CoViper is a wiper-type malware that abuses COVID-19 crisis to its own advantage
CoViper is malware that prevents users from booting into Windows correctly

CoViper is malware that prevents users from booting into Windows correctly
CoViper is a type of malware that destroys Windows computer’s MBR (Master Boot Record) by rewriting it. Security researchers spotted the virus in early April as a coronavirus-themed file. As it turns out, malicious actors are clearly trying to abuse the pandemic to install malware on users’ machines (a common phenomenon among cybercriminals, as such malware strains like Maze or Sodinokibi, are actively infecting hospitals and other industries).[1]
CoViper virus belongs to the so-called “MBR locker” family that is often associated and delivered with ransomware. The latter would show victims a ransom note, claiming that the machine and files can only be restored after they pay the attackers a particular sum of money. However, this wiper does not display any ransom notes and simply prevents Windows from booting (researchers believe that it is still in a development stage). As a result, users are unable to access their machines, making CoViper removal extremely difficult for those less IT-savvy.
| Name | CoViper |
| Type | MBR locker, wiper |
| Related files | COVID-19.exe, coronavirus.bat, mainWindow.exe, run.exe, cursor.cur, Update.vbs, wallpaper.jpg |
| Developer | Angel Castillo |
| Operating principle | Rewrites Master Boot Record on Windows, preventing users to load the system correctly |
| Symptoms | Inability to boot into Windows; a black wallpaper with “Your Computer Has Been Trashed” is displayed instead |
| Infiltration | No clear attack vectors were observed, although researchers believe that malware can be spread via phishing messages on Discord communications app |
| Termination | In order to prevent malware from impacting the MBR, you should press CTRL+ALT+ESC, and then the PC will restart. After that, you should access Safe Mode with Networking as explained below and then eliminate the infection (end.exe binary) with the help of security software |
| System fix | When dealing with wiper malware, we recommend eliminating it first and then fixing the damaged Windows system with the help of Reimage Reimage Cleaner Intego |
CoViper is a relatively new wiper-type malware that was discovered by security researchers from Avast.[2] They said that the installer, which was titled as COVID-19.exe, was found accidentally, and there are little implications that malware is being widespread. Nonetheless, it is highly likely that its main attack vector is phishing messages delivered by a chatting app Discord.
Nonetheless, if CoViper malware will be developed further and combined with ransomware, it might be delivered in various other ways in order to be more successful. For example, the following methods could be used:
- Spam email attachments and embedded hyperlinks;
- Fake updates and scam messages on malicious sites;
- Software cracks and pirated program installers;
- Software vulnerabilities and exploit kits,[3] etc.
Once inside the system, CoViper delivers several files into the Temp folder on the machine, which is located in C:\Users\[username]\AppData\Local\Temp. From there, the virus copies all these files to a new location in the home directory, which is titled “COVID-19.” Five seconds later, the malware executes three executables: run.exe, Update.vbs, and end.exe, with the latter being the main file, which causes MBR to malfunction and prevents normal Windows boot sequence.
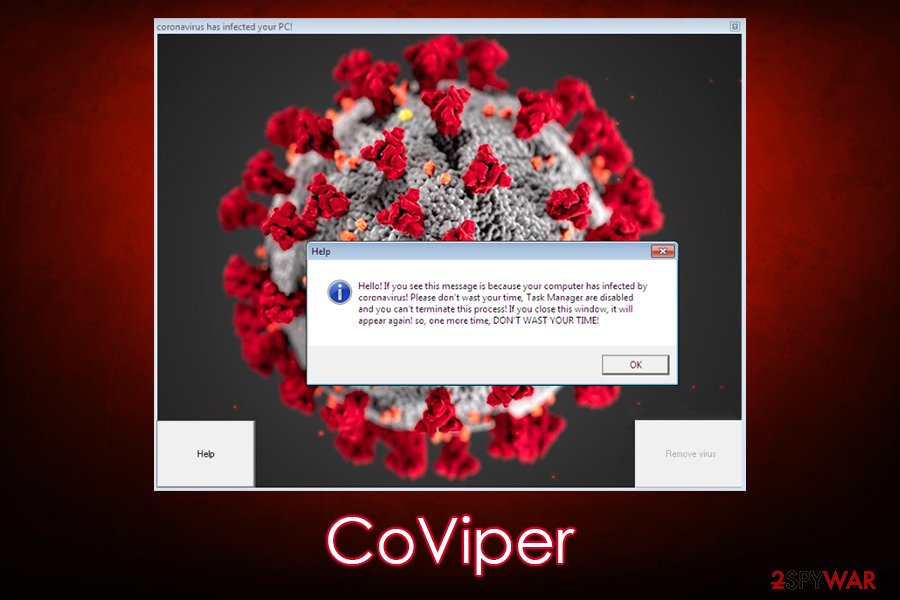
After the system is booted, victims will find that they are unable to use the Task Manager and that the appearance of their mouse cursor is now different. Then, CoViper malware will launch a pop-up window that is titled “coronavirus has infected your PC!” which includes the famous COVID-19 related picture. In the corners of this window, users can see two buttons – “Help” and “Remove virus.”
CoViper is a type of wiper that is often called a MBR locker

CoViper is a type of wiper that is often called a MBR locker
The former opens another pop-up, which claims that the Task Manager has been disabled and that it is impossible to do anything about that. The latter button is grayed out/disabled, so this might be a pre-release function that would allow users to disable malware functionality after a ransom is paid.
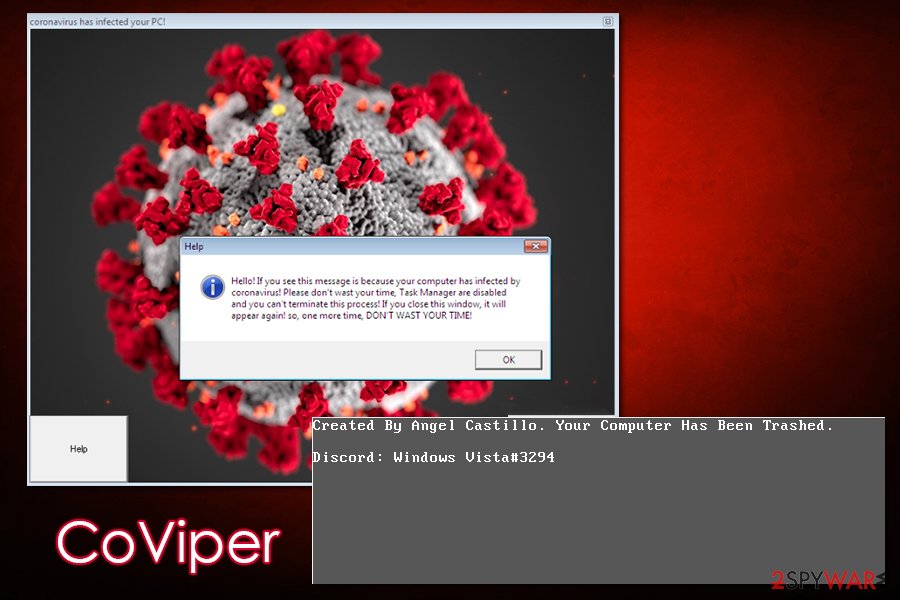
If the system is rebooted once more, users will not be able to see anything apart from a black wallpaper which states:
Created by Angel Castillo. Your Computer Has Been Trashed.
Discord: Windows Vista#3294
Researchers claimed that CoViper was compiled thanks to an open-source tool that is available online, but will not disclose its name, or the author’s name, to the public:
Furthermore, we would like to mention that while investigating CoViper, it is clear that this malware was actually generated by a custom tool publicly available on the Internet, for free. Because we have come to a conclusion that the author of this tool is not actually the author of CoViper itself, we will not disclose his name. We will also not disclose the tools’s name so that we don’t bring more attention to it.
Although CoViper is a wiper, researchers managed to find a way to trick its operation and allow users to boot into normal Windows mode themselves. The trick is to press CTRL+ALT+ESC on the keyboard and then allow the system to reboot – a normal MBR boot sequence would be initiated in such a way. However, this does not solve all the problems, as the malware will begin the reinfection process as soon as Windows is booted.
To bypass that and remove CoViper safely, users should boot into Safe Mode with Networking and perform a full system scan with powerful security software, such as SpyHunter 5Combo Cleaner or Malwarebytes. Once malware is terminated, users should also scan their machines with Reimage Reimage Cleaner Intego to ensure that all Windows settings and functions are back to normal.
Currently, it is hard to say what the main goal of CoViper malware is, as it does nothing to benefit the attackers. Considering naming patterns and its functionality, it is highly likely that the malware is currently operated as a prank, and might be later developed into something more sinister.
Avoid malware infections that could result in negative consequences
If users get infected with malware sample that is still in the development stage, it is typically not difficult to eliminate and avoid more serious consequences, such as financial losses, loss of access to personal files, or even identity theft. However, in most cases, malware is well polished by the attackers and functions as intended – it can compromise users’ online safety and computer security. What makes matters worse is that threats like keyloggers or remote access trojans (RATs) are designed to sustain low visibility on the host system, preventing users from noticing it on time. As a result, malware can sit on computers for weeks, months, or even years before it is detected.
According to research, CoViper is still in development and might be provided with ransomware functions later

According to research, CoViper is still in development and might be provided with ransomware functions later
Therefore, it is always important to secure the machine from cyberattacks and practice precautionary measures. As mentioned above, malicious actors can use a variety of methods for malware infiltration, so comprehensive preventive measures should be performed at all times. Here are some tips from industry experts:[4]
- When dealing with Discord or other chat applications, do not click on links that come from unknown individuals as this action can result in malware infection;
- Update your Windows OS and all the installed applications as soon as security patches are shipped by developers;
- Employ comprehensive anti-malware software and keep it updated at all times;
- Protect all your accounts with strong passwords and never reuse them for different accounts;
- Do not download software cracks or pirated application installers;
- Backup all your personal files on a removable drive, such as USB Flash;
- Never allow email attachments to ruin the macro function and never click on links inside suspicious emails.
Eliminate CoViper virus and avoid personal data loss
If you have never heard about CoViper virus or similar MRB wiper around, its actions performed on the machine might come as a shock – regular wallpaper is gone, the taskbar is not accessible, and the PC does not work as it is supposed to all. Even calling up the Task Manager is impossible (this would allow killing the main process of the malware, although it can be done with apps like Process Explorer). Besides, the button to remove CoViper does not work, either. As a result, it is impossible to launch any apps or even navigate throughout the PC normally.
However, the malware is relatively flawed, and it has a backup mechanism that can be initiated with a simple CTRL+ALT+ESC combination. Once this is pressed, you should interrupt the boot sequence three times (simply press the Power button for a few seconds), and you should be able to access Safe Mode. Then, use a portable anti-virus application that you should place into the USB stick or another removable device and then scan the computer fully for CoViper removal.
This entry was posted on 2020-05-19 at 04:38 and is filed under Malware, Viruses.

