHL, or other reliable shipping companies even though you have not been waiting for an order to arrive lately;
- Ensure the safety of all your accounts by using password managing app and two-factor authentication;
- Use ad-blocker on high-risk sites, although do not forget to add exclusions for sites you want to support;
- Do now download pirated software or its cracks or keygens;
- Scan every unknown executable with tools like Virus Total or Hybrid Analysis;
- Use a VPN when using the Remote Desktop Protocol and ensure a strong password.
Finally, to negate the damage done by a ransomware infection, prepare backups regularly. For more accurate information, we want to inform users that ransomware developers are likely to hack RDP such as the TCP Port 3389 for secret malware infiltration. Additionally, exploit kits such as Fallout and SpelevoEK are widely used for distributing ransomware-related payload.
Terminate Maze ransomware virus by using powerful malware removal tools
You should not attempt to remove Maze ransomware manually, as such a method should only be used by IT professionals. Besides, cryptovirus can modify Windows system files and embed itself deep into the OS, so reverting these changes is almost impossible. According to experts from Virusai.lt,[7] it is very important not to skip any malicious objects, otherwise, the ransomware virus might boot itself automatically within the next PC startup process.
Instead of taking the risk on your own hands, employ reputable anti-malware software for Maze ransomware removal. We suggest you use anti-malware tools. You also should benefit from tools that may fix the damage and system files after the virus termination. Applications like Reimage or SpyHunter 5Combo Cleaner, Malwarebytes, or other options are also available – choose the one that suits you the most.
Be aware that the Maze ransomware virus might prevent your security software from performing correctly. In such a case, you need to access Safe Mode, as it will temporarily stop malware’s activities.
Once you delete Maze virus, you can attempt to recover your data. Please follow detailed instructions for this process below. We cannot assure you that all of the below-provided techniques will work perfectly but trying them is definitely a better thing to do than the risk to lose a huge amount of money while paying the cybercriminals.
This entry was posted on 2019-11-04 at 10:47 and is filed under Ransomware, Viruses.

