GoldenEye virus is the new ransomware version of Mischa and Petya ransomware creators

Authors of Petya and Mischa ransomware[1] viruses have developed a new one, which is called GoldenEye virus. Despite that the virus is named after the sequel of James Bond film franchise[2], the cyber threat has no other associations with it.
The malicious software brings updated Petya and Mischa viruses into the computer and uses them to corrupt data stored on the disks. Upon arrival on the target system, GoldenEye ransomware finds a random .exe application on the system, copies its name, and saves its executive file under the copied name in %APPDATA% folder.
This file is then automatically executed and run. First of all, the virus unfolds a high-level attack, which reads files on the system and encrypts them with AES encryption in CBC mode. This key is 32 bytes long and cannot be guessed or brute-forced easily. In fact, it is nearly impossible to do so.
During the encryption, GoldenEye appends specific file extensions to the files to show the victim which files were encoded. Once the ransomware encrypts all data, it attempts to bypass User Account Control (UAC) to implement low-level attack and install Petya ransomware on the PC.
In case the UAC is set to maximum, an annoying pop-up asking to allow the malicious program to make changes on the computer comes up repeatedly.
The “Yes” will execute Petya, and the “No” option will get you Mischa. In case the UAC is set to low or default, the malware bypasses it and successfully installs Petya[3]. After encrypting the victim’s files, Goldeneye malware saves YOUR_FILES_ARE_ENCRYPTED.TXT ransom note on the desktop, which provides “three easy steps” on how to restore encrypted data.
While NotPetya/Petya.a wreaks global havoc, Goldeneye virus makes a move as well
Besides May 12, which netizens may remember as the day when notorious WannaCry came into daylight, the world will remember June 27, 2017 as well. On this day, a new threat struck the virtual community. Though initially, it raises assumptions that it was none other than the latest version of Petya, soon specialists have found that it is an independent malware labeled as NotPetya/Petna/Petya.a. [4]
It managed to break into systems of governmental institutions, advertising agencies in the UK, nuclear power plant in Ukraine, wreak operation of petrol stations in the USA.
Fortunately, an IT specialist has found a way how to prevent the cyber assault for now.[5] Users have to create a text file or download the file.
While everyone has concentrated attention on the latter threat, it seems that the developers of the original Petya virus were working on another campaign. The Cadbury chocolate factory located in Tasmania reported to have been hit by Goldeneye version, though, according to the ransom image, it might be the same Petya.a virus.[6] Similar reports have been recorded in Romania as well.[7]
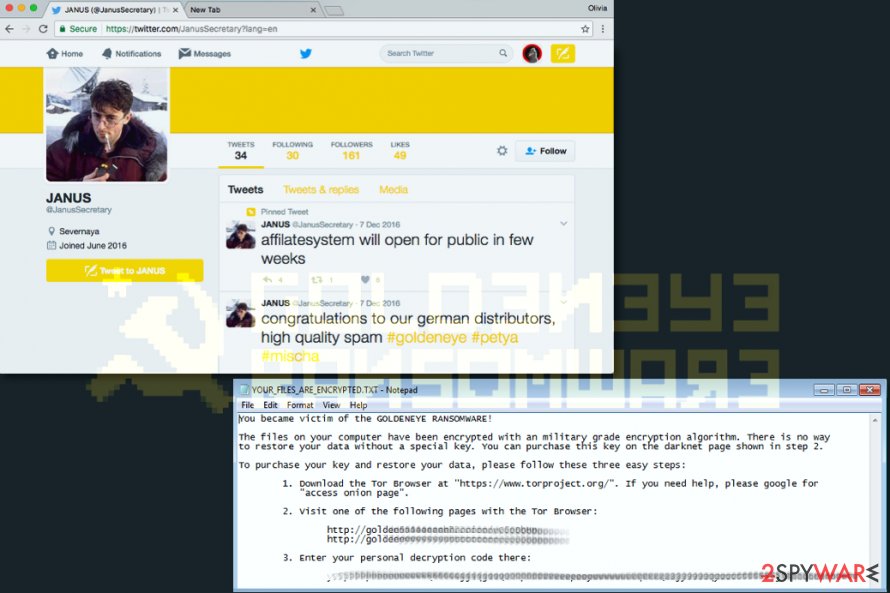
In this picture, you can see a Twitter account of GoldenEye author and the ransom note (YOUR_FILES_ARE_ENCRYPTED.TXT) that the virus leaves on the system after it encrypts files.

In this picture, you can see a Twitter account of GoldenEye author and the ransom note (YOUR_FILES_ARE_ENCRYPTED.TXT) that the virus leaves on the system after it encrypts files.
Speaking about the low-level part, the malware crashes the system and starts it with a bogus CHKDSK. This system tool is supposed to check logical file system errors; however, this fake version implements Master File Table encryption via Salsa20.
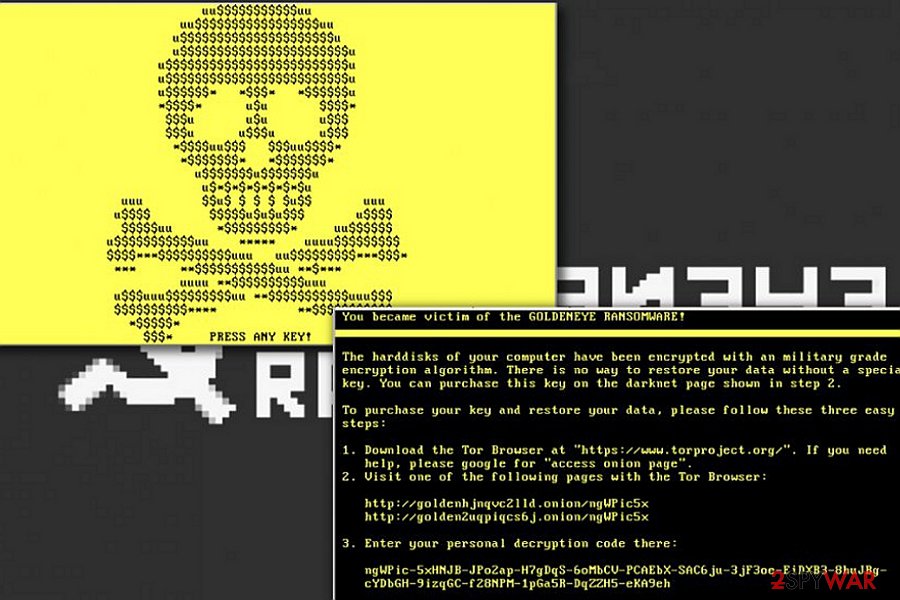
Once this procedure is finished, the computer displays a golden screen with an ASCII skull blinking on it. The screen says “PRESS ANY KEY!” and then displays the same information like YOUR_FILES_ARE_ENCRYPTED.TXT ransom note. It states that the data in hard disks was encoded by using a complex military-grade encryption method and asks for a ransom. Victims are instructed to follow access Tor network and proceed with the payment.
Usually, it demands 1,3 BTC which equals approximately 1000 USD. Needless to say, that it is unwise to pay the crooks since racketeers earn stunning amounts of money from ransomware business and there are few reports of returned data [8]. The information from the ransom note is displayed below.
The hardisks of your computer have been encrypted with an military grade encryption algorithm. There is no way to restore your data without a special key. You can purchase this key on the darknet page shown in step 2.
To purchase your key and restore your data, please follow these three easy steps:
1. Download Tor Browser . If you need help please google for “access onion page”.
2. Visit one of the following pages with the Tor browser :
[page link] [page link]3. Enter your personal decryption code there:
[address]If you already purchased your key, please enter it below.
The provided web addresses can be accessed only via the Tor browser. The indicated pages are designed for each victim individually. The web page consists of three sections – Payment, FAQ, and Support. The crooks promise to provide the decryption key right after the victim pays the indicated ransom.
GoldenEye Decrypter requires a correct key in order to work, otherwise, all files could be destroyed. Therefore, the Decrypter provides an option to backup encrypted files so that in case the victim enters the wrong key, another chance to decrypt them would be left.
If you have become a victim of GoldenEye attack, we highly suggest you remove GoldenEye malware via Safe Mode with Networking using anti-malware tools like Reimage Reimage Cleaner Intego or SpyHunter 5Combo Cleaner. Read instructions on how to begin GoldenEye removal below the post.
The transmission preferences
As common for the type of such viruses, GoldenEye hijack takes place after a victim opens an infected email and enable macro settings [9]. The latest version of this ransomware was detected to be the German version. It seems that the actor behind this ransomware, who calls himself/herself Janus, provides an affiliate program for anyone who wants to join him and help to distribute the ransomware.
As common for ransomware, the payload is disguised in a fake report attachment. The very message is entitled to Bewerbung and addresses a victim in a formal manner. It might disguise in the following .xls files: Wiebold-Bewerbung.xls, Meinel-Bewerbung.xls, Seidel-Bewerbung.xls, Wüst-Bewerbung.xls, Born-Bewerbung.xls, and Schlosser-Bewerbung.xls.
Afterward, when they are opened, you are asked to enable the content. Likewise, the ransomware activates incorporated base64 strings to proceed further with the encryption. As for the prevention tips, do not rush to open any emails even if they might be sent by the FBI or the police officer. Verify the sender before opening the attachments.
Get rid of Goldeneye ransomware
Firstly, you need to eradicate the file-encrypting malware. For that, you can employ an anti-spyware tool, for example, Reimage Reimage Cleaner Intego or Malwarebytes. Make sure that virus definitions are updated for the software to remove GoldenEye virus completely. Only when the process is complete, you might proceed to data recovery options. We have provided several of them for your convenience.
If you cannot complete GoldenEye removal due to the locked screen or a non-responding computer, do not panic and use our guidelines. Since Petya has been cracked down after a while, the new version might be terminated eventually, though it might take a while.
Remove GoldenEye using Safe Mode with Networking
If you want to remove GoldenEye ransomware from your computer and you can’t do that because it blocks your remover, you should try Safe Mode with Networking method before launching it. Make sure you run a full system scan as soon as you disable the virus.
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
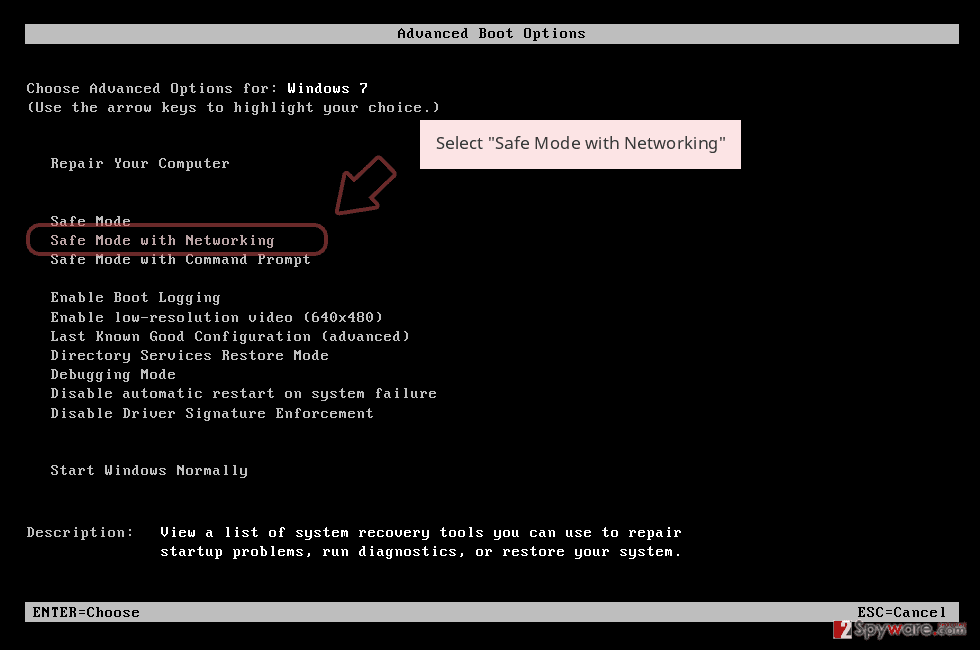
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
Windows 10 / Windows 8
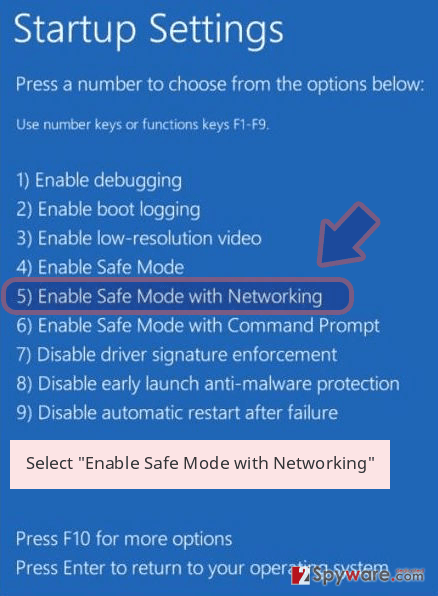
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner Intego or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete GoldenEye removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove GoldenEye using System Restore
If rebooting to Safe Mode with Networking failed to help you, you should try using System Restore method to disable GoldenEye. Once you perform the steps given below, you should run a full system scan with our recommended security software to remove its malicious files.
Bonus: Recover your data
Guide which is presented above is supposed to help you remove GoldenEye from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If your files are encrypted by GoldenEye, you can use several methods to restore them:
Opting for Data Recovery Pro to restore files encrypted by GoldenEye ransomware
This program might be one of the last chances to decrypt the files since there is no decryptor at the moment.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by GoldenEye ransomware;
- Restore them.
Can Windows Previous Version feature help you to recover data locked by GoldenEye virus?
It is an incorporated feature in Windows OS. There is a chance of retrieving each file by following the below-displayed instructions.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
How viable is ShadowExplorer?
This program gives you a bigger probability since it restores the files by accessing shadow volume copies. It is an effective way to return the files unless the ransomware deletes the copies beforehand.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
GolderEye decrypter is not available yet
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from GoldenEye and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner Intego, SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2020-05-22 at 06:23 and is filed under Ransomware, Viruses.

