Corona-lock is yet another ransomware campaign using the disease as a lure

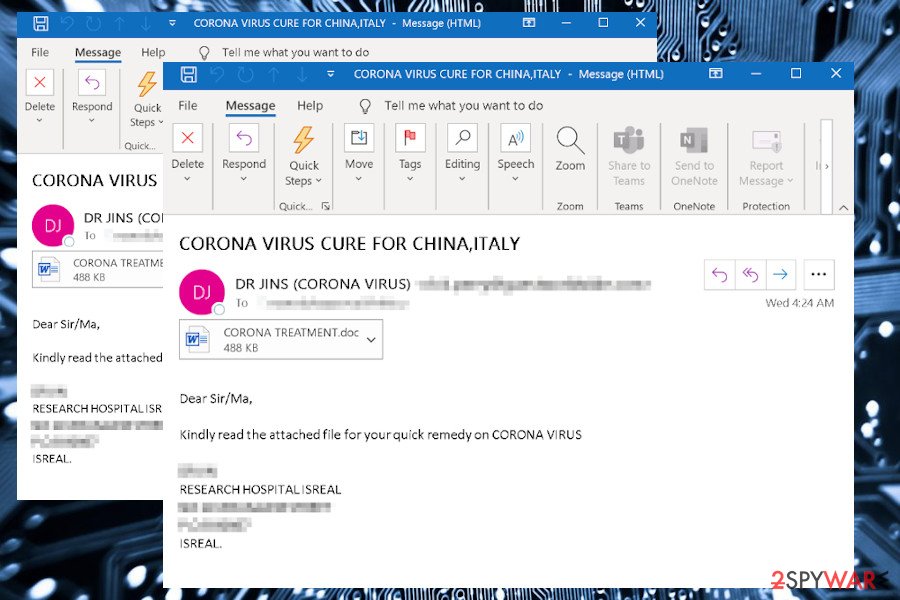
Corona-lock ransomware is a cryptovirus that misuses the COVID-19 pandemic to trick people into opening malicious ransomware payload and lock personal people’s files. It has been found spreading via spam emails[1] called “Corona virus cure for China, Italy.” The email contains a CORONA TREATMENT.doc file, which is infected with the malicious ransomware payload.
Upon the infiltration, the Corona-lock virus roots into the OS by changing Windows Registry entries and injecting malicious executables among boot up files. After that, the system is forced to restart leading to a complete lock of personal files. All non-system data gets encrypted by the .corona-lock! file extension. Usually, victims cannot fully understand what happened until the README_LOCK.txt note gets placed on the desktop and other folders.
The Corona-lock ransomware is also known as the CovidWorldCry virus. Both variants are not decryptable. At least not yet. The criminals behind this threat programmed this threat to run a combination of ChaCha and AES encryption algorithm, which is a tough nut to crack for cybersecurity experts.
| Name of the virus | Corona-lock |
| Also known as | CovidWorldCry ransomware, CoronaLock ransomware, Corona-Lock virus, BigLock ransomware |
| Ransom note | README_LOCK.txt or !!!READ_ME!!!.TXT |
| Encryption model | ChaCha + AES |
| Contacts | Criminals provide the [email protected] email |
| Payload | Usually, people are represented with malicious spam emails that contain CORONA TREATMENT.doc file with a hidden 2020-05-22_17-36-19.exe payload |
| File marker | The ransomware locks files using a strong encryption model and appends .corona-lock file extension. However, people can also be attacked by other Corona-lock ransomware variants exhibiting .biglock file marker |
| Goals | The ransomware is a crypt-extortionists, meaning that it’s sole purpose is to earn the money. For that, it locks files and demands a ransom payment |
| Distribution | The virus has been found spreading via Coronavirus-related spam email messages in particular. However, experts warn that the payload can also be launched via Rig exploit kit, rogue software installers, and cracks |
| Removal | If ransomware infected the machine, the only way to delete it is to restart the machine into Safe Mode with Networking (a guide below explains how to to that) and then run a full system scan with a professional AV engine. |
| Data recovery | There’s no official Corona-lock decryptor. However, it’s advisable to backup encrypted files and send the samples to cybersecurity experts for analysis. Besides, you can try decrypting the data using alternative methods, such as Volume Shadow Copies |
| Windows recovery | Upon ransomware elimination, recover the system using Reimage Reimage Cleaner Intego repair tool |
The Corona-lock virus is ransomware without a family. It’s a stand-alone threat, which only can be attributed to the COVID-19 campaign viruses[2] alongside Cov19, Coronavirus ransomware, Dharma, Maze, REvil, CovidLock, and many others. Although it’s one of the ransomware-type viruses that take advantage of the Rig exploit kits, the most victims are caught on the hook by reliable-looking spam emails that contain the CORONA TREATMENT.doc file.
This CORONA TREATMENT.doc spam attachment disguises the malicious 2020-05-22_17-36-19.exe file, which is a unique Corona-lock ransomware payload. Once launched, the creates the following entries:
- %APPDATA%\key.file
- %HOMEPATH%\desktop\readme_lock.txt
- D:\install.log.corona-lock
- :\000814251_video_01.avi.corona-lock
- :\delete.avi.corona-lock
- :\join.avi.corona-lock
- :\archer.avi.corona-lock
- :\dashborder_96.bmp.corona-lock
- :\dial.bmp.corona-lock
- :\dialmap.bmp.corona-lock
Moreover, the Corona-lock virus creates malicious processes under names %WINDIR%\syswow64\vssadmin.exe, \conhost.exe, \dllhost.exe, \vssvc.exe, and %WINDIR%\syswow64\wbem\wmic.exe, which lock AV engines and increase ransomware persistence.
According to the VirusTotal analysis[3], the Corona-lock file virus executable can be detected and quarantined by 61 security tools out of 71. The most common detections are the following:
- Ransom:Win32/Coronalock.DEA!MTB (Windows Defender)
- Win32:Malware-gen (AVG)
- Trojan.GenericKDZ.67331 (BitDefender)
- Trojan.TR/AD.RansomHeur.eku (F-Secure)
- Trojan.Win32.DelShad.dfc (Kaspersky)
- Win32:Malware-gen (Avast)
- A Variant Of Win32/Kryptik.HDOJ (ESET-NOD32), etc.
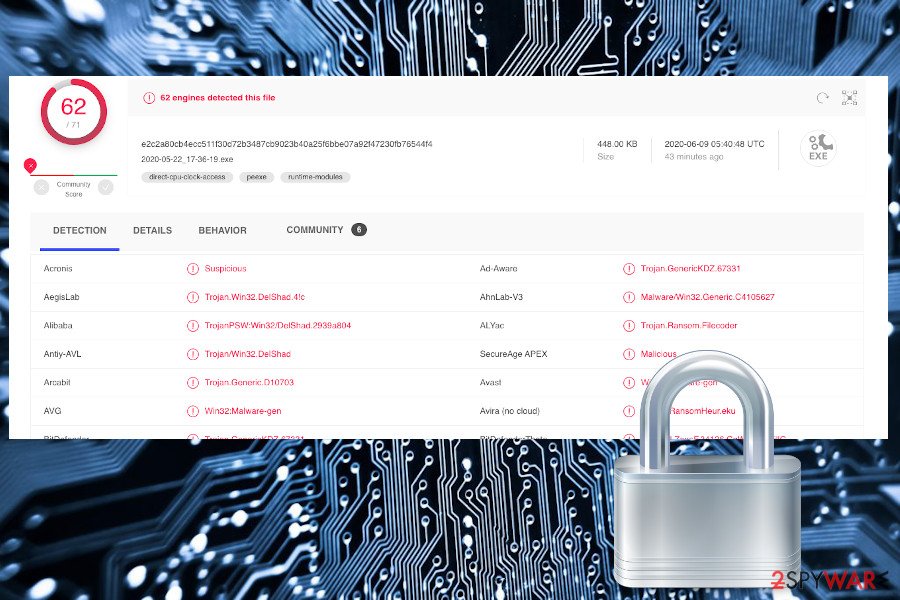
The corona-lock virus can currently be detected by most of the AV security tools

The corona-lock virus can currently be detected by most of the AV security tools
All activities initiated by Corona-lock ransomware are extremely malicious. It roots into the OS, compromises %AppData%, %Temp%, and entries in other directories, eliminates Shadow Volume copies, terminates core processes, and starts alternative ones, etc. All performance leads to one goal – complete restriction from personal files.
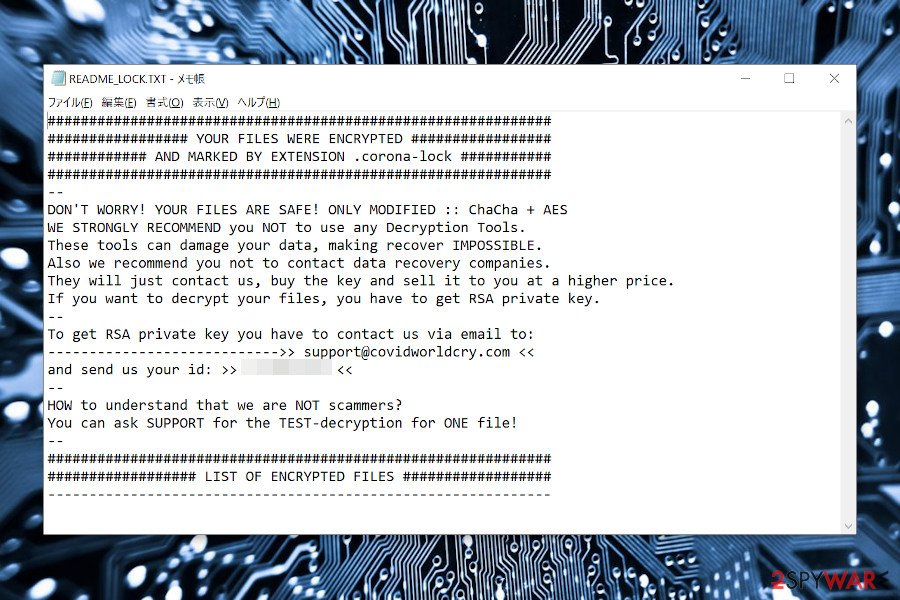
Once the files are encoded by .corona-lock file extension, the ransomware generates a note README_LOCK.txt or !!!READ_ME!!!.TXT, which contains a unique ID number, which is bound to a personal file decryption key stored by criminals. to get the key, victims have to write an email to [email protected] and pay the criminals a ransom payment.
YOUR FILES WERE ENCRYPTED
AND MARKED BY EXTENSION .corona-lock—
DON’T WORRY! YOUR FILES ARE SAFE! ONLY MODIFIED :: ChaCha + AES
WE STRONGLY RECOMMEND you NOT to use any Decryption Tools.
These tools can damage your data, making recover IMPOSSIBLE.
Also we recommend you not to contact data recovery companies.
They will just contact us, buy the key and sell it to you at a higher price.
If you want to decrypt your files, you have to get RSA private key.
—
To get RSA private key you have to contact us via email to:
—————————->> [email protected] <<
and send us your id: >> 2374052812 <<
—
HOW to understand that we are NOT scammers?
You can ask SUPPORT for the TEST-decryption for ONE file!
—LIST OF ENCRYPTED FILES
If you are currently seeing such a message, we strongly recommend you to backup the encrypted files to alternative storage (hard drive, USB flash drive, cloud storage, etc.) and then restart the machine into Safe Mode with Networking. The safe mode disables malicious processes and allows launching the security software. To remove Corona-lock ransomware virus from the system thoroughly, we recommend using Malwarebytes, SpyHunter 5Combo Cleaner, or similar security software.
Upon successful Corona-lock removal, it’s must to recover the Windows directories that the virus might have compromised. Distorted Windows Registries, disabled processes, and written/deleted files, modified attributes, and other performances can trigger Windows malfunctions and crashes. For this purpose, you can take advantage of the Reimage Reimage Cleaner Intego tool.
.corona-lock file recovery options
Do not get confused by false claims on some unreliable sources that the removal of Coronal-lock ransomware using an anti-virus tool will recover personal files. Ransomware removal means that the AV engine quarantines the malicious ransomware processes and files.
The data that is encrypted using the ChaCha + AES encryption algorithm and exhibits the .corona-lock file extension will not be encrypted upon virus removal. Data encryption requires a specific decryption software that reverts the changes initiated by the cipher.
Corona-lock virus appends .corona-lock file extension to encrypted files

Corona-lock virus appends .corona-lock file extension to encrypted files
Criminals behind the Corona-lock virus offer their victims to buy the decryptor for a considerable amount of money and we are sure that a part of victims agree with the payment as they crave for unlocking important data. However, we do not recommend supporting criminals in any way.
Instead of that, experts from NoVirus.uk[4] advisable to remove Corona-lock ransomware and then decrypt files using alternative methods. First of all, you can contact ransomware researchers and provide them with ransomware examples for testing. It’s very likely that sooner or later they can develop a free decryptor.
While the Corona-lock decryptor is under development, you can try decrypting the files using third-party data recovery programs, System Restore, or Shadow Volume copies. You can find a comprehensive guide at the end of this article.
.biglock file extension is related to Corona-lock ransomware
Corona-lock ransomware is also known as the CovidWorldCry virus. Both variants are equally dangerous. However, depending on the variant that infiltrated the machine, the diverse extension can be appended to personal files.
In many cases, people find their files encrypted by the .biglock file extension virus. Files that contain such a suffix cannot be opened, moved, deleted, or renamed. Unfortunately, automatically renamed personal files means only one thing – ransomware attack.
Beware that criminals seek to gain as much money as possible. Corona-lock virus managers may demand you to pay a redemption that varies from $480 to $1500 depending on the amount of encrypted data.
As we have already pointed out, this ransomware cannot be decrypted for free. Thus, you can either pay the criminals or get rid of Corona-lock virus from your machine and try data recovery methods provided by our security experts.
Coronavirus-themed email spam keeps flooding inboxes
During the worldwide Coronavirus pandemic, criminals launched thousands of disease-related spam campaigns, malware, and viruses. Unfortunately, millions of people were caught on the hook of intriguing news, disease prevention methods, charities, and other rogue email messages that were used by scammers to infect PCs with ransomware.
It’s very important to raise people’s consciousness, so we keep repeating that official and reliable organizations are sharing the information on the official website or other reliable sources. They are not sending emails with questionable attachments to random PC users unless they are registered or made their e-mails public.
However, the malspam campaign is not the only way to spread malware and ransomware viruses. Criminals can quite easily exploit software vulnerabilities, known as flaws. Hackers take advantage of the exploit kits to gain access to people’s machines. This particular ransomware is known for exploiting Rig exploit kit, which allows hackers to inject the malicious payload to the targeted machines remotely. Therefore, it’s crucial to update outdated software and patch reported vulnerabilities without a delay.
Corona-lock virus managers are exploiting spam emails and Rig exploit kits to infiltrate machines

Corona-lock virus managers are exploiting spam emails and Rig exploit kits to infiltrate machines
Therefore, people should be extremely careful with suspicious email attachments, avoid downloading pirated software, cracking software, visiting x-rated websites, or clicking on doubtful ads. Instead of that, take advantage of a reputable anti-virus suite, which features real-time protection and other additional security measures.
Corona-lock removal guide: learn how to eliminate the entire ransomware package thoroughly
Usually, people attempt to remove Corona-lock ransomware and similar cyber-infections by simply launching the AV tool in a regular Windows mode. Unfortunately, such an attempt is usually unsuccessful because ransomware runs malicious processes that block security software.
If you are currently solving such a situation, you should perform Corona-lock removal while the machine is restarted into Safe Mode with Networking. You can find a full guide explaining how to do that down below.
Besides, it’s very important to select a professional security software to elimination to Corona-lock virus. Ransomware, in general, is an intricate piece of software, which may remain in the disguise of Windows system files and re-attack the machine upon elimination if a single malicious entry is left intact. Our recommended programs are SpyHunter 5Combo Cleaner and Malwarebytes, but if you have another preferable security tool, you are free to use it, except make sure it’s fully up-to-date.
This entry was posted on 2020-06-09 at 03:17 and is filed under Ransomware, Viruses.

