GlobeImposter is a ransomware virus that has been updated over 100 times: the latest version spotted in spring 2020
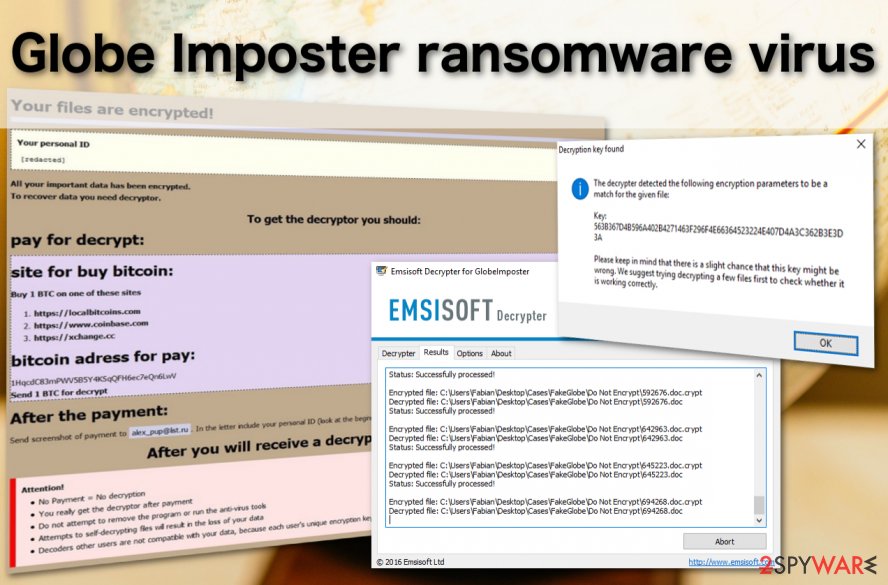

Globe Imposter is a crypto-ransomware that mimics an infamous Globe ransomware. Since it features similar characteristics, it is often referred to as Fake Globe. It has been infecting multiple machines since 2017 and keeps coming back with new versions. Since the release, the ransomware has been updated more than a hundred times, each version switching to a different file extension.
The latest version of the GlobeImposter before EMSISOFT released its decryptor showed up in early June 2018 and is dubbed as .emilysupp file extension virus. Since then, the virus went through a period of silence and returned in May 2020 with a new version named C4H ransomware. The latter does not differ much from is ancestors, except that it uses a .C4H file extension and has no decryption software available.
| SUMMARY | |
| Name | Globe Imposter |
| Type | Ransomware |
| Related to | Globe ransomware |
| Dubbed as | Fake Globe |
| Cipher used | RSA & AES |
| Versions | Over a hundred released. Each appends the different file extension |
| Main versions | GlobeImposter, GlobeImposter 2.0 |
| Latest version |
.emilysupp – discovered in May 2018. drops Read_Me.html note and urges users to contact hackers via [email protected] or [email protected] .C4H file extension virus – revealed in May 2020. It generates a ransom note Decryption INFO.html and demands victims to contact them via [email protected] or [email protected] email. |
| Decryptable? | Some versions only. For that, an official EMSISOFT GlobeImposter decryptor can be used. |
| Elimination | Download SpyHunter 5Combo Cleaner or Malwarebytes. Do not attempt manual recovery as it may lead to a permanent file loss. |
| System recovery | Upon GlobeImposter removal, it’s recommended to scan PC with the Reimage Reimage Cleaner Intego utility to recover corrupted Registry Keys, processes, and system files. |
Since its appearance, GlobeImposter has been appending new file extensions using AES / RSA cipher, and and been providing new email address (currently, victims are urged to contact the criminals via [email protected] or [email protected]). In response to the number of new versions flooding the cyberspace, EMSISOFT specialists created a free decryption tool. You can find it at the end of the article. However, not all versions are decryptable.
Currently, malware spreads using a misleading email attachment which is called “Emailing: IMG_20171221_”. Once it infects the system, it encrypts files by appending one of the numerous different file extensions, such as[1]:
.DREAM, ..doc, ..txt, .0402, .BONUM, .ACTUM, .JEEP, .GRAFF, .trump, .rumblegoodboy, .goro, .au1crypt, .s1crypt, .nCrypt, .hNcrypt, .legally, .keepcalm, .plin, .fix, .515, .crypt, .paycyka, .pizdec, .wallet, .vdulm, .2cXpCihgsVxB3, .medal, .3ncrypt3d .[[email protected]]SON, .troy, .Virginprotection, .BRT92, .725, .ocean, .rose, .GOTHAM, .HAPP, .write_me_[[email protected]], .VAPE, .726, .490, .coded, .skunk, .492, .astra, .apk, .doc, .4035, .clinTON, .D2550A49BF52DFC23F2C013C5, .zuzya, .LEGO, .UNLIS, .GRANNY, .911,.reaGAN, .YAYA .needkeys, .[[email protected]], .foSTE, .490, .ILLNEST, .SKUNK, .nWcrypt, .f41o1, .panda, .BIG1, .sexy, .sexy2, .sexy3, .kimchenyn, [email protected], .WORK, .crypted_uridzu@aaathats3as_com, [email protected], .TRUE, [email protected], .[[email protected]], .btc, .[[email protected]], [email protected], .black, .[[email protected]], .rrr, .{[email protected]}.AK47, .LIN, .apk, .decoder, .[[email protected]].rose, .fuck, .restorefile, .CHAK, .Chartogy, .POHU, .crypt_fereangos@airmail_cc, [email protected], .crypted_monkserenen@tvstar_com, .crypt_sorayaclarkyo@mail_com, .STN, .VYA, .crypt_damarles@airmail_cc, .pliNGY, .ñ1crypt, .suddentax, .Nutella, .gif., .emilysupp, .C4H
The purpose of the GlobeImposter is to encrypt files and demand to pay the ransom by using scare tactics.[2] As soon as it finishes data encryption, malware delivers a ransom note where extortionists sell the decryption key for the victims.[3] The instructions on how to get back access to the files might be provided in one of these files:
- Read___ME.html;
- HOW_OPEN_FILES.hta;
- how_to_back_files.html;
- RECOVER-FILES.html;
- !back_files!.html;
- !free_files!.html;
- #HOW_DECRYPT_FILES#.html;
- here_your_files!.html)
- !SOS!.html
- Note Filename: support.html;
- READ_IT;
- #HOW_DECRYPT_ALL#.html;
- Read_ME.txt;
- Read_Me.html;
- Decryption INFO.html;
Different versions of the Fake Globe include a different email or BitMessage addresses in order to communicate with victims. Criminals asked victims to contact them using these email addresses. However, the list might expand because new variants keep emerging:
- [email protected]
- [email protected]
- write_me_[[email protected]]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected]
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
- [email protected];
Fake Globe virus can encrypt files just as successfully as any other ransomware that has been developed from scratch. Considering that there are numerous variants of this ransomware, we can only say that certain viruses tend to use RSA and AES ciphers which most ransomware use in their attacks [4]. While some versions GlobeImposter can be decrypted, the rest remain extremely dangerous.
The security experts from Emsisoft have succeeded in creating a decryption tool the ransomware – a free Globe Imposter decrypter which helps ransomware victims recover their files and restore order on their computers [5]. At the moment of writing, this rescue tool has already been downloaded over 11844 times which only proves that the parasite is spreading rapidly and everyone should take action to protect their devices against it.
If it is already too late for you to take any preventative steps, you should scroll down to download the decrypter and learn how to remove GlobeImposter from your computer. We suggest scanning the system with Reimage Reimage Cleaner Intego or Malwarebytes to eradicate the infection.
Necurs botnet was used by hackers to contaminate as many PCs as possible
Criminals have significantly increased the rate of infections with GlobeImposter since they used Necurs botnet to create a massive malspam campaign at the end of 2017. The spam emails were distributing this file-encrypting virus in the form of 7zip attachments. According to the analysis, they contained VBS files that install the ransomware once opened.
Researchers detected two variants of malicious emails:
- The first campaign pushes emails with a subject line that includes the word “Emailing” and a random string of numbers, for instance, “Emailing – 10006004318”. The body of the message informs about the “strictly confidential” email.[6]
- The second campaign spreads emails with a subject line “FL-[random-numbers] [day.month.year.]. However, these emails are empty and do not contain any text. However, it includes a 7zip attachment that matches the name of the subject line.[7]
This version of malware appends .doc file extension to targeted file types on the affected computer. Following data encryption, it drops a ransom note in HTML file where victims are offered to buy a decryption software for $1000 in Bitcoins in two days. After the deadline, the size of the ransom will increase.
GlobeImposter has multiple variants
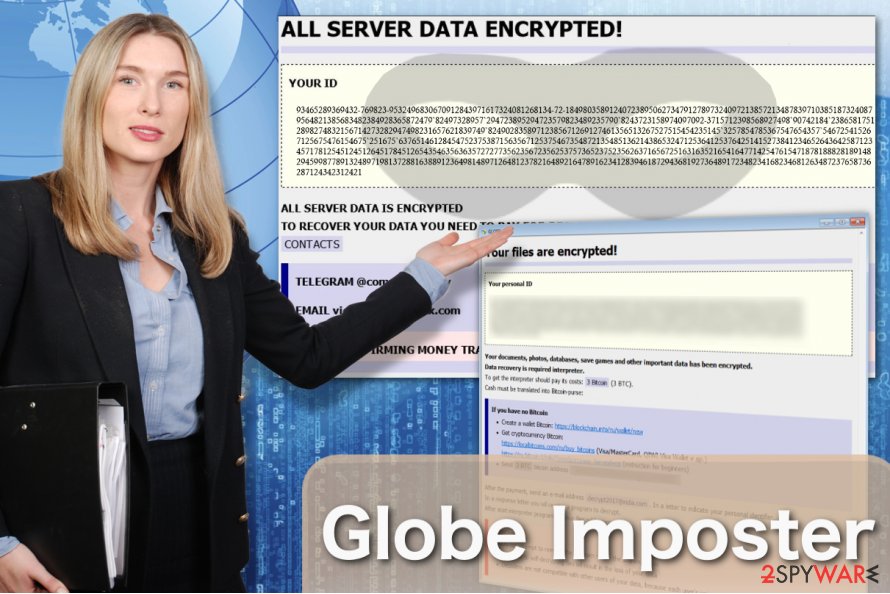
Globe Imposter ransomware has numerous offsprings which might come in a different language or append a different file extension.

Globe Imposter ransomware has numerous offsprings which might come in a different language or append a different file extension.
GlobeImposter 2.0 virus can be recognized by the .FIX extension which is appended at the end of the filenames following data encryption. Since this crypto-malware employs a complex encryption technique, it is impossible to recover corrupted information and this variant of Globe Imposter is undecryptable.
However, its victims should still follow the removal guidelines to get rid of GlobeImposter 2.0 and fix their computers. Note that regular computer users are not advised to perform the elimination without the help of an IT technician or professional anti-malware software.
Since you cannot retrieve files encrypted by GlobeImposter 2.0, it is always a good idea to keep backups of your most important files somewhere, where the malicious ransomware script could not reach and encrypt them. This way, you will always have the backup recovery plan in case your data gets corrupted.
GlobeImposter German version. To reach more victims, ransomware developers often adapt their malicious creations to target specific countries and speak to the users in their native language.
The German ransomware version is a perfect example of such a strategy: the ransom note with explanations on how to recover the encrypted files is presented in German. The criminals demand 0.5 Bitcoin for the data recovery key. After the money is transferred, the victims are required to send a screenshot of the transaction to an indicated email address – [email protected].
But even the completion of all the criminal’s demands does not guarantee files will be recovered. The extortionists are unpredictable and can simply vanish with the money. That’s why we recommend to stay safe and carry out the GlobeImposter German version elimination instead.
KeepCalm virus. The virus encrypts and appends them with .keepcalm extensions which are where this virus gets its name from. The parasite runs a strong encryption script to render the victim’s files unreadable and then offers to decrypt the files if only the victim is willing to pay a considerable amount of money.
The extortionists give a more detailed description of data recovery in the ransom note called HOW_TO_BACK_FILES.html. Essentially, the victims must contact the criminals via [email protected] email address. The ransom payment snapshot along with the personal ID must be sent to this email to receive the decryption tool. Unfortunately, this is not what normally happens.
On the opposite the criminals tend to vanish as soon as they have the money in their pockets, leaving victims stranded with a bunch of undecryptable information. In such a case, all you can do is remove KeepCalm from the infected device and to bypass the encryption in some other, safer ways.
Wallet GlobeImposter virus. At the beginning of May 2017, a new version of the fake Globe virus was detected. This time, it uses .wallet file extensions in order to spoof Dharma ransomware, which is known to be using .wallet file extension to mark encrypted files.
The ransomware drops how_to_back_files.html ransom note on the desktop, which contains the victim’s ID and criminals’ BitMessage address in case the victim wants to reach out to them – BM-2cXpCihgsVxB31uLjALsCzAwt5xyxr467U[@]bitmessage.ch.
The virus deletes Volume Shadow Copies to prevent the victim from restoring files without paying the ransom.
.s1crypt file extension virus. This parasite serves as another variation of the ransomware. It presents the demands in how_to_back_files.html ransom note. It also informs users that all their documents and data have been encrypted.
In order to decrypt files, victims should purchase the specific decoder which supposedly costs 2 bitcoins. Needless to say that the tool does not boost the chances of data recovery.
In addition, the developers also provide three additional links for users who are not aware of how to purchase bitcoins. In case of technical difficulties, they may contact the perpetrator via [email protected].
The ending of the email may suggest that the cybercriminal may have registered domain in the territory of Switzerland. Yet again, it may be only a diversion. Antivirus tools may identify the malware as Trojan.Generic.DB75052.
.au1crypt file extension virus. The malware functions as the counterpart of the former version. Its GUI also differs. The ID seems to be the result of AES and RSA cryptography. The ransom note, how_to_back_files.html, explains that users’ files have been encrypted due to “a security problem with your PC.”
Unlike the former version, which indicated the bitcoin address, this version instructs users to contact cyber criminals via [email protected] and [email protected]. Though it seems that the malware is rather a “summer entertainment” for the hackers, members of the virtual community should be vigilant.
At the moment, its Trojan is identifiable as Variant.Adware.Graftor.lXzx.
.goro file extension virus. This virus specifically targets victims via weak Remote Desktop Protocols (RDP). Since the version is still brand new, there is no decrypter released yet. The developers also used a similar .html ransom note for instructions.
You may terminate the goro.exe task on your Task Manager to interrupt the malware process. This version is also associated with the Wallet virus version of the Dharma ransomware family.
At the moment, this variation is detectable as Trojan[Ransom]/Win32.Purgen, Arcabit Trojan.Ransom.GlobeImposter.1 by majority security applications. [email protected] email address is another indicator of this version.
.{email}.BRT92 file extension virus. This virus does what its name suggests – adds .{email}.BRT92 extensions to the encrypted files. In addition to the new extension, this Globe virus follow-up displays its ransom note via #HOW_DECRYPT_FILES#.html file.
On this html page, victims are provided with a personal ID number which is basically a code that helps perpetrators differentiate between their victims.
Hackers indicate two email addresses [email protected] and [email protected] for communication with the victim.
.ocean file extension virus. This one of the Globe Virus versions that showed up in 2017. The virus adds .ocean extensions and drops a note called !back_files!.html to demand payment. In order to retrieve their files, victims must contact the criminals via [email protected] email address. 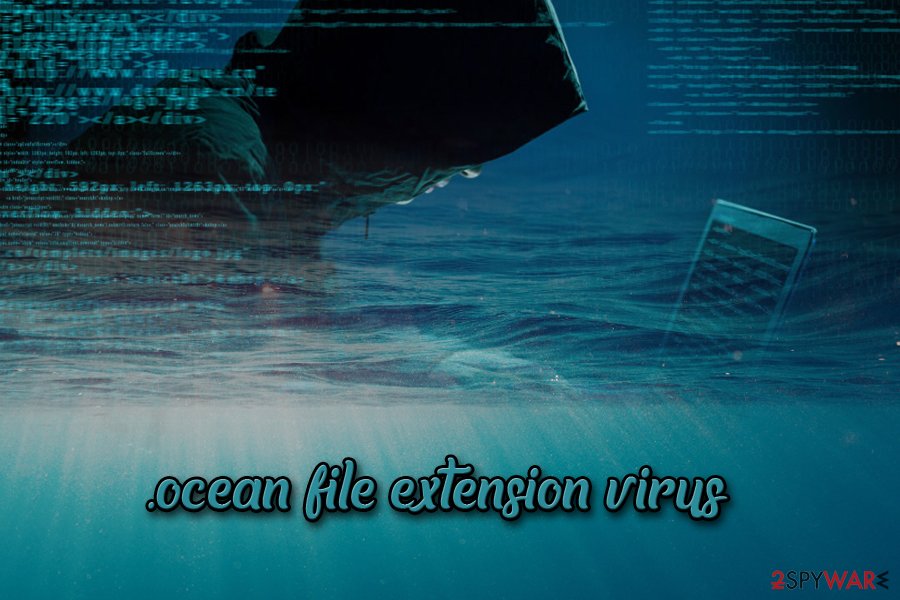
Hackers come up with yet another variant – .ocean

Hackers come up with yet another variant – .ocean
The hackers claim that the price of the file decryption will depend on how quickly the victim manages to contact them. Nevertheless, collaborating with the criminals is never a good option as you might end up scammed.
A1Lock virus. A1Lock is one of the more successful versions of the GlobeImposter virus. There are several versions of this parasite and each of them appends files with different extensions. We currently know about variants that use .rose, .troy and .707 extensions.
Ransom demands are typically listed in the documents labeled How_to_back_files.html and RECOVER-FILES.html. For communication with the victims, criminals indicate the following addresses: [email protected], [email protected], [email protected], and [email protected].
.Write_me_[[email protected]] file extension virus. Looking at its design, this version of the Fake Globe differs from most of the virus versions. Nevertheless, it works exactly the same: encrypts files and offers to obtain a paid decoder. Victims who are willing to pay for their files must contact the criminals via [email protected] email address.
The risk here is huge because the criminals are free to vanish after the victims pay for the decryptor. This way, files that the parasite marks with .Write_me_[[email protected]] extensions may remain this way forever.
.725 file extension virus. This ransomware version creates RECOVER-FILES.HTML with a ransom-demanding note. The virus, just like its previous versions, encodes files to demand ransom from the victimized computer user. The ransomware is recognized from file extensions that it adds to corrupted files – .725. Some of the spotted versions demand 0.19 Bitcoin as a ransom. So far, no 725 ransomware decryption tools were created.
.726 file extension virus. A little later after the discovery of .725 version, .726 file extension virus emerged. It is clear that GlobeImposter developers are rapidly changing the extensions they use, probably to confuse the victims and prevent them from finding help online. The ransomware saves RECOVER-FILES-726.html as a ransom note on the victim’s PC. Victims report that the virus asks for 0.37 Bitcoin in exchange for the data decryption tool.
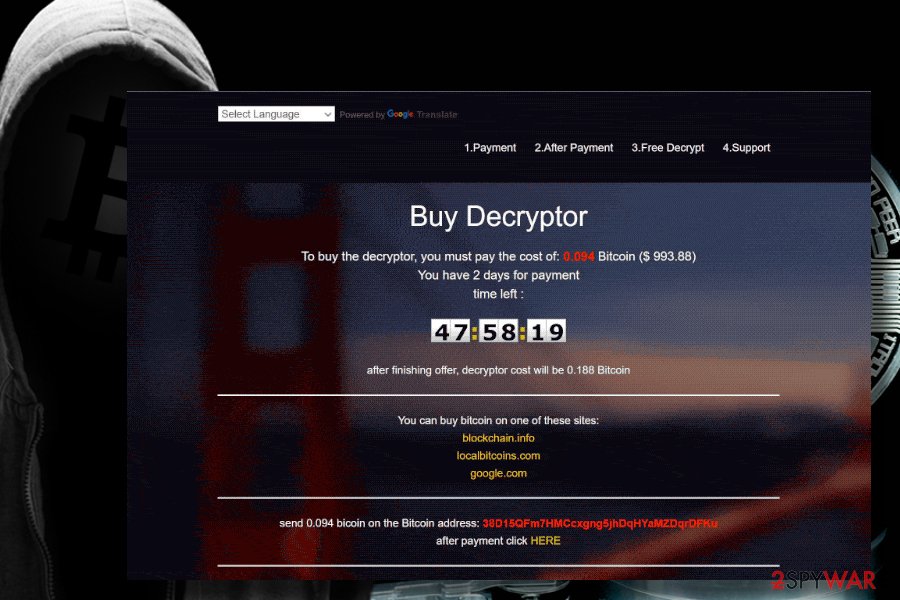
.gif ransomware uses macros in MS Office documents to initiate malicious code.

.gif ransomware uses macros in MS Office documents to initiate malicious code.
.490 file extension virus. .490 file extension virus is considered to be a version of A1Lock (GlobeImposter) that uses .490 to mark encoded files and creates !free_files!.html as ransom note for the victim. At the moment, no decryption tools are known to be effective against this virus.
.492 file extension virus. Yet another shady GlobeImposter remake uses .492 file extensions to stamp encrypted files. The design of the ransom note remained the same, but the name of the ransom note changed – now it is called here_your_files.html. The ransom note opens via default web browser and says that files were encrypted due to a security problem with the victim’s PC. According to the note, files can be recovered, but the victim has to write to [email protected] or [email protected].
.crypt file extension virus. Globe Imposter Crypt ransomware virus has been spotted being distributed by BlankSlate malspam. The mail spam campaign, which was recently used to distribute BTCWare Aleta virus, now switched to this new version of GlobeImposter. The ransomware comes in an email that contains no message – just a ZIP file attachment.
The attachment is usually named in this way: EMAIL_[Random Digits]_[Recipient’s Name].zip. This ZIP file contains another ZIP file, also named with a random set of digits. The final ZIP contains a JavaScript file dubbed with a random set of characters.
Once executed, the JS file connects to a certain domain and downloads 1.dat file, which is ransomware’s executable. It immediately encrypts all files on the system, adding .crypt file extension on its way. The virus then drops !back_files!.html ransom note, which instructs the victim to mail to [email protected] for instructions on how to decrypt files.
At the moment, none of the available ransomware decrypters can decrypt these files, so data backup is the only tool that can recover your files.
.coded file extension virus. Not surprisingly, the virus emerges with another file extension, this time – .coded. Traditionally, after changing the file extension used, the malware creator changes the contact email address as well. This CODED GlobeImposter version uses [email protected] and [email protected] email accounts for communication with ransomware victims.
.astra file extension virus. Clearly enough, there are no exceptional features in this virus. It simply uses different file extensions to mark encrypted records, therefore it sometimes is called Astra ransomware virus. To provide the victim with data recovery guidance, it creates and saves a message in here_your_files!.html file (known as the ransom note). No decryption tools are available at the moment of writing. The only way to restore files is to rely on a data backup.
.f41o1 file extension after completing the encryption process. What is more, this version also presents a graphic user interface – READ_IT.html.[8] It does not indicate a specific email address but instead provides a specific .onion address for victims to proceed with data recovery. The perpetrators also offer to purchase their Decrypter. Victims are supposed to receive further instructions within 48 hours. Let us remind you once again that even if the software will decrypt the files, it may system with spyware which might facilitate future hijack.
Interestingly, GlobeImposter developers are shifting to boost malware distribution via malspam. One of the samples function via the VBS script and hide under INV-000913.vbs or similarly named fake invoice file. Another virus edition fishes users via corrupted hosts, such as errorkpoalsf.top/(…). Furthermore, developers also added Nemucod trojan to the distribution campaign.
Decoder ransomware virus. Hackers inform that the files were encrypted due to the “Security problems” detected on the PC. They indicate [email protected] and [email protected] email addresses to pay and ransom and receive a decryptor for .decoder files. The ransom note is named as Instructions.txt and dropped on the desktop shortly after Decoder ransomware infiltration.
ABC ransomware virus. While developing this variant of the Globe Imposter virus crooks employed AES and RSA ciphers to perform data encryption. Afterward, it leaves Read_IT.txt which serves as a ransom note. You should note this version is still under development. Thus, it might drop README.txt or HOW_TO_DECRYPT.txt files.
According to the research, ABC virus spreads via exploit kits, spam emails or other common distribution techniques. Victims report that they are demanded to pay from 0.3 to 0.5 BTC in return to data recovery.
.Ipcrestore file extension virus. The victims are provided with how_to_back_files.html file which has a common name of a ransom note. They are asked to make a digital currency transaction in a specific Bitcoin account to get a decryption tool for files with .Ipcrestore extension. While this offspring of FakeGlobe is still in development, the PC users are advised to take precautionary measures and be aware of all possible extensions and ransom note names.
.suddentax file extension virus. The latest GlobeImposter ransomware variant appends .suddentax file extension to all locked files and demands to pay 2 Bitcoins for a decryptor. The victim is asked to contact extortionists as soon as possible via [email protected] or [email protected] emails and send them a screenshot of the payment. According to cybersecurity experts, this version targets business networks. It’s not clear yet if the ransomware is decryptable. However, it seems that it is capable of evading detection by many AV engines. According to VirusTotal,[9] only 31 out of 67 AV engines are capable of recognizing and immunizing it.
Update May 23, 2017. The ransomware keeps changing its attack techniques and according to the latest reports, this malicious virus is being pushed by Blank Slate malspam which was and is responsible for Cerber’s distribution[10].
It turns out that malicious files came packed in .zip archives named with a random set of chars, for instance, 8064355.zip. When unpacked and executed, the .js or .jse file inside connects to a certain domain and downloads ransomware from it.
Criminals tend to regularly switch the domains that host ransomware, but currently known domains are newfornz[.]top, pichdollard[.]top and 37kddsserrt[.]pw.
Update August 1, 2017: New Globe Imposter malspam campaign (most likely based on the Necurs botnet) with new subject names have been spotted. Below you will find a list of email addresses, subject titles and attachment files associated with Fake Globe distribution:
- [email protected] — Payment Receipt_72537 — P72537.zip
- [email protected] — Payment 0451 — P0451.zip
- [email protected] — Payment Receipt#039 — P039.zip
- [email protected] — Receipt 78522 — P78522.zip
- [email protected] — Receipt#6011 — P6011.zip
- [email protected] — Payment-59559 — P59559.zip
- [email protected] — Receipt-70724 — P70724.zip
- [email protected] — Receipt#374 — P374.zip
- [email protected] — Payment Receipt#03836 — P03836.zip
- [email protected] — Payment_1479 — P1479.zip
According to malware-traffic-analysis.net website which compiled this list, the zip files contain vbs files which carry the malicious payload.
Besides, new subject titles have been added to the spam campaign distributing FakeGlobe as .js file. Be careful with emails that read “Voice Message Attached, or “Scanned Image”.
Update August 14, 2017. Different GlobeImposter ransomware versions emerge and disappear rapidly. In less than a week (starting from August 8th) malware developers introduced new ransomware versions that append either ..txt, .BONUM, .trump, .rumblegoodboy, .0402, .JEEP, .GRAFF, .MIXI or .ACTUM file extensions to encrypted files. As always, no outstanding improvements or updates come with these versions.
Some of the versions call the ransom note differently – for example, the 0402 virus uses !SOS!.html and the ..txt file extension virus uses Read_ME.html name for the note. So far, no decryption tools for these versions were discovered.
Update September 15, 2017. As usual, every month introduces a couple of new GlobeImposter variations. Most recent are: .YAYA .needkeys, .[[email protected]], .foSTE, .490, .ILLNEST, .SKUNK, .nWcrypt. Though appended extensions differ, there are no crucial modifications of the malware.
The developers continue the theme of US presidents as well. One of the recent editions mark encrypted files with .reaGAN extension and present [email protected] email address for contact purposes. Additionally, another version does not only add a different extension – .911 – but also displays the demands in the !SOS!.html page.
Luckily, the current versions are detectable as Ransom:Win32/Ergop.A, Trojan.Purgen.ba, Generic.Ransom.GlobeImposter.56A888, etc. However, perpetrators act more insidiously. These versions disguise under cmd.exe (a referrer to Command Prompt executable), btm1.exe, encv.exe, and similar executables which are used by legitimate apps. After the infection, the malware launches additional commands: ADVAPI32.dll, KERNEL32.dll,SHLWAPI.dll,USER32.dll, and ole32.dll.
Update September 20th, 2017. At the beginning of autumn 2017, GlobeImposter was noticed proliferating via massive ransomware campaign that was mostly associated with the infamous Locky ransomware. Experts from TrendMicro have specified that the malicious domains used to download the ransomware on victim’s computers serve FakeGlobe and Locky ransomware in a rotation. Therefore, it means that the compromised domain can serve Globe Imposter for several hours and then switch to pushing Locky and vice versa.
Spam campaigns delivering the malware to victims are providing malicious links in the message body, suggesting to view an invoice online. Clicking on the link downloaded a .7z file which was also attached to the email. The file inside the archive is set to connect to remote domains and download Locky or GlobeImposter virus.
According to NoVirus.uk experts[11], this isn’t the only type of malicious emails that scammers are using to push ransomware. They are also sending thousands of emails without any information in the message body and an attached .doc file instead of an archive. The doc file contains a macros code set to download the ransomware from a remote server. As soon as the victim closes the file, the script will activate itself via Auto Close VBA Macro.
Update November 17, 2017. A month has passed – new versions GlobeImposter virus sprung to life. Finally, the developers decided to introduce more changes rather than simply altering the name of appended extensions and email addresses.
Now they slightly changed the encryption way of the configuration. Now the encryption key is more complex. It was done supposedly to bother the decryption tool creation process. The authors also changed the ransom note – now the demands are delivered in #HOW_DECRYPT_ALL#.html[12].
Except for these slight modifications, no other significant changes are visible. Globe Imposter crypto-malware continue amusing themselves and IT experts with random file extensions. While some of the older file extensions are used, there are new ones.
One of them, .kimchenyn, mockingly relates to the leader of North Korea Kim Jong-un. Another extension, .panda, possibly refers to the latest version of Zeus Panda banking trojan appeared. Another Globe Imposter version refers to popular Hollywood actor – Colin Farrel – as it appends [email protected] extension.
The most recent versions of file-encrypting virus
Not all versions of Globe Imposter are decryptable.

Not all versions of Globe Imposter are decryptable.
.DREAM file extension virus. Currently, experts have detected a new offspring of GlobeImposter ransomware which uses .DREAM extension after encrypting the information. Malware researchers still cannot tell whether it is possible to recover encoded files. Thus, victims are advised to try all alternative recovery methods for the best results.
Note that the criminals try to intimidate the owners of victimized computers and insist on contacting them via [email protected] and [email protected] email addresses which are provided in the ransom note — how_to_back_files.html.
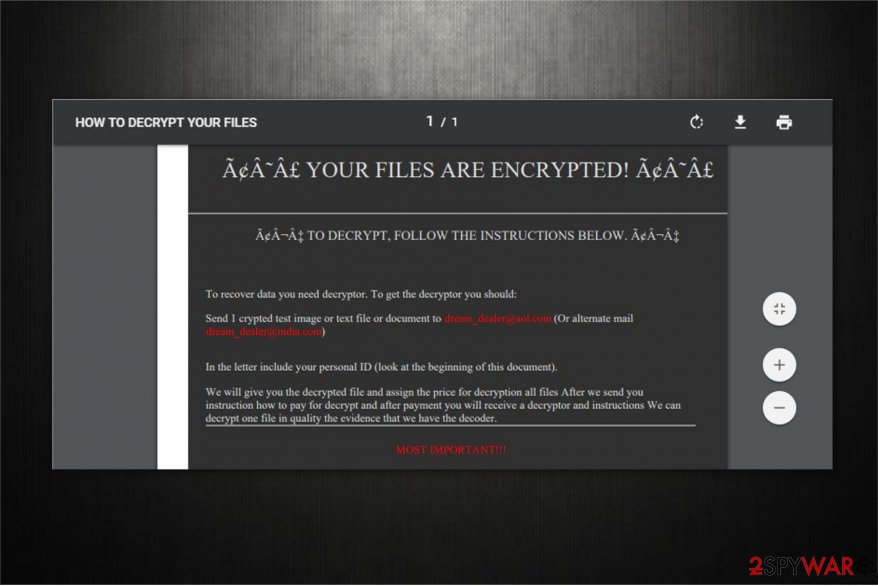
The fraction of the ransom-demanding message:
YOUR FILES ARE ENCRYPTED!
TO DECRYPT, FOLLOW THE INSTRUCTIONS BELOWTo recover data you need decryptor. To get the decryptor you should:
Send 1 crypted test image or text file or documents to [email protected] (Or alternate mail [email protected])
In the letter include your personal ID (look at the beginning of document).We will give you the decrypted file and assign the price for decryption all files. After we send you instruction how to pay for decrypt and after payment you will receive a decryptor and instructions. We can decrypt one file in quality the evidence that we have the decoder.
However, like in any other ransomware attack, we encourage you to get rid of the new version of GlobeImposter and NEVER agree on paying the ransom. There is a high-risk that the criminals will leave you empty handed after the transaction or demand even more money. For that reason, check the elimination guide below.
.GRANNY file extension virus was first discovered in August, 2017. Users get infected via malicious torrent files which hold the Trojan inside. Unlike some of the latest GlobeImposter variations, the malware presents its independent interface. Victims are instructed to contact the perpetrators via [email protected] or [email protected]. The cyber criminals offer decryption of one file to earn users’ trust.
.Trump file extension virus is another worth mentioning recently appeared sample. The malware launches a quite plain interface with an unusually long victim’s identification address. Additionally, the crooks offer users to contact them via [email protected] and [email protected]. As in previous cases, the felons did not indicate the specific amount of money but instead encourage users to contact them directly.
{[email protected]}.BRT92 file extension virus strikes again with slight modification in its email domains. Perpetrators now deliver the demands in #DECRYPT_FILES#.html file. As in other variants, the racketeers urge to purchase their decoder and offer one file decryption service for free.
Though the very extension has been exploited before, now crooks switched to [email protected] address.[13] The tendency to take inspiration from fiction, pop culture or just random daily life implies that the crooks might not be an organized gang of cyber villains. However, the rate of new malware variations certainly suggests their persistence.
Other August GlobeImposter editions include variants which append .D2550A49BF52DFC23F2C013C5, .zuzya, .LEGO, .UNLIS file extensions. No significant changes in the operation peculiarities nor in the distribution methods are detected.
With the beginning of academic year, GlobeImposter malware developers bombard users again with a series of new samples. The cyber criminals do not seem to lose a sense of humor as well. One of the variations appends .clinTON file extension and indicates [email protected] for contact purposes.
On the 18th of October, 2017, the Rig exploit kit (RIGEK) was spotted spreading Globe Imposter version via hacked websites. that appends .4035 file extension. Following data encryption, it delivers a ransom note in READ_IT.html file were victims are asked to pay the ransom in order to get back access to their files.
Later researchers detected another version of ransomware appending .doc file extensions to the targeted files. The malicious program locks data with strong encryption cipher and provides ransom note in Read___ME.html file. This version of malware spreads via two malspam campaigns that are pushed by Necurs botnet. Malware asks to pay $1000 in two days; otherwise, the payment will double.
At the end of October, the new version of the GlobeImposter has been noticed appending .apk file extension. Malware payload spreads as an apkcrypt.exe file. As soon as this file is executed on the system, the virus starts data encryption procedure. Following successful encryption, it delivers a ransom note in Note Filename: support.html file where victims are asked to transfer Bitcoins for data recovery.
On 9th of March 2018, security expert Michael Gillespie noted,[14] that the newest version of GlobeImposter crypto-virus is using .Nutella extension. Just as its predecessors, this type of the virus encrypts all personal files and demands the ransom to be paid for data release.
Let us remind you that free GlobeImposter Decrypter might help you decode the files if this cyber misfortune seized control of your files.
.gif file extension virus. Yet another variant of the infamous Globe Imposter ransomware has been detected at the end of March 2018. Cybersecurity experts spotted a new way of spam emails spreading via Necurs botnet.
Once the payload is executed, the ransomware targets the most popular file types and appends .gif file extension to each of them. Upon successful application of AES cipher, the ransomware creates a Read_ME.txt file on the desktop. The ransom note contains the following information:
Your files are Encrypted!
For data recovery needs decryptor.
How to buy decryptor:
1. Download “Tor Browser” from hxxps://www.torproject.org/ and install it.
2. Open this link In the “Tor Browser”
hxxp://djfl3vltmo36vure.onion/sdlskglkehhr
Note! This link is available via “Tor Browser” only.
Your Personal ID:
Additionally, the .gif file extension virus generates a GIF window on the web browser, which instructs the victim on how to make the payment. At the moment of writing, the sum of the ransom demanded by Globe Imposter .gif version is 0.094 Bitcoin, which is approximately $1000 USD. The GIF page contains a countdown clock, which will end in 48 hours. After that, the ransomware is supposed to duplicate the sum of the ransom.
Do not pay the ransom. Although the virus tries to intimidate victims claiming that all encrypted data will be deleted if he or she downloads a third-party data recovery tool, do not fall for believing that. You should immediately download Reimage Reimage Cleaner Intego or another powerful security tool and then try to retrieve locked data with the help of free GlobeImposter decrypter or third-party data recovery software.
We would not recommend paying the money for cybercriminals. Although they claim to recover one file for free before you pay the ransom, that does not guarantee that a Globe Imposter decryptor will be able to retrieve all your data. Instead, you should remove .gif file extension ransomware and try alternative data recovery methods. You can find a tutorial down below.
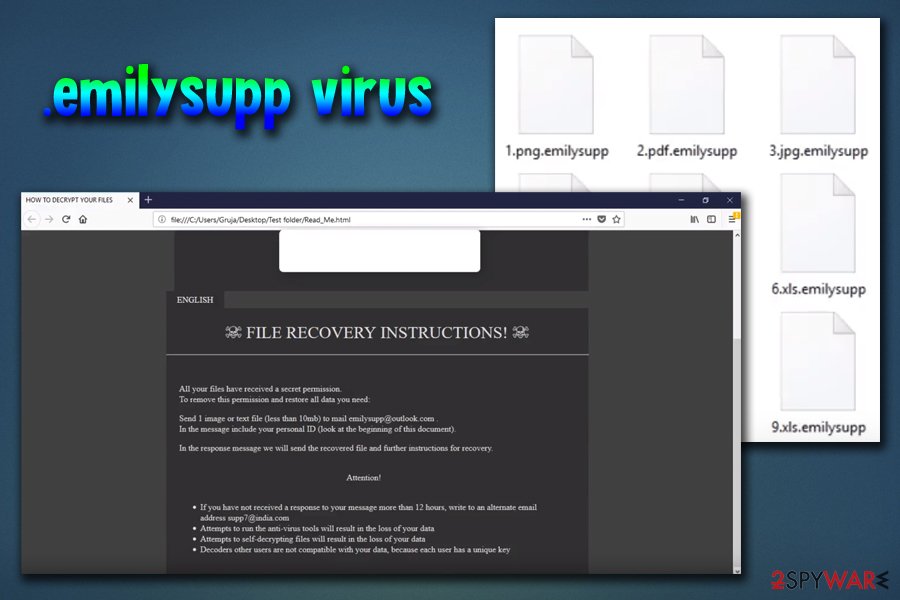
.emilysupp file extension virus. This version of GlobeImposter was spotted by security experts[15] in early June 2018. The malware appends .exilysupp file extension. As usual, hackers made sure the target knows what happened to his or her files, and dropped ransom note (which is written in a .html format) in each of the affected folders.
I the note, victims are informed that their personal files just have been encrypted and are prompted to contact cybercriminals via [email protected], or via [email protected] if no answer is received within 12 hours after the attack. Hackers also urge users to attach an encrypted file, so that they can make sure that the decoding is possible.
Additionally, victims are warned not to use any anti-malware tools as it will result in loss of the data, as well as decryption keys sent to other users will not work. Unfortunately, this variant of Globe Imposter is not decryptable. Nevertheless, we advise users to stick to security software and ignore hackers. Merely remove the .emilysupp virus using Reimage Reimage Cleaner Intego or SpyHunter 5Combo Cleaner and then recover your data from a back-up. If you do not have one – try third-party software that may be able to recover at least some of your files.
The latest version of Globe Imposter malware is not decryptable. Nevertheless, we urge users not to contact cybercrooks and restore data from backups.

The latest version of Globe Imposter malware is not decryptable. Nevertheless, we urge users not to contact cybercrooks and restore data from backups.
Since May 2018 the virus has been idle. However, it has revived in spring 2020 with a new variant dubbed C4H. The malware appends the .C4H file extension, which prevents people from accessing personal data stored on the D: drive. For the file encryption process, it uses AES and RSA ciphers.
The ransom note named as Decryption INFO.html shows up in the victim’s PC screen upon the phase of encryption and instruct to establish contact via [email protected] or [email protected] email addresses. The size of the redemption demanded is currently unknown.
Crooks strictly prohibits the usage of AV engines for C4H removal, as well as the usage of third-party data recovery tools because of a permanent data loss. Nevertheless, paying the ransom is not recommended due to various risks of disclosing any personal details to criminals.

C4H is the latest variant of the GlobeImposter ransomware virus. It emerged in spring 2020

C4H is the latest variant of the GlobeImposter ransomware virus. It emerged in spring 2020
Experts recommend people to remove .C4H file extension virus immediately by rebooting the system into Safe Mode and running a scan with a professional AV engine. After that, you may give a try for Emsisoft’s decryption software or other third-party data recovery tools for returning your files and documents.
Hackers try out various ways to distribute the virus payload
Since Globe Imposter is not a new threat to the cyber community, its developers have tried more than one distribution method to spread this file-encrypting virus. Employing different techniques allows criminals to make sure that it will take time for security experts to detect the new source of the ransomware and inform people about the threat.
GlobeImposter virus has already used Rig exploit kit to detect system vulnerabilities and infiltrate computers easier. Additionally, malware researchers have detected malicious ads that automatically install the ransomware once clicked and there have been several cases when the malware has entered the targeted system via drive-by downloads[16].
Another recently discovered way how GlobeImposter reaches its victims is malspam campaigns pushed via Necurs botnet. Hackers employed deceptive email letters to trick users into opening them and activating bogus scripts that infiltrate the ransomware.
Therefore, be aware that this malicious program might take advantage of outdated software and security vulnerabilities. However, most of the time crooks want to trick users into the opening or downloading infected content, such as ads or email attachments. For this reason, you should be careful and click content only if you are 100% sure that it’s safe.
To protect the system from malware attacks, a decent and up-to-date anti-malware software is required, besides, we recommend finding some external storage to keep copies of your files in. You may use thumb drives, external HDDs or any other device you prefer. Just don’t forget to keep it unplugged from your computer!
Delete Globe Imposter ransomware using reputable security software
Ransomware-type infections are more complex than those related to browser hijacking or displaying ads on your frequently visited websites. It is because file-encrypting viruses have the ability to infiltrate other dangerous programs which might complicate the elimination procedure even more. For this reason, we suggest only automatic GlobeImposter removal.
Reimage Reimage Cleaner Intego, SpyHunter 5Combo Cleaner, and Malwarebytes will remove GlobeImposter and other related malicious software for you. Just download the antivirus from official websites and let it scan your computer system thoroughly. Shortly after, you should be able to use ransomware-free computer again.
Also, in case you cannot get rid of Globe Imposter, you might need to boot your computer into Safe Mode first. Check the instructions below to learn how to terminate the ransomware safely. However, we kindly ask you to follow the attentively to succeed in the elimination.
This entry was posted on 2020-05-14 at 23:24 and is filed under Ransomware, Viruses.

