DecYourData ransomware – a file locking virus that asks users to contact hackers for a chance of restoring personal data
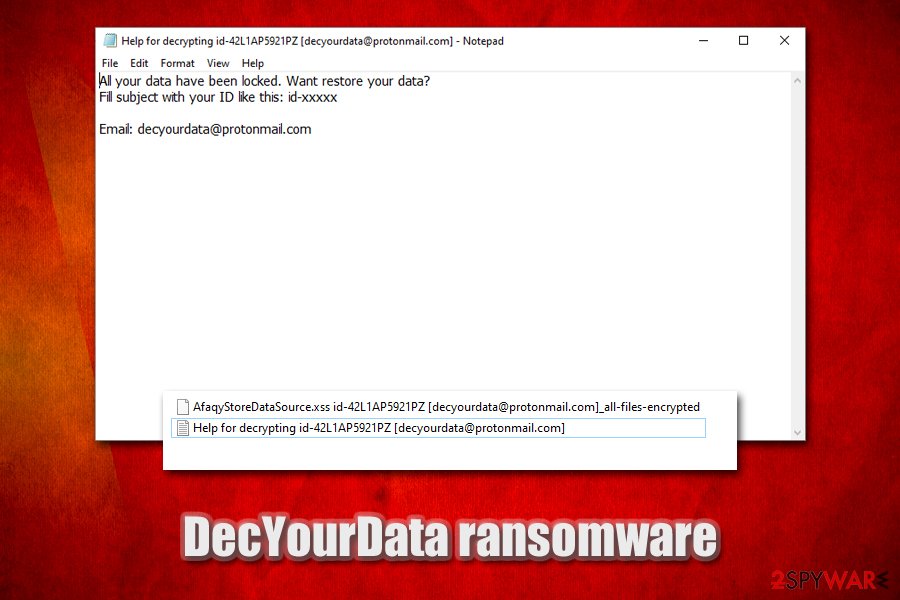
DecYourData ransomware is a file locking virus that encrypts all personal files with AES and then demands ransom in Bitcoin for their redemption

DecYourData ransomware is a file locking virus that encrypts all personal files with AES and then demands ransom in Bitcoin for their redemption
DecYourData ransomware is a crypto-malware that was first spotted in December 2019, with a new variant appearing a month later.[1] Just as many other similar viruses of such type, it relies on file encryption process (which is performed with the help of AES[2] cipher) to hold all personal files like pictures, documents, databases, videos, PDF, and others, hostage, and demand ransom payment in Bitcoin cryptocurrency for DecYourData ransomware decryption software.
Once the DecYourData virus infection is triggered, it will scan the machine for encryptable files and provide a unique ID for each victim, which will later be used for identification, payment, and decryption process. To make sure that users know how to proceed next, malicious actors drop a ransom note “Help for decrypting id-victim ID [contact email].txt, which emails that users have to contact them via [email protected], although later version used [email protected] and [email protected] emails. The encrypted data is marked per the following template: id-victim ID [contact email]_all-files-encrypted. Currently, the only safe way to recover DecYourData ransomware encrypted files is by using backups, although using a few alternative methods might sometimes prove successful.
| Name | DecYourData ransomware |
| Type | File locking virus, cryptomalware |
| Encryption algorithm | All files are locked with the help of a symmetric AES encryption algorithm |
| Extension | There is no dot after the full name of the file – instead, the malware uses a space. Each of the encrypted files is appended with a particular template that consists of victim’s ID and contact email; an example of an encrypted file: AfaqyStoreDataSource.xss id-42L1AP5921PZ [[email protected]]_all-files-encrypted |
| Ransom note | A template for the ransom note is also used, and includes victim’s ID and email address, for example: Help for decrypting id-42L1AP5921PZ [[email protected]].txt |
| Contact | [email protected], [email protected] and [email protected] |
| Ransom size | Some victims were asked to pay $5,000 in Bitcoin to recover all encrypted data |
| Associated crypto-wallet | 1RTvJ9ygzWm74g1WuNcLuQMHXiMtL5hP1 |
| Data decryption | The only safe way to retrieve files is by using backups, although using third-party recovery software might be helpful for some victims |
| Malware removal | To get rid of ransomware infection, scan your computer with reputable anti-malware software (for example, SpyHunter 5Combo Cleaner or Malwarebytes) in Safe Mode with Networking |
| System fix | Malware can cause significant damage to Windows system files. To fix virus damage and restore the registry, use Reimage Reimage Cleaner repair tool |
Due to relatively low prevalence of DecYourData ransomware, pinpointing its exact distribution techniques can be difficult. Nevertheless, most of file locking malware is delivered via the following methods:
- Malicious spam email attachments or hyperlinks;
- Pirated software installers or software cracks/loaders/keygens;
- Poorly protected Remote Desktop (RDP) connections;
- Exploit kits and software vulnerabilities;[3]
- Fake updates and other executables presented on phishing sites.
As soon as the DecYourData virus breaks into a computer (it can attack all Windows versions, including the latest Windows 10), it populates various files into %TEMP%, %Users%, and other folders, one of which is typically a main executable of the malware. This file is generally used to examine particular ransomware behavior by automated sandbox tests.
Once launched, DecYourData proceeds with various system modifications, such as deletion of Shadow Volume Copies (prevents data recovery from automated backups), modification of Windows registry database (increases persistence), termination of various recovery features, etc. Due to these changes, DecYourData ransomware removal might sometimes not be successful in the normal environment, which is why experts[4] suggest users accessing Safe Mode and only then perform a full system scan with powerful security software.
Once the preparations are complete, DecYourData ransomware proceeds with file encryption process witch appends a lengthy extension to most commonly used file types, such as .doc, .pdf, .mp4, .jpg, .dat, .mdb, .ini, etc. As a result, victims can no longer access their data, and they see a blank icon instead of an original one. Unlike most of the other ransomware, the DecYourData virus does not use the dot, which is followed by a predetermined file extension but instead replaces it with space.
After that, a brief ransom note is presented to the infected users, which states:
All your data have been locked. Want restore your data?
Fill subject with your ID like this: id-xxxxx
Email: [email protected]
Most experts recommend avoiding contact with DecYourData, as well as other ransomware authors, as there is no guarantee that they will provide a decryption tool. However, because the decryptor is unique to each victim, there is little chance of recovering data without paying criminals or negating ransomware devastating effects by using backups.
DecYourData ransomware is a type of virus that specializes in money extortion

DecYourData ransomware is a type of virus that specializes in money extortion
If your files are encrypted by DecYourData, and you have no backups available, you should consider what is best for you. We highly recommend avoiding paying the ransom, although it might be the only choice in some cases (you should realize that you might also lose your money, however). Some victims who contacted cybercriminals claimed that they were asked to pay as much as $5,000 in BTC for decryption software.
Instead, you should copy encrypted files to an external or a virtual drive, remove DecYourData ransomware with anti-malware software, fix your Windows with Reimage Reimage Cleaner or similar repair software, and then attempt data restoration via methods provided in our recovery section below.
Data-encrypting malware can be spread via various different methods
As already stated before, there are a variety of methods that cybercriminals behind ransomware viruses can use, including exploits, fake updates, spam emails, weakly protected RDP connections, etc. Some of these methods are relatively primitive, while others are far more sophisticated and complicated, and because no anti-malware software can catch 100% of the incoming computer threats, having a security program installed is not enough to protect yourself.
One of the most prominent ransomware and other malware distribution method is spam emails, where crooks clip malicious attachments or insert hyperlinks. As a general rule, malspam campaigns use popular brand names, such as Amazon, UPS, etc., although random short email messages are common too. With the help of email spoofing[5] and good social engineering skills, criminals convince users to open attachments embedded with malicious macros or click on hyperlinks that would connect to a remote server and deliver the malicious ransomware payload. Thus, please do not casually open email attachments or click on links inside, unless you are sure that the email is real.
Additional protection measure tips include:
- Use strong passwords for all your accounts;
- Apply security updates for all your installed applications and the OS immediately;
- Never download pirated software installers or cracks;
- Employ additional tools for protection, such as ad-block and Firewall;
- Do not use the default TCP port for RDP and disconnect as soon as you are done using the feature;
- Backup your files regularly.
Data recovery options and DecYourData ransomware removal method
Getting infected with ransomware is a tough situation to be in, as DecYourData ransomware removal would not restore all the encrypted files, despite the popular belief. It is important to realize that, once files are encrypted, only a specialized decryption tool that is stored in the reach of hackers or, in some cases, third-party software might be able to work.
Note that security researchers are also constantly working on finding bugs within the encryption process of ransomware viruses, which already resulted in successful decryptor release for multiple malware families or its versions, including BigBobRoss, Djvu, Cerber, Paradise, and many others. You can find many of such tools on the No More Ransom Project page. Thus, while there is no guarantee, it is possible that decryption software will be created for the DecYourData virus as well.
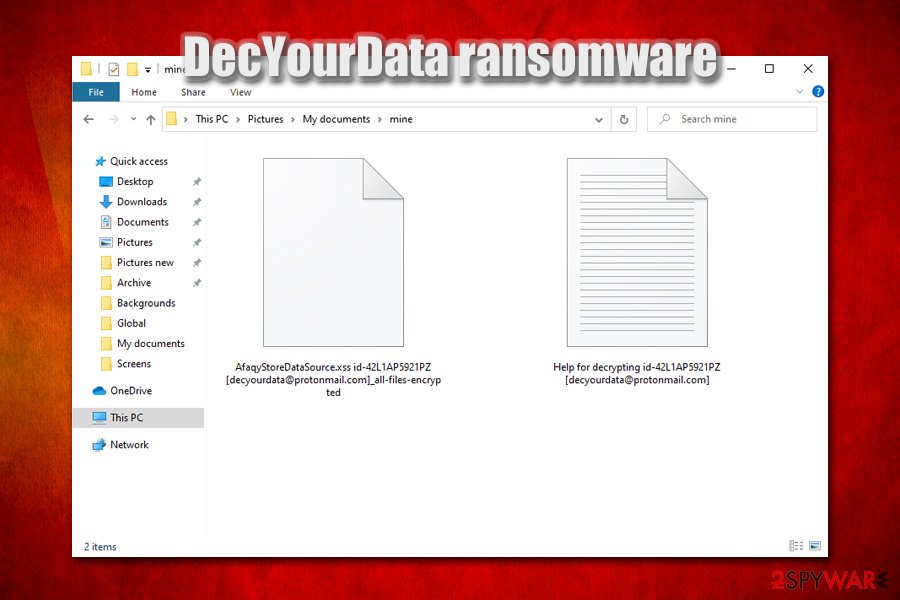
Once DecYourData ransomware encrypts files, icons become blank, and accessing them becomes impossible

Once DecYourData ransomware encrypts files, icons become blank, and accessing them becomes impossible
If you had no backups, you should safely copy the encrypted files over (otherwise, the files might get permanently damaged, and even a working decryptor will not be successful in its recovery), remove DecYourData ransomware by following the instructions below, and then use third-party software tools to attempt file recovery.
This entry was posted on 2020-02-05 at 07:14 and is filed under Ransomware, Viruses.

