CryptoPatronum ransomware – a file-encrypting parasite that requires a ransom equal to 1 Bitcoin or 50 Ethereums in exchange for file release
CryptoPatronum ransomware is a dangerous cyber infection that urges for 1 BTC or 50 Ethereum as the payment for the decryption key
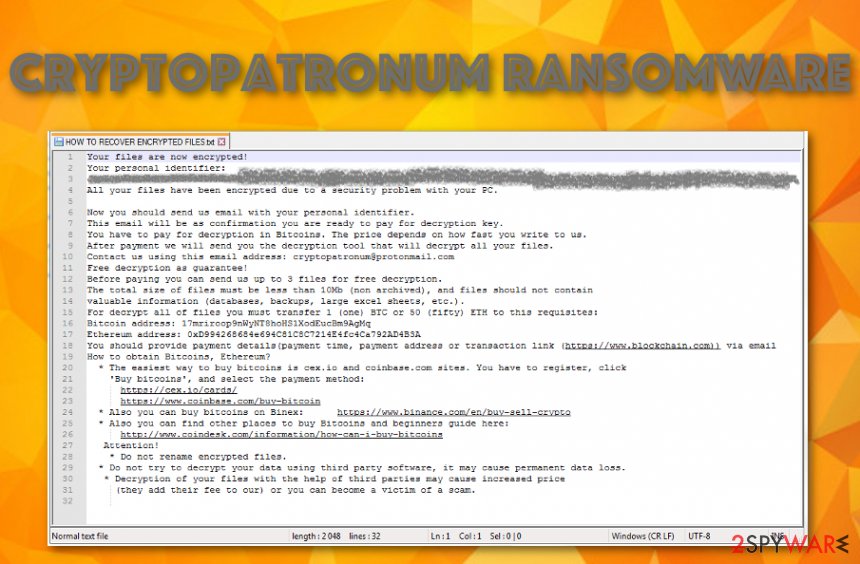
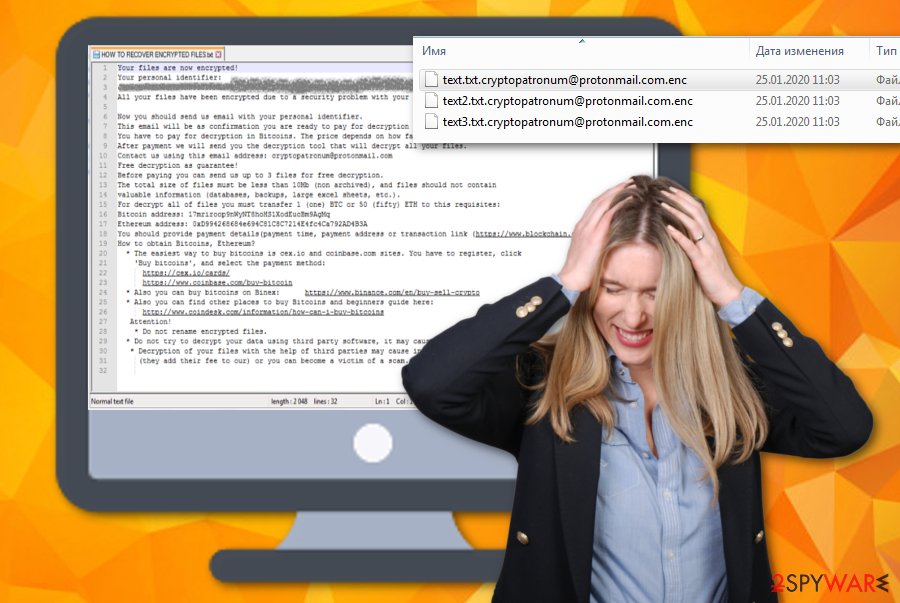
CryptoPatronum ransomware, also known as Enc ransomware, is a cryptocurrency-urging cyber infection that has emerged in the second half of January 2020. This malicious strain is recognized from the [email protected] email address and .enc extension that it appends to the encrypted files that are modified by the AES-256 cipher.[1] For example, if you had a document named lists.docx, the file will be renamed to [email protected] and you will not be able to access it properly anymore. Regarding this fact, the CryptoPatronum ransomware developers want to “help” people to get their files and documents back by providing specific ransom demands via HOW TO RECOVER ENCRYPTED FILES.txt text message.
The criminals are orientated in earning 1 Bitcoin that is around $9000 or 50 Ethereum that is approximately $8500. CryptoPatronum ransomware provides information on how to obtain Bitcoins or Ethereum directly in the ransom note by adding certain website URLs. The hackers also include the Bitcoin and Ethereum wallet addresses where the demanded price needs to be transferred. Furthermore, these people offer to provide evidence of the decryption tool’s existence by encouraging the victims to send them 3 files that hold no more total size than 10 MB for free recovery.
| Name | CryptoPatronum ransomware |
|---|---|
| Also known as | Enc ransomware |
| Category | Ransomware/malware |
| Encryption | This malicious parasite locks all types of files and documents by employing the AES-256 cipher. All the affected components end up with the [email protected] appendix |
| Ransom note | The malicious actors provide the HOW TO RECOVER ENCRYPTED FILES.txt message after locking all files. This note holds all the conditions required for the ransom transfer |
| Payment | The hackers appear to be very greedy, they urge for a payment of 1 Bitcoin that approximately equals $9000 or 50 Ethereum that is around $8500 |
| Distribution | Criminals use stealth distribution techniques to spread their created malware. Most of the time, ransomware is delivered via email spam and malicious attachments that come together with the phishing message. Furthermore, you can receive the dangerous infection through a hacked RDP, cracked software that is placed on p2p networks, malvertising ads, infectious hyperlinks, fake software updates, etc. |
| Removal | Once you spot the ransomware virus on your Windows computer system, you should take action against the parasite immediately. This includes fast termination by employing a reliable antimalware product. We recommend not trying to get rid of the cyber threat on your own in order to avoid possible mistakes |
| Data recovery | If you are looking for ways to restore your files and documents, you can try some of the techniques that are described at the end of this article. You should be aware that the cybercriminals are focused on their goal only and they might not provide you with a decryption tool after the payment is processed |
| Fix software | If the ransomware virus or any additional malware has damaged some system components, you can try fixing the compromised areas with a repair tool such as Reimage Reimage Cleaner |
CryptoPatronum ransomware alters the Windows Registry to include malicious registry keys that allow the virus to boot itself up during the computer activation process, scan the system for encryptable files, launch the encryption code, and run other background processes. Besides messing with the Registry, the cyber threat also injects malicious processes into the Windows Task Manager section one of which is named crss.exe.
Even though CryptoPatronum ransomware might aim to evade antivirus detection, this malicious threat has been spotted by 52 antimalware programs out of the total 69, according to VirusTotal provided data.[2] However, if the virtual parasite aims to block your antivirus product, you might have difficulties while dealing with the CryptoPatronum ransomware removal process. In this case, you have to boot your computer in Safe Mode with Networking or activate the System Restore feature.
CryptoPatronum ransomware is a virtual parasite that adds malicious processes to the Windows Task Manager and includes hazardous keys to the Registry section
Furthermore, CryptoPatronum ransomware might try to harden the recovery process of locked data files as much as possible. It might run the “vssadmin.exe delete shadows /all /Quiet” command via PowerShell and permanently terminate all the Shadow Volume Copies of encrypted files. Also, it might be able to damage the Windows hosts file in order to prevent you from accessing security-related sources where you could get valuable information on file recovery.
After the decryption process, the cybercriminals store both encryption and decryption keys on remote servers that are reachable only for the owners themselves. This type of thing also hardens the recovery process for the user. However, you should not let CryptoPatronum ransomware frighten you even though the hackers will try to convince you that the only way of restoring your data is by paying the ransom and other tools would not work:
Your files are now encrypted!
Your personal identifier:
–
All your files have been encrypted due to a security problem with your PC.
Now you should send us email with your personal identifier.
This email will be as confirmation you are ready to pay for decryption key.
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
Contact us using this email address: [email protected]
Free decryption as guarantee!
Before paying you can send us up to 3 files for free decryption.
The total size of files must be less than 10Mb (non archived), and files should not contain
valuable information (databases, backups, large excel sheets, etc.).
For decrypt all of files you must transfer 1 (one) BTC or 50 (fifty) ETH to this requisites:
Bitcoin address: 17mriroop9nWyNT8hoHS1XodEucBm9AgMq
Ethereum address: 0xD994268684e694C81C8C7214E4fc4Ca792AD4B3A
You should provide payment details(payment time, payment address or transaction link (hxxps://www.blockchain.com)) via email
How to obtain Bitcoins, Ethereum?
* The easiest way to buy bitcoins is cex.io and coinbase.com sites. You have to register, click
‘Buy bitcoins’, and select the payment method:
hxxps://cex.io/cards/
hxxps://www.coinbase.com/buy-bitcoin
* Also you can buy bitcoins on Binex: hxxps://www.binance.com/en/buy-sell-crypto
* Also you can find other places to buy Bitcoins and beginners guide here:
hxxp://www.coindesk.com/information/how-can-i-buy-bitcoins
Attention!
* Do not rename encrypted files.
* Do not try to decrypt your data using third party software, it may cause permanent data loss.
* Decryption of your files with the help of third parties may cause increased price
(they add their fee to our) or you can become a victim of a scam.
Even though CryptoPatronum virus is likely to have the decryption key for your files, paying the ransom price cannot make you 100% sure that you will receive the tool after all. The cyber crooks could decide to scam you and run off with your money. This way you will be left with nothing else just an empty bank account as paying the demanded 1 BTC or 50 Ethereum ransom is a big amount of money to spend.
The main reason why CryptoPatronum ransomware orders cryptocurrency payments instead of regular dollar transfers is that Bitcoin or Ethereum payments do not require entering any personally identifiable information that the cybercriminals find very beneficial as they can stay untracked and anonymous all of the time.
CryptoPatronum ransomware can be really frightening not only with its ability to encrypt data and big ransom payments but also with the possibility that it might bring other malicious infections into the computer system. Some ransomware viruses can bring others of their kind or can distribute Trojan viruses. The last ones are known for their ability to steal personal information, swindle money, damage software, mine cryptocurrency, and so on.
The only way to avoid risks of getting an additional malware infection is to remove CryptoPatronum ransomware from your Windows computer system permanently. This type of process can be successfully performed with a reliable virus removal tool. Afterward, go to the end of the article and view all possible data recovery solutions. By the way, if the malware has caused any type of damage to your computer, you can try repairing the altered areas with the help of software such as Reimage Reimage Cleaner .
The most popular distribution ways of ransomware viruses
IT specialists from NoVirus.uk[3] claim that ransomware infections are most commonly spread through email spam campaigns. The criminals often pretend to be from reputable organizations such as FedEx or DHL shipping companies and drop fake notes to random potential victims. These messages often come with an executable or word document that is the hidden malicious payload. Sometimes the hackers can include an infected link directly into the email.
Continuously, the ransomware-related payload can be delivered through multiple sources at a time. Even though email spam is considered to be the most common way employed by the crooks, these people also use other methods such as:
- Injecting the malicious payload into software cracks. You can get cracked products from p2p networks such as The Pirate Bay, eMule, and BitTorrent.
- Hacking RDPs. RDP that includes weak password protection or none at all is at risk of getting hacked by various cybercriminals.
- Malvertising. Ransomware virus can get delivered through malicious advertisements that show up on third-party websites.
- Fake software updates. Some hackers camouflage their products as fake flash player or JS updates and encourage users to falsely upgrade their software. During the false update process, the malicious payload is loaded.
Learn how to protect your device and files from ransomware
Once you have gained a little bit of knowledge in the ransomware distribution field, you can now start learning how to protect your device and files from these dangerous parasites. First of all, make sure that you have got strong antivirus protection. Update this type of tool whenever you are required to do it. It is necessary for proper operating.
Continuously, you should be careful with random email messages that fall into your email box. Avoid opening any letters that come to the spam section and better delete them immediately. If you have received a message that you were not ever expecting to get, do not feel afraid to contact the company that supposedly sent the letter. Also, check the text for possible grammar mistakes that should not be found in an official letter, do not open any attachments that you are not sure about.
Another piece of advice would be to prevent yourself from visiting unsecured p2p networks[4] and other websites that can hold infectious hyperlinks or advertisements. If you are ever provided with a bogus update request, do not rush to upgrade your software before checking the official update releases at the developer’s website. Also, proper RDP configuration should include a strong and reliable password that consists of random letters, numbers, and symbols.
Your files can be protected by always creating backups for important data. These types of components should be saved on a remote device such as a USB flash drive, CD, or DVD. Also, you can store some information on a remote server such as iCloud or Dropbox.
Advanced removal possibilities for CryptoPatronum ransomware
CryptoPatronum ransomware removal should be taken care of as soon as you spot the first symptoms of infection that usually include encrypted files and the specific ransom note. Be aware that you should not try to delete the malware on your own as this type of process can be too difficult for even a highly-experienced user.
You should employ only reliable antivirus tools to remove CryptoPatronum ransomware from your Windows computer system. Furthermore, if you think that your system is suffering from some type of damage, you can check such speculation by downloading a tool such as SpyHunter 5Combo Cleaner or Malwarebytes. If you run this software and it shows some sad results, you can try fixing the affected computer areas with the help of another program such as Reimage Reimage Cleaner .
When you uninstall CryptoPatronum ransomware, you can start thinking about data recovery possibilities. At the end of this page, we have included some tools that might help you to restore at least some of the encrypted files and documents.
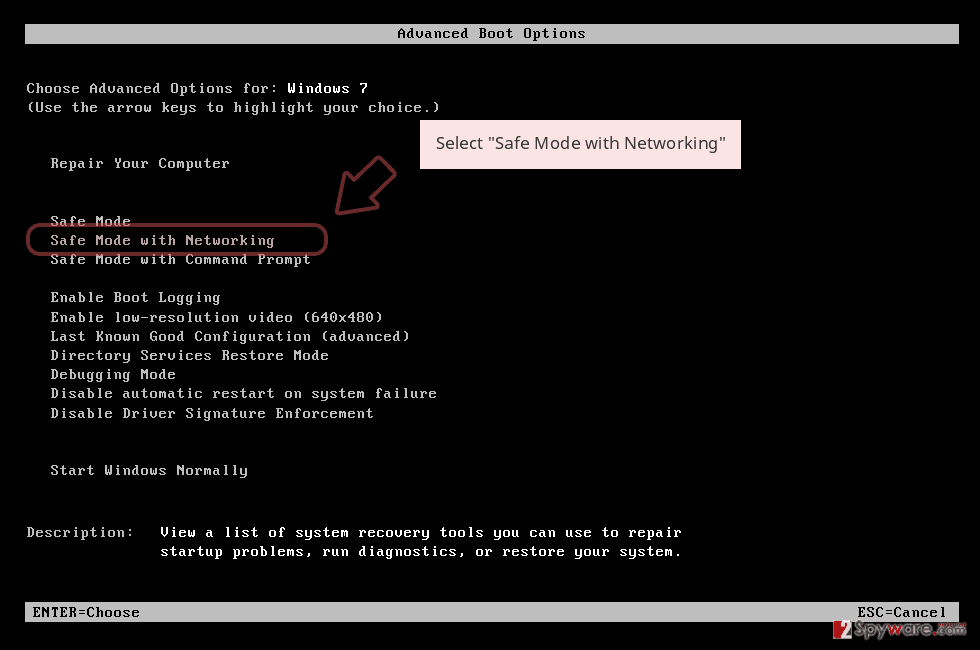
Remove CryptoPatronum using Safe Mode with Networking
To diminish malicious processes on your Windows computer system and bring the device back to its previous state, you should enable the Safe Mode with Networking option:
- Windows 7 / Vista / XP
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see the Advanced Boot Options window.
- Select Safe Mode with Networking from the list
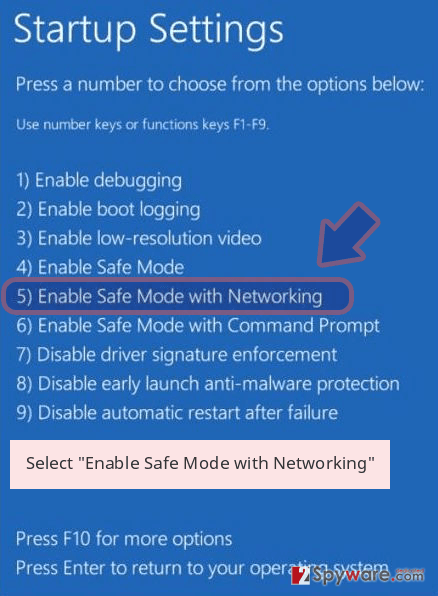
Windows 10 / Windows 8
- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
-
Log in to your infected account and start the browser. Download Reimage Reimage Cleaner or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete CryptoPatronum removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Remove CryptoPatronum using System Restore
To disable malware-related activities on your Windows device and deactivate the ransomware virus, use the following steps to activate the System Restore feature:
Bonus: Recover your data
Guide which is presented above is supposed to help you remove CryptoPatronum from your computer. To recover your encrypted files, we recommend using a detailed guide prepared by 2-spyware.com security experts.
If your files are encrypted by CryptoPatronum, you can use several methods to restore them:
Using Data Recovery Pro might help you with data recovery tasks:
Try employing this software if you are looking forward to recovering some encrypted files.
- Download Data Recovery Pro;
- Follow the steps of Data Recovery Setup and install the program on your computer;
- Launch it and scan your computer for files encrypted by CryptoPatronum ransomware;
- Restore them.
Windows Previous Versions feature might allow you to restore some files:
If you have enabled the System Restore function in the past, this type of technique might allow you to bring some of your files back.
- Find an encrypted file you need to restore and right-click on it;
- Select “Properties” and go to “Previous versions” tab;
- Here, check each of available copies of the file in “Folder versions”. You should select the version you want to recover and click “Restore”.
Shadow Explorer can result in data recovery:
Using this tool might help you to recover some individual files. However, note that this type of software might not work if the ransomware virus had permanently erased the Shadow Volume Copies of your encrypted data.
- Download Shadow Explorer (http://shadowexplorer.com/);
- Follow a Shadow Explorer Setup Wizard and install this application on your computer;
- Launch the program and go through the drop down menu on the top left corner to select the disk of your encrypted data. Check what folders are there;
- Right-click on the folder you want to restore and select “Export”. You can also select where you want it to be stored.
The cybersecurity experts are still working on the decrypter.
Finally, you should always think about the protection of crypto-ransomwares. In order to protect your computer from CryptoPatronum and other ransomwares, use a reputable anti-spyware, such as Reimage Reimage Cleaner , SpyHunter 5Combo Cleaner or Malwarebytes
This entry was posted on 2020-01-31 at 08:50 and is filed under Ransomware, Viruses.

