KODC ransomware is a file locking virus that mainly spreads via software cracks
KODC ransomware is a money extortion-based malware that stems from the notorious family Djvu
KODC is a new variant of Djvu/STOP ransomware family that was first spotted by security researcher Michael Gillespie in the second half of January 2020.[1] Just as its predecessors .piny, .redl, .nbes, and others, .kodc version belongs to the newer surge of infections that apply a more secure RSA encryption algorithm[2] to lock all videos, documents, PDF, and other personal files, and then demands $980 to for an alleged KODC ransomware decryption tool.
All data encrypted in such a way is appended with .kodc extension, and no access to it is available. Additionally, the virus also drops a ransom note _readme.txt explaining to users what happened to their data and that they should contact hackers via [email protected] or datahelp.iran.cc. Unfortunately, while recovering data without paying KODC ransomware developers might be possible, the likelihood is relatively low.
| Name | KODC ransomware |
| Type | File locking virus, crypto-malware |
| Malware family | Djvu/STOP ransomware – one of the most prolific crypto-malware families, as hundreds of versions have been released since its release in December 2017 |
| Distribution | Most of the victims infect their computers with this virus when they download pirated applications or use software cracks |
| Encryption algorithm | Ransomware uses a secure RSA encryption algorithm to lock the most popular file types, although system files and executables are skipped in order to ensure that Windows is functional |
| Extension | Each non-system and non-executable file located on the local and networked drives is marked with .kodc extension; for example, a picture.jpg turns into picture.jpg.kodc |
| Ransom note | _readme.txt is dropped into each folder that holds the encrypted files |
| Contact | [email protected] or datahelp.iran.cc |
| Ransom size | Users are asked to pay $490 or $980 worth of Bitcoin for decryption software |
| Data recovery | Recovering data from backups is the only secure way to retrieve it without risks. However, in cases where KODC ransomware failed to contact its C2 server, Emsisoft’s decrypter might work; alternatively, Dr.Web’s paid decryption service might be used to retrieve at least some types of files. If nothing helps, recovery software can be used, although chances of it being successful are relatively low – check the recovery section below for more information |
| Malware removal | Use reputable anti-malware software to scan your machine in Safe Mode with Networking |
| System fix | If you experience issues after you delete malware, you can apply Reimage Reimage Cleaner to fix virus damage and revert Windows to its pre-infection state in order to avoid reinstalling it completely |
Djvu ransomware family has been one of the most prevalent crypto-malware for some time now, and security researchers now have a long history with creating tools like STOPDecrypter, as well as other decryptors that previously helped many users to recover their files for free. Nevertheless, because versions of this virus might install additional modules that could steal personal information, it is important to remove KODC virus and all its components promptly.
.KODC files virus is mostly spread with the help of software cracks and pirated software installers. Therefore, most users who visit torrent, warez, and similar sites are at an elevated risk of getting infected. To avoid this, you should stay away from pirated software sites, as they are known to be used as one of the main attack vectors for ransomware, trojans, worms, cryptojackers,[3] and other malware. That said, cybercriminals might be open to new methods, so check out our tips below to ensure your computer’s safety in the future.
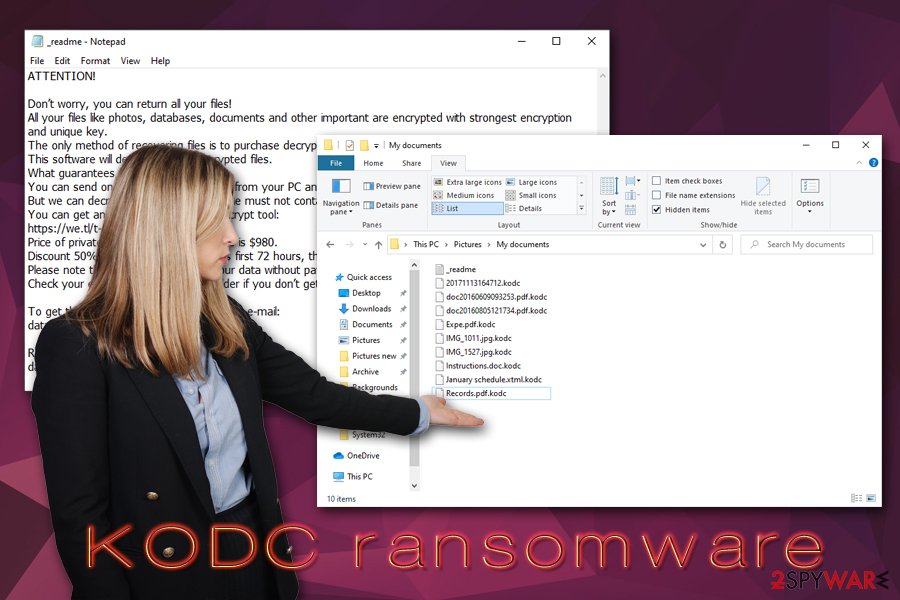
KODC ransomware is a file locking virus that primary spreads with the help of software cracks
Infection and encryption routine
Once inside the system, KODC ransomware does not immediately encrypt all data, as special preparations need to be made and system modified. As soon as the main executable (can be named as anything, for example, crack.exe, c652.tmp.exe, or update.exe) is launched, it places itself into %Temp%, %AppData% or %LocalAppData% folder.
From there, .KODC virus begins to launch all the necessary files that would enable it to perform file encryption, and also modify Windows system settings, such as changing Windows registry, disabling startup repair, and deleting Shadow Volume Copies.
It is also important to note that the virus also adds a predetermined list of IP addresses into Windows hosts file – this action prevents users from reaching those websites. These are security-focused sites that could help users with .KODC ransomware removal and file recovery process, such as 2-spyware. To fix this, users should delete the hosts file located in the following folder:
- C:\Windows\System32\drivers\etc\
During the infection process, KODC also attempts to establish a connection with its Command & Control server[4] – a process which, as researchers found out, fails relativity often. If that happens, users have a greater chance of data recovery with the help of Emsisoft’s decryption tool; alternatively, if Shadow Volume Copies fail to be deleted, retrieving data becomes a much easier task by using automatic backups.
If KODC ransomware performed the file encryption process using an offline ID, Emsisoft’s tool might help to recover them
KODC ransomware uses an asymmetric[5] RSA encryption algorithm to encrypt all data on the machine, as well as all the connected drives. Nevertheless, it skips system, executable, and some other file types in order to ensure that Windows can operate – it is not threat actors’ goal to corrupt the computer but rather extort money. During the encryption process, KODC ransomware might show a fake Windows update pop-up window to cause less suspicion and prevent users from shutting down the machine.
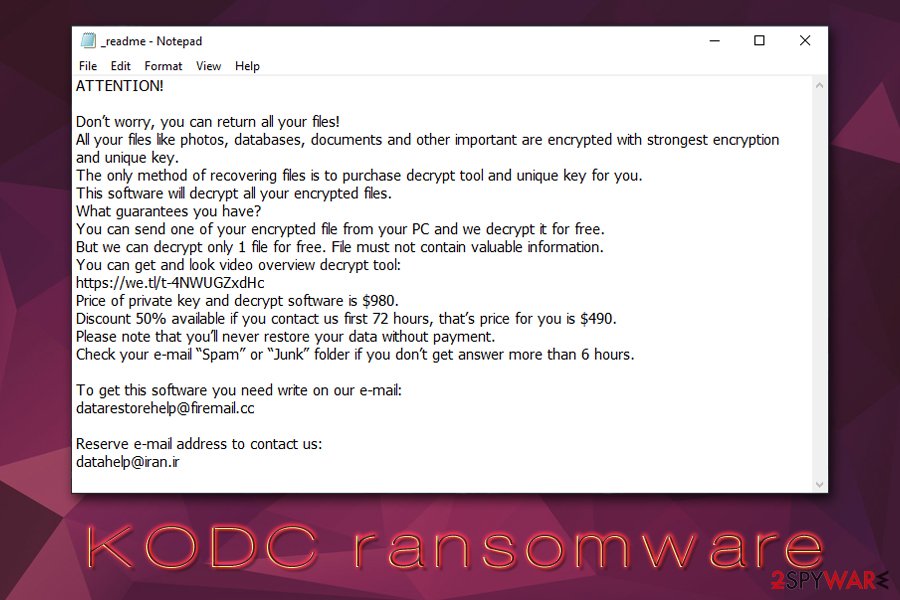
_readme.txt file pops up before victims’ eyes as soon as the file encryption process is over. As a result, users see their file icons as “blanks,” and each of them has a .kodc extension appended. The note states the following:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-4NWUGZxdHc
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
[email protected]Reserve e-mail address to contact us:
[email protected]
As stated above, if none of the predetermined ransomware functions fail, paying criminals might be the last hope of retrieving the locked data. However, keep in mind that threat actors cannot be trusted, and might never send you the required software to recover .KODC files.
If you have no data backups, you should copy all the important files that were encrypted before using .KODC remover, as such a process might permanently damage them and turn them into a cluster of unreadable data. In such a case, even the decryption tool from the attackers would not be able to recover your files.
Note that KODC might damage certain system files or registry files in a way that might start making Windows to malfunction. Thus, if you experience system crashes, errors, and other disturbances after the infection, scan your machine with Reimage Reimage Cleaner – it can fix virus damage and save you from reinstalling the operating system.
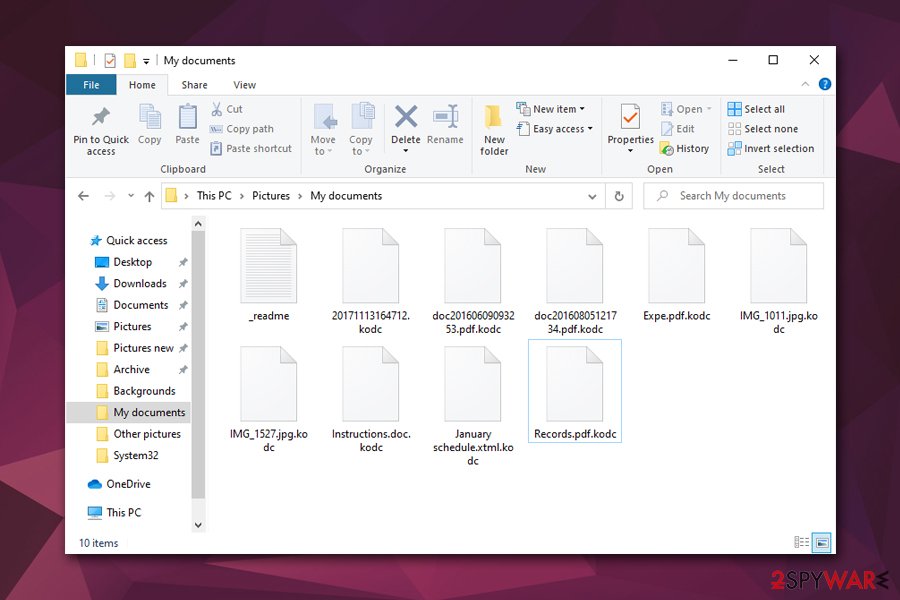
As soon as KODC ransomware performs file encryption process, victims are unable to access their data
Software cracks are dangerous – stay away if you want to keep your computer virus-free
The safety record of software cracks and pirated program installers, while highly debatable, still serves as a major security risk. Because cracks are essentially tools that are used to break certain code within an application, they will be considered malicious by most anti-malware applications. In some cases, cracks/keygens/loaders are designed to work as intended but, due to a modified executable file by cybercrooks, a malicious payload might also be installed in the background. Therefore, even if you scan a crack with anti-malware software, there is no way to check whether it is actually malicious or not. As a result, you might inject all sorts of malware into your computer, and you will not even know about it (unless it’s ransomware, of course).
Thus, the best solution would be avoiding not only software cracks but also websites that distribute such software, as they are known to have a poor safety record and might have additional infection triggers, such as malicious ads. Here are some basic tips from security advisers:
- Equip your computer with powerful anti-malware software and keep it updated.
- Prepare regular backups of your files – use remote cloud-based service or an external device like USB flash.
- Patch your operating system and all the installed software with the latest security updates.
- Employ secondary protection measures like a Firewall and ad-block.
- Make sure you turn off Remote Desktop connections as soon as it is not needed and ensure its protection during the usage (such as not relying on the default TCP/UDP port 3389).
- Never reuse passwords and make sure you use strong ones for all your accounts; alternatively, use a password manager.
- Do not allow macros to be run on documents that were clipped to an email from unknown origin; do not click on embedded links.
Backup your encrypted files and only then remove KODC ransomware from your machine
While KODC ransomware removal is imperative to regaining full control of your computer, you should not rush doing some. The first step you should do (unless you are sure that you have all your files on backups), is using an external device to copy all the encrypted files over. As mentioned before, any type of system modifications after the KODC virus infection might result in a permanent corruption of data.
Once that is done, you should then remove KODC ransomware from your machine by scanning it with anti-malware software, such as SpyHunter 5Combo Cleaner, Malwarebytes, or other security tool (note that new variants might require a scan with different anti-malware, as each of them uses different databases which might not recognize a threat immediately after its release). If you are having trouble, you should access Safe Mode with Networking as explained below – malware might tamper with security applications in order to stop victims from terminating it.
Finally, you can then attempt to recover your lost data in one of the ways described below. There are several options available, although there is no guarantee that any of them will work for you.
Remove KODC using Safe Mode with Networking
To remove KODC file virus safely, enter Safe Mode with Networking as explained below:
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
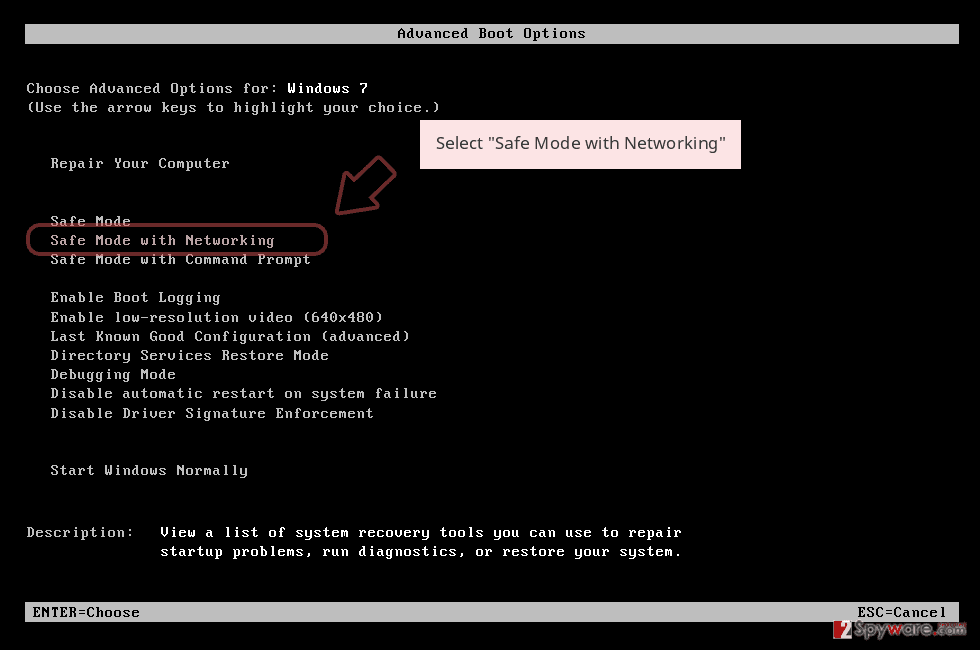
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
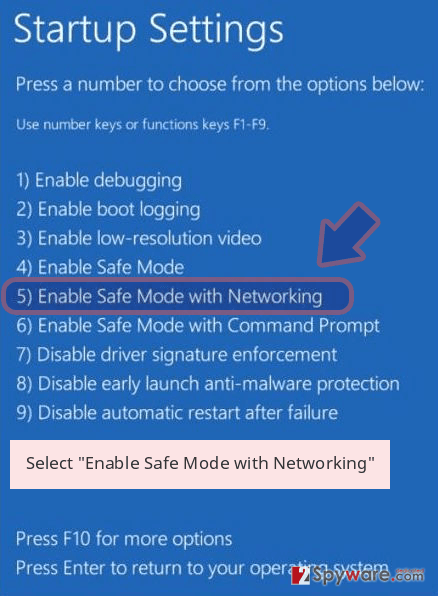
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete KODC removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove KODC using System Restore
System Restore might sometimes be useful when trying to eliminate the virus:
Bonus: Recover your data
Guide which is presented above is supposed to help you remove KODC from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If your files are encrypted by KODC, you can use several methods to restore them:
Make use of Data Recovery Pro
Data Recovery Pro might be successful in recovering some portion of your files if you did not use your computer after the infection that much. In other words, the less you use your PC after the ransomware locked your data, the more chances you have of recovery software being successful.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by KODC ransomware;
- Restore them.
Windows Previous Versions Feature might be useful
This method might work if you had System Restore prepared before the infection.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
ShadowExplorer might be the best solution
Shadow Volume Copies might not get deleted if you are lucky. In such cases, ShadowExplorer might serve as an excellent tool to retrieve the encrypted files.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Try Emsisoft’s decryption tool
In case KODC ransomware used an offline ID to lock your files, you should immediately make use of Emsisoft’s decrypter – it is highly likely to recover your files in such a case. Additionally, you could also contact Dr.Web – the security firm offers a paid service that could recover some file types (MS Office documents, PDFs, etc.).
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from KODC and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner , SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2020-01-23 at 03:13 and is filed under Ransomware, Viruses.

