[email protected] ransomware – malware that hits Windows computers and demands a BTC ransom for the release of locked files
[email protected] ransomware – malware that uses unique ciphers to code up data that is found on the infected Windows PC

KENS@TUTA.IO ransomware – malware that uses unique ciphers to code up data that is found on the infected Windows PC
[email protected] ransomware is considered to be a malware form from the family of file-encrypting threats. The main goal of this parasite is to locate all of the remaining files, folders, and documents on the infected Windows computer and use a unique algorithm to lock them all up. When the encryption process is finished, all the file names get the [email protected] appendix added and this is the mark that shows victims that the data has been coded.
Afterward, [email protected] ransomware releases a ransom message named how_to_back_files.html where cybercriminals urge for a Bitcoin ransom in exchange for the release of the blocked components. Hackers also insist on receiving communication via email [email protected] or [email protected]. Afterward, the users are likely to receive further payment instructions and the ransom price as it is not mentioned in the message. Our recommendation would be to avoid paying criminals as there is a high chance of getting scammed and not receiving the decryption tool at all.
| Name | [email protected] ransomware |
|---|---|
| Type | Ransomware virus/file-encrypting cyber threat |
| Family | This malware belongs to the GlobeImposter ransomware family |
| Extension | When all of the files, folders, and documents are encrypted with a unique algorithm, all of the filenames receive the [email protected] appendix as a sign of the encryption process |
| Ransom note | The ransomware virus provides the how_to_back_files.html ransom note where the ransom demands, crooks contacts, and threatenings are written |
| Price | Even though hackers do not provide a particular price that needs to be paid in exchange for the decryption tool, these people outline that Bitcoin cryptocurrency is a requirement. Further information is said to be passed to victims after they contact hackers via email addresses |
| Crooks’ emails | Crooks provide [email protected] or [email protected] email addresses as a way to make contact with the victims |
| Distribution | Ransomware infections are commonly spread through phishing email messages that pretend to come from reliable companies. The malicious payload often comes in the form of some type of attachment |
| Removal tip | If you have been dealing with this malware lately, you should take care of the elimination process ASAP. For this task, employ reliable antimalware software to make sure that the cyber threat has been deleted properly |
| Fixing tool | If you have encountered any damaged or compromised areas on your Windows computer system, you can try repairing them by employing a fixing tool such as Reimage Reimage Cleaner Intego |
[email protected] ransomware is a virtual parasite that can be downloaded to the computer system through an infectious attachment that comes clipped to a phishing email message. Also, you can receive the malicious payload from a software crack that is downloaded from a pirating network. This mostly happens to users who are not aware of their online safety.
[email protected] ransomware developers target Windows computer systems as this type of operating system is the most commonly used in the world and easier to hack than macOS or Linux. When the malware settles on the PC, it makes significant changes to the Windows Registry, Task Manager, and other directories.
Some ransomware viruses can end up messing with the computer boot options and system settings. Also, these threats can disable Firewalls and other security software to stay persistent on the infected Windows computer and avoid detection. Beware that [email protected] ransomware might be capable of these activities too.
[email protected] ransomware can also run specific PowerShell commands to delete the Shadow Volume Copies[1] of the encrypted documents. This way the authors of the malware seek to harden the decryption process for the victims. Besides, they also write threatenings in the ransom message to keep users away from other file recovery options:
Your files are encrypted!
Your personal ID
–Your important documents, databases, programs, saving games, documents, network folders are encrypted for your network security problems.
No data from your computer was not stolen or removed.
To restore your files, follow the instructions.
How to get the automatic decryptor:
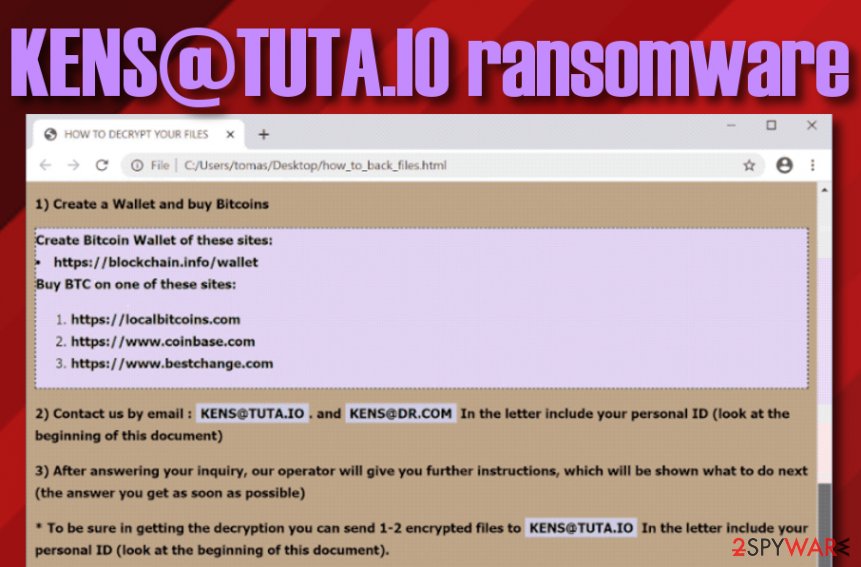
1) Create a Wallet and buy Bitcoins
Create Bitcoin Wallet of these sites:
hxxps://blockchain.info/wallet
Buy BTC on one of these sites:
hxxps://localbitcoins.com
hxxps://www.coinbase.com
hxxps://www.bestchange.com
2) Contact us by email : [email protected]. and [email protected] In the letter include your personal ID (look at the beginning of this document)3) After answering your inquiry, our operator will give you further instructions, which will be shown what to do next (the answer you get as soon as possible)
* To be sure in getting the decryption you can send 1-2 encrypted files to [email protected] In the letter include your personal ID (look at the beginning of this document).
** Write here on the mail for a faster response [email protected]
Attention!
Do not attempt to remove the program or run the anti-virus tools.
Attempts to self-decrypting files will result in the loss of your data.
Decoders are not compatible with other users of your data, because each user’s unique encryption key.
We are not liars or cheaters. You pay – we help.
The demanded ransom price is not mentioned and will supposedly be provided when the victims aim to connect hackers via email. However, [email protected] ransomware creators urge for a Bitcoin ransom price as digital currency transfers help cyber crooks to stay anonymous and avoid their transactions getting cost. However, this also decreases the victims’ chances of receiving their lost money almost to zero.
[email protected] ransomware can also initiate remote malware installations. Ransomware viruses[2] can bring others of its kind or can include trojans, spyware to the computer system. This way the users can receive important file losses, get their data and money stolen, experience permanent system or software corruption.
[email protected] ransomware removal is the only way to diminish the chances of getting infected with additional malware. Also, you will not be able to recover your files if you do not get rid of the ransomware. Note that it is very important to terminate all malicious components from the computer system, otherwise, the infection can automatically return within the next computer boot process.
You can remove [email protected] ransomware from your Windows PC with the help of a reliable antivirus product that is capable of detecting the malware and dealing with it. Also, if you have discovered any system compromisation that happened during the malware attack, you can try repairing the altered areas by employing a tool such as Reimage Reimage Cleaner Intego.
[email protected] ransomware is a malware form that belongs to the GlobeImposter ransomware family

KENS@TUTA.IO ransomware is a malware form that belongs to the GlobeImposter ransomware family
Paying the ransom vs. trying third-party tools
Crooks who distribute ransomware viruses want to receive their payments as soon as possible and their only goal is money. Sometimes these people might make it look like they care about what is going to happen with the victim’s files but they truly do not. By paying the demanded ransom price for [email protected] ransomware developers or any other hackers, you risk not receiving the decryption tool at all or getting a fake one.
Criminals are likely to scare people by claiming that if they try to touch their files, they will be permanently damaged, etc. Also, crooks discourage using third-party software as it is also claimed to cause severe destruction. However, this is not true and alternative software is not going to destroy your files. If you choose the right tool, it might truly be helpful and allow you to restore at least some of your locked files and documents.
Since there is no official decryption tool released for files that have been locked by [email protected] ransomware, we also recommend employing third-party tools that might help you to recover at least some of your files. Note that this is definitely better than letting crooks to benefit from you and tricking you. You can find three different tools provided at the end of this article. Go through all of the suggestions and try out the most suitable ones.

File-encrypting malware and phishing emails are closely related
Cybersecurity experts from LosVirus[3] urge people to be careful of spam letters and various received email that you were not expecting lately. Crooks often misuse the user’s naivety and credulity and aim to drop legitimate-looking messages to random people’s email boxes. You might receive an email from some type of shipping, healthcare, or banking organization. However, you should not rush to believe in it if it was very unexpected.
First, check the sender and if the letter is coming from some type of rogue person – delete it immediately. Also, search the entire text for grammar mistakes as official companies would not leave any in their email messages. However, you can even try contacting the company that has emailed you via mobile phone, this way you will be sure if the message is official or not. Most importantly, do not open any attached files without scanning them with antimalware software first.
Ransomware infections can also get delivered through software cracks, for example, key generators that are posted on peer-to-peer websites such as The Pirate Bay. These types of networks do not offer anything legitimate and many hackers often find ways how to misuse them for their own illegal purposes.
Installing reliable antimalware protection is also a step that should be taken by every computer user as automatic security ensures a higher level of safety that cannot be achieved only by the user himself. Also, do not forget to regularly update your antivirus/antimalware tool as outdated software might also be the target of crooks.
Advanced removal possibilities for [email protected] ransomware
If you have been attacked by [email protected] ransomware, you should complete its removal process as soon as possible before it causes any additional malware infiltration. Also, you will not be able to restore your files if you do not get rid of the parasite first.
For [email protected] ransomware removal, employ reliable antivirus tools that would be capable of deleting such complex malware from your Windows computer. Also, if the ransomware virus has been blocking your antimalware product lately, you can try diminishing such unexpected changes with the help of Safe Mode with Networking. The instructions on how to perform this method are added to the end of this article.
When you remove [email protected] ransomware from the PC and are sure that no malicious entries are left, you can start searching for possible system damage. Tools such as SpyHunter 5Combo Cleaner and Malwarebytes should help you find all of the altered objects. If the scan results show any infected areas, you can try repairing them with another program such as Reimage Reimage Cleaner Intego.
Remove [email protected] using Safe Mode with Networking
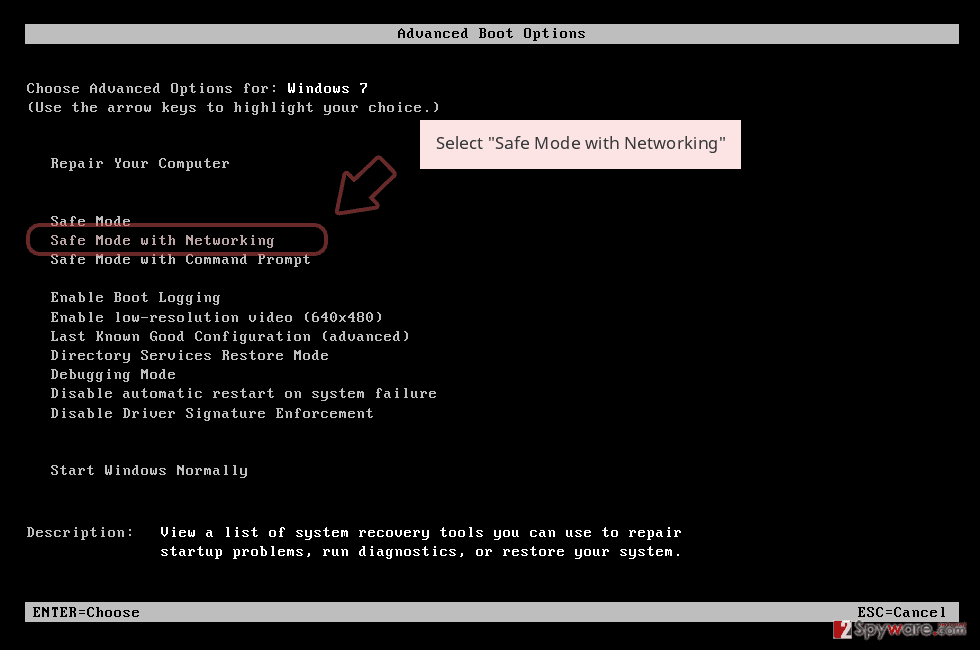
To diminish malicious changes and deactivate the ransomware virus on your Windows computer, you should reboot the machine in Safe Mode with Networking as shown in the below-provided guidelines:
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
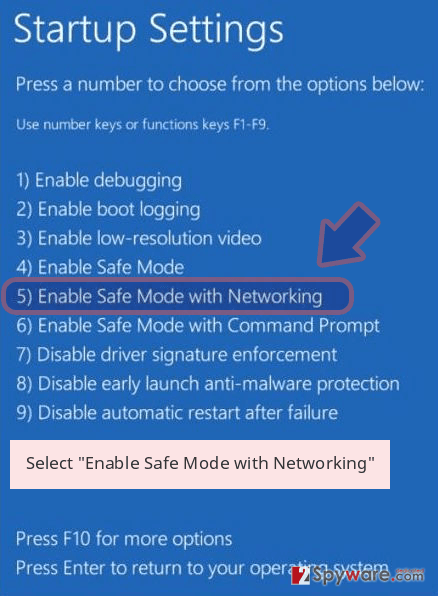
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner Intego or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete [email protected] removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove [email protected] using System Restore
To deactivate the parasite and all of the malicious settings that it has included on the Windows machine, use the System Restore feature. If you do not know how to activate this type of function, look at the following instructions.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove [email protected] from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
Locked files can cause a lot of stress and the users might rush to pay the demanded price to the crooks. However, this is not a really good option as there is a lot of risk of getting scammed. Rather than taking such chances and probably losing your money for nothing, try some of the following data recovery methods.
If your files are encrypted by [email protected], you can use several methods to restore them:
Employ Data Recovery Pro for file restoring tasks
If the ransomware virus has encrypted your files, you can try recovering some of them by using this piece of software. Carry out all steps exactly as required to reach the best results possible.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by [email protected] ransomware;
- Restore them.
Use Window Previous Versions feature to recover some data
If you have enabled the System Restore function in the past, applying this method might bring you very good results and help you to restore at least some of your files and folders.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Chose Shadow Explorer for data recovery
Try restoring at least some files and documents with the help of this software. However, note that the product might not work if the ransomware virus has permanently erased or destroyed the Shadow Volume Copies of encrypted data.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
Currently, cybersecurity experts are still working on the official decryptor.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from [email protected] and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner Intego, SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2020-03-27 at 17:29 and is filed under Ransomware, Viruses.

